How to detect and counter the "North Korean hacker team" around you?
- 核心观点:朝鲜黑客组织Lazarus威胁加密安全。
- 关键要素:
- 四年盗超28亿美元加密资产。
- 伪装求职者渗透企业系统。
- 公开63名黑客身份数据。
- 市场影响:推动企业加强安全审查机制。
- 时效性标注:长期影响。
Original | Odaily Planet Daily ( @OdailyChina )
By CryptoLeo ( @LeoAndCrypto )

The crypto world has suffered from North Korean hackers for a long time!
Recently, the Security Alliance (SEAL) published a post titled "Helping You Identify Real North Korean Developers," along with six photos of North Korean hackers from a website it launched. The Security Alliance also published the source URL for the images: lazarus.group
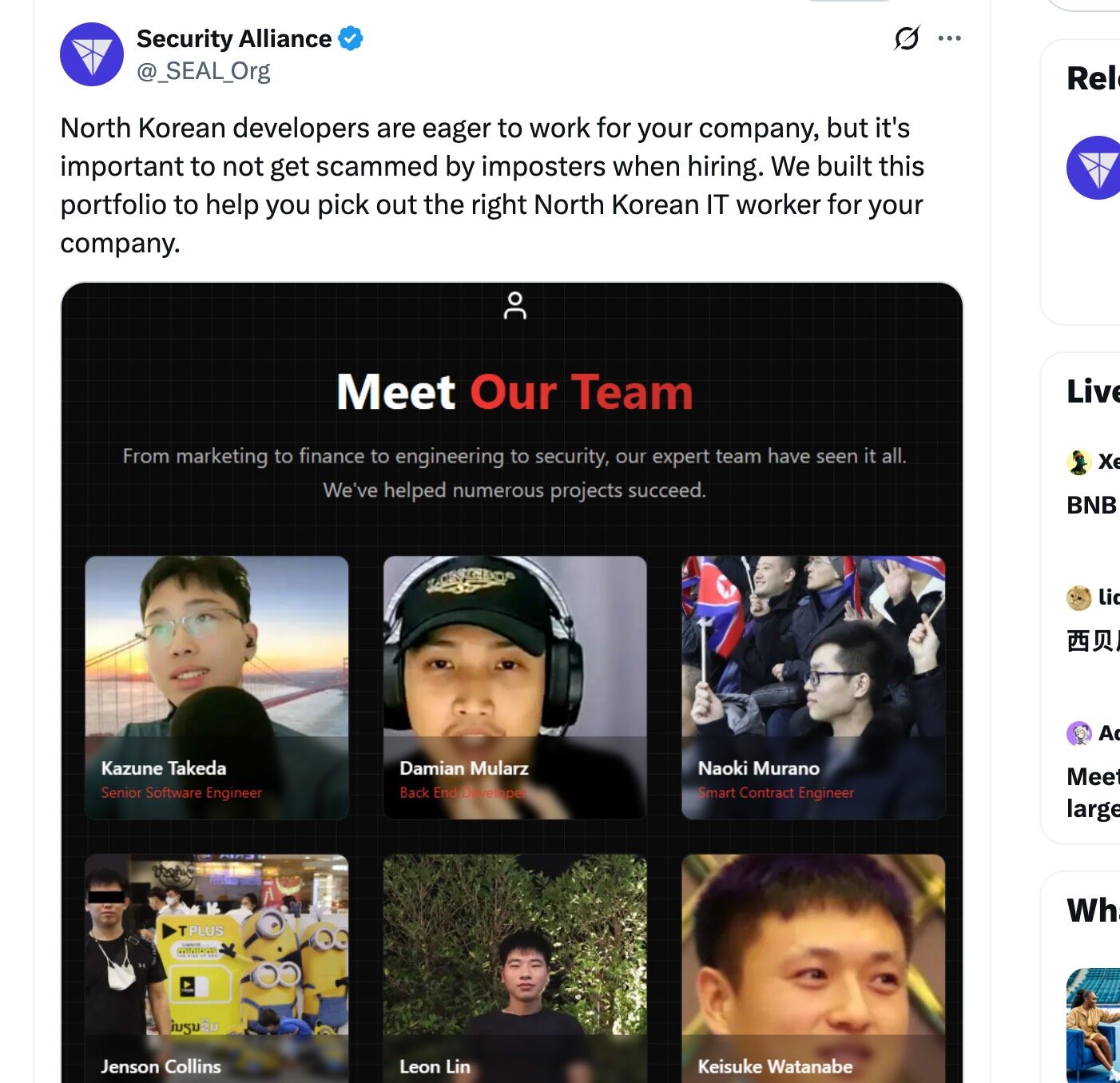
Everyone is probably familiar with the Lazarus Group, the notorious North Korean hacker group. This post quickly sparked heated discussion on social media, driven by the fact that North Korean hackers are using fake identities like internet developers and engineers to infiltrate projects and businesses, launching various attacks to steal funds and cause projects to fail prematurely.
