5 つの次元から 10 個のクロスチェーン ブリッジをスコアリングし、選択結果は次のとおりです。
この記事の由来は Decentralisedこの記事の由来は

Nomadクロスチェーンブリッジは約1億9000万ドルでハッキングされた。 Ronin のハッキングにはクロスチェーン ブリッジも関係しており、推定 7 億ドルが関与しました。明らかに、より多くの資金を投資する前に、クロスチェーンブリッジが有用で信頼できるかどうかを評価するためのより良いツールが必要です。この記事では、5 つの次元からクロスチェーン橋の信頼性スコアリングを紹介し、最後に 10 個のクロスチェーン橋のスコアリング結果を添付します。
副題
使いやすく信頼性の高いクロスチェーンブリッジを定義する
クロスチェーンブリッジの 5 つの重要な特徴をまとめました。
セキュリティ: クロスチェーンブリッジに保存されている資産のセキュリティ。
パフォーマンス: クロスチェーンブリッジ関連のトランザクションの背後にあるモデル。
抽出可能な値: Flashbot または他の仲介者がトランザクションの一部を抽出する可能性。
接続性: クロスチェーン ブリッジが接続できるネットワークの数。
私たちが知る限り、現在、デジタル資産をサポートするクロスチェーン ブリッジが 60 近くあります。専門化がさらに進むかもしれません。一部のクロスチェーン ブリッジは速度を最適化しますが、他のクロスチェーン ブリッジはサポートするさまざまな資産に焦点を当てます。この記事のスコアリングの枠組みは非常に幅広いため、お気に入りのクロスチェーン ブリッジの中には、特定の特性では最高であっても、全体としては低いランクにランクされる場合があります。読みやすいように、各セクションのパラメータを細分化し、監査人が割り当てることができる最大スコアを表形式で示しました。私たちは可能な限り定量的なフレームワークを使用することにこだわっていますが、業界の初期の性質を考慮すると、いくつかの側面は定性的です。
副題
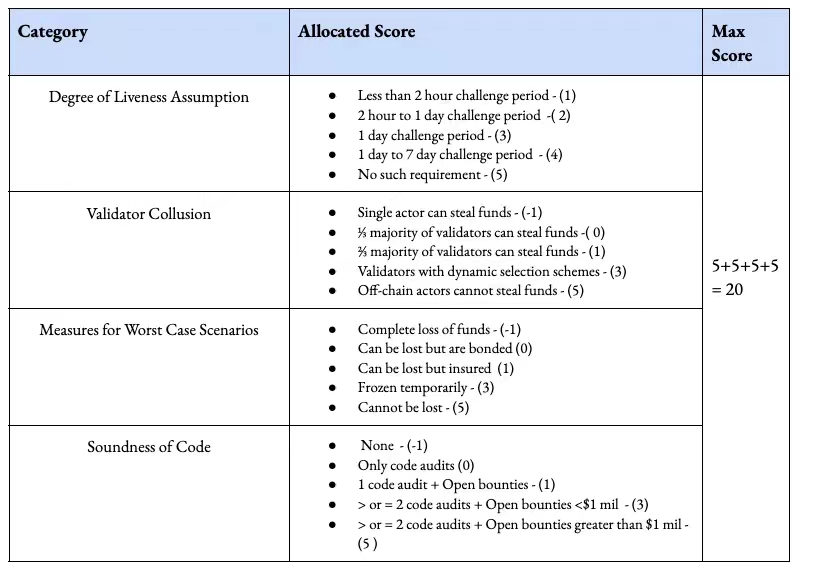
1. セキュリティ
セキュリティを 4 つの鍵に分けます。活性仮説は主に、ハッキングされる可能性のあるトランザクションに対するクロスチェーンブリッジの紛争時間を調査します。銀行に関する限り、取引を解除する必要がある前に銀行が AML/KYC 操作を実行する必要がある期間についての成文法はありません。代わりに、スマート コントラクトには事前定義されたパラメーターが必要です。
