全景解读MEV赛道项目与前沿发展
原文作者:Benny Attar
原文编译:DeFi之道
有关区块链黑暗面的介绍,最早出现在 Reddit 上一篇题为「Miners Frontrunning」的帖子中,在这篇具有历史意义的文章中,基于以太坊内存池的公开性,作者概述了矿工借此如何进行抢先交易,并从中套利的过程。当然,在金融领域,这并不是一个新事物,迈克尔·刘易斯在 2014 年出版的《Flash Boys》一书中,就讲述了高频交易中的交易抢跑,之后在 2019 年发表的《Flash Boys 2.0 》论文中,他将这些观察结果运用到区块链领域,并展示了在这种所谓的公平金融系统中,人们如何利用机器人进行广泛的交易套利。据统计,直到今年 9 月以太坊合并为止,区块链系统的套利交易累计价值已经超过了 6.75 亿美元!
MEV(最大可提取价值)可能是区块链行业最糟糕的流行语缩写,它是由验证者、矿工节点、区块生产者等共同合作,通过对某区块内的交易进行重新排序所获得收益。当然,MEV 并不完全由区块生产者所提取,被称为 "搜索者 "的套利交易者和机器人也会检测区块链数据来寻找套利的机会。通常,搜索者和验证者通过协同工作来寻找区块链上的潜在盈利交易,所以,MEV 也成为了发生在链上套利交易的总称。

图片来源:由无界版图 AI 生成
MEV 攻击类型
套利交易者、机器人和脚本也可以从区块链应用中提取了相当比例的 MEV。从某种程度上来说,MEV 可以被定义为每笔链上交易背后的隐藏税,在我们分析 MEV 解决方案的全景图之前,了解生态系统中所发生的 MEV 攻击类型也很重要。当然,可能还有一些攻击类型我们还不知道,但下方是一些最典型的利用 MEV 的攻击方式。
抢先交易
抢先交易是指机器人密切关注一个区块链网络的内存池,并从中寻找有利可图的交易,一旦找到这样的机会,抢跑机器人就会发起相同的交易,并通过支付更高的 GAS 费,来获得抢跑的潜在收益。
DEX 套利
鉴于自动做市商可以在任何时候为代币提供不同价格的流动性,这为那些想通过价格差异进行套利的机器人提供了可能。比如:当两个 DEX 以不同的价格为某个代币提供流动性时,机器人就可以在其中一个低价的 DEX 上购买,并在另一个 DEX 卖出。其实,在很多情况下,DEX 套利对生态网络发展不都是好的,更多时候,DEX 需要不断地重新平衡资金池来保持 DEX 的健康发展。
尾随交易
尾随交易是指交易发送者希望他们的交易处于 "目标交易订单 "之后。通常情况下,这些交易可能是为了利用新的代币上市、或是 rebase 代币(如 AMPL),或是利用 DEX 上大额交易后的价格差异。
清算
作为一种回溯策略,搜索者通过不断的分析区块链上的数据,根据货币波动和价格预言机以确定可以在何处清算借款人的借贷协议。一旦头寸可以被清算,机器人就会提交清算交易并从清算费用中获利
三明治攻击
搜索者在内存中扫描潜在的大金额交易,在交易发生之前,搜索者买入最终会升值的资产,而在鲸鱼的交易执行之后,搜索者马上卖出相同的资产,从而 "夹住 "这笔大金额的交易(大家俗称为夹子),流动性提供者也可以利用三明治攻击,来创造更高的滑点。
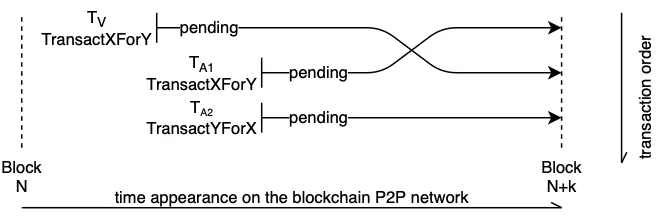
套利机器人的三明治攻击可视化(来源:Liyi Zhou )
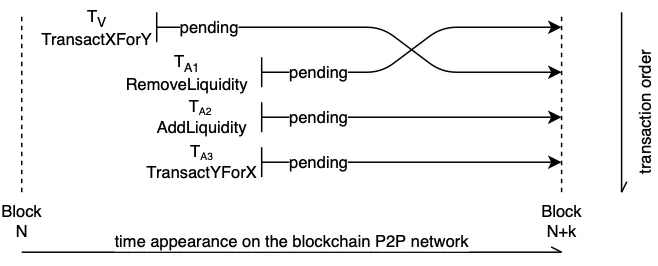
流动性提供者的三明治攻击可视化(来源:Liyi Zhou )
时间强盗攻击
时间强盗攻击是一种更高级别的 MEV 攻击形式,即重组过去的区块,在其中提出包含改变交易的新区块,牺牲网络用户的利益。虽然这种攻击极难实现,但如果发生,一定会影响区块链的安全和共识。
NFT MEV
搜索者或区块生产者可以设计交易,成为第一个购买某款热门 NFT 的人,或者在同一交易中购买更多的 NFT。
JIT 流动性
即时流动性(Just-In-Time)是 MEV 交易排序中的另一种形式,LP 提供者在 swap 前后立即 mint 和 burn 头寸,虽然它的竞争性很强,但提高了交易的执行力,不然会受到高价格的影响,此外通过 JIT 流动性方式达成的交易数量其实很少。
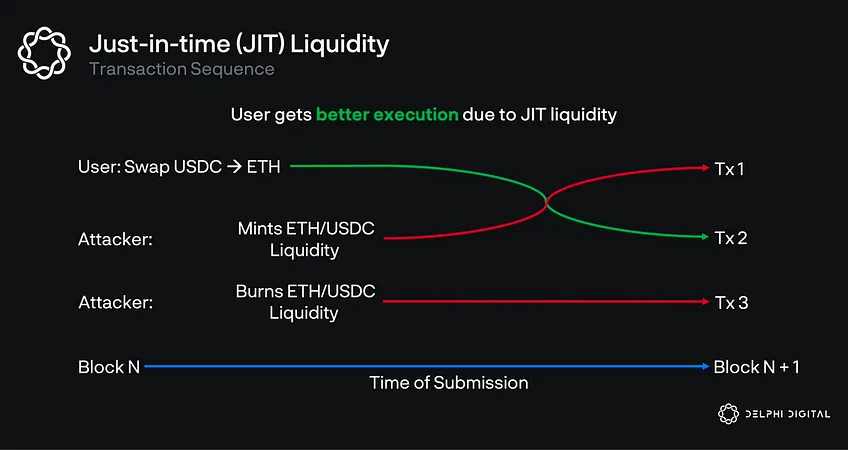
JIT 流动性可视化(来源:Jon Charbonneau,Delphi Digital)
还有一些其他受人关注的 MEV 攻击形式,比如:跨链 MEV、稳定币套利、uncle-bandit 攻击攻击等。
MEV 的好与坏