The Lazarus Group, North Korea's biggest behind-the-scenes threat
As North Korea's largest hacker group, they have been involved in every large-scale hacking incident in recent years. They have used various hacking techniques to steal huge amounts of crypto assets from major institutions and companies. They even ranked third in the list of government entities holding Bitcoin, surpassing Bhutan and El Salvador, the two largest BTC diamond holders, and their holdings are second only to the United States and the United Kingdom.
Related reference: Lazarus Group is the top three Bitcoin holdings on the blockchain. Is North Korea also trying to encrypt its strategic reserves?
In reality, the Lazarus Group's theft activities extend far beyond the crypto industry. Its "business" is broad, encompassing the theft of bank funds, sensitive data, trade secrets, military intelligence, and ransomware. Some also suggest that the Lazarus Group's operations are not always motivated by money, but rather by stealing official technology and data to support North Korea's technological development and to sow chaos in support of geopolitical objectives.
Regarding the crypto world, Lazarus Group’s operational performance over the past four years is as follows:
2022: Over $600 million in crypto assets stolen from Axie Infinity
Specifically, the hacker contacted an engineer at Sky Mavis, the developer of Axie Infinity, via LinkedIn and WhatsApp, luring him to an interview with a new job opportunity. After multiple interviews, the engineer was offered a highly lucrative position and a fake offer. This fake offer was sent as a PDF file. After the engineer downloaded the PDF, a malware embedded in it infiltrated the Ronin system. The hacker then took over the Ronin network validator and stole funds.
2023: Poloniex and HTX lose over $200 million
The Poloniex and HTX thefts were caused by the compromise of private keys. Hackers used advanced persistent threat (APT) tactics to infiltrate and monitor Poloniex for extended periods, ultimately gaining access to the hot wallet. APT attacks are characterized by high stealth, targeted targeting, persistent attacks, and advanced methods.
Both platforms are related to Justin Sun (it can be concluded that Brother Sun was targeted at the time).
2024: Over $500 million stolen from DMM Bitcoin ($300 million) and WazirX ($230 million)
In May 2024, Japanese cryptocurrency exchange DMM Bitcoin detected an improper outflow of 4,502.9 bitcoins from its wallet. The Financial Services Agency of Japan requested DMM investigate the theft and provide a compensation plan for customers. A subsequent official statement stated that the theft was caused by a social engineering attack by TraderTraitor, who posed as a LinkedIn recruiter and tricked employees of Ginco Inc., responsible for managing DMM's trading, into downloading malicious code. The malicious code then manipulated trade requests and transferred funds to the hacker's wallet. DMM also promised to compensate customers, but due to financial pressure, it closed in December 2024. DMM will subsequently migrate customer accounts and assets to SBI VC Trade on March 8, 2025.
In July 2024, the Indian trading platform WazirX was hacked, resulting in the theft of approximately $230 million. An investigative report revealed that the theft was caused by a cyberattack on one of WazirX's multi-signature wallets. The attacker exploited a discrepancy between the Liminal interface and actual transaction data to trick three WazirX signatories and one Liminal signer into approving a seemingly normal transaction (e.g., a standard USDT transfer). In reality, this transaction contained a malicious payload that had modified the wallet's smart contract logic by upgrading it. This tampering allowed the attacker to gain complete control and transfer all funds without requiring WazirX's key.
2025: $1.5 billion stolen from Bybit
In February 2025, Bybit suffered a $1.5 billion theft, the largest cryptocurrency theft in history. Specifically, a developer's computer with system publishing privileges was compromised. The attacker uploaded and modified a JavaScript code file stored in Safe's AWS S3 bucket. This file contained malicious logic targeting Bybit's Ethereum Safe wallet and an unknown wallet (presumably used by the attacker for testing and verification), thereby compromising the Safe{wallet} front-end interface. Subsequently, during Bybit's normal hot and cold wallet token transfers, all Safe{wallet} users saw and used the Safe{wallet} front-end, which had been infected with the malicious code. As a result, Bybit multi-sig participants saw the Safe{Wallet} front-end display as normal. Ultimately, the hacker deceived multiple (three) signatories and ultimately gained control of the multi-sig wallet through malicious transactions, completing the attack.
