
Over the past few months, a phishing kit known colloquially as the Monkey Drainer has become a favorite of fraudsters.
Malicious vendors sell such kits to would-be fraudsters trying to steal user funds. Monkey Drainer and similar phishing tools exploit aIce PhishingThe technology is used to deceive users, inducing victims to give fraudsters unlimited permissions to spend their account assets.
In November 2022, an Ice Phishing incident led us to the discovery of wallets used by two fraudsters, Zentoh and Kai, involved in the Monkey Drainer scam.
Our investigation has established with a high degree of confidence that Zentoh and Kai are behind the fake Porsche non-fungible token website.
Process details
image description
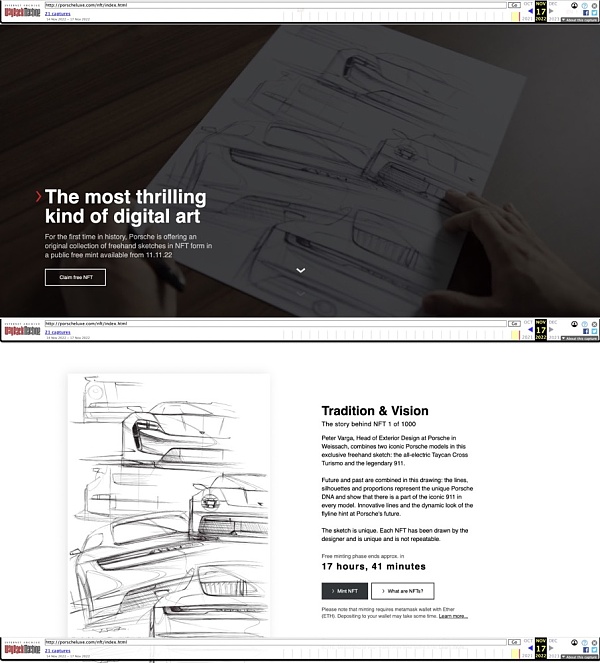
Source: Porsche Monkey Drainer website
The site is now inaccessible, but it was hyped on social media by various Twitter users and bots. Looks like maybe @BrieflyCrypto shared this scam site with his followers.
A victim using the Ethereum Name Service (ENS) responded to a now-deleted tweet by @BrieflyCrypto, claiming that a website shared by @BrieflyCrypto was claiming to use users' WBTC. Although users said they had "rejected" the transaction, they appear to have fallen victim to the scam as seen in the image below.
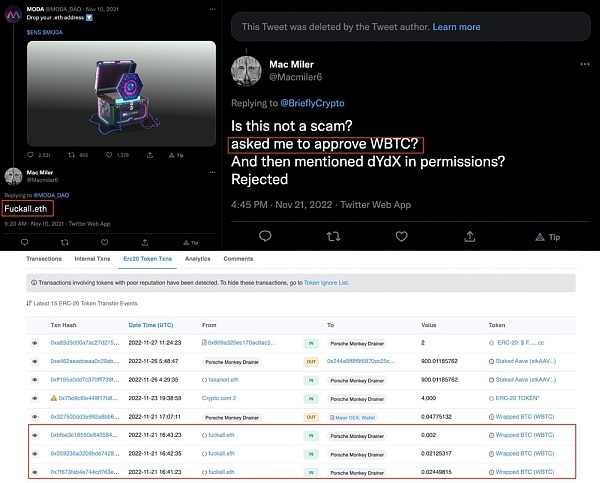
image description
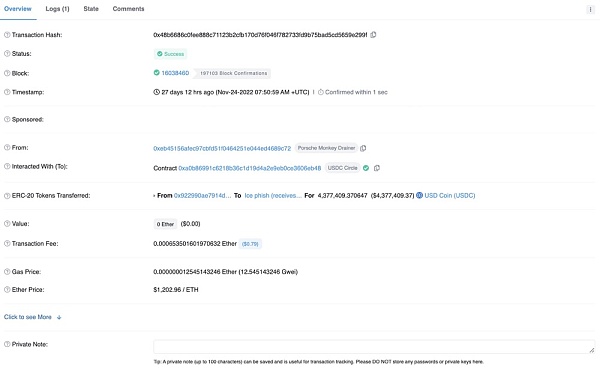
Source: Etherscan
image description
Source: Etherscan
image description
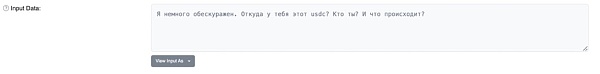
Source: Etherscan
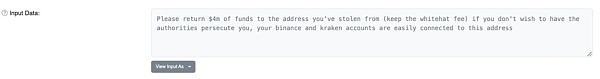
Translated by Google, the information is roughly as follows:
"I'm a bit lost, where did you get this USDC? Who are you? What happened?"