从第一眼看,MEV 似乎会对区块链的生存威胁。潜藏在钱包签名下的隐性交易成本对于一种新的技术范式来说,一定不会有正向的经济效益,MEV 的确是为数不多的导致新手和高级用户体验恶化的原因之一。比如:用户遭受更大的滑点和大额交易的更差执行(由于三明治交易和 DEX 套利)、GAS 的增加和链上交易的变慢(由于抢跑交易)、遭受可能的共识稳定性威胁(验证者重组区块)等。
然而,虽然有负面影响,但 MEV 的存在也有一些积极因素,比如:套利交易者确保了各 AMM 的代币定价是相同的、满足了稳定币平价的机制、确保 DeFi 贷款的顺利清算、保持对区块提议者的激励以增加区块链的安全性(通过提供更高的奖励)等。
不论 MEV 所带来的积极影响和消极影响谁大,但 MEV 始终是存在,特别是在合并后的区块链世界。现在,鉴于对 MEV 及其它在区块链中的生存方式的不同,也有不同的方法来面对 MEV 的影响。对 MEV 的分类和处理有几种不同的方式。我们可以按照对 MEV 问题的认知和看法来进行划分:
1 、进攻性--MEV 不可避免,我们应该找到一种替代方法来进行更民主化的价值提取。
2 、防御性--MEV 是一种存在的威胁,我们应该防止它。
这些解决方案可能的发生地:
1 、P 2 P 层
2 、应用层
理论上,所有的 MEV 保护方案都是在链上建立的,但有些只是通过指定的前端在应用程序级别上使用。将这些面向用户的平台称为应用层,通过这个视角来寻找 MEV 解决方案的空间,我创建了 MEV 保护的四个象限。
这四个类别是。
1 ) 进攻性链上保护
2 ) 进攻性应用层
3 ) 防御性链上保护
4 ) 防御性应用层

在这篇文章中,我将介绍了每个象限阵营的不同参与者,以及他们是如何解决 MEV 困境的,我也提出了一些我对行业发展的想法。因为整个行业在极速发展,一些方案无法全面囊括,如果有需求,我将发表后续文章,概述我没有介绍到的解决方案。
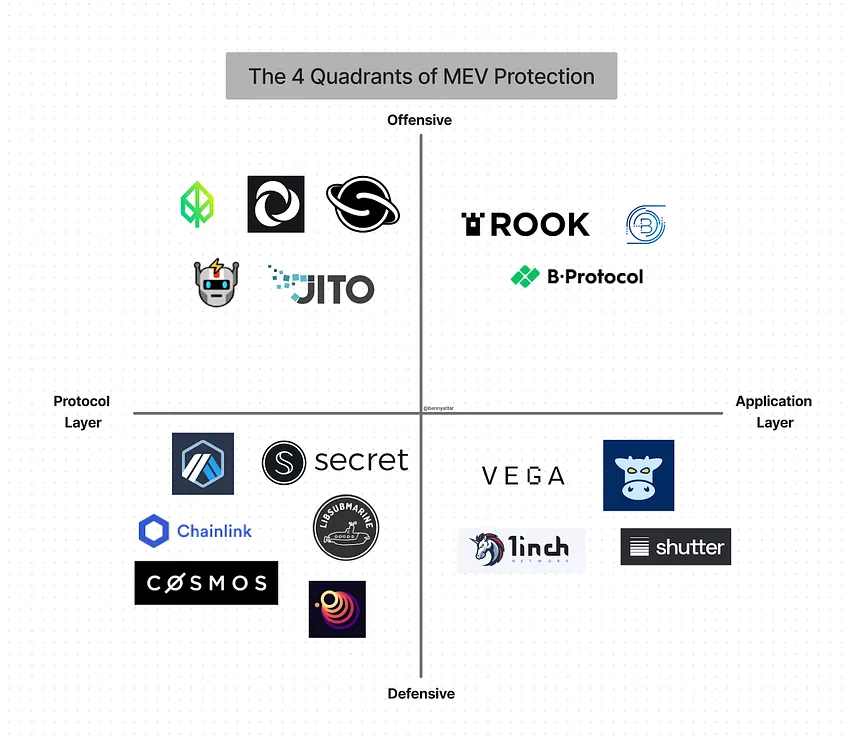
MEV 的四象限防护应用图
进攻性链上保护
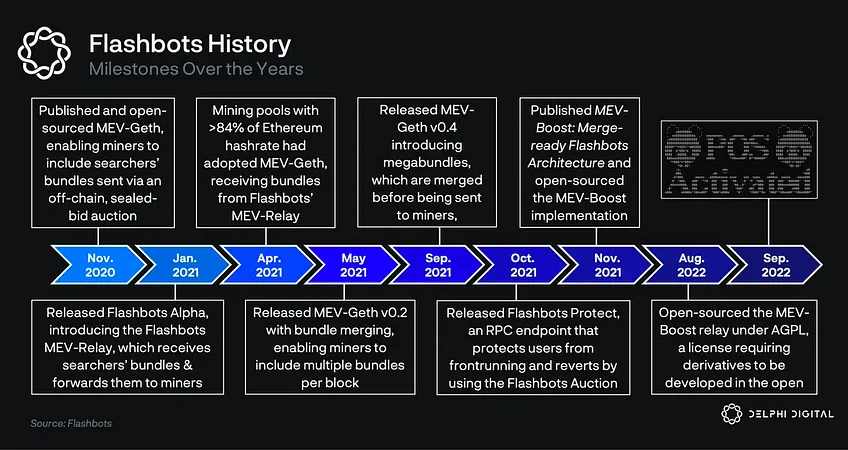
Flashbots
Flashbots 是一家致力于减轻 MEV 负面影响的研发组织。通过一系列的产品研究,Flashbots 成为民主化和重新分配 MEV 收入的领先组织之一,同时也为生态系统带来更多透明度,要了解 Flashbots 的生态系统,我们首先从 Flashbots 拍卖开始讲起。
Flashbots 拍卖
Flashbots 拍卖是以太坊用户和验证者之间的私人通信渠道,用于有效沟通区块内的首选交易顺序。Flashbots 拍卖最初是作为 go-ethereum 客户端之上的一个补丁与 POW 以太坊上的 mev-relay(交易包中继器)相结合而推出的,在现在 PoS 以太坊上,Flashbots 拍卖则是建立在 MEV-Boost 上的(稍后会详细介绍)。
Flashbots 拍卖跳过了传统的公开竞价拍卖,后者往往会造成不必要的网络拥塞,并给投标人增加额外成本。Flashbots 拍卖允许用户私下交流他们的出价和交易订单偏好,而无需为失败交易出价付费,同时最大化验证者的奖励并防止抢跑交易,私人交易池与密封投标的结合确保了以太坊网络的公平和最佳区块的构建。
MEV-Boost
考虑到以太坊与权益证明的合并,Flashbots 拍卖转向了mev-boost ,这是 PoS 以太坊提议者 (proposer) 与构建者 (block builder) 分离 (PBS) 的实现。MEV-Boost 让验证者将区块构建外包给竞争激烈的区块构建者市场,并通过称为中继(relays)的服务接受最有利可图的区块构建,从而最大限度地减少 MEV 的负面影响。MEV-Boost 增强了以太坊的安全性和去中心化,无论验证者规模如何,都能使验证者获得支持 PBS 的 MEV 奖励,而让 MEV 不只有少数人的游戏。
交易通常以两种方式上传到区块链:公共内存池或通过私人 RPC(也称为单一订单流)。无论哪一种,MEV-Boost 交易流程都是相似的。发送到公共内存池的交易由「搜索者」排序打包,这些捆绑包通常以提取最多 MEV 的方式排序,然后,搜索者将他们的捆绑包发送给区块构建者,他们以最大化 MEV 利润的方式收集捆绑包,同时在区块上构建它们。最终,他们通过中继发送区块(内置了一组捆绑包),中继聚合来自多个构建者的区块并按奖励顺序对它们进行排名,此外还对它们进行过滤审查,最后,验证者选择从 MEV-boost 收到的最有利可图的块并将其添加到以太坊网络。
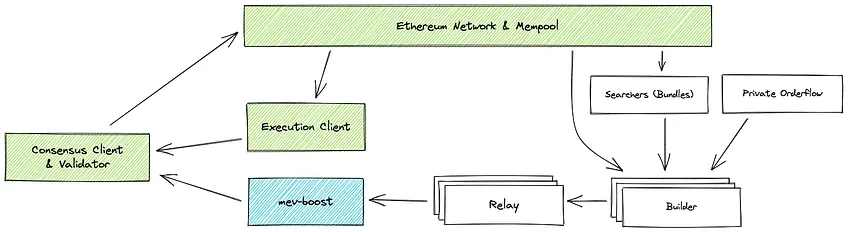
来源:Flashbots Github
MEV-Boost 的四个主要参与者
1 ) 搜索者是机器人、资深以太坊用户、交易员或任何积极搜索内存池以寻找套利机会的人,这些机会可以找到有利可图的交易并试图将他们的交易包含在一个区块中,搜索者收集交易,将它们添加到捆绑包中,然后将它们发送给区块构建者。
