Chengdu Lianan x Footprint jointly released the 2022 Web3 Security Research Report
Full version of the report:first level title
Data Sources:Footprint Analytics
Overview of Web3 Security Situation in the First Half of 2022
image description
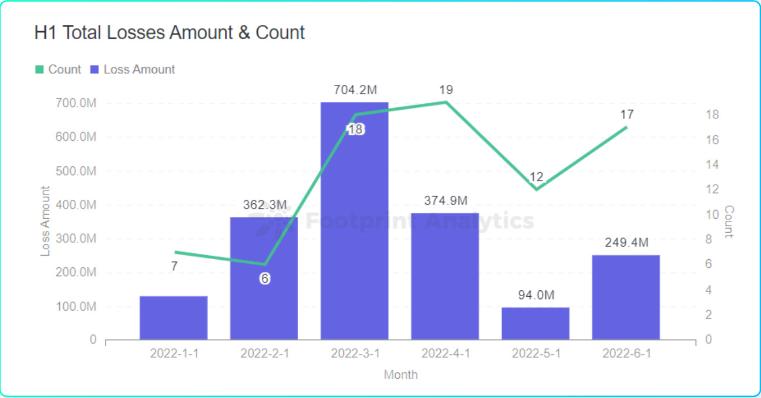
We can see the overall situation of the Web3 security field in the first half of the year from the following set of data:
In the first half of the year, there were 7 cross-chain bridge attacks, with a total loss of 1.13599 billion US dollars; 53% of the attacks were contract exploits; about 26.6% of the attacks were flash loans; there were 5 security attacks with losses exceeding 100 million in the first half of the year Event; the TVL of the entire DeFi market fell from US$276 billion in early January to US$80 billion at the end of June, a drop of 71%; hackers laundered a total of US$1.1407 billion through Tornado Cash; about 71% of the attacks occurred in the DeFi field.
In the security reports for the first and second quarters, we have shown and analyzed the overall situation in the blockchain security field from various dimensions, including the total amount of losses, the type of projects attacked, the amount of losses on each chain platform, attack methods, Fund flow, project audit status, etc.
data one
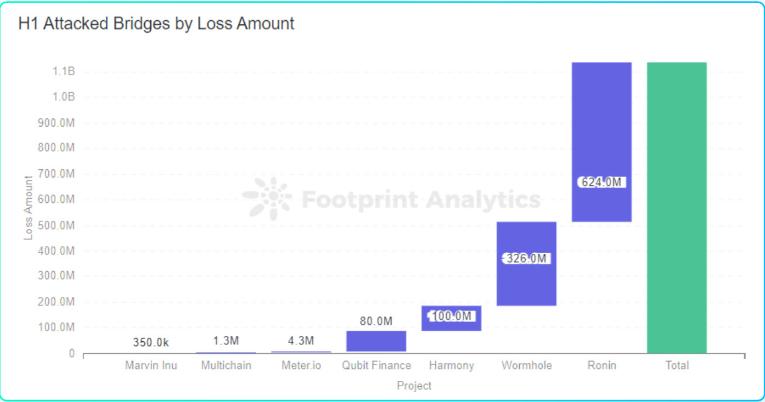
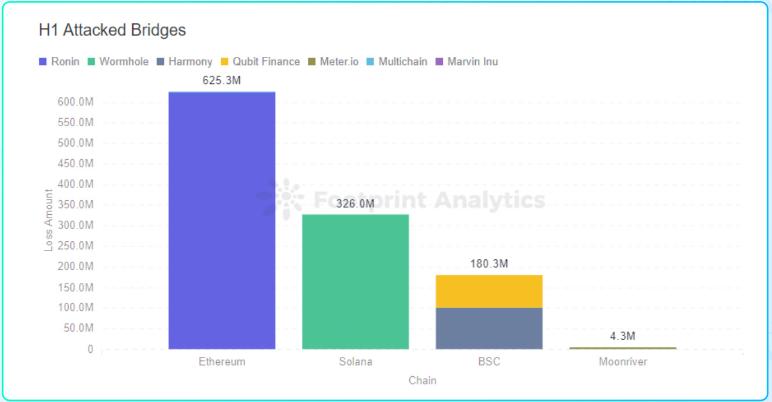
In the first half of 2022, a total of 7 cross-chain bridge attacks occurred
image description
data two
53% of attacks are contract exploits
In the first half of 2022, a total of 42 major attack cases caused by contract loopholes were detected, and about 53% of the attacks were exploited by contract loopholes.
According to statistics, in the first half of 2022, a total of 42 major attack cases caused by contract loopholes were detected, with a total loss of 644.04 million US dollars.
image description
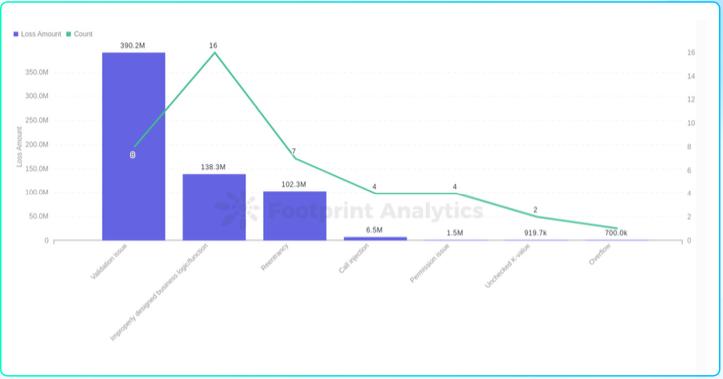
Footprint Analytics - the number of exploits and the amount of damage caused by each vulnerability
The largest single loss amount is the signature verification vulnerability. On February 3, 2022, the Solana cross-chain bridge projectWormhole under attack, The cumulative loss is about 326 million US dollars. Hackers exploited a signature verification vulnerability in the Wormhole contract that allowed hackers to forge sysvar accounts to mint wETH.
