From privacy-preserving payments to privacy-preserving collaboration: How cryptography is reshaping trust and freedom for individuals, businesses, and society.
- 核心观点:隐私支付是区块链大规模应用的关键。
- 关键要素:
- 保护企业薪酬、供应链等商业机密。
- 守护个人消费、资产等财务隐私。
- 实现可审计隐私,满足精准合规。
- 市场影响:推动区块链进入主流商业与个人应用。
- 时效性标注:长期影响。

This article was jointly written by Benfen and TX-SHIELD.

Transparency is the cornerstone of blockchain's trust mechanism, but this publicly recorded nature has become a core obstacle to large-scale application . For the Web3 vision, this is a double-edged sword : it brings verifiable trust, but at the cost of sacrificing trade secrets, personal financial privacy, and compliance flexibility.
For businesses, every on-chain settlement could expose core supplier relationships, procurement costs, and compensation strategies to competitors; for individual users, every on-chain payment permanently records and publicly discloses their consumption habits, asset status, and social relationships; and for regulatory agencies, a new balance needs to be found between "protecting public privacy" and "fulfilling financial compliance responsibilities."
Transparency should not come at the expense of core privacy. TX-SHIELD, a public blockchain , has officially launched its privacy payment function. This marks a shift from an era of "trust for transparency" to a new paradigm of "trust built on privacy." This article will be divided into two parts: Part One will demonstrate how privacy payments address the pressing issues facing businesses, individuals, and regulators; Part Two will unfold a future vision, delving into how, based on the cornerstone of privacy, we can collectively build a complete ecosystem encompassing on-chain Dark Pools, confidential voting, confidential auctions, and even entirely new models of social collaboration.
TX-SHIELD is a technology company that develops privacy-preserving payment algorithms, providing regulatory-friendly and privacy-protecting one-stop solutions for public blockchains, stablecoin issuers, and DEXs. www.tx-shield.com 
Addressing Current Pain Points: Urgent Application Scenarios and In-Depth Analysis of Privacy-Focused Payments
For B2B enterprises: Privacy-preserving payments are a strategic tool for business competition and compliance management.
1. Protecting salary payment privacy: Taking Deel as an example , creating a "strategic tool" for enterprise talent management.
In modern enterprises, especially multinational corporations, the global competition for talent is a core strategic component of compensation systems. However, when companies attempt to adopt transparent blockchain technology for salary payments, they face a serious problem.
Take Deel , a global payroll management platform, as an example. As one of the fastest-growing SaaS companies in history, its core business lies in processing employee payroll payments worldwide. Deel actively embraces blockchain technology, allowing global employees and contractors to instantly withdraw funds using cryptocurrencies such as Bitcoin and USDC through its "Deel Crypto" service, effectively solving the pain points of slowness and high fees in traditional cross-border wire transfers. However, it is precisely this adoption of blockchain payment efficiency that exposes it to a serious challenge of transparency.
For Deel and its tens of thousands of client companies, using a transparent blockchain for payroll would permanently expose every on-chain payment to the public, revealing the client's compensation structure, salary levels across different countries and positions, and even the income information of individual employees. This would not only lead to internal salary disputes and external poaching, but also directly leak Deel's most core business secret—its global payroll database—posing a fundamental threat to the foundation of its multi-billion dollar valuation.
This reality, reflected in real-world business scenarios, has created a clear and urgent need for businesses: global companies like Deel, which have already taken the lead in adopting blockchain payment efficiency, and many companies seeking efficient and transparent payroll management, urgently need a payment solution. This solution must be able to efficiently, accurately, and immutably process global payroll payments using blockchain technology, while also ensuring the absolute confidentiality of payroll data, just like traditional financial systems, to prevent catastrophic data breaches caused by the transparency of payment tools.
Currently, numerous leading Web3 companies and DAOs have successfully validated the feasibility and necessity of privacy-preserving payments in payroll management by adopting privacy technologies such as Zcash or Aztec Network for payroll disbursement. These practices demonstrate that upgrading payroll confidentiality from a "contractual commitment" relying on systems and trust to a "technological guarantee" based on cryptography has become an inevitable direction for the evolution of management in modern enterprises, especially globalized companies.
BenFen Chain ( www.benfen.org )'s privacy payment function, powered by the MPC solution provided by TX-SHIELD, is a solution tailored to meet the needs of such enterprises. We further propose building a complete "enterprise-grade privacy payroll system" where companies can distribute salaries to their global employees via BenFen Chain. The entire process is completed on-chain, ensuring accuracy and auditability while concealing key information such as payment amounts, sender and receiver identities. For enterprises, the system will serve as an "invisible strategic asset," supporting efficient and transparent global payroll management while comprehensively protecting the company's core payroll data and business strategies. For the blockchain ecosystem, this system is expected to be a key step in promoting the large-scale deployment of enterprise-level applications—it precisely addresses the core concerns of companies like Deel in the highly sensitive area of payroll management, clearing key obstacles for blockchain technology to enter mainstream commercial applications.
2. Supply Chain Finance and Settlement: Taking Apple and Foxconn as examples, breaking the dual dilemma of "data silos" and "excessive transparency".
The current predicament of supply chain finance stems from the inefficient transfer of trust among participants. McKinsey's "Global Payments Report" reveals a massive $1 trillion funding gap annually in global supply chain finance. This gap is essentially a classic "trust" problem. Take the partnership between Apple and its core supplier Foxconn as an example: their business data forms typical "data silos." This makes it difficult for Foxconn to prove the legitimacy of its "accounts receivable," representing the true transaction background, to obtain low-cost financing from financial institutions, ultimately leading to the persistent problem of difficult and expensive financing across the entire supply chain. However, simply adopting blockchain in pursuit of data sharing and transparency leads to an even more fatal dilemma: Apple's precise purchase prices to Foxconn, settlement periods, and even the production scale of new products—its most core business secrets—will be completely exposed to all on-chain participants, including competitors. Competitors can use this to accurately calculate Apple's cost structure and product strategy. This new risk introduced by solving an old problem significantly hinders the implementation of blockchain technology in core business scenarios.
Complex supply chains, exemplified by the automotive manufacturing and consumer electronics industries and their vast supplier networks, are seeking an innovative solution that can simultaneously satisfy two seemingly contradictory goals: First, they must automate business processes and ensure the verifiability of key data to meet trust requirements and overcome financing bottlenecks; second, they must ensure that all sensitive business details are absolutely protected during the collaboration process to prevent the leakage of core competitive advantages.
Industry exploration has validated the feasibility of this direction. The Baseline Protocol project (driven by industry giants such as EY, Microsoft, and AMD) is a pioneer in this field. Its core lies in using advanced cryptographic technology to enable enterprise systems to synchronize business process states on a public blockchain while ensuring the confidentiality of all commercially sensitive data. This practice powerfully demonstrates that achieving "competition within collaboration" through technological means is possible—that is, improving the overall efficiency and trust of the supply chain while building a robust data moat for each participant.
