Rejecting "security claims," wallet security is entering an era of verifiability.
- 核心观点:Web3钱包安全重点转向交易前风险拦截。
- 关键要素:
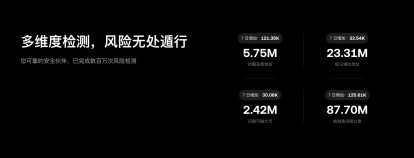
- 钓鱼等“交易前风险”成主要威胁,年损失近5亿美元。
- 行业趋势是将安全能力“产品化”,提供可理解的风险清单。
- 审计报告需集中、可查、持续更新,形成可复核证据链。
- 市场影响:推动钱包安全标准透明化,影响用户选择。
- 时效性标注:中期影响。

In 2025, Web3 will enter a new phase of "larger-scale and higher-frequency use," and wallets will evolve rapidly from "crypto storage tools" to on-chain entry points and transaction operating systems. Market research firm Fortune Business Insights predicts that the crypto wallet market will be worth approximately $12.2 billion in 2025 and could grow to $98.57 billion by 2034.
The expansion on the user side is equally evident: a16z crypto estimates in "State of Crypto 2025" that there are approximately 40-70 million active crypto users, while the number of crypto asset holders who "hold coins but are not necessarily active on the chain" is approximately 716 million; Crypto.com Research's report also gives a figure that the number of global crypto holders will increase from 681 million to 708 million in the first half of 2025.
The rise in scale and penetration rate also amplifies security risks. It's no longer just about "whether the contract has vulnerabilities," but rather whether risks can be prevented in advance at key user points, such as clicking links, connecting wallets, signing authorizations, and transferring funds.
The attack surface in the on-chain world often extends beyond contract vulnerabilities, frequently encompassing low-barrier-to-entry phishing attacks, fake domains, impersonation of customer service, and authorization fraud – all considered "pre-transaction risks." For example, Chainalysis's definition of "crypto drainers" (wallet drainers/phishing authorization tools) points out that these tools don't steal account passwords, but rather trick users into connecting their wallets and approving malicious transactions, thereby directly transferring assets. Public data also shows that losses related to "wallet drainers" approached $500 million in 2024.
Therefore, improving the security of Web3 wallets will no longer focus solely on whether contracts have vulnerabilities, but will require further attention to how to proactively intercept risks at key points in user behavior, i.e., "pre-transaction security".
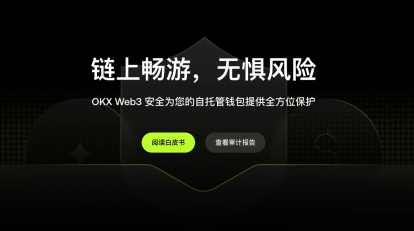
Against this industry backdrop, "security" is becoming increasingly difficult to address with a mere slogan. Instead, it is more like a set of governance capabilities that need to be continuously proven: whether it can be verified, traced, and disclosed in a timely manner is becoming an important basis for users to choose a wallet.
From "security claims" to "an understandable list of security capabilities"
For a long time, wallet projects often touting security with phrases like "We've done audits," "We have a white paper," and "We take risk control very seriously." However, with the industrialization of fraud and phishing, these "security claims" are losing their persuasiveness. The moment users actually get caught often occurs in extremely short interactions like clicking a link, connecting to a wallet, and signing an authorization. Chainalysis describes "crypto drainers" as a typical path: attackers impersonate legitimate pages, guide users to complete authorizations, and then transfer their assets; their research even mentions cases of forging the Magic Eden page to carry out malicious transactions targeting Ordinals users.
Publicly available data is also driving the industry narrative towards greater "understandability." Security Week, citing statistics from Scam Sniffer, reported that nearly $500 million in losses were caused by wallet emptyers in 2024, affecting over 332,000 victims—these incidents don't require attackers to breach complex systems, but rather rely on users not understanding the risks during interaction. Meanwhile, Chainalysis, in its 2025 disclosure, estimated that on-chain fraud revenue in 2024 was at least $9.9 billion, and this figure could be revised upwards as more addresses are identified. When the risk primarily stems from "readability gaps on the user side," wallet vendors must move security from backend engineering to the frontend of their communication.
As a result, more and more wallets in the industry are beginning to "productize" their security capabilities: instead of simply telling you "we are secure," they break down protective actions into a list that users can understand—which tokens will be marked as high-risk, which transactions will trigger alerts, which addresses or DApps will be blocked, and why. The essence of this change is to rewrite security from a "qualification narrative" to an "interactive narrative": allowing users to obtain actionable information before signing, rather than having to look at an audit PDF afterward.