Suffered from flash loan plus reentry attack, causing a total loss of 80.34 million US dollars.Rari Fuse PoolSuffered from flash loan plus reentry attack, causing a total loss of 80.34 million US dollars.
The most common occurrences in the audit process are generally divided into four categories: 1. ERC721/ERC1155 re-entry attacks; 2. Logical loopholes; 3. Lack of authentication; 4. Price manipulation.
According to the statistics of security incidents perceived by Chengdu Lianan Hawkeye Blockchain Security Situation Awareness Platform, almost all of the loopholes in the audit process have been exploited by hackers in actual scenarios, and the exploit of contract logic loopholes is still the main part.
data three
In the first half of 2022, the number of attacks using flash loans reached 21
image description
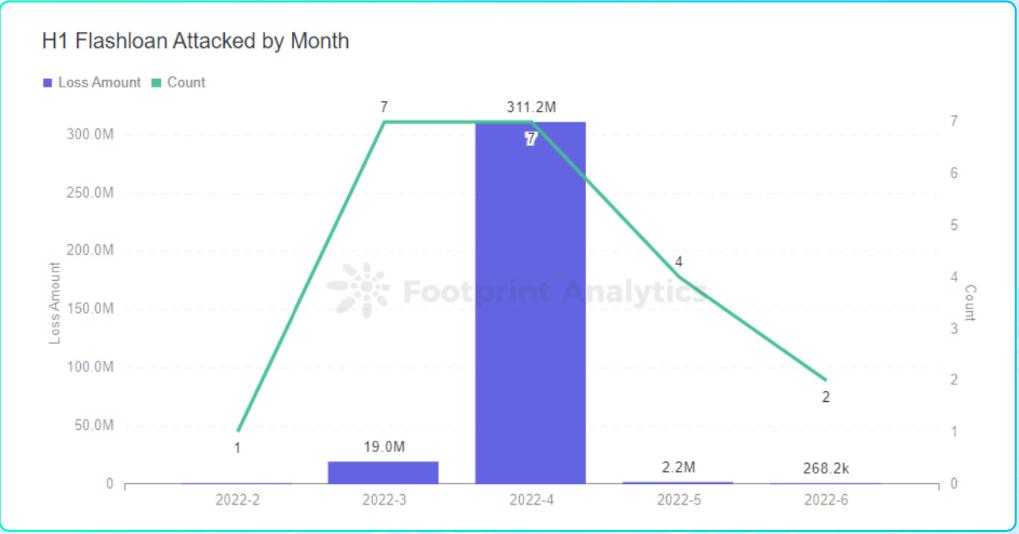
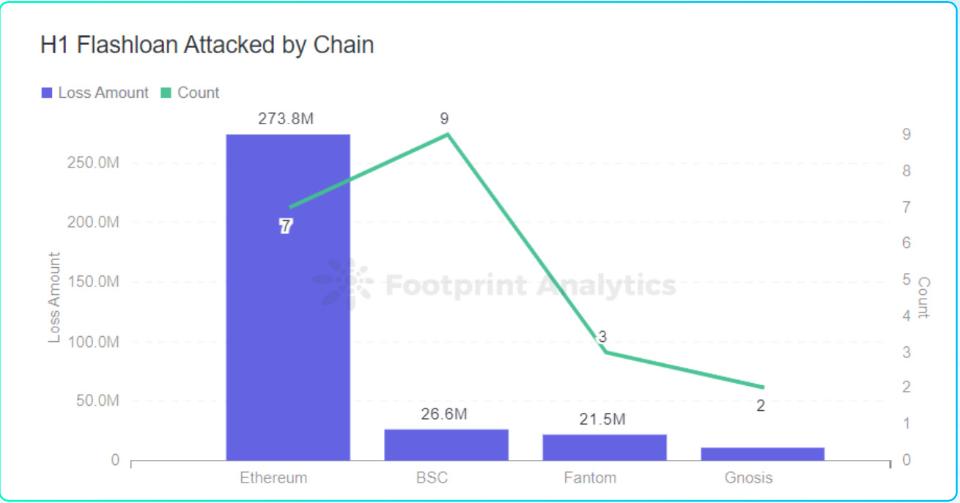
Footprint Analytics - Flash loan attack frequency and loss amount of each chain platform
1) On April 17, 2022, Beanstalk Farms, an algorithmic stablecoin project, was attacked by lightning loan and governance. The hacker made a profit of 76 million US dollars, and the protocol loss reached 182 million US dollars.
2) On April 28, 2022, the multi-chain derivatives platform DEUS Finance encountered a flash loan plus price manipulation attack, causing a loss of approximately US$15.7 million.