ネットワーク上のバリデーターが何か問題があると疑った場合、トランザクションが停止する可能性があることをユーザーが知っているため、紛争が長いクロスチェーンブリッジが上位にランクされます。最近、Synapse への攻撃がクロスチェーン ブリッジ上のバリデーターによって警告され、最終的にシステム全体がダウンしました。これにより、クロスチェーンブリッジは一晩で 800 万ドルの損失を回収することができました。Ronin クロスチェーン ブリッジに対する 6 億ドルを超えるハッキングは、業界最大規模のハッキングの 1 つです。それは使用することを含みます偽のオファーが上級エンジニアのコンピュータにハッキングされた、11 個の認証キーのうち 5 個をコピーしました
。理想的なクロスチェーンブリッジは、検証者がユーザーの資金を取得できないことです。私たちが使用するフレームワークは、トークンにアクセスできる個々のバリデーターはペナルティを課されるべきである一方、バリデーターのステータスはあるがユーザー資金にアクセスできないバリデーターが理想的であることを示唆しています。
クロスチェーンブリッジが実際にハッキングされた場合、チームは通常、2 つの方法のいずれかでユーザーを安心させることができます。 1 つはクロスチェーン ブリッジ (Nexus Mutual などの DeFi 保険プロジェクトを通じて保険が適用されます) を介するもので、もう 1 つはユーザーが保有する資金量に比例してクロスチェーン ブリッジ ネイティブ トークンをユーザーに発行するものです。
最後に、「セキュリティ対策」では、橋が監査された回数と、橋が侵害された可能性があることを橋に通知するハッカーの動機を観察します。監査自体にはあまり意味がありません。これが、複数の監査と報奨金の必要性を強調する理由です。 Immunefi のようなパブリック プラットフォームで提供されるバグ報奨金は、実際には、チームが独自の作成物を監査してもらうことを一般に呼びかけています。
副題
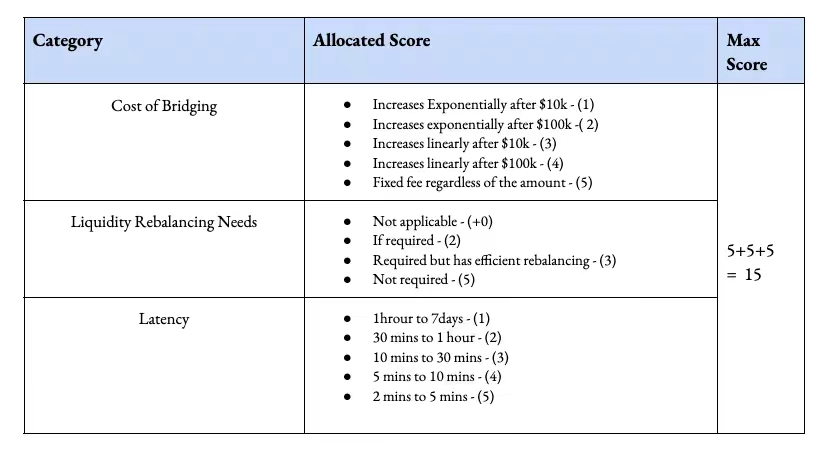
2. パフォーマンス
私たちが観察したほとんどのクロスチェーン ブリッジでは、ネットワーク間で USDC を取引するコストは固定 (約 1%) または無料です。安定した資産は、収量農業のためにチェーンをまたがって移転されることがよくあります。クロスチェーン取引所(自動マーケットメーカーが関与する)を伴う資産移転のコストは急激に増加します。これはどういう意味ですか? Optimism でイーサリアムから USDC への送金を行っているとします。支払う手数料は、関連する資産の規模に応じて急激に増加します。
