深入与解读Vitalik默克尔树的改进方案和对CEX发展的影响
FTX的暴雷给原本就日渐冷清的加密市场再泼了一盆冷水。用户对中心化交易所的信任程度迅速降低,提币运动此起彼伏。为留住用户和资金,CEX 们纷纷发布储备金证明,以自证清白。Vitalik也发文讨论了偿付能力证明,从技术角度解答和展望了如何实现更安全的 CEX。本文将结合对 Vitalik 文章的解读、各家 CEX 的证明方案和各方提议,讨论 CEX 如何自证清白并继续发展。
1. 用技术手段证明偿付能力
证明 CEX 拥有偿付用户取款的能力就基本上等同于证明了它没有挪用用户的存款。这需要证明一个不等式:CEX 控制的资产总和(资产证明)>=所用用户存款总和(负债证明)。除了公布这两个数值以外,CEX 还需要证明不等式的左右两边的数字都是真实的,即资产属于且一直属于交易所,它没有篡改用户的存款余额。
各类技术手段都围绕着证明这两点而开展。对于资产证明,中心化机构需要提供其持有的链上地址,并对其进行验证和审计。常见的做法是提供数字签名以证明其对链上地址的所有权。这个做法难度不大,被普遍采用。当前的讨论集中在负债证明上,各家交易所近期纷纷公布的默克尔树 Merkle Tree 资产储备证明就是最典型的负债证明。
1.1 将默克尔树用于负债证明
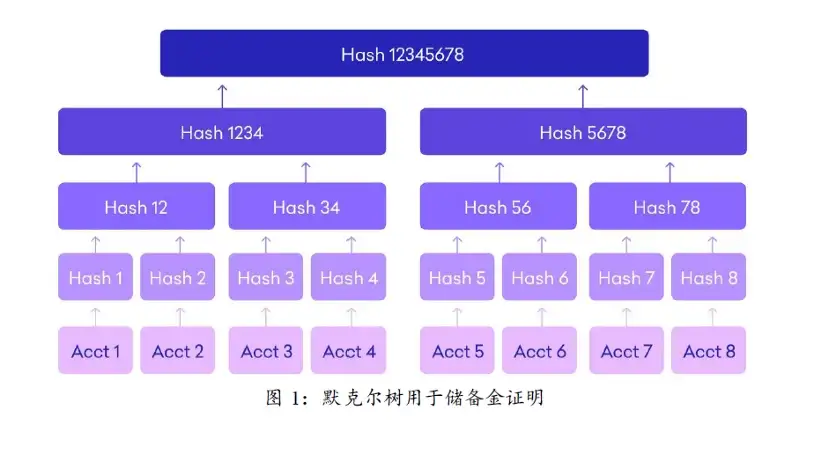
默克尔树是区块链中非常常见的数据结构。它是一种典型的二叉树结构,由一个根节点、一组中间节点和一组叶子节点组成。默克尔树的每个更高一级的中间节点(父节点)都是它下方的两个中间节点(子节点)的哈希,经过这样的逐层计算得到最后的根节点。所以根节点包含了所有叶子节点的信息。底层数据的任何变动,都会传递到其父节点,并逐层传递到根节点。它常用来快速证明某个集合中存在或者不存在某个特定的元素、比较大量数据是否完全相同、寻找修改位置等。
CEX 使用默克尔树建立用户账户资产余额的匿名化且不可篡改的集体快照,从而证明它们没有篡改用户的余额。最基本的方法就是把每个用户的用户名/UID(添加一个只有交易所和用户知道的数字后做哈希计算)与它的余额一起做哈希计算并作为叶子节点从而构成默克尔树。如果用户发现用自己的余额和默克尔树上的路径无法计算出正确的默克尔根,即可判定交易所挪用用户资产。