The privacy payment function of this blockchain was developed precisely to address this complex challenge. Based on TX-SHIELD's verifiable privacy technology, we can build a trusted settlement layer on the blockchain. At this layer, suppliers can prove the validity and compliance of their accounts receivable to financial institutions without disclosing any sensitive information such as specific amounts, counterparty identities, or contract details. This provides financial institutions with the key trust element needed for their decision-making without revealing any trade secrets. Referring to McKinsey's predictions for digital supply chains, such solutions are expected to significantly optimize supply chain cash flow efficiency, shortening settlement cycles from months to days, and providing a powerful next-generation infrastructure for revitalizing the industrial chain and reducing overall financing costs.
3. Cross-border B2B Payment and Settlement: Taking SHEIN's global supply chain as an example, balancing efficiency, cost, and trade confidentiality.
Traditional cross-border payment systems have been hampered by speed and cost issues for decades. Payments made through traditional correspondent banking channels like SWIFT typically take 2 to 5 days to complete, accompanied by high fees and opaque intermediaries. Take global fast-fashion giant SHEIN as an example; its business model heavily relies on a global supply chain network of thousands of suppliers requiring rapid response. Therefore, it is extremely sensitive to the efficiency and cost of cross-border payments. To address the shortcomings of the traditional SWIFT system, the industry has naturally explored more efficient blockchain solutions such as stablecoins. However, even with the introduction of new tools like stablecoins to improve efficiency, companies still face the combined challenges of data privacy rules (such as the EU GDPR) and complex compliance requirements across different jurisdictions. Moreover, for SHEIN, every payment on a transparent blockchain could inadvertently reveal its precise procurement prices for different suppliers, order allocation strategies, and even global fund transfer paths to its competitor, Temu, directly threatening its core competitive advantage. Businesses urgently need a payment solution that combines the privacy guarantees of traditional banking systems, the settlement speed of stablecoins, and the compliance flexibility to cope with complex global regulatory frameworks.
BenFen Chain's privacy-focused payment system offers a novel solution: a "B2B cross-border privacy settlement layer." This solution utilizes TX-SHIELD's privacy-preserving stablecoin technology, enabling near-instantaneous on-chain transactions between businesses. Crucial transaction amounts and counterparty identities remain hidden, visible only to the transacting parties and authorized regulatory bodies. The solution aims to achieve near-instantaneous settlement, reduce average transaction fees by over 50%, and ensure zero leakage of core business secrets such as procurement strategies and sales channels, thereby building a critical information advantage for businesses in the fierce global trade competition.
4. Privacy-enhancing Treasury Management: Taking MicroStrategy as an example, reshaping the enterprise-level blockchain financial system.
As global enterprises accelerate their digitalization, treasury management has transformed from a back-office function into a core element of corporate strategy. It not only determines the safety and liquidity of corporate funds but also directly impacts capital structure, market signals, and strategic decisions. However, as more and more companies attempt to optimize their treasury structure using blockchain and crypto assets, new problems have emerged—while efficiency increases, increased transparency also brings the risk of strategic exposure . Take MicroStrategy , a US-listed company, as an example. This company is one of the world's most well-known "blockchain treasury pioneers." Since 2020, MicroStrategy has continuously purchased Bitcoin through bond financing and its own funds, incorporating it into its balance sheet to combat inflation and optimize long-term value reserves. While this move has become a milestone in corporate asset allocation innovation, it has also exposed the privacy dilemmas of blockchain's public ledger. Every time a company conducts a fund transfer, asset rebalancing, or a new round of purchases, it is recorded and analyzed in real time on the blockchain. Any market observer can infer its positions, cost ranges, and even future operational intentions from the transaction paths. This means that while blockchain brings transparency and trust, it also exposes a company's fund allocation, investment pace, and even internal financial structure to global analysts. For a listed company, this could not only trigger market volatility and speculative behavior, but also affect its market capitalization management, bond ratings, and even the precise control of capital market signals.
More and more companies are no longer satisfied with the closed and slow traditional treasury systems and are beginning to explore real-time financial systems based on blockchain. However, they are also concerned that adopting a public ledger would be equivalent to making all funds publicly available. Therefore, companies urgently need a treasury solution that can realize the advantages of blockchain's "instant settlement and automated scheduling" while protecting fund privacy and meeting audit compliance requirements like the traditional banking system .
This is precisely the unique value of this subchain privacy payment system . Through the sophisticated MPC technology provided by TX-SHIELD, this subchain allows enterprises to complete asset transfers, profit reinvestment, or stablecoin liquidity allocations on-chain while simultaneously encrypting key financial information (including transaction amounts, flow, and asset structure) for privacy. The system automatically generates verifiable encrypted proofs, granting verifiable access only to authorized auditing institutions or regulatory nodes. In this way, enterprises can execute treasury operations with the high efficiency of blockchain while achieving "invisibility off-chain" privacy protection under the premise of "verifiable on-chain."
If MicroStrategy operates its treasury management under this architecture, its fund allocation, currency distribution, and asset rebalancing will no longer be exposed to the public market, but it can still ensure that all on-chain operations comply with regulations, are auditable, and are consistent with financial reports. In other words, this subchain enables enterprises to achieve a truly "cryptographically verifiable treasury": public oversight and private execution.

5. DAO Treasury Management and Anonymous Funding: Building a "Strategic Barrier" for Decentralized Organizations, Using Uniswap DAO as an Example
Large DAOs (such as Uniswap DAO) typically manage hundreds of millions or even billions of dollars in assets. While complete transparency of their treasury is the cornerstone of community governance, it also brings real-world challenges and pain points: when Uniswap DAO considers investing in an early-stage DeFi project, the fully public details of negotiations and transfers make it easy for other whales or competitors to capture the investment, causing the DAO's acquisition costs to skyrocket and rendering the investment strategy completely ineffective. A strong practical need exists to provide a degree of operational privacy for teams or specific committees when executing investments, distributing grants, and rewarding contributors, while maintaining effective community oversight of the overall health of the treasury and the general direction of fund usage. This would protect their competitive strategies and operational efficiency.
We envision providing a dedicated "privacy treasury" module for DAOs on this subchain. DAOs can utilize the subchain's privacy payment functionality to make specific confidential investments, anonymously fund projects, and privately reward contributors. Afterwards, DAOs can use a selective disclosure mechanism to demonstrate to the community the overall rationality and compliance of fund usage within a specific timeframe, without disclosing details of every sensitive transaction. The technical feasibility of this solution has been validated in official use cases by privacy-focused blockchain projects such as Aztec Network. Furthermore, the Messari report, "Understanding Decentralized Confidential Computation (DeCC)," provides a theoretical framework from an industry perspective for this exploration of introducing data confidentiality capabilities while maintaining decentralization. This solution will empower DAOs, granting them protection capabilities similar to the "trade secrets" of traditional companies, thereby attracting more traditional capital and institutions seeking strategic privacy to enter the Web3 world through the DAO model, promoting the further prosperity and maturity of the decentralized ecosystem.
For end users: Privacy-preserving payments are the technological cornerstone of personal financial dignity and freedom of life.