2 ) 区块构建者是一个专门的实体,它们连接到搜索者并获取捆绑包(由交易组成),创建最终的区块通过中继器发送给验证者。
3 ) 中继器从多个区块构建者那里收集区块,并选择最有利可图的区块(由构建者的出价决定)发送给验证者进行提案。中继器在审查制度中起着至关重要的作用,因为它们能够挑选要包含的块(稍后会详细介绍)。
4 ) 验证者使用 MEV-Boost 订阅一个或多个中继,找到其订阅的中继器接收到的最有利可图的区块,并进行的最终验证并和上链。
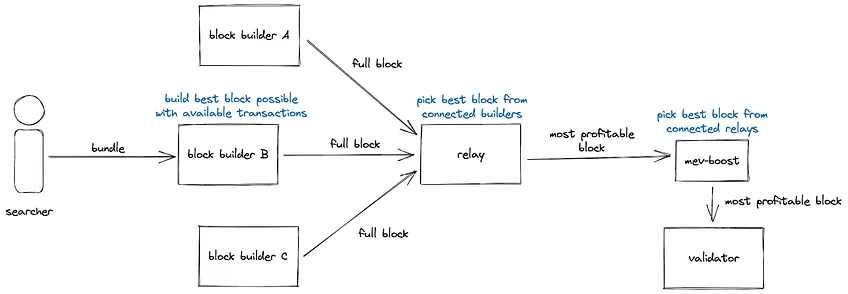
MEV-Boost 运行过程
由于以太坊尚未将 PBS 完全添加到其协议中,因此 MEV-Boost 目前是区块生产和 MEV 最小化生态系统的附属工具。伴随以太坊的升级,MEV-Boost 最终将通过 Proposer Builder Separation (PBS) 直接纳入以太坊基础层,并在基础层完全构建者和提议者角色的分离,如下图所说,目前绝大多数 MEV-Boosted 区块都是通过 Flashbots 实现的:
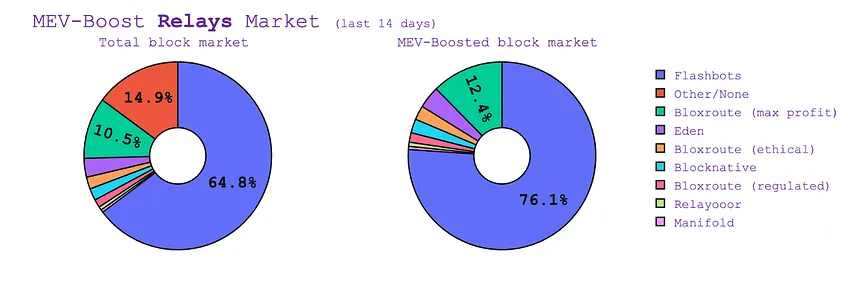
MEV-Boost 中继器市场占比
然而,最令人印象深刻的是 MEV-Boost 的全部功能完全基于信任运行。
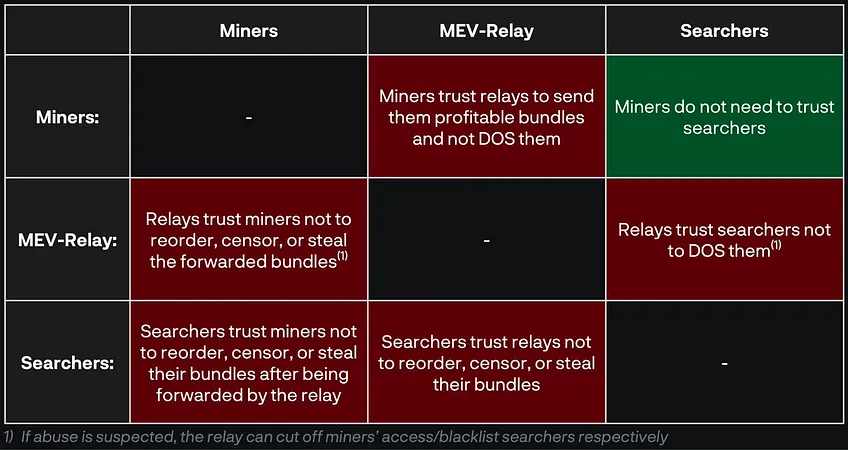
Flashbots 的防护
除了 Flashbot 在验证器级别的 MEV 保护之外,Flashbots 还为任何区块链用户提供了多种产品来保护自己免受 MEV 的侵害。Flashbots Protect 是 Fl ashbot 为用户和开发者提供的领先保护工具。Flashbots Protect RPC 允许普通用户通过在他们的钱包中使用自定义 RPC 端点轻松地将他们的交易提交给 Flashbots 拍卖。对于用户来说,一切都是一样的,除了交易被发送到 Flashbots 构建器而不是公共内存池。因此,这些交易是完全私密的,不会被潜伏在内存池中的套利机器人看到。
审查问题、缺点和后续发展
尽管 Flashbots 取得了令人难以置信的进步,但他们的解决方案仍然存在一些问题,这些问题是当前的技术模式下所面临的,例如,如果整个网络连接到同一个中继并且该中继器是出价最高的,它自然会被验证者选择,但是,如果该中继器扣留这个区块怎么办?那最终将会创建一个无休止的空槽然后发布到链上,这种担忧被称为有效性问题(liveness issues)。幸运的是,Flashbots 概述了两种可能的解决方案,一旦 PBS 被纳入以太坊本身,这个问题就会自行消失。不仅如此,如果 MEV-boost 没有中继器运行或所有中继器都离线,那么信标节点将回退到公共内存池构建区块。
Flashbots 的另一个问题是它们的中心化问题。由于它是一个以以太坊利益最大化的私人组织,因此在以太坊社区想要什么和不想要什么之间总是有一条界线。最近,Flashbots 宣布将根据美国财政部的制裁,开始审查被美国财政部外国资产控制办公室 (OFAC) 列入黑名单的交易(即所有 Tornado Cash 交易,这引起了公众的强烈反对), 并提出了几个与区块链相关的哲学问题。无论如何,MEV-Boosted 区块上的绝大多数交易都符合 OFAC 标准,而且它肯定也会朝着这个方向发展。
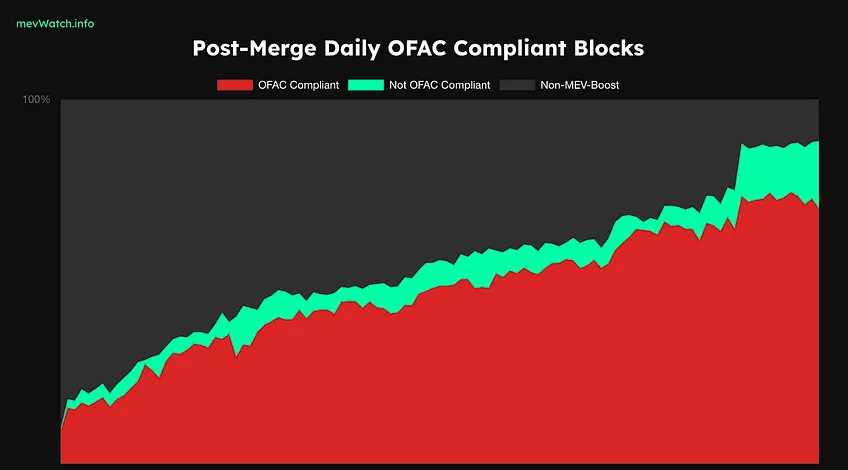
截图自MEV Watch 2022 年 11 月 8 日
最近,Flashbots 宣布了他们致力开发软件的下一个迭代版本——「SUAVE」。从早期预告来看,SUAVE 似乎将是一个 MEV 感知的加密内存池,供用户和钱包使用,他们计划朝着完全去中心化、开源、兼容 EVM 的方向发展,并支持 rollup 和跨链,我对此感到非常兴奋,希望这会成为改变 MEV 的新范式。
3.2 Manifold Finance
与 Flashbots 一样,Manifold Finance 建立了自己技术基础设施,以尽量减少 MEV 的负面影响。Manifold Finance 的基础是他们的 Secure RPC 系统,该系统允许用户提交安全和私人交易。通过向 Manifold 的 SecureRPC 或 Flashbots 这样的 RPC 终端发送订单,用户的交易是通过一个中介发送的,这可以保护用户免受公共池中搜索者套利者影响。
