มีช่องโหว่ในภาษา Vyper บางเวอร์ชัน และโครงการเช่น Curve ก็ถูกโจมตี
เมื่อวันที่ 30 กรกฎาคม ตามเวลาปักกิ่ง พบว่าภาษาโปรแกรมสัญญาอัจฉริยะ Vyper บางเวอร์ชันมีช่องโหว่ร้ายแรง และส่งผลให้โครงการสำคัญบางโครงการรวมถึง Curve Finance ถูกโจมตีด้วยเหตุนี้
ตามประกาศของ Twitter จาก Vyper ภาษาการเขียนโปรแกรมสัญญาอัจฉริยะ Ethereum พบว่าสามเวอร์ชัน ได้แก่ 0.2.15, 0.2.16 และ 0.3.0 มีช่องโหว่ร้ายแรงที่อาจปิดการใช้งานการล็อคการกลับเข้าใหม่ สำหรับโครงการบล็อคเชน ปัญหานี้อาจทำให้กระบวนการดำเนินการของสัญญาหยุดชะงักหรือให้ผลลัพธ์ที่คาดเดาไม่ได้ ซึ่งส่งผลต่อความเสถียรของทั้งระบบ ในการประกาศ ทีมงาน Vyper ขอแนะนำอย่างยิ่งว่าโครงการทั้งหมดที่ใช้เวอร์ชันที่ได้รับผลกระทบเหล่านี้ควรติดต่อพวกเขาทันทีเพื่อรับการสนับสนุนทางเทคนิคและวิธีแก้ปัญหาอย่างทันท่วงที
อย่างไรก็ตาม ผลกระทบของช่องโหว่นี้ได้เกิดขึ้นแล้ว ทีมงาน Curve ทวีตในนาทีต่อมาว่าพูลเสถียรบางตัวที่ใช้ Vyper เวอร์ชัน 0.2.15 รวมถึง alETH, msETH และ pETH ได้รับความเดือดร้อนจากการโจมตีทางไซเบอร์เนื่องจากความล้มเหลวของฟังก์ชันล็อคการกลับเข้าใหม่ ช่องโหว่นี้ทำให้ผู้โจมตีสามารถเรียกใช้ฟังก์ชันบางอย่างได้หลายครั้งในธุรกรรมเดียว ซึ่งอาจก่อให้เกิดความเสียหายอย่างมากต่อโครงการบล็อกเชนที่เกี่ยวข้อง
คำอธิบายรูปภาพ
 !
!
แถลงการณ์ทางทวิตเตอร์ของ Curve
คำอธิบายรูปภาพ
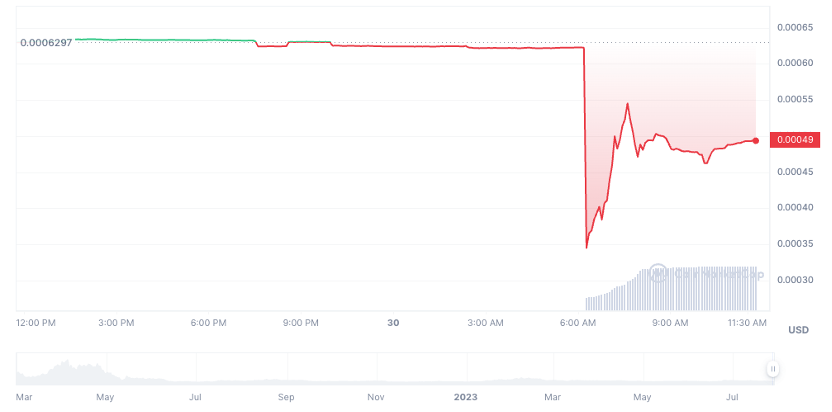
ราคาโทเค็นของ JPEG ที่มา: Coinmarketcap
โครงการ JPEG ยังตอบสนองหลังจากการเปิดตัว Curve โดยอ้างว่า โปรโตคอลของเราไม่อยู่ในขอบเขตของเหตุการณ์การแฮ็กนี้ และนักพัฒนาของเรามีประสิทธิภาพมาก
นอกจากนี้ ฝ่ายโครงการอีกสองฝ่ายก็ได้รับผลกระทบเช่นกัน ตามข้อมูลของ Hexagate โครงการให้ยืม AlchemixFi และโปรโตคอล DeFi MetronomeDAO ก็ถูกโจมตีเช่นกัน และผู้โจมตีสร้างรายได้รวม 13 ล้านดอลลาร์และ 1.6 ล้านดอลลาร์ ทั้งสองโครงการออกแถลงการณ์ในครั้งแรก Alchemix อ้างว่าสังเกตเห็นเหตุการณ์การแฮ็กซึ่งอาจนำไปสู่ความไม่แน่นอนในราคาของโทเค็นโครงการ และแนะนำให้ LP ถอนสภาพคล่องออกจากกลุ่มโดยเร็วที่สุด
MetronomeDAO กล่าวว่า “ผู้ให้บริการรายใดก็ตามที่ให้สภาพคล่องในคู่ msUSD และผู้ใช้ Optimism ที่โต้ตอบกับ msETH บน Velodrome ควรทราบว่าสถานะของพวกเขาจะไม่ได้รับผลกระทบ นอกจากนี้ เงินฝากของ Metronome และสถานะที่เปิดอยู่ทั้งหมดจะไม่ได้รับผลกระทบ ซึ่งได้รับผลกระทบจากเหตุการณ์นี้”