3) On April 30, 2022, Fei Protocol's official Rari Fuse Pool suffered a flash loan plus reentry attack, and the hacker made a profit of 28,380 ETH, worth about $80 million.
Flash loan attacks occur frequently, so how should the project party prevent or slow down the flash loan attacks? Here are a few possible suggestions:
Require key transactions to span two blocks
If a capital-intensive transaction needs to span at least two blocks, and the user needs to take out the loan in at least two block time periods, then the flash loan attack will fail. But for this to work, user value must be locked between two blocks, preventing them from repaying their loans.
Time Weighted Average Pricing (TWAP)
In the case of price manipulation, it is proposed to use time-weighted average price (TWAP) to calculate the price in the liquidity pool across multiple blocks. Because the entire attack transaction sequence needs to be processed in the same block, but TWAP cannot be manipulated without manipulating the entire blockchain, so that the instantaneous price anomaly caused by flash loans can be avoided.
More frequent price update mechanism
Also in the case of price manipulation, the frequency with which the liquidity pool queries the oracle and updates the price can be appropriately increased. As the number of updates increases, the price of the tokens in the pool will be updated faster, making price manipulation ineffective.
Stricter Governance Logic
When it comes to project governance, the rigor of the governance logic should be considered in many ways to avoid logical loopholes like Beanstalk Farms. Once there is a small loophole, it may be infinitely magnified through flash loans and eventually cause huge losses.
Ensure safety and reliability during business logic design and implementation
When the project party designs the business logic and the developers implement it, they should fully consider the integrity and security of the business logic and pay attention to extreme situations. When necessary, professional audit institutions should be found to conduct audit and research to prevent various possible risks.
data four
In the first half of the year, there were 5 security incidents with a loss of over 100 million
In the first half of 2022, a total of 5 security incidents with a loss of over 100 million occurred, namely:
RoninNetwork: $625 million
Wormhole: $326 million
Beanstalk Farms: $182 million
Elrond: $113 million
Harmony: $100 million
The total losses caused by these five hacking incidents reached 1.346 billion US dollars, accounting for 70% of the total losses in the first half of 2022.
In the quarterly report of Q2, we saw that the TVL of some projects directly returned to zero after being attacked, and there was no subsequent restart. So what happened to these projects that lost more than 100 million yuan after they were attacked?
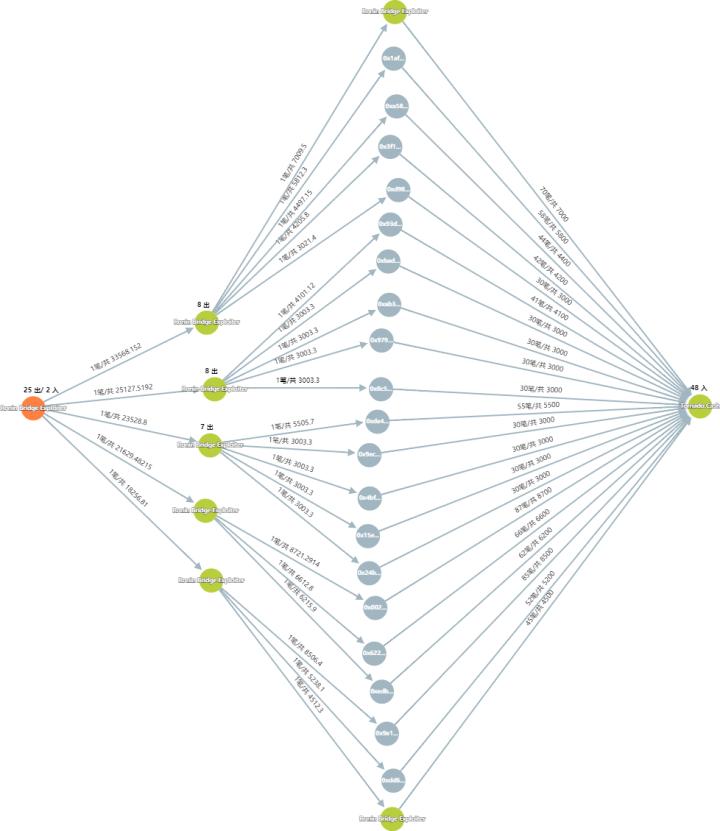
Ronin: $625 million loss, assets transferred to Tornado Cash
On March 29, Axie Infinity's Ethereum sidechain, Ronin Network, was hacked and lost about $625 million. The Ronin sidechain consists of 9 validator nodes, and to confirm a deposit or withdrawal, five validator signatures are required. The attackers managed to take control of four of Sky Mavis's Ronin validators and a third-party validator run by Axie DAO.
After the attack, the Ronin attackers transferred some of the stolen funds to Huobi, FTX, Binance, Crypto.com and other exchanges, but all major exchanges issued a statement saying that they would fully assist in recovering the stolen funds.
Subsequently, the attacker distributed the stolen assets to multiple addresses and cleaned them in batches through Tornado Cash. On May 20, the Ronin attackers transferred the last stolen funds to Tornado Cash, and all assets were cleaned. At this time, the unit price of ETH has dropped from $3,330 to about $2,000, and the hacker’s actual profit was $160 million less than when he attacked.
Using the Lianbizhui-Virtual Currency Case Intelligent Research and Judgment Platform to analyze the stolen funds, it can be seen that all the stolen funds eventually flowed to Tornado Cash.