The victim tried to contact the fraudster again, but never heard back.
Zentoh and Kai are two great dramas
image description
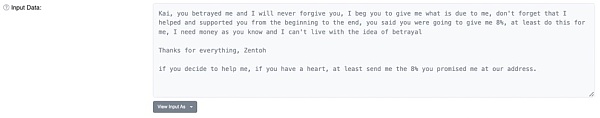
Source: Etherscan
From this information, it looks like a dog-eat-dog thing happened, with a fraudster moving $4.3 million worth of stolen coins into wallets that the self-proclaimed Zentoh crooks had no control over.
image description
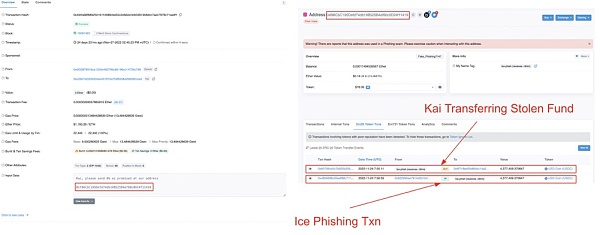
Source: Etherscan
image description

Source: Etherscan
It is rare for fraudsters to "possess their bodies" through messages on the chain, so how did they coordinate and communicate normally before this? (Arranging scripts in advance, etc.) The answer seems to be Telegram.
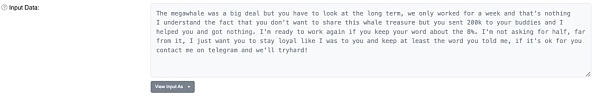
first level title
💻 Zentoh
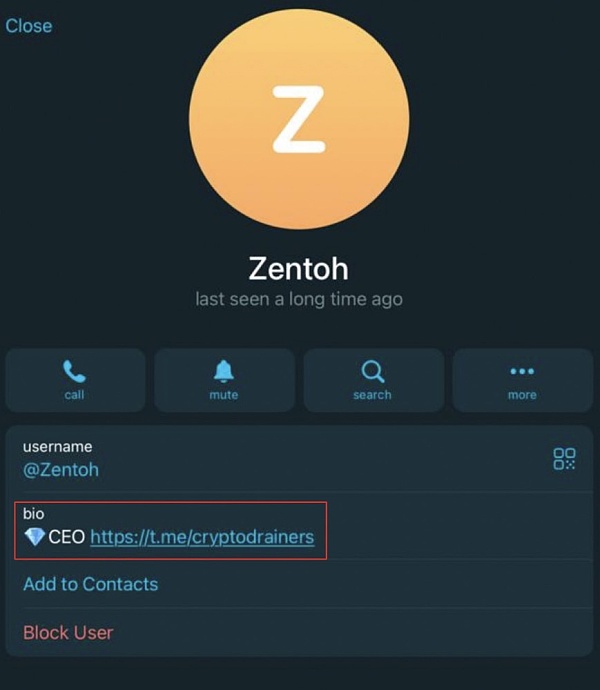
Since the fraudster used the name "Zentoh" and we noticed that Kai was able to communicate on Telegram, it is speculated that Zentoh is most likely the username of the fraudster's Telegram account.