リバランスを必要とせず、固定コストを提供するプールには 5 ポイントを与えますが、ジャンプ トランザクションを提供せず、10,000 ドルという低いしきい値を超えると高額な手数料を請求するクロスチェーン ブリッジには、それぞれ -1 ポイントのペナルティを与えます。ここで考慮すべきもう 1 つの要素は、クロスチェーン ブリッジに必要な時間です。鎖橋の所要時間が 1 時間を超える場合は減点され、所要時間が 1 分未満の場合は 5 点が減点されます。最後に、イーサリアムのような一部の L1 は、混雑度が高いときはブロックの確認に時間がかかるため、ここでは不利になる可能性があることに注意してください。
副題
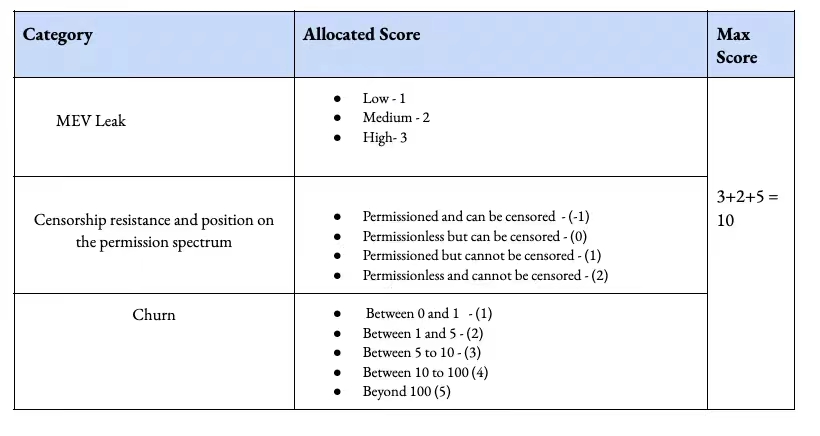
3. 抽出可能な価値 (MEV)
MEV 抽出では、エンド ユーザーのコストがさらに増加します。繰り返しになりますが、これは個人が少額の利益を得るために事前にオンチェーン取引を行うことができるという事実を指します。これまでのところ、イーサリアムベースのインデックスだけで約 1 億 8,000 万ドルが MEV 収益として引き出されています。この指標を定量化できる 1 つの方法は、クロスチェーン ブリッジ上の MEV を介して引き出した資本の量を通じて行うことです。
ただし、橋から引き上げられた MEV の数が多いということは、単に橋が使用率の高いプラットフォームであることを意味している可能性があります。したがって、クロスチェーンブリッジ取引から価値を引き出す難しさに基づいて定性的な尺度が与えられます。特に、デフォルトで MEV を持たないチェーンと対話するブリッジは、ここで上位にランクされます。高い MEV を持つチェーン上に構築されたクロスチェーン ブリッジは、Cowswap などの保護手段の使用を選択する場合があります。これが、イーサリアム上の DEX アグリゲーターの今日の動作方法です。トルネードが受けた精査のレベルにもよりますが、クロスチェーンブリッジが将来の制裁の中心になると私たちは考えています。現在、制裁は住所レベルで行われます。将来的には、ネットワーク全体、特にプライバシーとトランザクションの保護を重視したネットワークがブラックリストに登録される可能性があります。