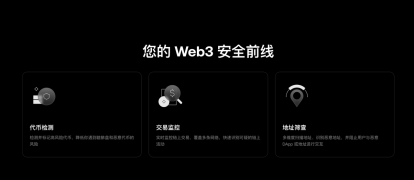
In response to this trend, OKX Wallet's newly launched and upgraded Security Center page provides a typical example of "checklist-based expression." The page clearly outlines user-facing security capabilities as three "front lines of defense": Token risk detection, Transaction monitoring, and Address screening, each explained in a single sentence: "Marking high-risk tokens to reduce exposure to honeypots and malicious parties," "Real-time cross-chain monitoring to identify suspicious on-chain activity," and "Blocking interactions with malicious DApps and addresses." The advantage of this approach is that even users unfamiliar with security terminology can quickly connect the information to their current actions—whether they should click, sign, or transfer funds.
Click here to access: OKX Wallet Security Landing Page Audit Report: https://web3.okx.com/zh-hans/security
More importantly, "understandable" does not equate to "talking to oneself." On the same page, OKX Wallet also provides an entry point for "View audit reports," linking the "capability list" with "third-party verification." Furthermore, its Help Center's audit report collection page further clarifies the audit scope, the number of issues found, and the status of fixes, allowing users to move from "understanding capabilities" to "verifying evidence" when needed.
The core value of this shift "from security claims to understandable checklists" lies not in making security sound more grandiose, but in making it more actionable: as fraud increasingly relies on inducement and disguise, the ability of wallets to provide risk warnings at interaction points and explain in language that users can understand "where it is dangerous, why it is dangerous, and what you should do" is becoming part of security capabilities and increasingly determines whether users will fall into a trap at a crucial step.
Audit information is "publicly accessible": transforming third-party endorsements from "linked" to "verifiable chain of evidence."
In the wallet industry, auditing has long faced a real problem: many projects have indeed "undergone audits," but the information is scattered across announcements, PDFs, and social media reposts, making it difficult for ordinary users to quickly understand "who audited, what was audited, whether it was fixed, and when it was updated." OKX Wallet's more conspicuous move this time is to centralize publicly available third-party audit reports into a unified entry point and directly label them on the page as "Published on November 11, 2022, updated on November 17, 2025," allowing users to immediately determine that this is not a one-off display but an continuously maintained information disclosure window.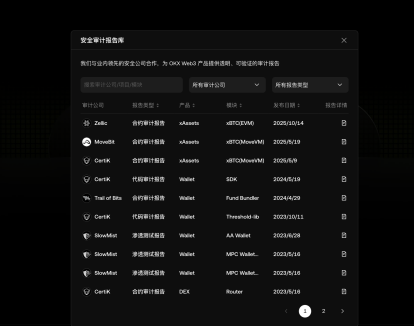
Judging from the publicly available entries on this collection page, its scope of disclosure does not stop at the traditional audit object of "smart contracts". Taking CertiK's entry from 2024-05-23 as an example, the audit content clearly covers the key code paths of the mobile and front-end: including iOS/Android components, front-end ReactJS UI components and JS controllers that interact with the keyring, as well as multiple wallet SDK modules, and also provides the audit methods and conclusions.
On the same page, the entries for SlowMist are closer to the "new paradigm" of wallet evolution in the past two years—AA smart contract accounts, MPC keyless wallets, and Ordinals transaction modules are all listed as publicly auditable objects; in addition, the audit information for the "private key security module" is listed separately, stating directly that "the private key or mnemonic phrase is only stored on the user's device and will not be sent to external servers," using a clearer boundary description to respond to users' core concerns about key security.
The value of this "centralized display" lies not only in more complete information, but more importantly in binding "new capabilities" and "verifiability" to the same entry point: as the wallet industry increasingly moves towards complex architectures such as AA and MPC, what users need most is not a statement like "we are secure", but evidence that can be quickly verified—whether the audit scope covers key modules, what the methods are, whether the risks have been closed-loop repaired, and whether the information is continuously updated.
Meanwhile, according to OKX Wallet, after this upgrade, newly added audit reports and related information can be updated directly through configuration without the need for a new release. If this mechanism can operate stably in the long term, it actually shortens the path to "external verifiability," rather than simply saving on R&D and release costs.
For users, this means that when an audit is added or a fix is completed, the public entry point can reflect the "latest status" more quickly, reducing the uncertainty of "only being able to judge based on forwarded screenshots/old links" in the critical risk window. For third-party observers and researchers, it is easier to form a traceable timeline: which modules were audited and when, what level of problems were found, when the fix was confirmed and publicly updated, thus truly turning "third-party endorsement" into a continuously verifiable chain of evidence, rather than a one-time PDF.