When we searched for Zentoh, we found an exact match.
The account has been identified as running a Telegram group that is selling phishing kits to crooks.
In a thread on a Crypto Drainers Telegram channel, a video tutorial on how the wallet drainer works was posted. The tutorial lists wallets 0x4E0...13cD8.
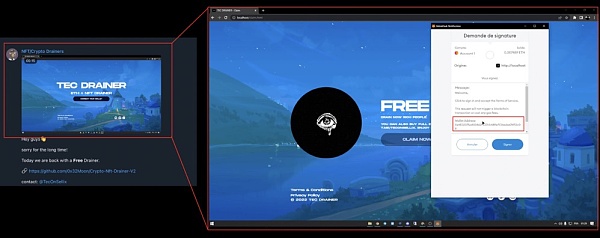
image description
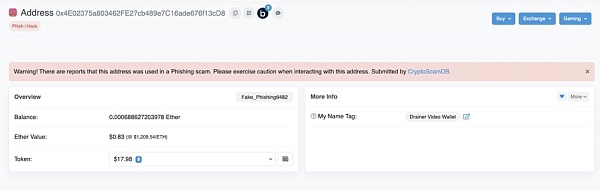
Wallet used in the drainer demo (Source: Etherscan)
first level title
💻 Link to monkey-drainer.eth
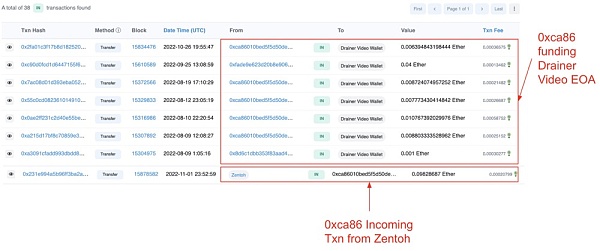
There is a direct link between the wallets controlled by Zentoh and Kai and the most recent and most popular Monkey Drainer scam wallets.
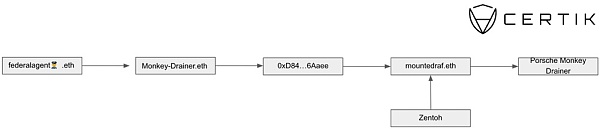
For example, Zentoh funds the EOA directly through ENS mounteddraf.eth, which also previously held ENS ZachXBT-fan.eth.
The wallet funding mounteddraf.eth interacts with 0x D 84...6 Aaee, which receives funds from the wallet holding ENS federalagent.eth, which in turn sends funds to monkey-drainer.eth.
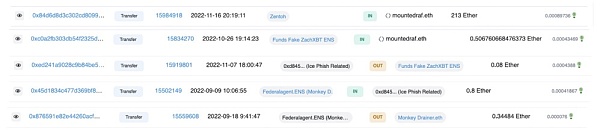
On-chain sleuth ZachXBT analyzed the monkey-drainer.eth and federalagent.eth wallets in his original thread on the Monkey Drainer scam.
The following figure is a simplified process:
Connect with TecOnSellix
Telegram user TecOnSellix was identified as the seller of the Monkey Drainer phishing kit on Twitter by security researcher @PhantomXSec, who is also a contact for the aforementioned Crypto Drainers Telegram.
In addition, TecOnSellix is listed as the owner of the Telegram channel Crypto Drainers, but according to Zentoh, he is also the CEO of the channel - so TecOnSellix and Zentoh may also be the same person, and 0x 32 Moon may also be one of them. .
When searching for "TecOnSellix" on GitHub, we saw multiple accounts posting encrypted drainer repositories, one in particular stood out: Berrich 36.
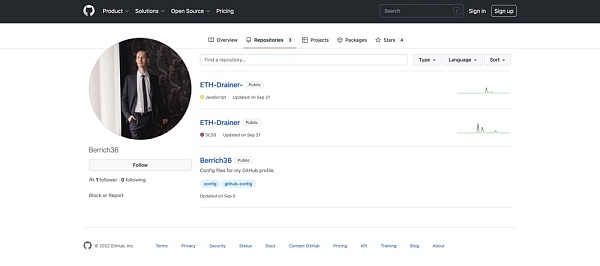
We have identified a number of accounts attributed to GitHub user "Berrich 36".