不过正如 Vitalik 所言,一般的默克尔树有个小 Bug。因其不能帮助用户识别负值,所以不能直接用于储备金证明。如下图所示,如果一个交易所的客户存款总数是 1390 枚ETH,但是它挪用了 500 枚 ETH,所以它的储备只有 890 枚 ETH。这个 CEX 会对外宣称用户存款总数是 890 枚 ETH。为了掩盖挪用用户资产的行为,它可以在树的某个位置上添加一个由它本身控制的假账户,账户余额为-500 ETH。经过哈希计算后,不管是正数还是负数都会出现一串很没有规律的数字,其他用户无法分辨。利用这个假账户得到的默克尔树会完美包含其他用户的余额信息,导致用户验证的结果总是正确。审计公司可以发现这个漏洞,但若是它与交易所联合作恶,默克尔树将形同虚设。
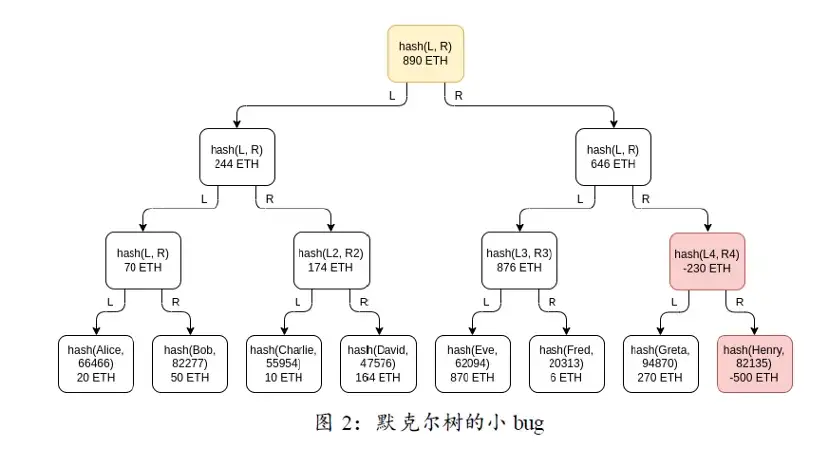
针对负值问题,Vitalik 在文中提出了名为默克尔总和树(Merkle sum tree)的改进方案。默克尔总和树的每个节点都包含余额和哈希这 2 个信息。底层叶子节点是各个用户的余额和用户名哈希。在每个较高层节点中,余额是下面两个节点余额的和,而哈希值是下面两个节点整体信息的哈希,即对这两个节点的余额和哈希值一起做哈希运算。将余额单独显示出来,有助于用户识别负值,从而暴露 CEX 挪用用户资产的行为。如上图所示,Greta 在做自行验证时,会发现 Henny 的余额为负;Eve 和 Fred 都会发现 Greta 和 Henny 余额的总和为负。这会导致他们 3 人验证不通过。
经过改造后,交易所使用默克尔树发布储备证明的过程如下。
● 生成默克尔树证明:交易所委托外部审计公司或由其本身对所有用户余额进行快照,然后将其汇总至默克尔总和树。
● 验证:审计师对比并核实交易所控制的余额是否大于等于默克尔树所提供的数目。由此证明客户的资产是否有全额准备金所支持。用户可自行核对,若用户的用户名和余额数值在默克尔树中,且计算过程中未出现负余额,则证明交易所没有篡改用户余额,也就是没有挪用用户资产。
1.2 默克尔树的改进方案
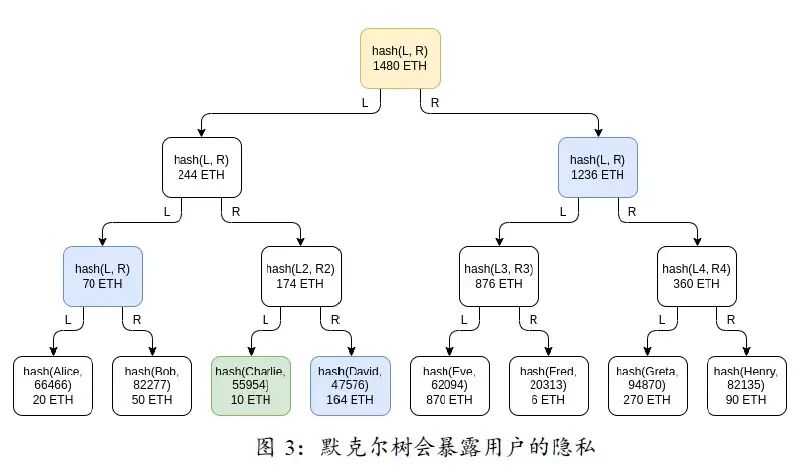
用默克尔树证明用户余额仍然有一个小小的缺点,那就是会暴露隐私。如下图所示,Charlie 自行验证时,CEX 必须告诉他 David 的余额、Alice 与 Bob 余额之和、树的右半边所有用户余额之和。尽管用户得知了这些信息后也不会(至少目前看来是不会)做出有危害性的行为,但是对于交易所和被暴露余额的用户来说,隐私的泄露总不是一件让人舒服的事。
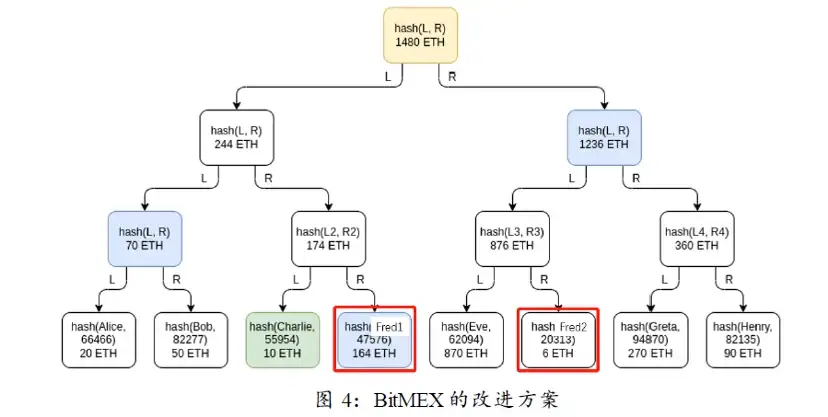
针对这个问题,BitMEX提出了一种简便的解决方法。他们将一位用户的账户余额随机拆分成几份,再把每一份都随机填入 Merkle 树的一个底层叶子节点。这样暴露出来的用户的余额都只是碎片化的,可以在一定程度上缓解隐私问题。比如图中的 Fred,他的账户被拆分成 2 个部分,Charlie 不知道他到底有多少存款。只是如果真有人想通过多个账号来获取他人信息,他需要付出更多的努力,但还是能做到。