検閲への抵抗をスケールで定量化することは困難であり (したがって、ここでのスコアは相対的なものです)、検閲を許可しない、または検閲に抵抗するクロスチェーン ブリッジの最大 2 ポイントとなります。最後に説明するのは資本の流れです。より低い資本要件に合わせて最適化されたクロスチェーンブリッジがますます多くなる可能性があります。
一方、Hyphen や Hashflow のようなクロスチェーン ブリッジは、わずか約 1,000 万の資金で数十億のクロスチェーン ジョブを実行しています。この場合、解約率は 100 を超えており、システムが遊休資本を残さずに資本を完全に使用できることを示しています。しかし、繰り返しになりますが、この指標は原始的です。なぜなら、アセットの視聴者とその需要に応じて、多くの場合、クロスチェーンブリッジがデフォルトでスラックでアセットを所有する可能性があるからです。
副題
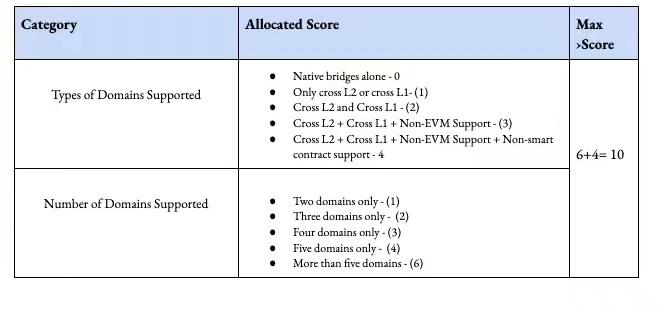
4. 接続性
接続性とは、クロスチェーン ブリッジがさまざまなネットワークと対話できる順列と組み合わせを指します。ドメインは、資産が移動する層またはネットワークです。一部のクロスチェーンブリッジは深い流動性プールを持ち、EVMベースのチェーン(ETH、Avax)のみに焦点を当てていますが、他のブリッジはチェーン幅を最適化しています。ネイティブのクロスチェーン ブリッジ (Polygon や Celo で使用されているものなど) は、一般に流動性の流入を目的としており、ユーザーの選択肢が制限されているため、最も低くランク付けされています。
クロスチェーンブリッジの初期段階では、特定の資産の大規模な移転がよく見られます。この良い例は、ビットコインからイーサリアムへのラップされたビットコインの転送です。次のステップには、Optimism などの L2 ソリューションのサポートが含まれます。 Solana、Avalance、ETH ネイティブ L2 間の資金の流れは、それらの間の資金の流れを大幅に刺激しました。多くの場合、クロスチェーン ブリッジは、プールのリバランス メカニズムに基づいて資産の移動を制限します。クロスチェーンブリッジの TVL 内の資本の量によって、資産がどのように流れるかが決まります。現在の制限要因は、EVM および階層タイプ全体でプールのバランスを再調整するために必要な労力です。理想的なクロスチェーン ブリッジは、サポートされるすべてのドメイン タイプにわたる資産の簡単なフローを即座にサポートします。
副題
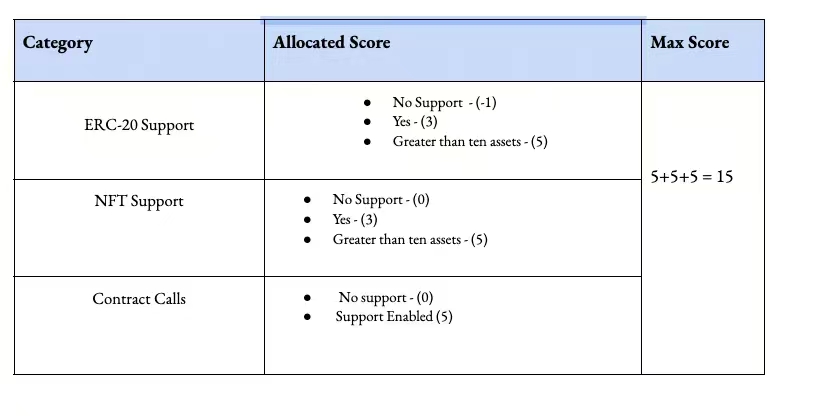
5. 能力