在他们的 SecureRPC 之上,Manifold 提供了几个产品。OpenMEV(以前称为 YCabal),这是一个 SDK,使协议和应用程序能够防止 MEV 的套利,事实上,Manifold Finance 已经有了一些大牌的合作伙伴,比如:Sushi Guard,它是 Sushi 的 OpenMEV 实现。每当你在 SushiSwap 上提交交易时,如果你的交易符合获得其交易成本退款的条件,你将获得~ 90% 的回扣。然而,如果你的交易不符合条件,它将立即通过一个私有的 RPC 层提交。虽然你不会得到交易回扣,但你仍然从受保护的交易提交中受益。Manifold Finance 还运行他们自己的 MEV 中继器(类似于 Flashbots),它是抗审查的(与 Flashbots 不同)。你可以在下图看到围绕 SecureRPC 的整个生态系统。
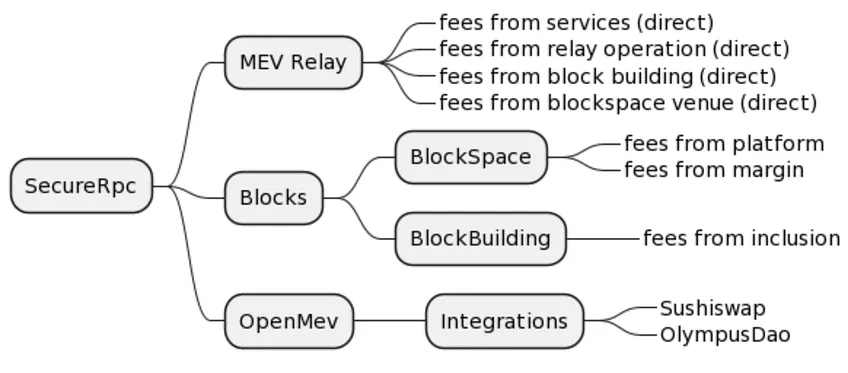
来源:Manifold Finance Docs
Manifold Finance 生态系统围绕着他们的 FOLD 代币。然后重新分配 OpenMEV 捕获的所有 MEV : 50% 给到用户、 25% 给验证者和 25% 给 xFOLD 质押者。预计他们将很快宣布其质押产品的 V 2 版本,这是社区所期待的。然而,尽管令人印象深刻,但 Manifold Finance 的文档并不完整,因此无法挖掘出他完整的产品技术细节。此外,通过他们的质押组织、公司和创始人在社交媒体上展示,以及他们的代币经济学模型等方面,我也存在一些担忧,这些担忧是否证明不审查交易是有道理的,尤其是当这个问题非常小的时候,这是一个有待讨论的问题。总的来看,Manifold Finance 有机会来控制 MEV 生态系统,但前提是他们能正确的行动。
3.3 BloxRoute
在 Flashbots 之后,BloxRoute 正在成为第二大中继器提供商。他们目前运行三种不同的中继器:BloXroute Max Profit、BloXroute Ethical 和 BloXroute Regulated。以下是它们的规格:

来源:BloxRoute 官方文档
关于目前中继器是否需要对制裁交易负责问题的讨论时,BloXroute Labs 的首席执行官 Uri Klarman 曾告诉 CoinDesk,BloXroute 认为决定验证器是否应该或不应该包括受制裁的交易不是我们考虑的问题,选择推出一个中继器,会根据用户的判断和具体法律对 Tornado 进行审查。
除了 BloxRoute 的中继器产品,他们还有一个名为 BackRunMe 的攻击性应用产品,它允许用户安全地提交私人交易,同时允许搜索者通过 MEV 跟随交易以产生额外的套利利润。私人交易功能使你的交易对在抢先交易和三明治机器人的公共池中隐藏起来。此外,如果有跟随交易可用,则 BackRunMe 会将此额外利润的一部分返还给用户。这些后台交易不会影响用户所提交的交易,因为它发生在交易确认之后,所以对所有人来说都是双赢的。目前,BackRunMe 可以在 SushiSwap 和 Uniswap V 2 上使用。
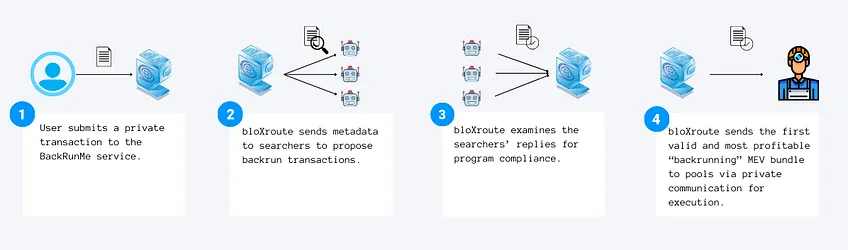
BackRunMe 的工作原理
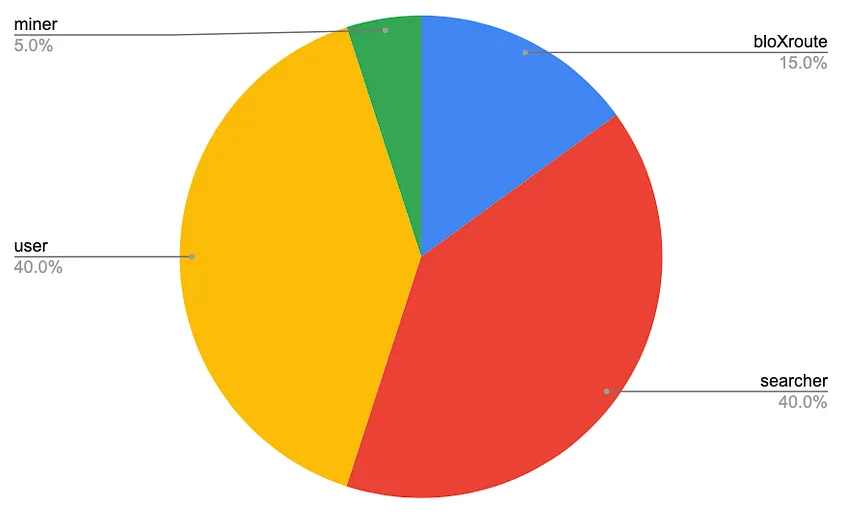
分润比例 Backrunning
BloxRoute 还提供了一种的防护性产品,称为Fast Protect ,可用于以太坊上的所有 Dapps,尽管它对初学者来说不是那么友好,但 BloxRoute 也是 MEV 保护领域的领导者之一。
3.4 Eden Network
Eden Network 是 MEV 的第四个进攻性链上解决方案。与上述三者类似,Eden 有三种相关但不同的 MEV 保护产品:RPC、中继器和捆绑包(bundles)。Eden RPC 是一个 RPC 端点,用户可以将其添加到他们的钱包中,将他们的交易发送给 Eden 构建者。Eden RPC 为 Eden 中继器提供支持,Eden 中继器将验证器连接到区块构建者网络,以最大限度地提高验证器的效率。这样,可以保证用户不会在 Eden 区块中处于领先地位。最后,通过 Eden 的 RPC,搜索者可以将「捆绑包」发送到 Eden 的区块构建者网络。在所有 MEV-Boosted 块中,Eden 做得很好(接近 Flashbots)。
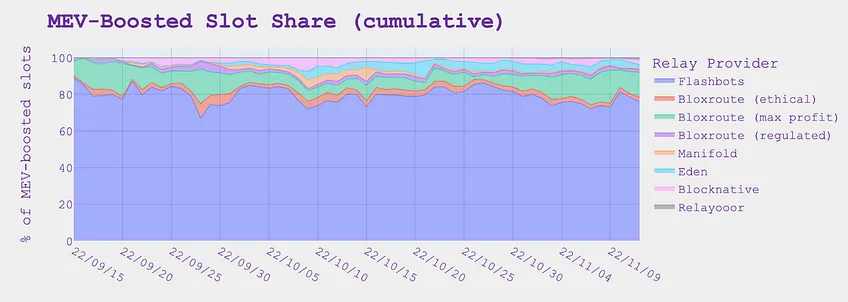
MEV-Boosted slot 占比 来源:MEVBoost.Pics
另一个值得一提的中继提供商是 Blocknative。他们的中继器称为 Dreamboat,是公开可用的、透明的,但会过滤受制裁的地址。交易审查问题是一个有待讨论的问题,区块链社区最近对此讨论很多。无论你站在哪一边,都会存在一定的争议,Flashbot 和整个 MEV-boost 生态系统为区块链和 MEV 做了很多工作,我很期待 MEV 领域的下一步发展。