要想完全解决隐私问题,可以引入 ZK-SNARK。正如V神文章里提到的,用所有用户的余额生成默克尔树,使用 ZK-SNARK 来证明树中的所有余额都是非负的,并且加起来是某个声称的值。如果我们使用哈希来加强隐私,那么给每个用户的默克尔树路径将不会透露任何其他用户的余额。或者是用所有用户的哈希用户名和余额建立一个多项式,并对其做出 KZG 多项式承诺。交易所证明它知道这个多项式。用户验证的方法是以他的余额作为多项式上的一个点,让交易所计算多项式在此处的取值,并以此生成一个见证,用户验证承诺、取值和见证之间的对应关系。在 KZG 承诺中,多项式、承诺、见证都有对应关系,不能任意伪造,这一点和默克尔树一样。它不需要提供“姐妹节点”作为证明的依据,可以在不泄露隐私的情况下完成证明。
1.3 各类方案的总结和不足
这里先对基本默克尔总和树、BitMEX 方案、ZK-SNARK 默克尔树、KZG 多项式承诺做出总结和比较,如下表所示。前两种方法操作简单,尽管有隐私暴露的风险,但在目前看来没有重大隐患,已经足够应用在实际中。后两种方法中要使用 ZK-SNARK 证明加法计算,这会给交易所带来额外的操作,所以增加了操作的成本。KZG 多项式承诺的方法更高级,但是交易所计算承诺的过程资源消耗大,涉及大量椭圆曲线点运算,所以可能暂时还不会获得采用。以上所有方法用户都不需要有搜索操作,且都容易验证。
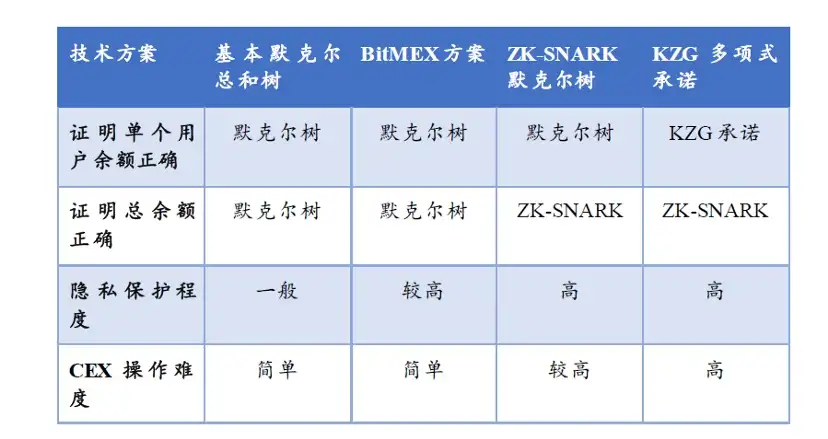
这些负债证明的技术方案与较为普遍采用资产证明方案,都还没有解决以下几个问题:
第一,这些负债证明方案都需要用户来监督,但如果自行验证的用户太少,不足以检查出交易所的作恶行为。需要持续教育用户,提高用户的自觉性。另一种方法是由交易所之间互相监督。大型交易所可在其他交易所注册一定数量的账户,存放少量资产以验证其负债证明。
第二,资产证明和负债证明都不是实时的证明,交易所完全可以在做资产证明之前通过借贷的方式获得资金,应付检查,随后再归还。解决这个问题有两种方法,其一是可以约定一个固定时间,各大交易所同时进行审计;其二是可以进行不定期的突然审计。这两种方法都可以压缩资金拆借的时间。
第三,证明的过程依赖值得信任的审计公司,但如果审计公司与交易所勾结,其后所有技术手段都会失效。
第四,这一点是最关键的,这些方案都没有强制的约束力。交易所可以在资不抵债的状态下运行。尤其在熊市中,如果短期的经济压力大到了让交易所撑不到下一个牛市,挪用用户资金就成了自然而然的举措。