1. Protecting Daily Consumption and Digital Life: Safeguarding the "Digital Persona" of Cryptocurrency Traders
With the improvement of the global cryptocurrency payment infrastructure—from the crypto cards launched by Visa and Mastercard to the integration of USDC payments by mainstream fintech companies such as PayPal and Revolut—more and more users are beginning to use cryptocurrencies to complete daily transactions in the real world. Blockchain payments are moving from a "niche behavior for investors" to a "lifestyle for the general public." However, an overlooked fact is that the complete transparency of public blockchains is turning "digital life" into a glass house that can be spied on.
Imagine a well-known cryptocurrency trader or Web3 entrepreneur whose every purchase—from Starbucks coffee and Netflix subscriptions to holiday gifts for family—is made through the same public wallet. This information can be easily tracked, aggregated, and cross-analyzed. Blockchain analytics firms and advertisers can then use this data to profile their lifestyle, wealth distribution, interests, and even health and family relationships. This complete data exposure threatens personal privacy, security, and even personal freedom. In fact, this is not an isolated case. 2024 annual reports from Chainalysis and CipherTrace both indicated that over 70% of on-chain identity profiles were built from user behavior exposed in "everyday transactions," rather than during large investment events. CoinDesk and The Block also stated bluntly in their commentary: "Without privacy, cryptocurrency payments will forever remain in the experimental stage."
For Web3 payments to truly become mainstream, it's not enough to just address the issues of efficiency and cost; users must also regain the privacy boundaries of their digital personas. In other words, privacy is a prerequisite for the widespread adoption of payments, not just a technological option to enhance them.
BenFen Chain's privacy payment system is designed specifically to address this core pain point. Based on the BenPay (www.benpay.com) ecosystem built on this sub-chain, users can use the BenPay Card application within the BenPay ecosystem to complete everyday small payments such as dining, subscriptions, travel, and online purchases. This allows stablecoin payments to be integrated into daily life in a more accessible and frequent manner, enabling small payments for items like dining, subscriptions, travel, and online purchases. The system utilizes sophisticated MPC technology to automatically hide the amount, time, recipient information, and address relationships between different transactions for each transaction. Furthermore, BenFen Chain has designed a "selective disclosure mechanism"—users can grant merchants or regulatory agencies limited transaction visibility when needed, achieving a "verifiable but untraceable" payment experience.
The expected effect of this solution is not only to protect personal privacy, but also to promote the widespread adoption of blockchain payments in society.
• For ordinary consumers, it means regaining cash-like freedom in the digital world—consumption is no longer an entry point for data mining;
• For merchants, it increases user trust and promotes more frequent use of Web3 native payments;
• For regulators, privacy is no longer synonymous with a "black box," but rather a kind of "transparency with boundaries."
In the longer term, privacy-preserving payments will become a fundamental public infrastructure of digital life . It is both a technological manifestation of personal data sovereignty and a prerequisite for the true integration of the Web3 economy into social life.

2. Protecting the Purchase of Sensitive Goods and Services: Taking the Purchase of Prescription Drugs as an Example, Safeguarding Individual Consumer Privacy.
Against the backdrop of increasing global compliance pressures and the growing centralization of payment platforms, consumers are gradually losing their last line of defense for privacy when purchasing legitimate but sensitive goods or services. Traditional payment systems, through centralized accounts and identity verification mechanisms, make every transaction traceable and analyzable. For groups who need to regularly purchase prescription drugs or mental health services, this is tantamount to exposing their personal lives to the spotlight.
The rise of blockchain payments, especially stablecoin payments, has offered a completely new possibility for such scenarios: it boasts advantages such as instant settlement, cross-border accessibility, and no risk of intermediary-induced freezing , making it particularly suitable for sensitive consumption scenarios in an internationalized digital life. However, this transparent ledger characteristic also brings more intractable problems—when a transaction for medicine or psychological counseling is recorded on the blockchain, anyone can trace the purchase, thereby reconstructing an individual's health, lifestyle, and financial situation. This "transparency backlash" renders blockchain payments unusable in areas where privacy is most crucial.
Mainstream media outlets such as CoinDesk have repeatedly commented that "without privacy, cryptocurrency payments will struggle to be adopted in mainstream consumer scenarios." This assessment is already supported by market evidence—the use of privacy coins like Monero in some e-commerce and sensitive service sectors demonstrates users' strong demand for privacy protection. However, such solutions often conflict with compliance requirements, making it difficult for them to enter mainstream payment systems.
BenFen Chain 's privacy payment feature is highly helpful in such scenarios. Users can pay merchants through BenPay Merchant, an ecosystem application of BenPay. The entire process is completed on-chain, ensuring transaction execution, but crucial transaction amounts, address information of both parties, and the specific consumption details derived from them are all hidden. This allows users to securely access the services they need without worrying about core details of their private lives being permanently recorded on a public ledger, becoming a future threat. We aim to further promote privacy payments as the "default payment option for sensitive consumption scenarios." For users, it's like providing a "protective shield for consumption freedom," guaranteeing their fundamental right to consume according to their own will without harming others, and upholding their personal dignity. For the blockchain payment ecosystem, this is a crucial step in penetrating the mainstream consumer market and meeting users' deeper needs, as it solves a real pain point that also exists in traditional electronic payments but is amplified dramatically on the blockchain.
3. Protecting freelancers and micro-businesses: Taking Upwork designers as an example, providing them with "trade secret protection."
In today's booming global digital economy and remote collaboration, freelancers and micro-businesses are rapidly increasing their demand for efficiency and flexibility in cross-border settlements. More and more people are adopting blockchain and stablecoin payments as a new option for cross-border payments and settlements. Whether it's creative workers on traditional platforms like Upwork and Fiverr, or Web3 developers providing services for DAO and NFT projects, they are increasingly accepting stablecoin payments such as USDT and USDC. The reasons are practical: blockchain payments offer seamless cross-border transactions, instant settlement, lower fees, and avoid the complex processes and geographical restrictions of traditional banks. This makes stablecoins a new universal currency in the global freelance market.
However, as more individual economic activities are brought onto the blockchain, they are also passively exposed to a "completely transparent" ledger. A top UI designer taking on projects on Upwork might simultaneously serve a cash-strapped startup and a Fortune 500 client. Their pricing strategies, revenue fluctuations, and even the sources of their main clients, once all publicly available on the blockchain, can be easily observed by competitors, clients, and even third-party data analytics companies. This "naked" state on the blockchain puts them at a disadvantage in price negotiations and may even lead to trust and disputes, directly weakening their pricing power and market competitiveness. Individual business owners also need to protect their "trade secrets"—especially pricing strategies and client relationships. In the traditional economy, this information is naturally protected by bank account privacy and business confidentiality systems; but in the on-chain economy, they have virtually no barriers.
This phenomenon of "transparency backlash" is becoming a hidden concern for the new generation of individual economies. While centralized payment platforms such as Stripe and Payoneer offer some privacy protection, users must completely entrust their data to the platform and have no control over their business information. A 2024 report by CoinDesk also pointed out that "in the Web3 economy, privacy is no longer just a personal issue, but part of business competitiveness." This subchain privacy payment provides a structural solution for this user group. By using subchain payments, individual workers and merchants can securely complete payments on-chain while hiding transaction amounts, counterparty identities, and transaction connections, effectively preventing external inferences about pricing strategies or customer relationships. This mechanism retains the efficiency, low cost, and global accessibility advantages of blockchain payments while providing confidentiality similar to traditional business systems, giving individual economic participants their first "technological bargaining umbrella." It allows independent designers, developers, content creators, and cross-border merchants to control the security of their business data like large enterprises, continuously creating value in a fair and respectful market environment.