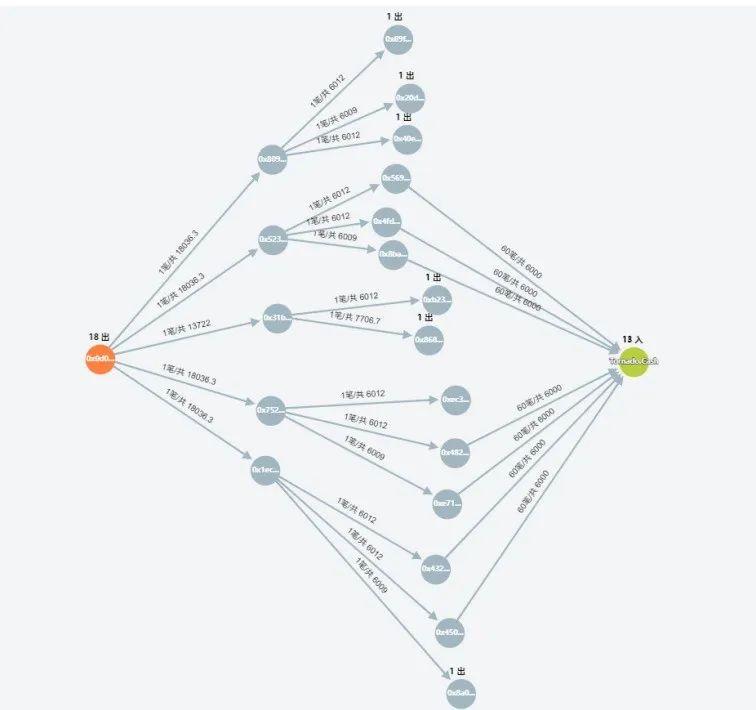
Harmony: 42,000 ETH transferred to Tornado Cash
On June 24, Harmony's cross-chain bridge Horizon Bridge was attacked, causing losses of more than $100 million.
On June 26, the founder of Harmony stated that the attack on Horizon was not caused by a smart contract vulnerability, but by the leakage of the private key. Funds were stolen from the Ethereum side of the cross-chain bridge. Although Harmony stores the private keys encrypted, the attacker decrypted some of them and signed some unauthorized transactions.
Harmony said it has started a global investigation of the hackers with law enforcement agencies and all trading platforms. At the same time, Harmony has also increased the amount of the hacker's stolen coins from the initial $1 million to $10 million. However, the hackers laundered the stolen money through Tornado Cash.
As of June 30, through the analysis of the stolen funds through the Lianbizhui-Virtual Currency Case Intelligent Research and Judgment Platform, it can be seen that the hacker has transferred about 42,000 ETH (worth about 46.2 million US dollars) to Tornado Cash.
data five
The entire DeFi TVL fell from $279.8 billion in early January to $82.4 billion at the end of June, a drop of 70.5%
The entire DeFi TVL fell from US$279.8 billion in early January to US$82.4 billion at the end of June, a half-year drop of 70.5%. Among them, the cumulative decline in TVL in May and June reached 63.2%, and it fell by 44.5% in a few days from May 5 to May 13 alone.
From the comprehensive perspective of the amount of losses in attack activities and the number of attacks, March and April are the months with the highest level of hacker activity, and the TVL in March and April is also at a relatively high point in half a year. In May, the TVL dropped sharply, and the frequency of hacking attacks and the amount stolen decreased significantly. In June, the TVL continued to decrease, and the activity of hackers increased compared with May, but it was still at a low level compared with March and April.
Although the TVL in January was at the highest level in half a year, the activity of hackers was relatively low. By comparing the data in January 2021, we found that the loss due to hacking activities in January 2021 was about 250,000 US dollars, which was also relatively low for the whole year. Therefore, the reason for the low hacker activity in January 2022 may be that January is the off-season for hacking activities.