2. 半中心化的 CEX
前文说到的各种证明,都是用于证明 CEX 没有作恶,但是 CEX 仍然拥有作恶的能力。如果我们更进一步,用技术的约束让交易所从没有作恶变成无法作恶,那么用户的信任就会恢复,甚至是增强,加密生态圈也会更繁荣。
Vitalik 按照对用户资金的控制程度和作恶的便利程度将交易所分为 5 类。当前交易所主要是其中的 3 类。下图左起第 1 类交易所完全控制用户的资金,没有措施监督和阻止它挪用用户资金。在 FTX 暴雷之前,几乎所有 CEX 都是这样的。现在大多数 CEX 是第 2 类,交易所控制用户的资金,但有外部的人为控制措施来监督。大多数DEX属于第 5 类,交易所完全不控制用户的资金,所以也就没有能力作恶。
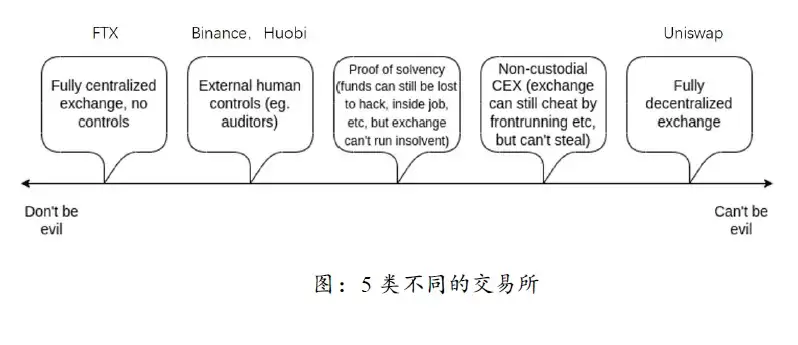
V神指出 CEX 与 DEX 不是二元对立的,在完全的中心化和完全的去中心化之间,存在半中心化 CEX 的中间地带。它们可以继承传统中心化交易所高效率的交易系统,并由如多重签名私钥持有者、验证者等分散交易所的权力,从而降低交易所作恶的可能性。它们就是V神文章里的第 3 类和第 4 类交易所。
第 3 类交易所仍然托管用户的资金,但是它不能在资不抵债的情况下运行。此类交易所尚未出现。如果要实现,需要对它进行一些限制。这里做出一点畅想,可以要求 CEX 将资产存放在几个固定的由多重签名控制的地址上,或者用 MPC 技术将私钥拆分为几份。通过实时或高频率偿付能力检测来监控交易所资金状态。常规情况下只需要 CEX 本身控制的私钥完成签名即可调动资金。若检测出资不抵债/单笔转出比例过高/连续转出等情况,其他私钥持有者可以启动紧急模式并集体拒绝交易,以达到冻结账户的效果。这种方式是用多个私钥持有者来降低了 CEX 的中心化程度,从而降低其作恶的便捷性。这类交易所可能是未来 CEX 的演进方向。
此类交易所若要继续发展,还需要审计工作再上一个台阶。未来审计的可信度、速度和自动化程度都需要提高,才能承接住这些交易所的需求。
第 4 类交易所就不托管用户的资金了,只是使用中心化的交易系统。用户的资金托管在智能合约中。DYDX 可以视为这类交易所的代表。它利用自己的交易系统在链下撮合交易,将交易结果压缩打包后提交到以太坊主网上。它即利用了中心化交易系统的便利性,又获得了以太坊这个结算层的安全性。现在它的 V 4 版本迁移到了Cosmos生态上,其底层是专为它量身打造的区块链,但中心化交易+去中心化结算的范式没有改变。这一类交易所需要有低成本高安全性的底层区块链作为保障,且在处理跨链问题上不如一般的 CEX 方便,故不太可能成为 CEX 的演进方向。