4. Financial self-defense under geopolitics: Constructing an "economic lifeline" using Turkish designers as an example.
In the current climate of intertwined geopolitical and macroeconomic risks, blockchain is gradually becoming a "financial self-defense tool" for people in some regions. In countries like Turkey and Argentina, which have experienced hyperinflation or strict capital controls, freelancers, small business owners, and even ordinary depositors often find it difficult to secure their wealth or conduct cross-border payments through the traditional banking system. Therefore, they are turning to blockchain and stablecoins, with digital assets becoming an "alternative lifeline" to resist currency devaluation and circumvent capital blockades.
However, a new dilemma arises: the transparency of blockchain technology leaves users "naked" on the chain. Take a Turkish resident as an example: if he wants to convert some of his income into a US dollar stablecoin to hedge against lira devaluation, he finds all transfers, asset balances, and conversion paths exposed on the blockchain, meaning his entire financial footprint could be exposed to the public. This exposes him to a double threat: regulators may use these public records to determine if his actions violate capital flow policies, initiating a "freeze first, then review" process that locks up his assets; simultaneously, publicly disclosed wealth makes him an easy target for criminals. This "vulnerability brought by transparency" significantly diminishes the protective role of blockchain in high-risk countries.
This is creating a strong real-world demand: in regions with limited capital and volatile currencies, people not only need decentralized stores of value, but also privacy protection mechanisms —a financial infrastructure that can "survive" in an environment of distrust. BenPay Privacy Payment is precisely a response to this. When users save on-chain and complete peer-to-peer transfers through BenPay C2C, their asset balances and counterparty information are hidden, thus enabling them to both hedge against inflation using stablecoins and avoid the risks associated with on-chain transparency. Chainalysis research data shows a significant increase in cryptocurrency retail adoption in regions with high inflation and political instability, confirming the urgency of this trend. We believe that privacy payment is not only a technological innovation, but also a "financial human rights" infrastructure. It provides individuals in distress with a last line of defense to protect their wealth and free trade, becoming an "economic escape pod" for them to maintain economic activity and safeguard their dignity in extreme environments.
5. Maintain the purity of charitable donations: Take anonymous acts of kindness as an example to safeguard the original intention of doing good.
In today's philanthropic landscape, public figures, entrepreneurs, or ordinary philanthropists often face public pressure, moral blackmail, or persistent solicitations of donations after making large or sensitive donations, once their actions become public. For example, an entrepreneur wishing to fund cutting-edge technological exploration or fringe art creation might not want their name publicly associated with the donation to avoid unnecessary commercial attention or public misunderstanding. This distorts what should be a pure act of kindness and even deters some potential donors. Individuals wishing to donate anonymously and charitable organizations prioritizing donor privacy both need a payment method that ensures the safe and traceable delivery of funds to recipients while fully protecting donor anonymity, allowing goodwill to flow freely. The case of Ethereum founder Vitalik Buterin's anonymous donation to Ukraine using Tornado Cash is a powerful example, demonstrating that even industry leaders have a strong desire to protect donation privacy in certain situations.
BenFen Chain's privacy payment system is the ideal tool for achieving this goal. Donors can directly donate to charitable organizations' public addresses through BenFen Chain, completely concealing the donor's wallet address and the specific donation amount throughout the process. BenFen can further promote cooperation with large charitable foundations to jointly foster the establishment of "charitable privacy payment" standards. This will reshape the culture of philanthropy, encouraging more spontaneous donations, especially attracting donors who prefer not to flaunt their wealth or wish to maintain a low profile for various reasons, allowing acts of kindness to truly return to their purest and freest essence.
For government clients and third parties: Privacy-preserving payments are the next-generation regulatory technology for achieving "precise compliance".
1. Achieving "Auditable Privacy": Exploring a New Paradigm for AML/CFT Compliance Using the Tornado Cash Case as an Example
As blockchain technology continues to evolve, especially with the strengthening of anonymity and privacy protection, traditional financial regulatory systems are facing unprecedented pressure. Regulatory agencies have historically relied on transaction traceability and entity identifiability as two pillars to fulfill their AML/CFT responsibilities. However, while strong privacy technologies protect user data, they also weaken regulators' ability to obtain transaction information on-chain. This "technological blindness" forces regulators to rely on traditional methods such as territorial jurisdiction and sanctions against controllable entities, making it impossible to distinguish between legitimate users and violators. Consequently, regulatory measures often exhibit a "one-size-fits-all" characteristic—both cracking down on illegal activities and restricting citizens' freedom to engage in legitimate privacy transactions.
The Tornado Cash incident is a prime example of this dilemma. In 2022, the U.S. Treasury Department sanctioned Tornado Cash because the coin mixer was used by some malicious actors for money laundering, including for financial flows linked to North Korean hacking groups (US Treasury, 2022). This incident demonstrates that without efficient management of anonymous transactions, regulators can only control risks indirectly, unable to accurately distinguish between legitimate and illicit transactions. This reveals a deep contradiction: privacy technologies designed to protect individual rights and regulatory systems aimed at maintaining public safety are locked in a power struggle within the existing framework. Regulatory agencies urgently need a technological means to achieve efficient and accurate identification and prevention of illicit activities without monitoring all legitimate transactions or infringing on public privacy rights— a leap from "extensive blocking" to "precision governance."
Against this backdrop, this subchain proposes an innovative "auditable privacy" solution. We embed compliance capabilities into the protocol layer through Complex Multi-Party Computation (MPC), making "regulatory compliance" a core feature rather than an afterthought. Specifically, regulatory agencies can verify transaction compliance (e.g., "this transaction does not involve addresses on sanctions lists") without needing to examine the transaction amount or participant identities, achieving a technological paradigm upgrade from traditional "data-driven regulation" to "logical regulation."
This subchain's architecture adopts a two-layer compliance design :
• First layer: KYC identity foundation
By partnering with compliant service providers, we offer off-chain KYC verification for businesses and high-frequency users, generating verifiable credentials. This not only ensures the legitimacy of participants but also provides an institutional foundation for AML/CFT, serving as a trust anchor for all advanced financial activities, especially corporate payments and payroll.
• Second layer: Protocol layer with auditable privacy
Based on verified identity compliance, MPC is combined with zero-knowledge proof technology to achieve transaction privacy protection and auditability. Regulators can verify transaction compliance without exposing transaction amounts or the identities of both parties, thus ensuring that the vast majority of legitimate transactions enjoy default privacy, while providing regulators with precise governance tools.
This two-tier architecture systematically resolves the core contradiction in regulation: regulatory agencies can effectively combat illegal activities, while businesses and individual users can protect their financial data and trade secrets within a compliant framework. This subchain thus provides critical infrastructure for large-scale enterprise-level applications of blockchain finance, resolving the conflict between privacy and compliance and ushering in a new era of compliant technology.