MEV-Boost 的争议
除了 MEV-boost 产品外,还有几个值得一提知名项目正在构建关于链上攻击防护的产品。
3.5 Skip Protocol
Skip Protocol 正在 Cosmos 上构建与其生态系统匹配的 MEV 产品,放大 MEV 有效性,并最大限度地减少不良 MEV 的影响,并将这些 MEV 所产生奖励重新分配给验证者和质押者。Skip 在 Cosmos 链上发现了以下问题,因为这是先到先得的内存池:
1 ) 执行风险:在链高度拥堵的时期,没有办法表示某些交易对交易者或生态系统「更重要」或更有经济价值,这在 5 月 9 月的 Terra 崩盘期间广泛发生。
2 ) 浪费的区块空间和 GAS:你会发现大量套利机会背后会出现包含多个失败交易的区块(例如,Terra Classic 区块 5635240 )。
3 ) 利润集中:几乎所有套利机会都被极少数地址获取,这些地址可能由几个高频交易组织控制,这相当于对 Cosmos 用户和验证者征收隐性税。
4 ) 参与者整合:MEV 搜索者和验证者通过激励进行垂直整合,让他们的机器人和节点位于同一台服务器上,以更快实现内存池访问和交易广播。(例如,我们已经看到 MEV 搜索者和验证者之间在优先访问方面的伙伴关系取得进展),这破坏了长期的权力下放。
5 ) 链停止风险:大量的垃圾邮件可能会破坏完整节点或验证器(当它们暴露端口时)。
因此,Skip 提出的解决方案是创建一个密封投标、封闭式拍卖的系统,允许交易者向验证者提交小费交易,验证者根据区块的情况在区块中优先处理。
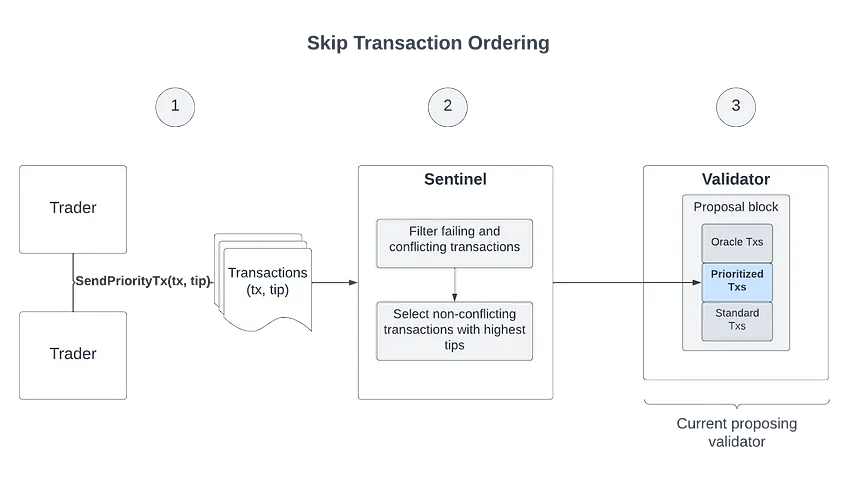
Skip Protocol 的交易排序
通过这样做,验证者可以在每笔交易中获得更多奖励,并且随着 MEV 奖励分配给质押者,质押利润将增加,这是一种双赢。
最近,Skip 宣布了他们的 Skip-Select 产品,允许验证者完全决定他们如何构建他们的区块。验证者可以选择 MEV 奖励的分配方式、选择 Skip 是否构建他们的区块、选择合规性、选择治理以及各种其他各种 MEV 偏好。这是他们Sovereign MEV愿景的一部分,即允许应用链的利益相关者、验证者和核心开发人员决定他们的 MEV 市场如何运作。为此,他们正在开发 MEV-SDK,它将这些偏好和区块构建者权利带入链上。在撰写本文时,Skip 在 Juno 的测试网和主网上很活跃,并将很快在 Evmos、Terra 2 和其他 Cosmos 链上启动。此外,他们一直在谈判与 Osmosis 进行各种合作。您可以在此处的仪表板上跟踪有多少验证器正在积极运行 Skip。
3.6 Jito Labs
与之前提到的以太坊和 Cosmos 生态系统中的项目不同,Jito Labs 的使命是通过高性能 MEV 基础设施扩展 Solana。鉴于他们属于攻击性 MEV 类别,他们试图将 MEV 的负面影响降至最低,同时将好的 MEV 影响最大化,并将收益重新分配给用户。通过协同工作的三种不同产品,Jito 在最小化 Solana 上的 MEV 方面处于领先地位。
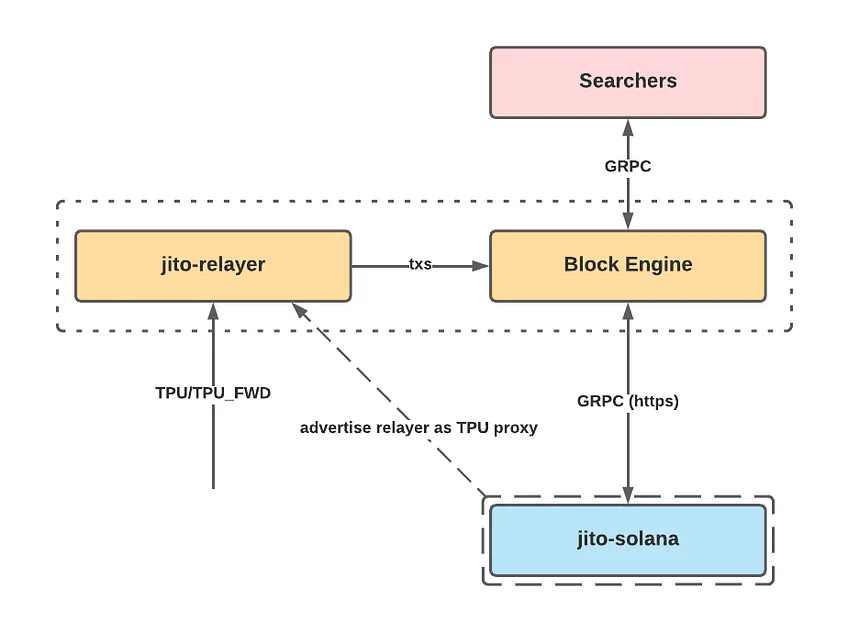
首先,验证者运行 Jito-Solana,这是一个经过修改的 Solana Labs 验证者客户端,允许验证者创建「捆绑」交易,让搜索者和高频交易者可以灵活地进行交易顺序。开源 Jito-Solana 验证器是网络的核心,管理与 Jito-Relay 的通信,它对正在处理的交易进行过滤和签名验证。出价最高和利润最高的捆绑包从中继器发送到验证器,以最终添加到链中。此外,Jito 提供了一个区块引擎,它通过链下密封投标拍卖将中继器、搜索器和验证器连接起来,以便将交易添加到链上。区块引擎模拟每个交易组合,并将支付最高的一批交易包转发给领先的验证者以便快速执行。在拍卖到期时,最有利可图的捆绑包被发送给领先者,巧妙的是,这个区块引擎是全球分布的,以确保验证者和搜索者无论身在何处都能获得低延迟访问。
验证者的 MEV 利润会在每个纪元结束时被重新分配,这是 Jito 制作的一个很酷的电子表格,用于计算 MEV 前后的验证者利润。
最终,攻击性链上阵营在 MEV 保护份额方面取得了令人难以置信的进步。我希望继续看到他们创新,因为验证器是每个网络的基础。现在,我们将分析进攻性应用程序 MEV 下的生态系统。
进攻性应用层
进攻性应用程序认为 MEV 是不可避免,因此他们提供应用程序和面向用户的解决方案来提取 MEV 的价值,并使之尽可能的民主化。我们已经在上面讨论了 BackRunMe(因为它是 BloxRoute 产品的一部分),所以我们将深入探讨这个阵营中的另外两个主要参与者。