3. 借鉴传统金融
正如 X Research DAO的分析师 Wilson 在文中所言,现阶段的中心化加密货币交易所存在着内部权限过大、资产保管不透明、收益放大冲动、不受外部约束等弊病。要解决这些问题,依靠技术进步只是一条路线,另外一条路线就是建立一整套合理的制度安排来拆分和限制 CEX 的权限。
当前的加密市场很像早期金融业的混业经营阶段。CEX 是集各项金融职能于一身的综合型机构,一方面提供场内交易委托和撮合,也全权托管客户充值的各类代币资产(也包括稳定币资产),还提供各类理财服务。多种业务也意味着多种权限,而当一个机构的权力太大时,它会不会凭借此谋取私利就只在一念之间了。
下一阶段加密市场必然有构建更安全交易模式的需求,借鉴历经数十年实践验证及完善至今的证券业制度不失为一条捷径。证券行业形成了规范化的交易制度,包括:
由第三方存管机构(商业银行)存管客户的交易结算资金。
由证券登记结算机构集中提供证券的登记、托管与结算。
由证券经纪商接受客户委托并代为买卖证券证券,提供融资和融券服务。
由证券交易所完成交易信息的场内订单撮合。
证券行业通过这样一套多方协作和制衡的制度,避免了单一机构作恶造成系统性风险的局面。而以上 4 项功能,全都由 CEX 完成,这就大幅度加重了单点故障的危害性。所以有必要结合加密资产交易的特点,借鉴传统金融分业经营的模式,让多个相互独立的机构承担当前加密货币交易所的多种功能,从而实现分权和制衡。
这种借鉴绝非容易,它存在以下困难:
分业经营意味着 CEX 交出很多权限,可能会降低其盈利能力,所以 CEX 自身没有意愿这么做。
这需要监管的介入,但该如何制定规则还需探索,且出台法律法规较为耗时。
各国的监管规则可能不一致,这会不会导致加密市场的割裂尚不明确。
更多的制度约束也意味着可能会出现更高的管理成本,这些成本都会转嫁到用户身上。
不过可以确定的是,加密资产若能成为主流资产,上述转变就一定会出现。多一点耐心和自我保护措施,更规范的 CEX 正在路上。
参考资料
1. https://www.odaily.news/post/5183267
2. https://vitalik.ca/general/2022/11/19/proof_of_solvency.html
3. https://www.kraken.com/zh-cn/proof-of-reserves
4. https://www.odaily.news/newsflash/304869
5. https://www.okx.com/proof-of-reserves
7. https://blog.bitmex.com/bitmex-pol-system-now-live/