All of the above are hacking thefts in which the Lazarus Group participated or was indirectly involved. The amounts of money stolen were huge and the methods were professional. Many of the thefts were not due to security vulnerabilities or human errors, but funds were still lost despite the long-term monitoring of the Lazarus Group. The Lazarus Group can be said to be omnipresent.
CZ helps warn of common scams used by the Lazarus Group
After the post was published, CZ quickly retweeted it and listed some common scams used by North Korean hackers:
1. Posing as a job seeker and trying to get a job at a company. This allows hackers to get close to their targets, and these hackers are particularly interested in development, security, and finance positions;
2. They pretend to be an employer and attempt to interview/hire your employees. During the interview, they will claim there is a problem with Zoom and send the interviewee an "update" link containing a virus that will take over the employee's device . Or they will ask the employee a programming problem and then send some "sample code";
3. Disguise as a user and send you a link in a customer support request that leads to a page that downloads a virus.
4. Obtaining data by bribing corporate employees and outsourcing suppliers. A few months ago, a major outsourcing service company in India was hacked, resulting in the leakage of user data of a major US exchange and the loss of user assets exceeding US$400 million (possibly Coinbase).
Finally, CZ called on companies to train employees not to download unknown files and to carefully screen job applicants.
These attacks apply not only to businesses, but individuals also need to be vigilant when encountering similar situations, such as seeing links from strangers, sharing screens, etc., especially in the crypto industry. Many people will encounter clipboard hijacking (Clipboard Hijacking) or address poisoning virus (Address Poisoning via Clipper Malware) when transferring money