4.1 Rook Protocol
Rook Protocol 是首批 MEV 提取解决方案之一,旨在在应用层捕获 MEV,保护用户和协议免受负面的外部影响,并减少共识层可用的总 MEV。最终,Rook 以提高整体网络和市场效率的方式在参与者之间重新分配 MEV 利润。
Rook 协议依赖 ROOK 来运行,ROOK 是一种 ERC-20 治理和实用令牌,用于在处理交易时发现 MEV 在交易中的价值。使用 Rook 协议的每个人——用户、智能合约、做市商、keepers 等,都通过 ROOK 代币与生态系统连接起来。Keepers 是自动机器人,可以完成用户的交易,将 ROOK 抵押到智能合约中并接收 xROOK 作为回报。Keepers 不断观察交易内存池以寻找套利机会,一旦发现有利可图的交易,Keepers 就会使用他们的 xROOK 进行竞价,以获得执行交易的机会,协调拍卖人模块会为赢得拍卖的 Keeper 开绿灯,他们履行交易,同时分配 Keeper 为该机会支付的成本。同时,ROOK 代币持有者可以将他们的 ROOK 放入 Rook 质押池中,以换取 xROOK,每次出价中捕获的价值的一部分直接流向 xROOK 持有者,使他们获得直接对应于 Rook 协议的效用和 MEV 收益。
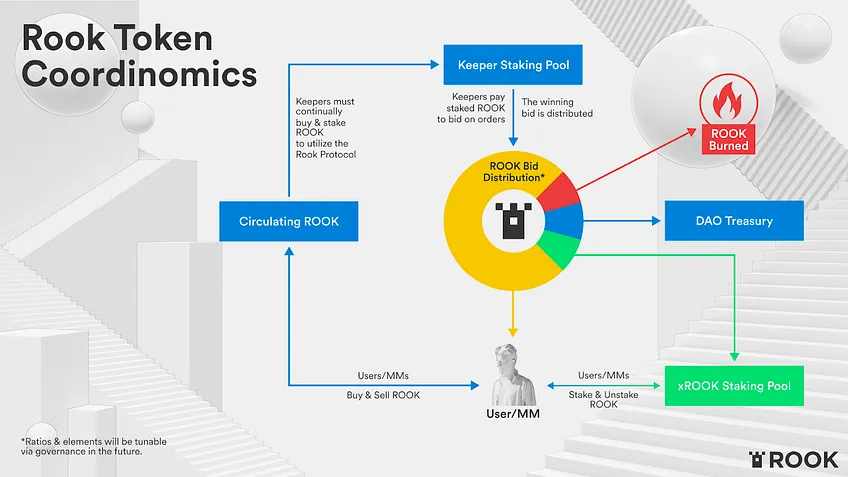
链下订单簿是用 Rook 的「隐藏订单簿」构建的,托管只能由 Rook Keepers 才能完成的交易。通过隐藏簿发送的订单对于其他掠夺性 MEV 机器人来说是无法访问的,因此允许用户以他们的目标价格接收他们的交易。Rook 的隐藏订单簿甚至可以通过他们自己的 DEX、游戏、API 或通过他们的合作伙伴来集成使用。
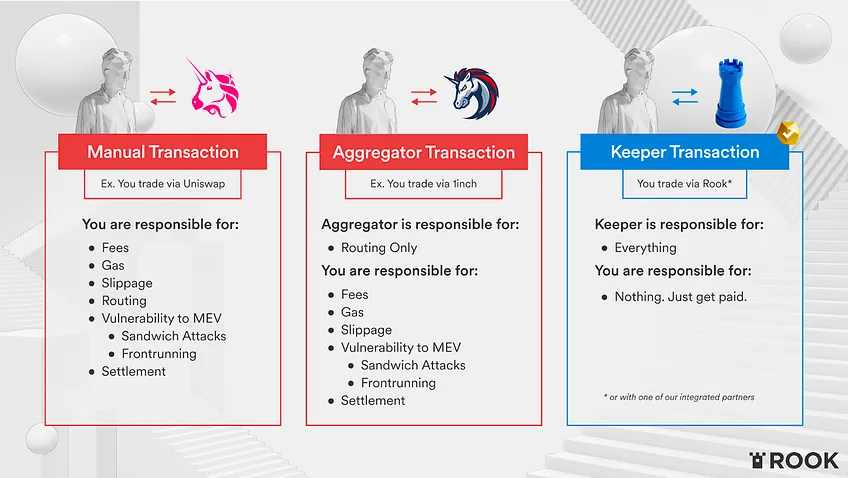
4.2 B.Protocol
B.Protocol 是另一种进攻性的应用级 MEV 解决方案。不过,它主要侧重于贷款和清算领域(与提到的其他解决方案相反,这中方案偏向于 DEX、抢先交易和三明治攻击等方向)。B.Protocol 以民主化清算,确保更高的资本效率,并对抗 MEV。
在 B.Protocol 集成的平台上,它将用户的资金集中到一个用于清算的 Backstop 池中。当资金闲置时,它们停留在收益平台中并为用户产生被动收入(利率或流动性挖矿奖励)。一旦发生清算,智能合约就会从支持中提取所需资金以促进清算,并自动出售扣押的抵押品。一旦售出,收益将存入池中,产生利润。这个视频对它具体的工作流程做了很好的概述。
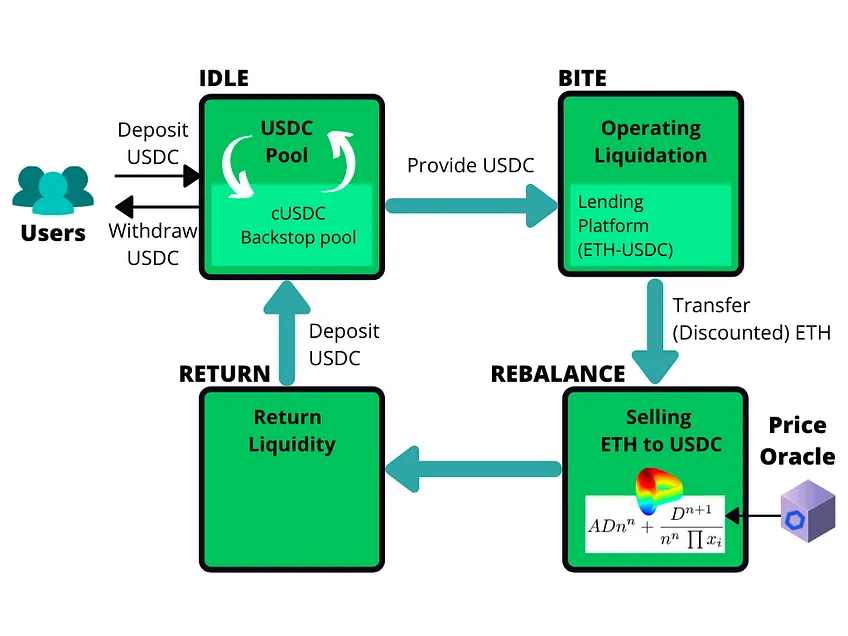
通过创建任何人都可参与的民主池,B.Protocol 与存入抵押品的用户分享 MEV 利润,并给予他们清算优先权。B.Protocol 目前在几个头部项目上上线,包括 Liquity 的 Chicken Bonds。B.Protocol 的与众不同之处在于,它是 MEV 保护领域中专注于清算领域的唯一玩家,属于很小众的进攻性应用层类别。
目前,MEV 进攻性应用层方面的参与者数量相对较少,但每个项目都有自己的特点,我对这个阵营的未来会越来越乐观。
防御性链上保护
如前所述,这些解决方案认为 MEV 是对区块链的生存威胁,因此它们通过链上和共识层来完全消除它。
5.1 Chainlink 公平排序服务
这一领域的主要参与者是去中心化预言机网络 Chainlink,他们将智能合约与链下数据安全地连接起来。这可以用于金融市场、体育数据,甚至天气和碳信用等各个领域。Chainlink 现在更进一步,通过引入 (FSS) 对其智能合约附加组件实施 MEV 保护。简而言之,FSS 是一个预言机网络,可以对发送到该智能合约的交易进行排序,它在链下收集用户交易,根据智能合约开发者的规范生成订单,并以去中心化的方式将交易提交到链上。
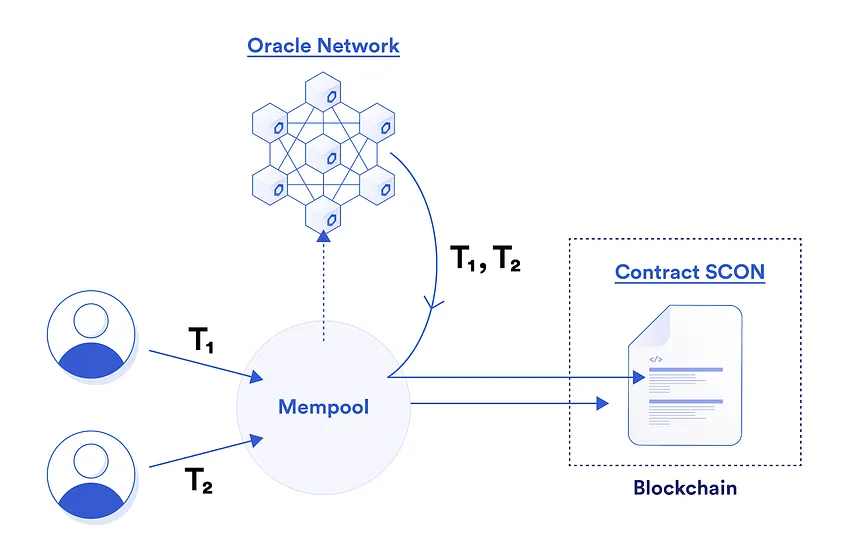
公平排序服务流程模型
此外,FSS 不仅可以用于预处理阶段的智能合约,还可以用于区块构建和 rollup 阶段。目前,FSS 已又有一个功能齐全的原型,并且有一个 Arbitrum 的试点项目。整个区块链和 MEV 社区都期待 FSS 在未来几个月内全面推出。
5.2 Secret Network