image description
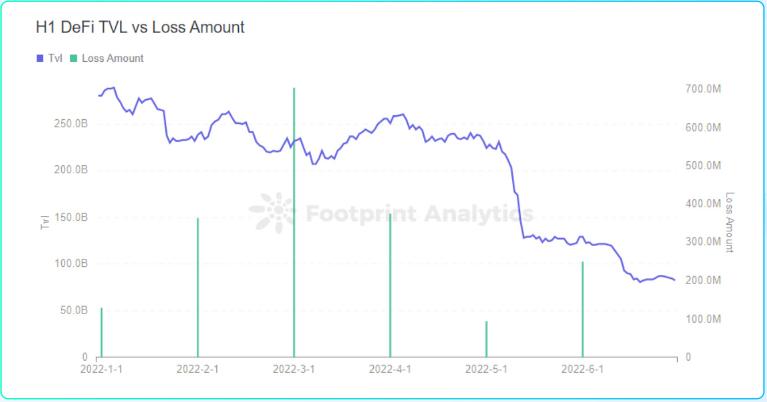
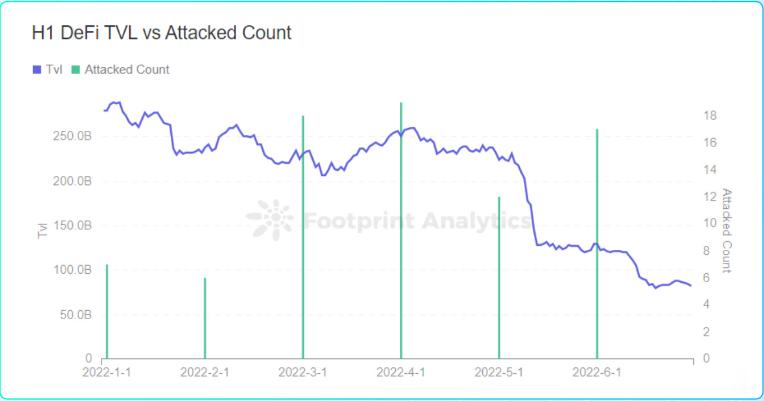
Footprint Analytics - The number of DeFi attacks and TVL trends in the first half of the year
image description
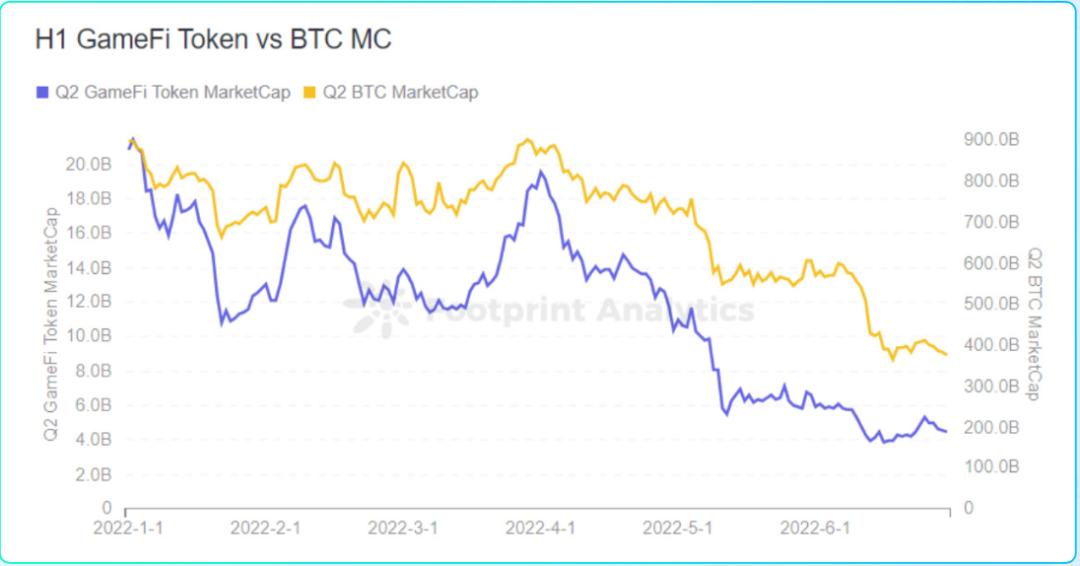
Footprint Analytics - Market value trend of GameFi and BTC in the first half of the year
Data six
Hackers Laundered $1.140.7 Million Through Tornado Cash
image description
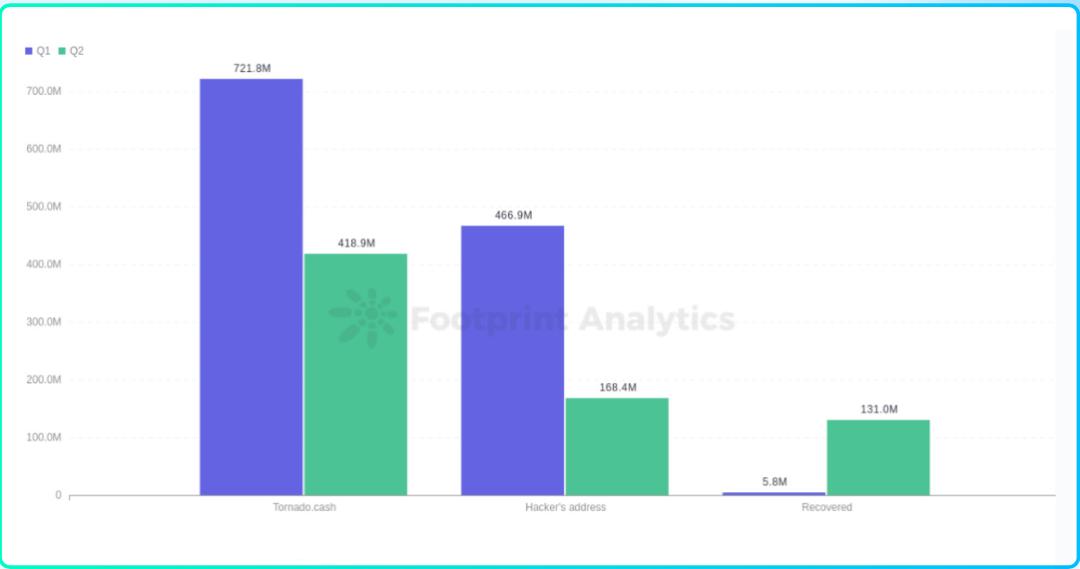
Footprint Analytics - H1 Stolen Funds Flow
Statistics show that in the first half of 2022, a total of 95,000 Ethereum (approximately US$2.34 billion) were deposited into Tornado Cash. In other words, at least 48.7% of the funds deposited in Tornado Cash came from hackers. This is assuming the remaining owners use Tornado Cash as a transaction privacy tool. In fact, a considerable number of people use Tornado Cash to conduct cryptocurrency criminal transactions, such data is not within the scope of this report.