8. https://twitter.com/XResearchDAO/status/1592058023715147779
9. https://www.odaily.news/post/5183328
10. https://m.jinse.com/blockchain/2667533.html
关于火必研究院
火必区块链应用研究院(简称“火必研究院”)成立于 2016 年 4 月,于 2018 年 3 月起致力于全面拓展区块链各领域的研究与探索,以泛区块链领域为研究对象,以加速区块链技术研究开发、推动区块链行业应用落地、促进区块链行业生态优化为研究目标,主要研究内容包括区块链领域的行业趋势、技术路径、应用创新、模式探索等。本着公益、严谨、创新的原则,火必研究院将通过多种形式与政府、企业、高校等机构开展广泛而深入的合作,搭建涵盖区块链完整产业链的研究平台,为区块链产业人士提供坚实的理论基础与趋势判断,推动整个区块链行业的健康、可持续发展。
联系我们:
咨询邮箱: research@huobi.com
官方网站: https://research.huobi.com/
Twitter: Huobi_Research
https://twitter.com/Huobi_Research
Medium: Huobi Research
https://medium.com/huobi-research
Telegram: Huobi Research
https://t.me/HuobiResearchOfficial
免责声明
1. 火必区块链研究院与本报告中所涉及的项目或其他第三方不存在任何影响 报告客观性、独立性、公正性的关联关系。
2. 本报告所引用的资料及数据均来自合规渠道,资料及数据的出处皆被火必区块链研究院认为可靠,且已对其真实性、准确性及完整性进行了必要的核查,但火必区块链研究院不对其真实性、准确性或完整性做出任何保证。
3. 报告的内容仅供参考,报告中的结论和观点不构成相关数字资产的任何投资建议。火必区块链研究院不对因使用本报告内容而导致的损失承担任何责任,除非法律法规有明确规定。读者不应仅依据本报告作出投资决策,也不应依据本报告丧失独立判断的能力。
4. 本报告所载资料、意见及推测仅反映研究人员于定稿本报告当日的判断,未来基于行业变化和数据信息的更新,存在观点与判断更新的可能性。
5. 本报告版权仅为火必区块链研究院所有,如需引用本报告内容,请注明出处。 如需大幅引用请事先告知,并在允许的范围内使用。在任何情况下不得对本 报告进行任何有悖原意的引用、删节和修改。