If the links between these accounts are legitimate and not intentionally misleading, Berrich 36’s true identity is that of a French national living in Russia.
Berrich 36 published a Telegram channel called "XXX Crypto FXXX" in one of the repositories.
When we search for members of this channel, we see that Zentoh has joined this group.
Below is another Telegram channel that sells the Monkey Drainer tool.
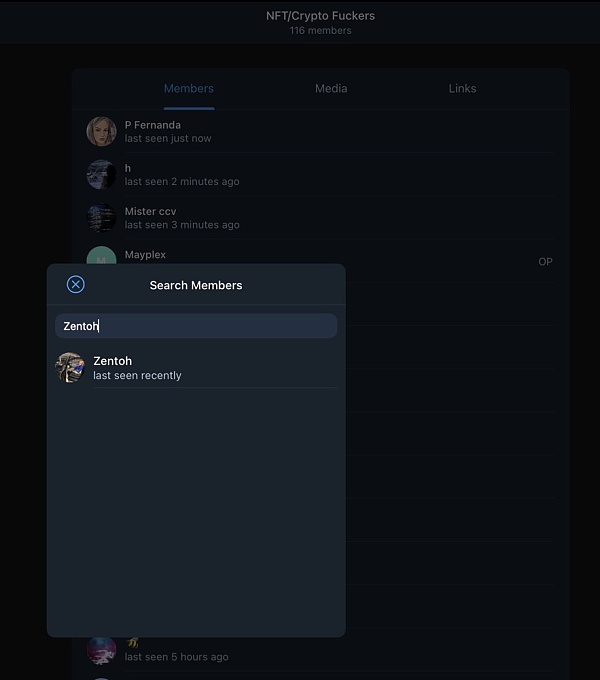
The Telegram channel links to another group that promotes a website where scammers can buy wallet drainers.
The Monkey Drainer phishing scam remains an ongoing threat to the Web 3.0 community.
Here CertiK recommends that you may wish to read【Loot millions of dollars, be wary of the upgraded version of Web3.0 unique phishing attack: Ice Phishingwrite at the end
write at the end
Several recent Discord incidents have been directly related to the Monkey Drainer wallet: Attacks on Yaypegs, Cetus, Sui Name Service, and Tsunami Finance Discord servers were linked to wallet 0x0000098a31...f4582, which in turn was linked to the Monkey Drainer scam wallet .
On January 21, 2023, CertiK alerted the community that 520 ETH (approximately $859,000) had been deposited into Tornado Cash from a wallet associated with the Monkey Drainer phishing campaign.
Scary enough, the Monkey Drainer Telegram channel continues to advertise the drainer's success in order to attract more fraudsters.
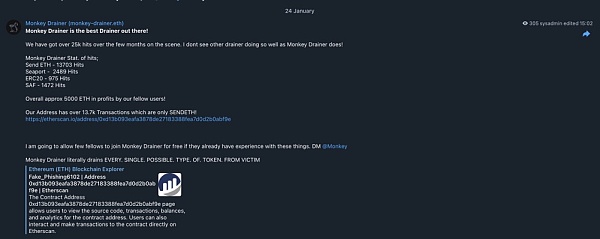
We have proven that Zentoh is a key member of the group that launched the wallet drainer tool.
These phishing kits make it fairly easy for malicious actors to steal assets from the Web 3.0 community. However, according to the on-chain information exchanged between Zentoh and Kai, when they transferred the stolen $4.3 million to their own wallets, it is likely that Kai was only a part of the Monkey Drainer scam. "Newbie".
Therefore, investors and users should be 200% vigilant against potential phishing scams. Don’t think that only skilled hackers can defraud you of your money, and don’t take chances and think that this kind of thing won’t happen. on himself.