Although currency mixing technology enhances the anonymity and privacy of transactions on the chain, it is also abused for crimes such as money laundering. The currency mixing technology increases the difficulty of tracking criminal assets on the chain. However, when hackers use Tornado Cash for money laundering, some data traces will also be exposed. Through the amount aggregation of all the addresses and amounts transferred to Tornado by hackers, and the amount aggregation of all destination addresses and amounts transferred out of Tornado Cash per unit time, the amount of mixed currency recharge and the amount of mixed currency withdrawn are associated Matching, so as to achieve the tracking of illegal funds by associating the hacker's gold deposit address with the gold withdrawal address.
At the same time, Chengdu Lianan is committed to the whole chain of combating virtual currency crime capacity building system, providing the whole chain of services + products to combat virtual currency crime, has experience in virtual currency anti-money laundering and supervision, and has assisted law enforcement agencies to complete several cases of entering Tornado Cash Case technical support.
Data seven
About 71% of attacks occurred in the DeFi field
image description
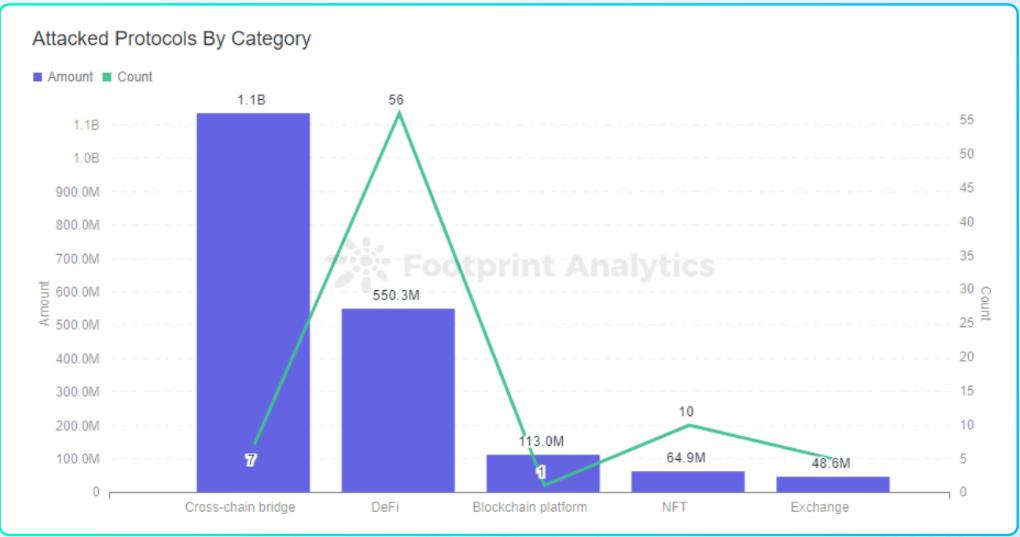
Footprint Analytics - Attacked project classification and loss amount
So, why has DeFi become the hardest hit area for hackers in the web3.0 world?
First, DeFi is highly active. As the hottest field of blockchain, DeFi has attracted much attention since its birth. The higher the activity, the more participating projects and users, and the easier it is to be targeted by hackers.
image description
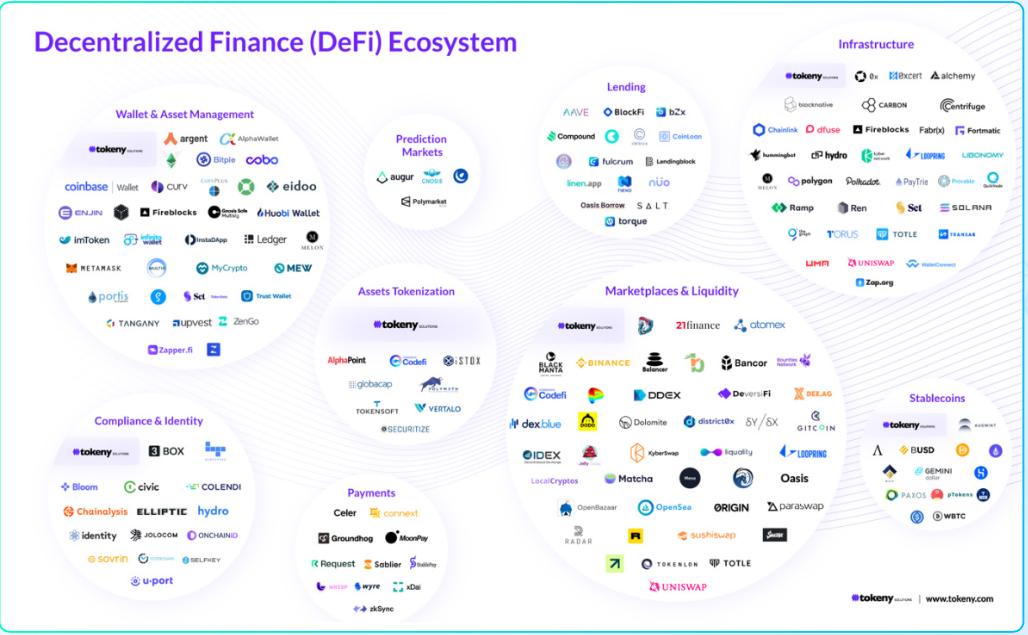
DeFi Ecosystem
Third, the business logic of DeFi is complex. Today, the DeFi ecosystem is getting bigger and bigger, and its business complexity is getting higher and higher. And because of the strong composability among DeFi products, this has led to liquidity and asset sharing among different DeFi products. Therefore, the complexity of DeFi business logic, coupled with the combination and interaction between products, is likely to lead to some security issues, which will be seized by hackers.