Secret Network 是建立在 Cosmos IBC 上的 L 1 区块链,具有保护隐私的智能合约。Secret 的智能合约,被称为「Secret Contracts」,默认情况下是私有的。一切都会被加密(输入、输出、状态等),其他人无法查看,除非他们被授予访问权限。这打开了在传统公共区块链上难以实现的用例。建立在这些「Secret Contracts」之上的「隐私 DeFi」,可以在去中心化金融生态系统保护隐私的,与传统 DeFi 应用程序一样,用户可以交易、交换、购买、借贷、出售,但在它的系统中用户的这些数据默认是私有的。由于这种固有的隐私性,订单在内存池中是不可见的。因此,可以免受 MEV 抢先和三明治机器人的攻击。Secret Network 是少数将隐私权作为权利的协议之一。
5.3 Comos 2.0
最近,Cosmos 宣布了他们的 2.0 版协议,其中他们提出的对抗 MEV 的解决方案——Interchain Scheduler。意想不到的是,ATOM 2.0 提案被 ATOM 社区否决了,虽然如此,依然有必要对 Interchain Scheduler 进行一些详细的说明。
由于 Cosmos 生态系统由多条链组成,因此网络中分散的 DEX 资产价格存在差异。除了创造明显的 DEX 套利机会外,它还引入了更复杂的抢先交易和三明治攻击。Interchain Scheduler 提议在链上创建一个 MEV 市场,帮助 Cosmos 的应用链将其区块空间的一部分作为可交易 NFT 出售。通过调度程序,他们将通过拍卖的方式,在参与的区块链上保留区块空间,然后,这笔拍卖所得将在整个生态系统(质押者、验证者等)中重新分配。
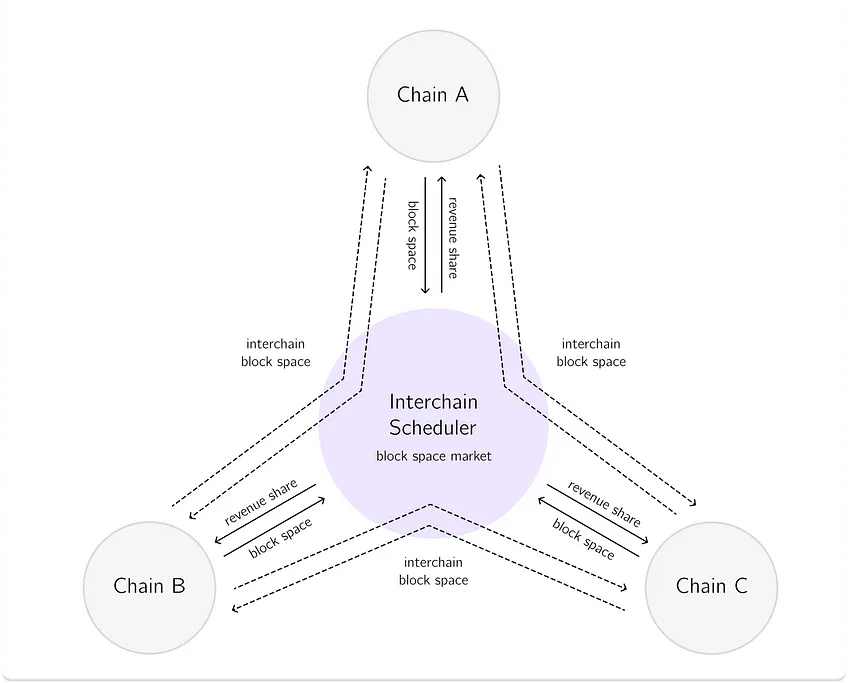
跨链调度过程
技术上比较复杂,细节可以在这里找到。
5.4 其他防御性链上工具和解决方案
除了上述产品外,还有多种其他防御性链上解决方案用于 MEV 保护。
Submarine Sends:
这是一个开源智能合约库,它通过暂时隐藏链上交易来保护您的合约免受领跑者的侵害。简而言之,用户将他的交易提交到潜藏地址,以隐藏的方式把数据提交给智能合约并锁定,一旦提交的交易保持在链上,智能合约就会解锁存储的数据并对其进行验证。
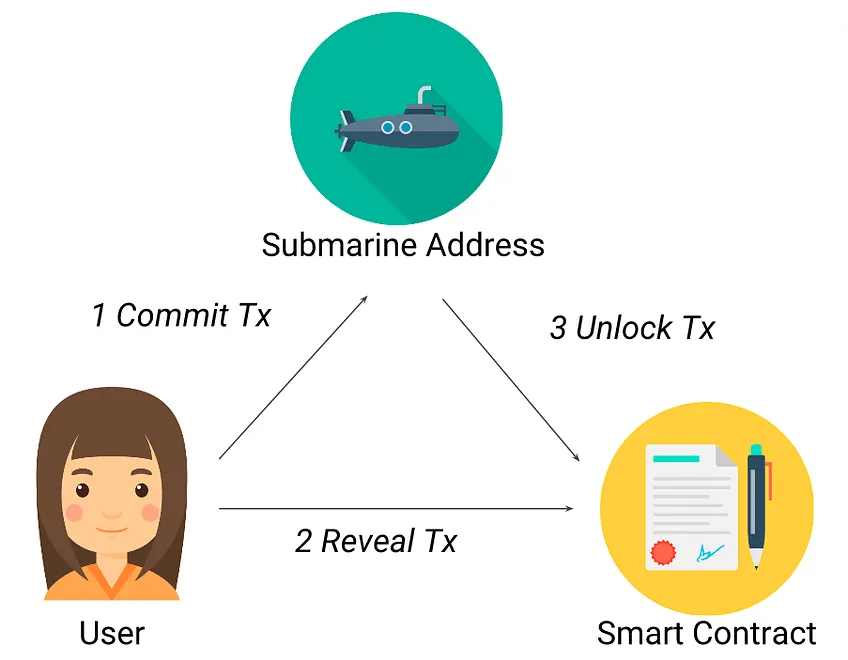
Submarine Sends 交易模型
Submarine Sends 的所有代码都在 Github 上公开可用,但它已经几年没有更新了。
ZeroMEV
ZeroMEV 是一种完全去中心化的解决方案,适用于以太坊验证器,以保护其用户免受抢先交易和审查。使用 MEV-Boost 时,用户有时会出现领先几毫秒的情况,为了防止这种情况,ZeroMEV 通过按时间而不是 gas 价格 对 MEV 交易进行排序,以保护他们的用户。事实上,ZeroMEV 保护用户的时间最多相差 500 毫秒,要使用 ZeroMEV,只需更改原始 Geth 中的三行代码。然而,目前使用 ZeroMEV 纯粹是出于利他目的,因为验证者可能会赚得更少,因为他们只在 EIP-1559 之后获得小费。不过,验证者可以退回交易,从而创造更多的利润,无论如何,ZeroMEV 依旧是一个令人难以置信的验证者 MEV 保护工具。
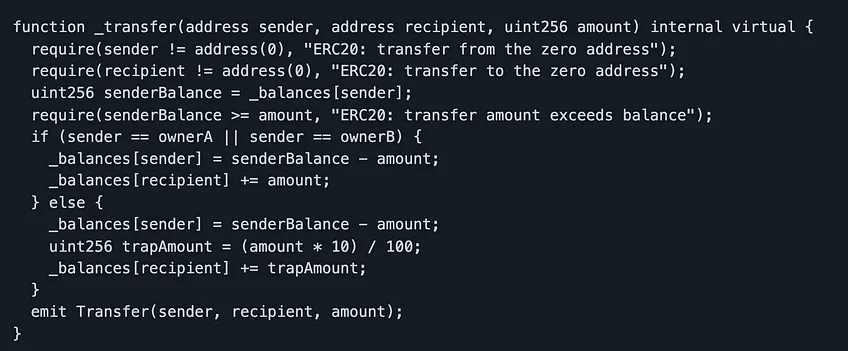
Salmonella Attack
为了欺骗三明治交易机器人,Defi-Cartel 引入了一种非常巧妙的技术来将权力还给交易者。Salmonella 的想法如下:创建一个典型的 ERC-20 代币,每当除指定所有者之外的其他人与它进行交易时,它只返回指定金额的 10% ——尽管发布的事件日志显示了完整的交易。在这里看到的它在全盛时期有过几项重大的功绩。
Kattana
和上一个类似,这是另一个愚弄机器人的应用,Kattana 是 DEX 与 CEX 的跨链交易的终端。在他们的代币发布期间,他们为抢先运行的机器人设置了一个陷阱,阻止他们出售他们的代币,有时,捕食者会变成猎物。
归根结底,防御性链上保护阵营相当先进、技术性强、隐秘,有时甚至还很幽默。当然,在 Chainlink 的 FSS 推出后,这个阵营将在整个行业掀起更大的波澜。
防御性应用
最后,我们来讨论的最后一个阵营——防御性应用领域。这些解决方案认为 MEV 是对区块链的生存威胁,因此他们提供应用程序和面向用户的解决方案以完全消除它。其中许多是区块链新手用户已经熟悉的产品,但深入了解其 MEV 保护功能非常重要。为了最好地解释它们,可以将它们分为几类。
6.1 自动做市商(AMM)
讨论防御性应用阵营,就不得不从自动化做市商说起。有关 AMM 的概要,请阅读我之前写的
MEV 捕获 AMM (McAMM)
最近有很多关于MEV 捕获 AMM 的讨论。简而言之,这个想法如下:AMM 有拍卖每个区块的第一笔交易的权利,从而出售一个潜在的 MEV 插槽,并将这些利润重新分配给交易者、质押者,甚至潜在的搜索者,这个提案非常有趣。