2. Improve tax audit efficiency: Taking the audit of small and medium-sized technology companies as an example, build a more harmonious tax collection and payment relationship.
In traditional tax audits, tax authorities typically require companies to provide several years' worth of bank statements and detailed accounts to verify the accuracy and compliance of their tax returns. For example, a mid-sized technology company, when undergoing a routine tax audit, not only needs to provide transaction records from the past few years but also faces the problem of an audit process that takes months and severely disrupts its R&D and operational schedule. More importantly, the company's management is always concerned that core trade secrets such as customer lists, partner information, and pricing strategies may be leaked during the lengthy audit process. This model reflects the shared dilemma faced by both parties: ensuring tax fairness while minimizing disruption to the company's normal operations.
As blockchain technology matures, businesses are beginning to explore using it to record transaction data in their daily operations to improve efficiency, transparency, and security. Some blockchain platforms (such as Ethereum and Hyperledger) can achieve real-time on-chain recording and automated recording of financial transactions, potentially facilitating tax audits. PwC has also proposed a solution using blockchain technology to track corporate taxes and transactions, aiming to improve tax compliance and transparency and reduce the burden of manual audits through on-chain data.
However, existing blockchain solutions still have significant drawbacks: while transparent ledgers provide complete transaction records, the amount of each transaction, the parties involved, and their relationships are publicly disclosed. This can lead to the exposure of corporate trade secrets, especially sensitive data involving customer lists, revenue structures, and partner information. Therefore, relying solely on traditional blockchain records cannot solve the need for corporate privacy protection during the auditing process.
BenFen Chain's privacy-preserving payment and related technologies were developed to fill this gap. When businesses use BenFen Chain to record transactions in their daily operations, they can generate necessary proofs during the audit process to verify propositions with tax authorities without disclosing every transaction detail. This "data usable but not visible" design effectively protects business secrets and customer privacy while ensuring audit compliance. Furthermore, BenFen Chain integrates sophisticated privacy computing technology (complex MPC) at the protocol layer and combines it with off-chain KYC authentication to form a "two-layer compliance system." Regulatory agencies can verify the compliance of transactions without seeing specific amounts or information about the transacting parties, achieving an advanced standard of "default privacy, selective disclosure." This not only improves tax audit efficiency and reduces corporate compliance costs but also helps build a more trustworthy and efficient tax-paying relationship, promoting the large-scale application of blockchain in corporate financial management and tax compliance.
The twelve scenarios we've analyzed in depth above collectively confirm a core point: privacy-preserving payments are not a marginal function, but rather a crucial component for fixing key flaws in the existing blockchain paradigm and unleashing its true potential. By providing sophisticated technical safeguards for trade secrets, personal dignity, and compliance efficiency, it enables blockchain technology to better serve mainstream business, individual users, and regulatory systems.
However, this is just the beginning. Once "payment privacy" becomes a reliable fundamental capability, a much broader space for innovation will open up. Imagine:
• If institutions can execute strategies on-chain without being targeted, how many times would DeFi liquidity increase?
• How fair would governance be if DAO voting were no longer influenced by large holders? (e.g., A16Z has veto power on Uniswap)
• How accurate would price discovery be if bidding were no longer anchored to expectations by the "first bid"?
• How many new collaborative models will emerge if companies can jointly analyze data without revealing trade secrets?
These scenarios were impossible in the past, not because the technology was immature, but because the conflict between "transparency" and "privacy" remained unresolved. When forced to choose between "transparency for trust" and "privacy but isolation," many high-value collaborations simply couldn't occur. Now, let's further consider what we can build with privacy when it becomes infrastructure, not a luxury.
This is not a display of technological prowess, but a redefinition of "trust"—from "trust can only be built through openness" to "trust can also be built through encryption," and from "collaboration can only be achieved through transparency" to "collaboration can also be achieved through privacy."
Building a Dream for the Future: From "Privacy Payments" to "Privacy Collaboration": A Paradigm Shift
Over the past decade, we have witnessed breakthroughs in privacy technology in the payment field—protocols such as Zcash, Monero, and Tornado Cash have made it impossible to trace "who transferred how much money to whom." This is the 1.0 era of privacy technology: information hiding .
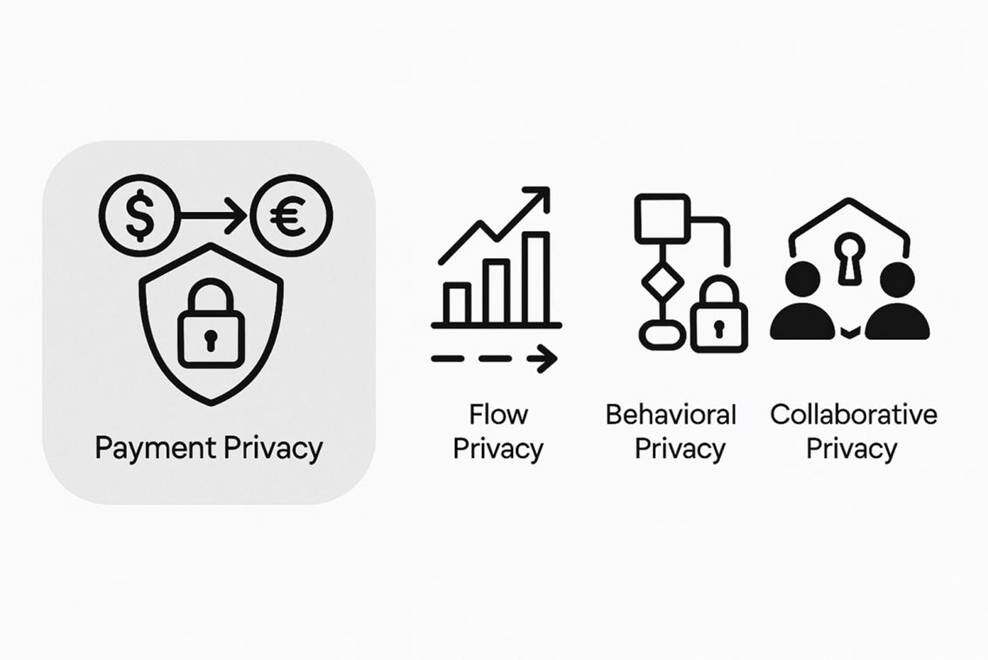
But payment privacy is just the beginning. The real future lies in flow privacy , behavioral privacy , and ultimately, collaborative privacy .
What are the differences between these three?
• Process privacy : Hides trading strategies, market behavior, and intent patterns.
• Behavioral privacy – Hides trading behavior, strategy paths, and market intentions to prevent operational patterns from being deduced.
• Collaborative Privacy : Establish a "protected collaborative space" among multiple parties, ensuring data stays on-premises and insights are shared securely.
We believe that the future world will be centered on "protected collaboration," redefining the boundaries of payments, transactions, governance, and social cooperation.
Privacy is no longer "invisible," but "selectively visible."
Trust no longer originates from a central authority, but from verifiable, encrypted collaboration.