image description
Comprehensive external security audits, codes that comply with security specifications, and simulation tests in a test network environment are the best implementations to ensure the security of DeFi projects.
For the code-level technical specification issues mentioned above, if the third-party security audit is accepted before the project goes online, the problem can be killed in the bud. Perhaps it is precisely because of this consideration that many DeFi projects have gradually begun to realize the importance of security audits, and choose highly qualified security companies to perform them.
Data Eight
There were 10 major security incidents in the NFT field, with a loss of approximately US$64.9 million;
image description
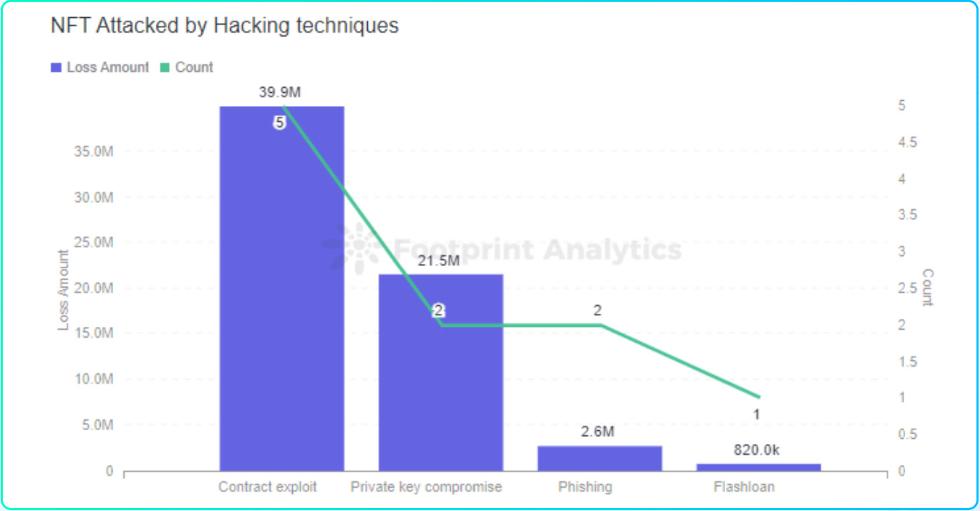
Footprint Analytics - NFT attack loss (by attack method)
NFT contract security
In the first half of the year, there were a number of security incidents related to NFT contracts. The main reason was that no comprehensive security audit was conducted. So what common problems will arise in the audit process of NFT contracts?
When auditing NFT series contracts, the Chengdu Lianan audit team found that the main problems of NFT contracts include the following categories:
(1) Signature counterfeiting and reuse:
Signature data lacks repeated execution verification (for example: lack of user nonce), resulting in the possibility of reusing signature data to mint NFT;
The signature check is unreasonable (for example: the signer is not checked for zero address), so that any user can pass the check to mint coins;
(2) Logical loopholes:
Contract administrators can mint coins through special methods such as private placement without being limited by the total amount, resulting in the actual amount of NFT exceeding expectations;
When auctioning NFT, the winner can rely on the attack in the order of receiving transactions to modify the auction price, so that the winner of the auction can obtain NFT at a low price;
(3) ERC721&ERC1155 re-entry attack
When the contract uses the transfer notification function (onERC721Received function), the NFT contract will actively send a call to the target contract of the transfer, which may lead to re-entry attacks;
(4) The scope of authorization is too large
Users only need to authorize a single token when staking or auctioning, but the contract requires _operatorApprovals authorization. Once the user authorizes successfully, there is a risk of NFT being stolen.
(5) Price manipulation
The price of NFT depends on the amount of tokens held in a certain contract, causing attackers to use flash loans to raise the price of tokens, causing the pledged NFTs to be abnormally liquidated.
Judging from the NFT contract security incidents that occurred in the first half of the year, the loopholes that often appear in the audit process will also be exploited by hackers in practice. Therefore, it is also necessary to seek professional security companies to audit NFT contracts.
wallet security
fishing
fishing
The current phishing methods usually trick users into authorizing the wallet in various ways, thereby endangering the security of the wallet. The following are some common phishing methods:
fake airdrop
This type of phishing website mainly uses methods such as fake airdrops to trick users into visiting phishing websites. After the user connects to the wallet, a button such as "CLAIM NOW" will appear to entice the user to click. After the user clicks, the black address of the phishing website will be authorized.
Trick users into filling in mnemonic phrases
This type of phishing website mainly tricks users into clicking on the web page connected to the wallet or other places, and then pops up a fake web page, prompting the user with information such as "The MetaMask plug-in version needs to be upgraded". If the user believes and fills in his wallet mnemonic, the user's private key will be uploaded to the attacker's server and the user's wallet will be stolen.