流动性集中
2021 年 3 月,Uniswap 宣布了他们 V 3 版本。其中,他们为 DeFi 和 AMM 引入了全新的范例:集中流动性。简而言之,集中的流动性使 LP 能够精细控制其资本分配的价格范围,从而实现更高的资本效率的同时,也能降低滑点,同时还可以防止任何资产自由落体的情况。由于它对每笔交易的价格影响较小,因此它对 MEV 的影响当然也较小。此外,在集中的流动性池上有一种令人着迷的 JIT 流动性 MEV 技术,它实际上有利于交易者。虽然集中的流动性并不能完全消除 MEV,但它肯定会将其最小化。
还有多种其他抗 MEV 的 AMM,比如:Hashflow 、Duality 、SwapSwap 和 Wendy(Vega Protocol 的一个关键特性)。这个 MEV 保护领域因创新而蓬勃发展,我非常期待这里的下一阶段的发展。
6.2 DEX 聚合器
对于那些不熟悉 DEX 聚合器的人,简单的理解就是:他们将数百个 DApps 连接在一起,并通过这些不同的流动性池提供最佳兑换比例。
1 inch
这是最著名和使用最广泛的 DEX 聚合器。最近,他们与 Flashbots 合作,以保护他们的用户免受抢先交易和三明治攻击。现在通过 1 inch 用户可以选择通过 Flashbots 路由他们的交易,这实现了验证器和 1 inch 之间的直接连接。但是,我不确定它是否已更新或者它在合并后是否仍然有效。 1 inch 提供的另一个领先保护工具是「自动滑点」,它能最大限度地减少机器人以交易为目标的可能性,因为它具有较低的滑点容忍度,因此操纵用户所需返回金额的空间较小。
CowSwap
你可以将它理解为聚合了 DEX 聚合器的聚合器。CowSwap 上的交易可以通过链上的自动做市商、其他 DEX 聚合器等进行结算,CoW 是点对点匹配的,因此每个人都可以获得更好的价格,并且没有人支付不必要的 AMM 费用,因为它搜索了所有其他流动性的潜在的最佳交易价格。交易中心,CoW 将这些交易分批提交给上链,将它们隐藏在公共的内存池中,并有效地防止矿工的交易重排和三明治机器人,CoW Protocol 在这方面肯定是独一无二的。
其他一些防御应用层 MEV 保护解决方案比如 MistX Labs 、DFlow 和 Shutter Network。这个领域其实竞争很多,但每个玩家都在减少 MEV 和保护用户方面做出了重要贡献。我的一个预测是,在未来,不保护用户免受 MEV 影响的 DApp 将不会受到用户青睐,MEV 保护将会成为行业标准。
MEV 的现状与未来
现在我们已经了解了整个 MEV 解决方案的全景图,更重要的依旧面临的问题,此外还要了解下一次创新将发生在何处。
首先,就像区块链中的大多数其他问题一样,这个问题太复杂了,普通用户理解门槛很高。绝大多数区块链用户往往会以更差的执行率进行交易,虽然每笔交易只损失几美分,在短期内可能不是这样的问题,但如果不了解这些问题,区块链将永远不会向更大的应用领域发展。更进一步,上述所描述的解决方案也非常复杂,需要理解各种不同的参与者,而且,对 MEV 感知并不能推动它的采用,这是一个哲学范畴问题。
其次,正在提供的这些解决方案既不提供所有权,也不提供其网络的权益(ROOK 和 COW 除外),它们纯粹是其它协议的附加组件或就是一个功能,很少有利润被分配。那些有利润分配的解决方案,是以他们自己的代币来分配的,而不是以实施的 DApps 代币本身来分配。
最后,在目前的情况下,许多解决方案都有一些私人订单流或屏蔽交易的事件,有一种说法是,私有订单流有其缺点,它消除了区块链的公共性质,并可能导致中心化。我觉得现实情况是,两方面总是要有取舍的。
尽管有这些担忧,在 MEV 保护领域发生的这些创新足够让人惊讶。这篇文章的篇幅就凸显了这个问题有多么重要,可以看到内存池的发展将会是 2023 年的重要主题之一,尤其是在熊市的低谷期,基础架构是主要创新阵地。
此外,有一些预测说,主要的 DEX 在未来会成为区块构建者,并在这个空间创造一个有趣的动态。在 Tornado Cash 失败之后,人们对保护隐私链和应用的兴趣不断上升,这也引起了一些人的注意,特别是 MEV 可以通过这些平台(如 Silent Protocol、Nucleo 和 Aztec Network)缓解隐私方面的忧虑。
由于最近几周 FTX 的影响,我相信这将更加增强对 MEV 的关注,因为越来越多的交易将会从 DEX 流向链上。最后,MEV 是对区块链的生存威胁还是可解决的挑战,这个问题最终掌握在我们的手中,我经常思考的一个问题是,我们是否需要学习如何生活、应对或潜在地利用 MEV 获利,还是几年后我们会完全忘记它,但现在,我们应该尽最大努力减少机器人的影响。