This is not a minor technical fix; it is a reconstruction of the trust infrastructure.
1. Transaction Process Privacy: The Birth of On-Chain Dark Pools
Why do institutions need a privacy marketplace?
The transparency of traditional blockchains is a protection for retail investors, but a curse for institutions.
When an asset management firm executes a large transaction on-chain, the entire market can see it: counterparties can speculate on your strategy, arbitrageurs can preempt your orders, and competitors can replicate your model. This "forced transparency" fills the on-chain market with information asymmetry, which in turn distorts the price discovery mechanism.
In traditional finance, dark pools exist precisely to solve this problem—allowing large transactions to take place in an anonymous environment, avoiding market shocks. However, centralized dark pools have a fatal flaw:
• Operators can engage in malicious activities : preemptive transactions, information leaks, price manipulation.
• Lack of regulatory transparency : It is impossible to verify whether transactions were executed fairly.
• Single point of failure : The collapse of a centralized system can destroy the entire market.
TX-SHIELD is building a regulated dark pool on-chain—a transaction infrastructure that achieves "selective transparency" in a decentralized environment. Benfen is the embodiment and core carrier of this infrastructure.
How can technology achieve "selective transparency"?
The core challenge here is: how to ensure that both parties in a transaction can see each other, that regulators can intervene when necessary, but that other market participants remain completely unaware?
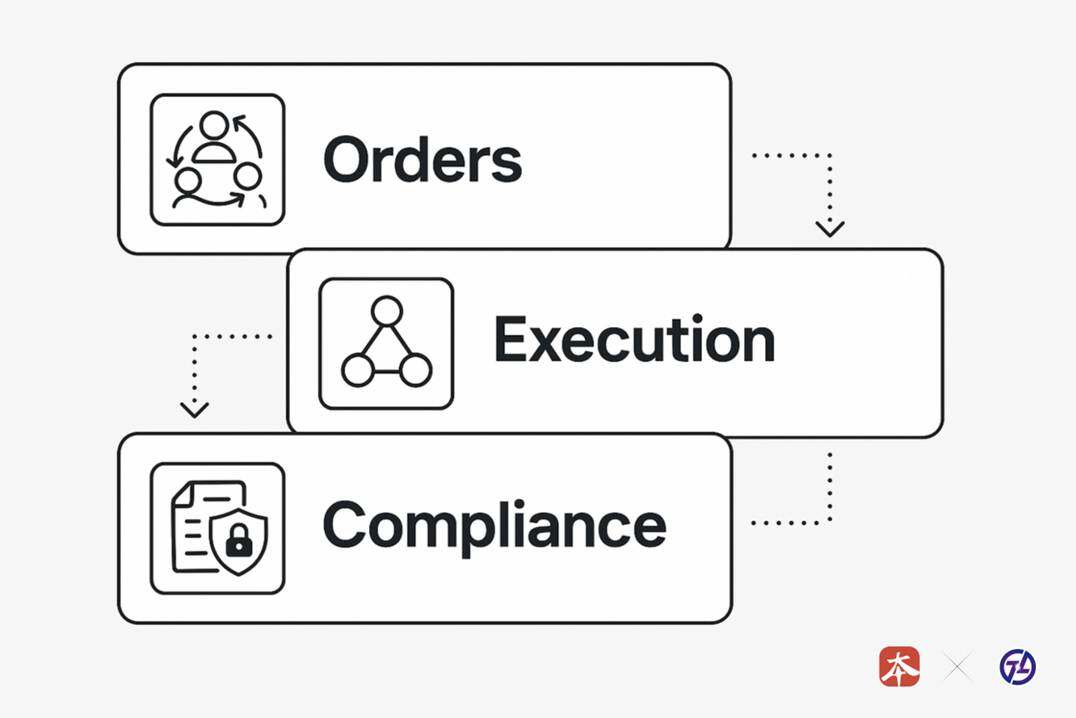
TX-SHIELD employs a multi-layered privacy architecture:
1. Order Layer : Based on a multi-party secure computation (MPC)-based order matching mechanism, transaction intentions are submitted and matched in a cryptographic state.
2. Execution Layer : Zero-Knowledge Proof (ZKP) ensures that the validity of transactions can be verified, but specific parameters (price, quantity, identity) are not disclosed.
3. Compliance Layer : Selective Disclosure Mechanism. Regulators hold the decryption key and can access specific transaction records during legal proceedings.
This means:
• Markets are no longer manipulated because they are public—trading intentions are kept confidential before execution.
• Institutions can securely execute policies on-chain —without worrying about information leaks.
Stablecoins and RWAs (Real-World Assets) can circulate with privacy —achieving both compliance and privacy.
Dark Pool is not just a market tool, but also the underlying infrastructure for privacy finance . For the first time, it allows traditional financial institutions to seriously consider "going on-chain," because they no longer need to choose between transparency and policy protection.
2. DAO Governance: How Confidential Voting Reshapes DAOs
The Dilemma of DAO Governance: The Cost of Transparency
The ideal of Decentralized Autonomous Organizations (DAOs) is to enable community members to make decisions collectively through voting, replacing traditional hierarchical structures with code and consensus.
However, in reality, DAO governance often doesn't go as planned.
• Voting results are observed in advance : The votes of large investors can influence the decisions of smaller investors, creating a "herd effect" (e.g., Uniswap, Radiant Capital).
• Social influence hijacks rationality : The public stance of well-known KOLs can suppress dissenting opinions.
• Bribery and collusion : When voting results are visible in real time, coordinated attacks become easy.
The root of these problems lies in the fact that excessive transparency leads to information asymmetry, rather than solving it.
True democracy requires two conditions: free expression (without the influence of others) and verifiable results (ensuring no cheating). Traditional open voting only satisfies the second condition.
Confidential voting: restoring honesty to governance
TX-SHIELD's confidential voting mechanism is based on homomorphic encryption and multi-party secure computation (MPC):
• Voters' ballots are submitted to the blockchain in a secret state.
• The vote counting process is conducted in an encrypted state, and no one can see the individual votes.
• The final result is publicly verified using zero-knowledge proofs, ensuring the accuracy of the vote counting process.
This seems simple, but it actually redefines the trust logic of DAOs:
"Privacy makes governance honest."
Within this framework:
• Each person's vote is independent and unaffected by others.
Large investors cannot manipulate small investors through "signal display".
The correctness of the result can be verified mathematically, rather than relying on trust.
More importantly, this mechanism can be extended to more complex governance scenarios :
• Hierarchical governance : Voters with different weights aggregate their weights in a dense state.
• Proxy voting : The proxy relationship is kept confidential, but the voting results are traceable.
• Prediction Market : A decentralized prediction market based on confidential voting
Only when governance shifts from "open transparency" to "verifiable privacy" does a DAO truly have the potential to become a new type of organization.
3. Confidential bidding reveals true value.
What is the essence of auctions?
In economics, auctions are considered a "price discovery mechanism"—using competition to bring goods back to their true value.
However, traditional auctions have a fundamental flaw: the information anchoring effect .
When the first bidder offers 1 million, the others' expectations are anchored around that number. Even if someone thinks the item is worth 2 million, they might only bid 1.1 million—because they are afraid of appearing foolish for "bidding too high."