APP fake wallet
This type of fake APP wallet usually tricks users into downloading in the following three ways. The first way is to trick users into visiting the fake official website of the wallet to download by purchasing an advertising space on a search engine; the second way is to send emails and posters to victims. etc., to lure users to download fake wallets; the third way is to use social workers to first gain the trust of victims, and then trick them into downloading fake APP wallets.
DiscordFishing
secondary title
How to effectively prevent phishing attacks?
Anti-phishing plugin
epilogue
epilogue
Judging from the market trend of the entire cryptocurrency market in the first half of the year, the general trend of the development of major tracks such as DeFi, NFT, and GameFi continues to decline. The total lock-up volume of DeFi dropped from US$279.8 billion at the beginning of January to US$82.4 billion at the end of June, a drop of 70.5% in half a year. The analysis found that there is a certain correlation between the frequency of hacker attacks and market trends. With TVL shrinking sharply in May and June, hacking incidents have decreased compared to previous months, and more funds on the chain will attract more hackers.
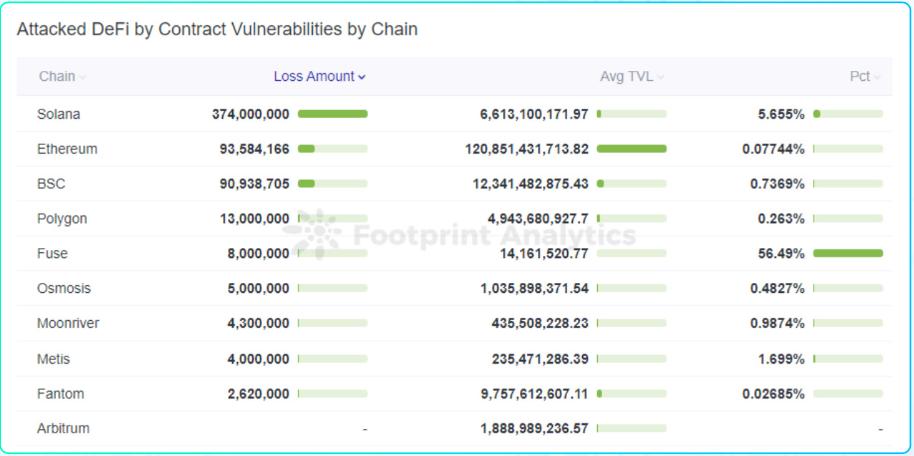
In the first half of the year, there were 7 cross-chain bridge attacks, with a total loss of 1.13599 billion US dollars. The attack methods of the cross-chain bridge are mainly contract vulnerability exploitation, private key leakage and offline program defects. For the project side, security audits, offline risk control, regular inspection of signature servers, strict review of signers, re-evaluation of security when versions are updated, and formulation of bug bounty programs are all effective means to ensure the safe operation of cross-chain bridge projects .
Among the attack incidents in the first half of the year, about 53% of the attack methods were exploiting contract vulnerabilities. By comparing the common vulnerabilities in the audit process with the actual exploited vulnerabilities, it can be found that most of the vulnerabilities can be detected during the audit stage, such as logic vulnerabilities and reentrancy vulnerabilities.
In addition, 26.6% of flash loan attacks caused a loss of 332.91 million US dollars. In addition to adopting some measures such as time-weighted average pricing (TWAP), higher frequency price update mechanism, and stricter governance logic, etc., There are also tools to monitor flash loans in real time.
In the first half of the year, there were 5 security incidents with a loss of more than 100 million yuan. The good news is that these 5 attacked projects all issued remedial measures after a period of time and went online again. In the past incidents, on the contrary, some small and medium-sized project parties with a large amount of funds will find it difficult to restart after a major attack.
In the first half of 2022, about $1.1407 billion in stolen funds were transferred to Tornado Cash by hackers, accounting for about 60% of the total loss. Although currency mixing technology enhances the anonymity and privacy of on-chain transactions, it is also abused by hackers for crimes such as money laundering. In past cases, Chengdu Lianan has successfully analyzed hacker data traces and tracked Tornado Cash several times. As of the time of publication of the report, the U.S. Treasury Department has announced that it willTornado Cashincluded in the sanction list.
As a world-leading blockchain security company dedicated to the construction of blockchain security ecology, and also the first company to apply formal verification technology to blockchain security, Chengdu Lianan has established partnerships with leading blockchain companies at home and abroad. In-depth cooperation; provided security audit and defense deployment services for more than 2,000 smart contracts, more than 100 blockchain platforms and landing application systems around the world. The self-developed "Lianbian" one-stop blockchain security service platform can provide security audit, security protection, security supervision, security warning, security consulting and other full life cycle for law enforcement regulatory agencies, financial institutions, blockchain enterprises, etc. Security solutions.
Footprint Analytics is a tool for discovering and visualizing blockchain data, covering relevant data in fields such as NFT and GameFi. So far, Footprint has collected, analyzed and cleaned up the data of 17 public chains, and built a no-code drag-and-drop dashboard for users. At the same time, Footprint also supports the use of SQL and Python for data analysis.
Twitter: https://twitter.com/Footprint_Data