スコアリング システムは、サポートされているアセット タイプとアセットの数で四捨五入されます。現在、多数の DeFi および消費者アプリケーションがイーサリアム上に構築されているため、ERC-20 のサポートを強調します。ただし、サポートされるアセットの数は 10 のままです。私の意見では、これは恣意的に低い数字です。たとえば、パンケーキ スワップのような自動マーケット メーカーは、取引ペアの数万の資産をすでにサポートしています。対照的に、クロスチェーンブリッジはまだ進化の初期段階にあります。
副題
要約する
要約する
現状では、このフレームワークはクロスチェーンブリッジを評価するための理論的なアプローチです。その最大の欠点は、特定の属性が定性的であり、専門家による評価が必要であることです。スマートコントラクトの監査と同様に、個人の主観的な意見には偏りがある可能性があります。また、相対的な「集中化」とインセンティブの不整合ももたらします。理想的なクロスチェーンブリッジのスコアリングフレームワークが完成するまでに、何度も反復を繰り返す可能性があります。私は個人的には、このフレームワークをクロスチェーンブリッジの評価に使用することはお勧めしません。
代わりに、DeFi Llama や L2Beat などのスタンドアロン プラットフォームで使用されることを期待しています。ユーザーに定量的な方法で情報を提供し、クロスチェーン ブリッジをランク付けすると同時に、クロスチェーン ブリッジが欠点を見つけられるように支援し、ユーザーがより良いサービス プロバイダーを見つけるようにガイドします。
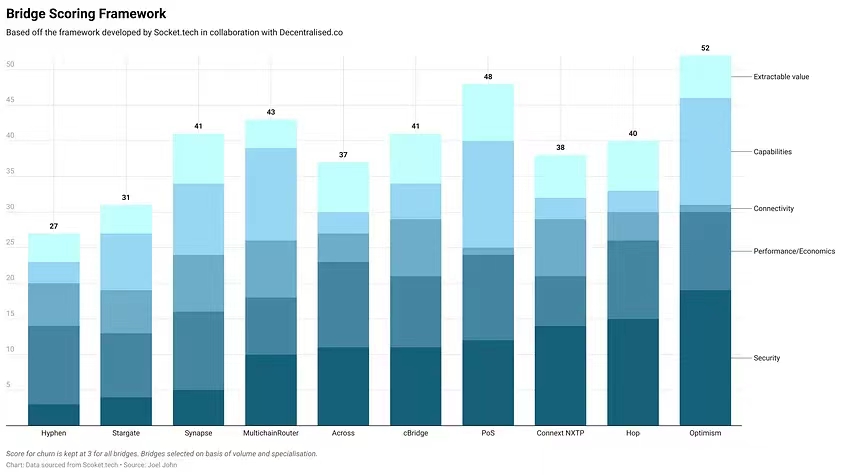
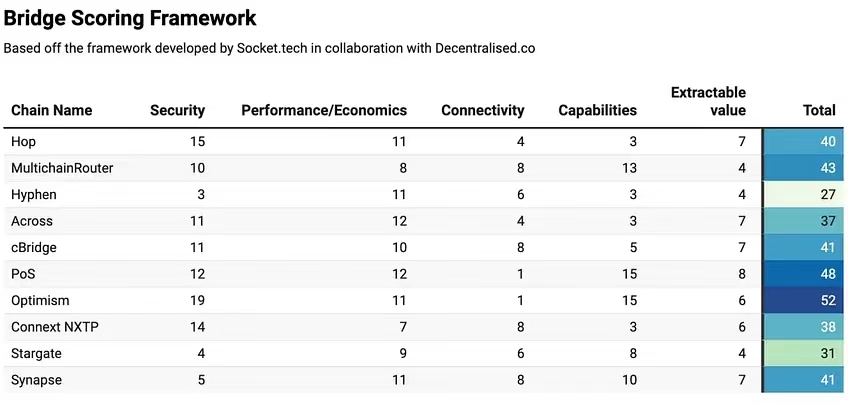
10 のクロスチェーン橋にスコアリング フレームワークを適用し、ランキングを評価しました。すべてのクロスチェーン ブリッジにチャーン スコア 3 を与えます。これは資本効率を重視する一部のクロスチェーンブリッジにとっては好ましくありませんが、すべてのクロスチェーンブリッジにはすぐに利用できるデータがないため、これを行う必要があります。私たちのフレームワークでは、想定される最大スコアは 70 です。評価した鎖橋の中で最高点は52点で、道路が障害物で長い。スコア自体はクロスチェーンブリッジの品質を定量化するものではないことに注意してください。ユーザーのユースケースとニーズに応じて、特定のクロスチェーン ブリッジがさまざまなパラメーターに合わせて最適化される場合があります。