The result is that auctions are not about discovering prices, but about guiding prices. The first person to bid controls the market's psychological expectations.
Blockchain Implementation of Sealed Auction
TX-SHIELD's privacy auction mechanism uses a digital form of sealed-bid auction :
1. Submission Stage : Bidders submit encrypted bids, and no one (including the auctioneer) can see the specific amount.
2. Reveal Phase : All bids will be automatically decrypted via a smart contract after the agreed-upon time.
3. Settlement Phase : The highest bidder wins, and all other bids are returned (or a second-price auction may be used depending on the mechanism design).
This allowed the market to truly achieve " competition with symmetrical information " for the first time—each bidder's offer was based on their own true valuation, rather than signals from others.
Application scenarios: From NFTs to carbon credits
This mechanism can be applied to all scenarios that require "fair price discovery":
• NFT Auctions : Artwork value is determined by genuine demand, not speculative expectations.
• Carbon credit market : Companies bid based on actual emission reduction costs, rather than strategic bidding.
• Spectrum auction : The government sells spectrum resources, preventing operators from driving down prices through signal negotiation.
• Data auctions : Businesses bid for datasets while protecting their privacy and avoiding price leaks.
Confidential auctions are not just a technological tool, but a crucial step for privacy technology to enter the value discovery layer. They demonstrate that privacy is not the enemy of efficiency, but rather a prerequisite for a fair market.
4. Unlock a brand new collaboration mode
The End of Privacy: The Restructuring of Social Collaboration
If the first three scenarios represent the application of privacy technology in "transactions" and "governance," then the fourth dimension is the reconstruction of social collaboration itself .
When individuals, institutions, and machines can collaborate securely in a secure environment, we begin to unlock new socio-economic models—models that were previously impossible due to "excessive trust costs" or "lack of privacy guarantees."
Scene 1: Anonymous Creation Reward System
Problem : Creators often face "identity bias" when publishing their work—works by well-known authors easily gain attention, while works by newcomers are overlooked. This leads to a distorted evaluation system.
TX-SHIELD solution :
• The identity of the work is encrypted and hidden upon submission.
• Reviewing and tipping are conducted anonymously.
• Once the quality of the work reaches a certain threshold, the creator may choose to reveal their identity.
• Revenue sharing is automatically executed through smart contracts, with creators, curators, and the platform distributing profits proportionally.
This model has already shown its potential in fields such as music, literature, and design—only when the "work" and the "author" are decoupled can the value of creativity be purely evaluated.
Scenario 2: Decentralized Credit Lending
Problem : Traditional credit assessment relies on centralized institutions (banks, credit reporting agencies), but these institutions either cannot cover global users or have data monopolies and privacy abuse issues.
TX-SHIELD Solution :
• A user's on-chain behavior (transaction history, DeFi participation, social reputation) is aggregated into a "credit score" in cryptographic mode.
• Neither the lender nor the borrower needs to disclose specific data, but they can verify each other's credit rating.
• The scoring model is governed by the community; the algorithm is transparent, but the data is private.
This model, which assesses credit based on encrypted data rather than identity, allows the unbanked to access financial services while protecting their privacy from abuse.
Scenario 3: Cross-enterprise joint data collaboration
Problem : Industries such as healthcare, finance, and logistics possess a wealth of high-value data, but this data cannot be shared due to privacy regulations (GDPR, HIPAA) and competitive relationships. This limits AI model training and hinders the generation of industry insights.
TX-SHIELD Solution :
• Based on the Federated Learning and Multi-Party Secure Computation (MPC) framework, data remains on-premises within the enterprise.
• Model training is performed in dense state, sharing only gradient updates (and the gradients undergo differential privacy processing).
The final model is jointly owned by all parties involved, but no single party has access to the original data of any other party.
This model is transforming fields such as medical research (multi-hospital joint training of diagnostic models), financial risk control (multi-bank joint anti-fraud), and supply chain optimization (multi-enterprise joint demand forecasting).
This is precisely the vision of TX-SHIELD's MPC-FL (Multi-Party Secure Computation + Federated Learning) framework: a system that enables "privacy to become the infrastructure of social collaboration." More importantly, TX-SHIELD solves a core problem in federated learning: how to fairly quantify the contribution of each party? This is the essential difference between TX-SHIELD and traditional federated learning solutions.
In traditional federated learning, all participants jointly train a single model, but it's impossible to accurately measure who contributed how much value. This leads to two fatal problems:
• Free-rider problem: The party with poor data quality can also enjoy the same rights.
• Incentive Imbalance: Those with high-value data lack the motivation to continue participating.
The TX-SHIELD framework, through dense-state computation, can quantify and score the model contribution of each party without exposing the original data.
Company A contributed 30% — the marginal contribution of its data to the improvement of model accuracy.
• Enterprise B contributed 34% — its data covers key long-tail scenarios.
Company C contributed 36% — its data quality was the highest, reducing model variance.
Based on this contribution metric, rights are automatically allocated:
• Governance power : Voting weight is directly proportional to contribution; those with higher contributions have greater say in model iterative decision-making.
• Profit Rights : Commercial revenue from the model is distributed based on contribution; the more you contribute, the more you earn.
• Data sovereignty : Any party can withdraw at any time; their contributions are recorded, but their data is not retained.
This contribution is not calculated once, but dynamically updated as the model iterates. As a party consistently provides high-quality data, its share of the equity gradually increases; if data quality declines or contributions cease, the share decreases accordingly. Only when the model is no longer updated does the equity allocation become fixed. This creates a self-optimizing incentive mechanism —participants are motivated to continuously provide high-quality data, rather than engaging in a "one-off transaction."
This is the essential difference between TX-SHIELD and traditional federated learning schemes.
Google's Federated Learning, OpenMined, and other solutions have solved the problem of "how to train models while protecting privacy," but they assume that all participants are equal—whether you provide 1 million high-quality data points or 10,000 noisy data points, your rights are the same.
TX-SHIELD further answers the question: How to ensure fairness in collaboration while protecting privacy? We not only protect privacy, but also quantify contributions and allocate rights.
This "verifiable fairness" transforms collaboration from a "moral constraint" into a "mechanism guarantee":
In the medical field, large tertiary hospitals and primary care clinics can collaborate fairly—tertiary hospitals provide complex case data, while primary care clinics provide data on common diseases. The contributions of both parties are accurately measured, and the situation is no longer one where "large hospitals dominate and small clinics follow along."
In the financial sector, large banks and small fintech companies can work together to combat fraud—both the historical data of large banks and the real-time data of small companies are valuable, and the rights and interests are distributed according to actual contributions, rather than a zero-sum game where the "big eats the small".
In the supply chain field, brands, logistics companies, and retailers can work together to optimize inventory—each party's data (sales forecasts, transportation efficiency, inventory turnover) is quantified as a specific contribution to model improvement, and the benefits are shared proportionally.
This is not only a technological innovation, but also a revolution in the paradigm of collaboration: when contributions can be quantified, trust can be calculated; when rights can be verified, collaboration can occur and continue.