after being attacked. This is also the most common attack method we may encounter: when the user copies the wallet address (BTC, ETH, SOL address), the software will automatically replace it with a similar address controlled by the attacker. These replacement addresses often have almost the same beginning and end (for example, the first 4-6 characters and the last 4-6 characters are the same), causing you to transfer money to the address controlled by the hacker.
In addition, you should be cautious when receiving links from strangers on social media, as these links may contain viruses.
A Blacklist: Data and Countermeasures for North Korean Hackers
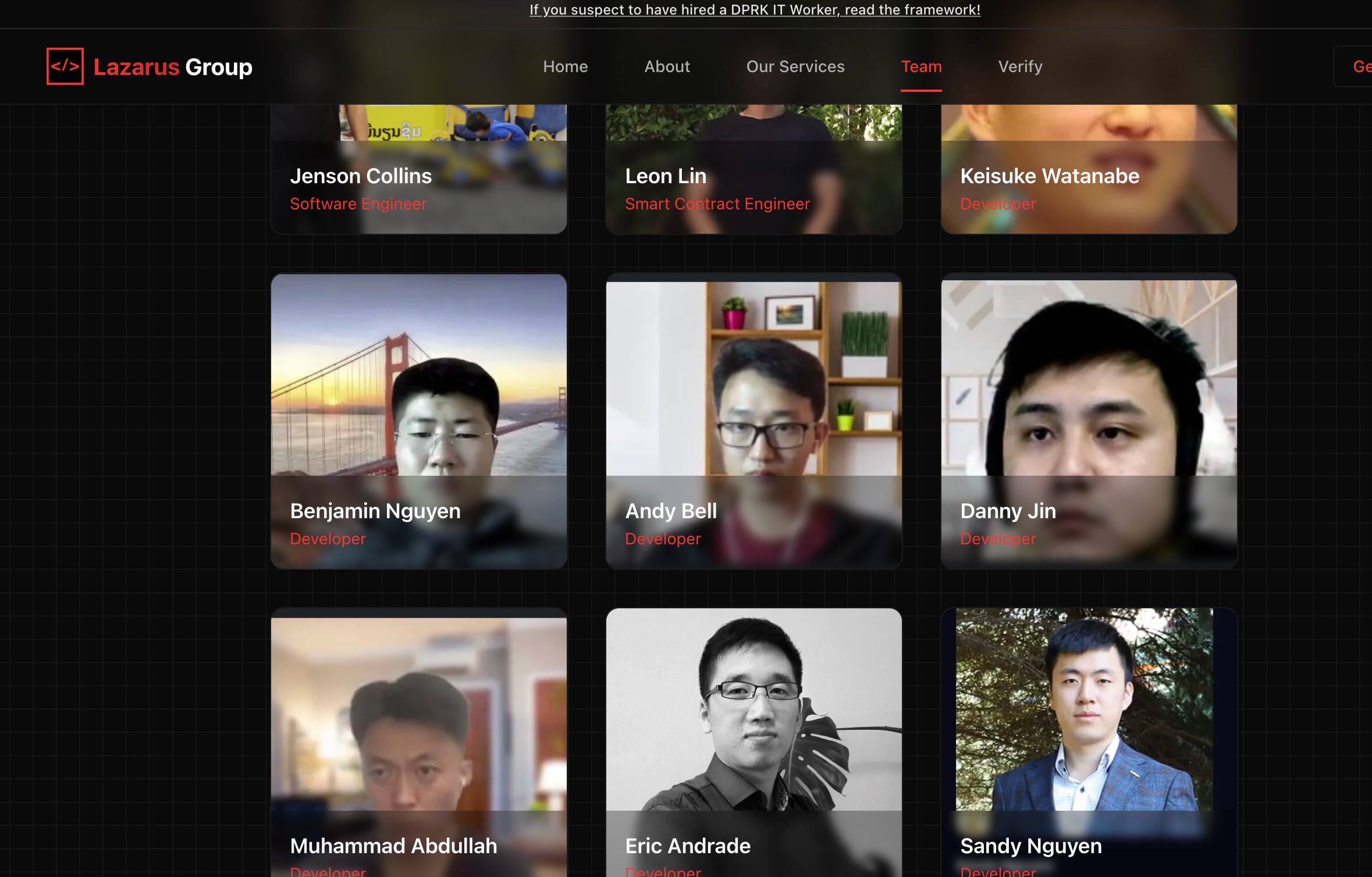
At present, the lazarus.group website has updated a list of 63 hackers. The background and status of each hacker's photo are different. These hackers tend to be developers, smart contract engineers, and software engineers (for Web 3, blockchain and back-end development). However, the information on the list is not their real information. It is likely that they are forged files by hackers of the Lazarus Group team, or they are members or associates of the Lazarus Group. Many people on the list are still working in companies.
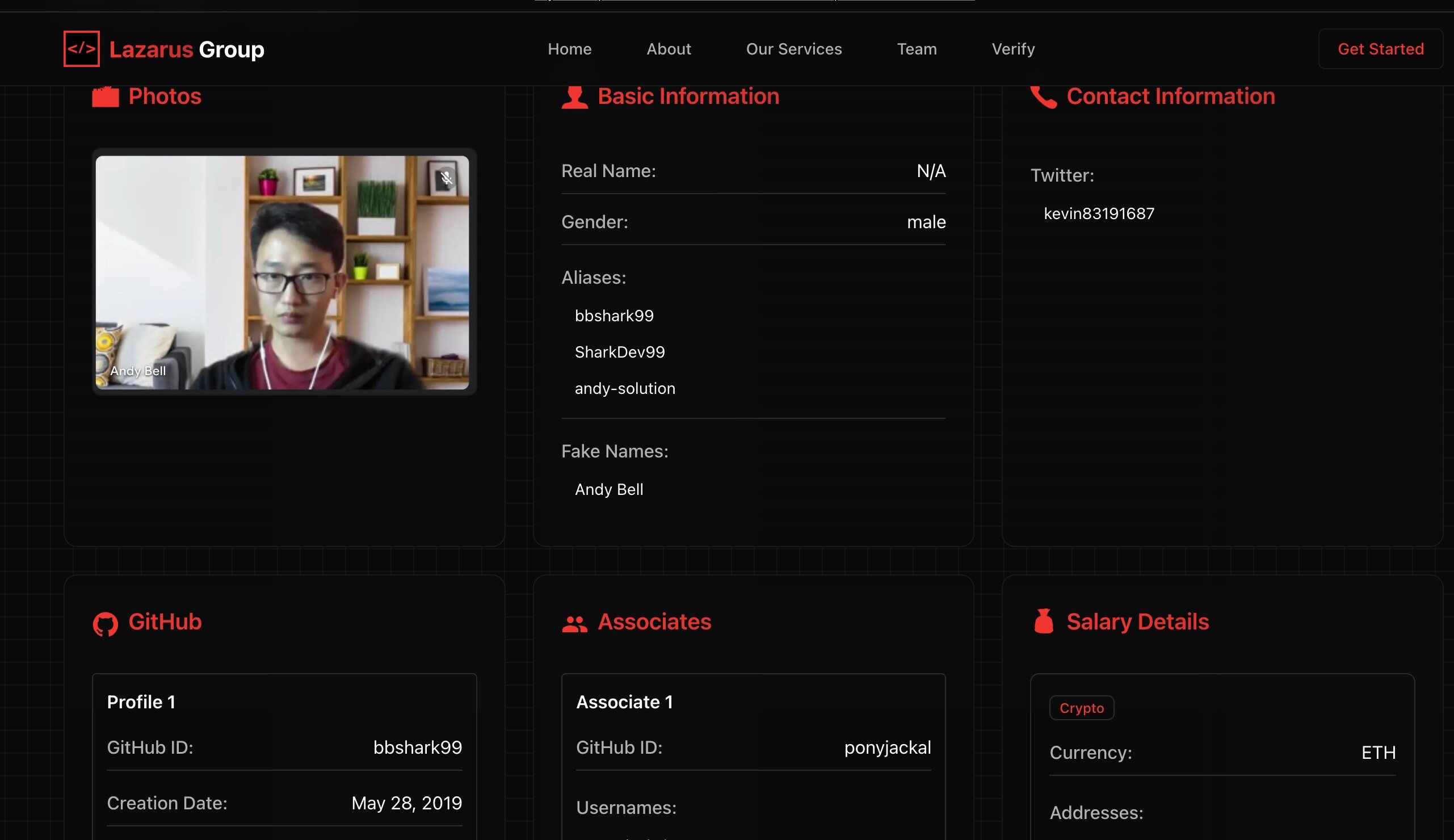
The interface lists their former names, social media accounts (email, Twitter, phone number, etc.), GitHub accounts, employment history, captured images, and even crypto wallet addresses. It also provides more detailed "resume" analysis (such as LinkedIn forgery traces and IP anomalies). This data can help HR and companies quickly identify potential risks in interviewees and employees.
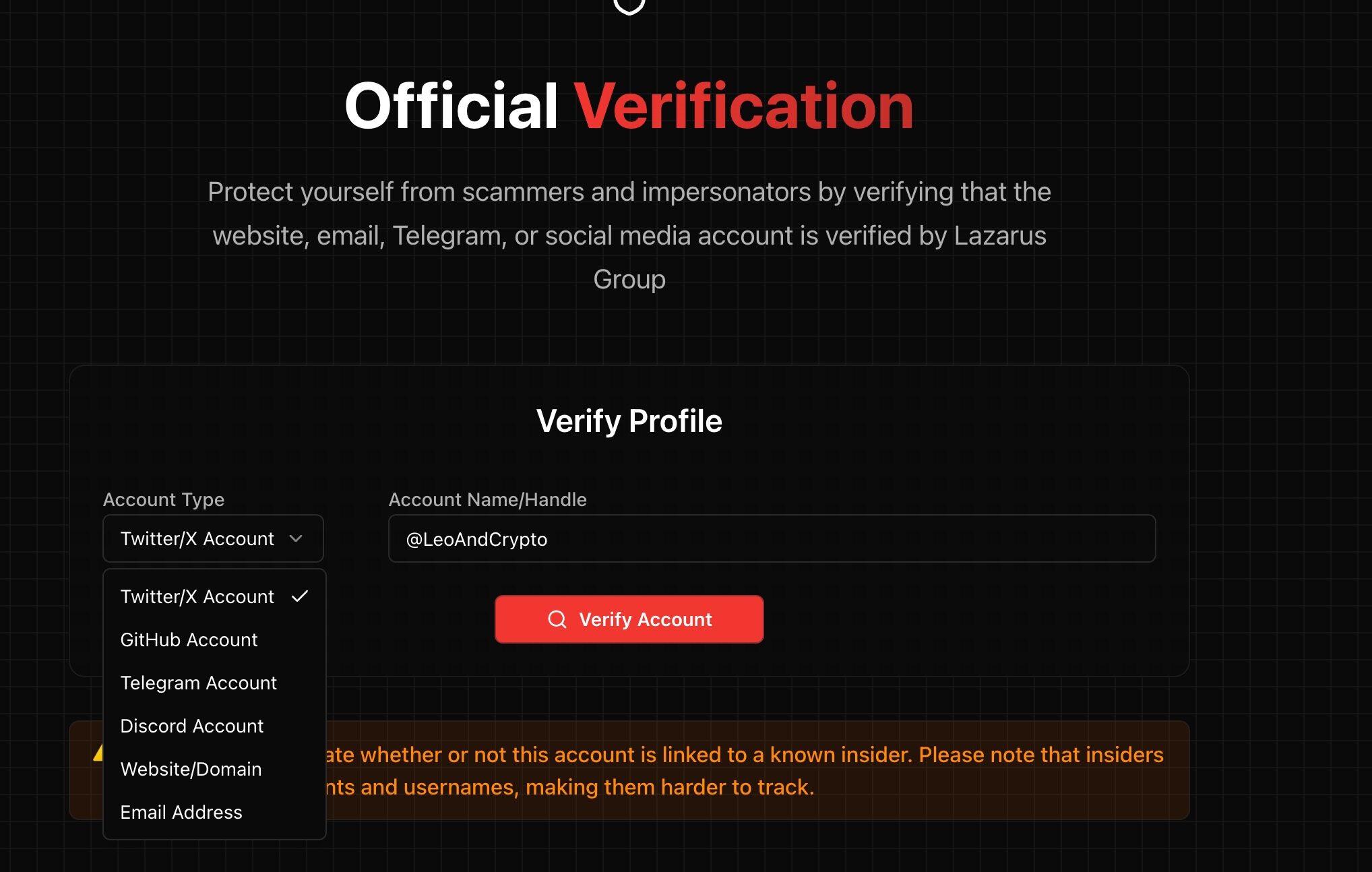
In addition, the website has also launched the function of verifying job seekers' accounts, including X, Github, TG, DC, website and email verification (free).
The SEAL Frameworks launched by SEAL can also help you better understand security-related knowledge. The document mentions:
North Korean IT workers, often using false identities to perform remote IT work for foreign companies, are a crucial source of revenue for the regime, particularly for its weapons programs. They perform a variety of IT tasks, but are not limited to IT, often disguising their identities and locations to secure freelance contracts and generate income, which is remitted back to North Korea. These workers are primarily based in China and Russia, with some located in parts of Asia, Africa, and Latin America.
The documents show that North Korea also operates a network of "facilitators" to help them conceal their identities and facilitate remote online work. Facilitators make money by lending their digital and physical identities, and their clients are mostly North Korean hackers.
Since 2010, North Korean IT workers have increased in number, become more geographically distributed, and diversified their activities . Their main goals are:
-Generate stable income for the North Korean regime through remote IT work;
-Building a support network for North Korea’s IT-related businesses (smuggling and money laundering);
- Access to Western companies’ technology, infrastructure, and identity information (including personal and corporate, digital and physical identity information);
- Disclosure of company secrets (intentionally or unintentionally);
- extortion (ransomware and blackmail);
- Avoid sanctions (North Korean entities are prohibited from accepting any form of payment from Western countries);
- Hacking (establishing permanent access to infrastructure in order to gain a foothold or infiltrate);
-Malware (to infect high-value targets for later theft).
Currently, estimates of the total number of North Korean hackers active across various companies and government agencies range from 2,000 to 15,000. However, this number includes multiple identities or inactive accounts reused by the same actor. SEAL estimates that approximately 3-5% of all Web 3 developers are North Korean, and at any given time, there are at least 200-300 North Korean-linked accounts actively seeking employment with Web 3 companies.
SEAL Frameworks also provides some advice for companies that discover that their employees are involved with the Lazarus Group:
-Don't fire them immediately, but keep things as normal while ensuring the safety of the organization to avoid alerting the enemy.
- Immediately stop all payments. If suspected, delay the process by claiming "financial problems" etc.
-Systematically revoke all access to code repositories, cloud infrastructure, and internal systems. Also, collect all available data (e.g., customer authentication documents, cryptocurrency addresses, emails, resumes) for reporting.
- Perform comprehensive security audits on all code contributions, paying close attention to dependencies, build files (Continuous Integration/Continuous Deployment), and potential backdoors.
- Once the security risk has fully resolved, terminate their contract for business-related reasons (e.g., downsizing, change of direction) and report the matter to law enforcement.
Continuously updated blacklists: short-term benefits or long-term benefits?
Regarding lazarus.group 's public list: Most people believe that the list can help companies better identify risky employees or interviewers, and perhaps reduce the number of hacking incidents.
While releasing hacker data might have some short-term benefits, in the long term, since the list is publicly visible, hackers are likely to modify their public account information and personal information after being listed. SEAL responded that many people still habitually use their usual accounts, revealing their identities. Currently, with the help of AI-powered deepfake technology, hackers may be able to update all personal information and even completely change their appearances. Therefore, the release of the list will only make hackers' disguises more covert and difficult to detect, especially since many people in the crypto industry work online.