Scenario 4: Dense Collaboration Infrastructure and Data Quantization
The most radical vision is that future intelligence will not belong to a single AI, but to a network of AI. Multiple AI agents will collaborate within a trusted privacy layer, much like neurons make up the brain—a single neuron is ordinary, but network connections create consciousness.
Why does AI need collaboration?
Today's AI models are becoming increasingly specialized: some excel at image recognition, some are proficient in natural language processing, and some specialize in mathematical reasoning. However, real-world problems often require cross-disciplinary capabilities—diagnosing diseases requires analyzing medical images, medical records, and genetic data simultaneously; autonomous driving requires integrating visual perception, path planning, and traffic prediction.
No single AI can handle everything; collaboration is inevitable.
But there's a fundamental contradiction here: AI models are assets, they are competitive advantages. When two AIs need to collaborate, they cannot simply "share their data" with each other—this would lead to reverse engineering of the models, inference of training data, and leakage of trade secrets.
TX-SHIELD's core solution is to provide the cryptographic infrastructure for building AI collaboration.
Specific scenario:
Medical Diagnostic Collaboration
• Agent A (image AI) analyzes CT scans and detects lung abnormalities.
• Agent B (Pathology AI) infers possible causes based on symptom descriptions.
• Agent C (Gene AI) assesses treatment plans based on patient genotype.
• Three AIs exchange inference results in a closed state to generate a comprehensive diagnostic report.
• However, no single AI can see the model parameters or training data of other AIs.
Financial risk control collaboration
• Agent A (Trading AI) detects abnormal trading patterns
• Agent B (Credit AI) assesses the user's historical credit record.
• Agent C (Anti-fraud AI) cross-validates multi-source data
• The final output is a risk score, but the models and data of each AI remain isolated.
Autonomous driving collaboration
• Vehicle AI needs to collaborate with urban transportation system AI, weather forecasting AI, and logistics scheduling AI.
• They share essential information (road conditions, weather, delivery needs) in a closed-loop manner.
• However, their respective algorithmic logic, historical trajectory data, and business strategies remain confidential.
Technical Implementation: Collaborative Reasoning in Close-State Models
When AI agents need to share models, experience, and inference results, they should not expose data directly to each other (this would lead to model reverse engineering or data leakage), but should exchange information in a closed state:
• Agent A and Agent B, without exposing their respective models, jointly deduce a conclusion.
Agent C can verify the correctness of this conclusion, but cannot deduce the model parameters of A and B.
• The collaboration process can be audited, but the details of the reasoning remain private.
This kind of "close-state collaboration" will become the foundation of the future AI economy.
When AI Agents begin to own assets (crypto wallets, digital identities), execute contracts (on-chain smart contracts), and provide services (API calls, data exchanges), the trust mechanism between them must be cryptographic—not "I trust you don't do evil," but "cryptographically guarantees you can't do evil."
Furthermore, TX-SHIELD's contribution quantification mechanism can also be applied to AI collaboration: each agent's contribution to the final result can be quantified, and the benefits are distributed proportionally. This allows for genuine "economic collaboration" between AIs, rather than simply technical collaboration.
Imagine a future Web3 collaboration scenario based on the TX-SHIELD framework:
• A medical diagnostic task is completed collaboratively by 5 professional AIs, costing $100.
• Imaging AI contributes 35%, pathology AI contributes 30%, gene AI contributes 20%, drug development AI contributes 10%, and coordination AI contributes 5%.
• Earnings automatically distributed: $35/$30/$20/$10/$5
• The entire process is verifiable on the blockchain, but the models and data of each AI are completely private.
This is not science fiction; it is the inevitable direction of the integration of cryptography, blockchain, and AI.
TX-SHIELD aims to become the trust infrastructure of this AI collaboration network—enabling agentic AI or robots to collaborate like humans, but with greater trustworthiness. In this new paradigm, trust comes from cryptography—you don't need to disclose information, you only need to prove you've followed the rules. Zero-knowledge proofs, secure multi-party computation, and federated learning —these technologies decouple "verification" from "public disclosure," and separate "collaboration" from "exposure." We believe that privacy is not a boundary, but a bridge to the future.
Conclusion: Privacy is the new language of trust.
Starting with addressing immediate pain points, we witnessed how privacy-preserving payments act as a robust barrier, protecting trade secrets, safeguarding personal dignity, and achieving precise compliance. It corrected the inherent flaws of transparent blockchains, enabling them to truly serve the real world. Furthermore, we moved towards building a dream for the future, envisioning the limitless possibilities that will emerge when privacy becomes the default setting. From on-chain Dark Pools to confidential voting, from confidential auctions to entirely new paradigms of data collaboration, we clearly see that privacy is no longer just about "hiding," but also about "empowerment"; it is not only a shield of defense but also an engine of collaboration.
This is a profound paradigm shift: we are moving from an era where "transparency must be exchanged for trust" to a new era where "cryptography can guarantee trust." The source of trust has shifted from forced public exposure to verifiable confidential computation.
The joint exploration between Benfen Public Chain and TX-SHIELD shares this vision: we are not merely developing a feature or a protocol, but jointly laying the foundation of trust for the next generation of the internet. In this future:
Businesses can collaborate without hesitation in competition, thus stimulating innovation;
Individuals can live freely in the digital world and regain their sovereignty;
Society can achieve more efficient collaboration while protecting privacy, thus unleashing collective wisdom.
Privacy is never the end. It is the starting point for a freer, fairer, and more efficient digital civilization. And we are working together to make it a reality.
About BenFen
BenFen is a high-performance public blockchain built specifically for stablecoin payments. Based on the Move programming language, we have created a secure, low-cost, and highly scalable underlying network. Its core feature is the ability for users to directly pay gas fees with stablecoins, significantly lowering the barrier to entry and paving the way for large-scale applications. Building upon powerful cross-chain and multi-currency settlement capabilities, BenFen covers diverse payment scenarios through a rich ecosystem of applications. More importantly, we provide enterprise users with crucial privacy payment options, ensuring they can enjoy the efficiency advantages of blockchain while protecting their core business data from leakage.
Benfen is committed to becoming a global stablecoin circulation network serving corporate payroll, cross-border payments, e-commerce, and offline merchants—a next-generation financial infrastructure that balances efficiency, cost, and security.
Regarding TX-SHIELD
TX-SHIELD is a regulatory on-chain privacy settlement infrastructure that provides stablecoins and blockchain applications with privacy-preserving and regulatory-visible payment and settlement capabilities.
Core Solution:
• TX-SHIELD: A privacy infrastructure for blockchain applications, enabling confidential transactions, dark pools, and a privacy-centric protocol layer.
Our innovations :
We not only protect transaction privacy, but also reshape asset ownership and security through distributed cryptography. TX-SHIELD's solution enables enterprises and financial institutions to achieve joint asset custody, privacy-based clearing, and regulatory compliance auditing without disclosing trade secrets.
We are building an infrastructure layer that will prevent privacy from becoming an obstacle to regulation and institutional adoption, and instead serve as a protective layer for financial flows.
TX-SHIELD — The private and regulatable settlement base-layer for stablecoin, blockchain and enterprise.