How did friend.tech without “innovation” create an encryption phenomenon?
How long has it been since you saw a dApp on Screen Time? Whether it is a so-called ponzi or not, friend.tech has done it.
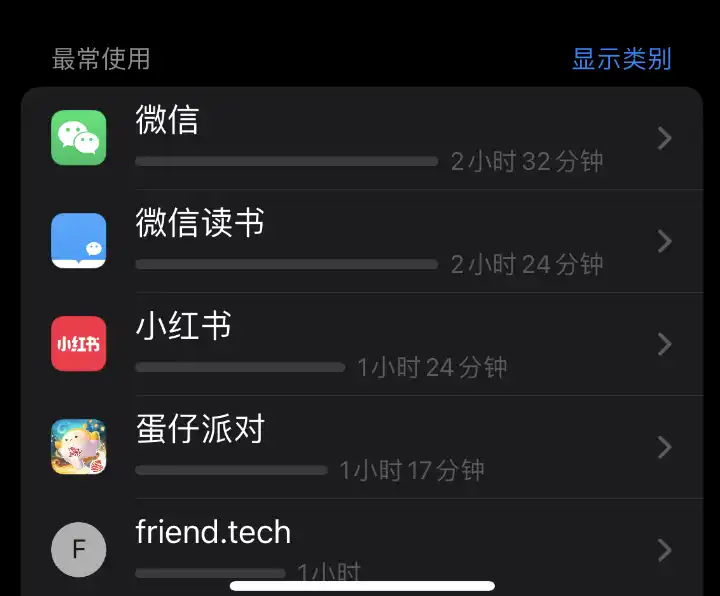
The average weekly usage time of friend.tech is 1 hour, but users more often choose to use the web version
Although some people joked about it, the most powerful thing about friend.tech (hereinafter referred to as ft) is their ability to mobilize top KOLs, which cannot be copied. The top KOLs and Paradigms golden brand in the encryption industry have indeed become the engines of fts first and second rounds of popularity, but they cannot explain the recent development trend of ft.
From the data point of view, the development of ft did not happen overnight. The cooling-off period from the end of August to the beginning of September not only kept ft away from the public eye, but also further reduced the number of speculators.
ft’s TVL and new users, data source: DefiLlama
It is the continuous product updates and iterations that have laid the foundation for fts relatively healthy growth in the near future. This round of FT expansion has also welcomed more DeFi and NFT players. There is even a slight out-of-the-circle effect, with some Youtube internet celebrities, OnlyFans managers, authors, practitioners from major Internet companies and VC groups also joining ft. Even though on September 22, ft reduced the point rewards for self-purchase users, it could not hide the popularity of the market. fts Total Value Locked (TVL) still hit a new high.
On September 28, 2023, ft products have been online for about 49 days, and the team’s fee income is approximately US$15 million.
From the perspective of social products, ft’s data is also remarkable. According to its officialpublished dataIt shows that the next-day retention rate of ft exceeds 75% and the weekly retention rate exceeds 50%, which means that the product is highly sticky and users are still using this product in large quantities. Meanwhile, the average active key holder uses FriendsTech for more than 30 minutes a day.
Although some netizens ridiculed that 27 minutes were spent refreshing the page, ft seems to have strengthened the server performance recently, and the user experience has been greatly improved compared to when it was first launched.
But for the long-term development of the entire industry, the focus is not solely on friend.tech itself, but also on its ponzi design and wealth effect. The real meaning of ft is to tell the market that with existing technology, we can build eye-catching products. Even if the product is still in its early stages, it can show the potential to become a consumer-grade product through creativity and mature operational methods.
Even if ft fails, it uses PWA technology that can bypass Apples tax, a login method that does not require a mnemonic phrase, an L2 interaction method with low procedures, and an optimized transaction matching form. We can tell the influx of founders and developers that even if we don’t build a new public chain or ZK, there are still many possibilities.
Each of the technologies mentioned above are not original to ft. As Henry Ford said, “I didn’t invent anything new, I just took what others had invented over the centuries and put it together into a car.”
This article is not intended to study whether ft is the Uniswap Moment for Social (Is Friendtech the Uniswap Moment for Social). Instead, we will analyze the protocols and infrastructure used by ft based on the social platform and known information of friend.tech founder Racer, starting from the first step of the login interface. If there are any protocols that are not covered, readers are welcome to inform us so that we can add them.
Stack 1: PWA
Not only is it strongly bound to Twitter, fts initial product is also strongly bound to an old technology - PWA (Progressive Web App, Progressive Web Application).
Although it is called an old technology, it is less than a year old to meet the needs of ft push. According to Farcaster founder Dan Romero, Safaris update to version 16.4 (launched in 2023) has strengthened support for PWA, which allows users to obtain ft message push more stably.
In general, PWA is still a web application, but by providing a standard framework on the mobile side, it can achieve a user experience similar to native applications in web applications. Including message push, background loading, offline use, native application interface (similar to the UI and UX of native applications) and desktop icons.
PWA is nothing new to many developers. Abroad, Twitter in the Jack Dorsey era has long supported PWA, and many domestic platforms such as Weibo and Minority also support PWA, and the user experience is also very good. Even in the crypto circle, projects such as Coinbase, Orca, and PancakeSwap all support PWA applications. Like ft, many DEXs also support jumping to local wallets such as MetaMask on the phone to complete authorization.

Protocols and websites that support PWA
For the encryption circle, PWA technology also means bypassing the supervision of various store software and the 30% Apple Store share. I don’t know if you still remember that a few years ago, Epic and Apple had a huge quarrel over Fortnite’s “Apple tax”. While Apple and many gaming giants were arguing over the Apple tax issue, Amazons cloud gaming business Luna cleverly chose the PWA model to bypass Apple Store supervision.
In the author’s communication with some developers, I learned that even without considering the Apple tax, the overall cost of launching a PWA is lower than that of logging into the app store, and the operation and maintenance costs for the same user level are also lower. After this ft uses PWA technology and successfully attracts enough attention, PWA may become an important implementation path for crypto industry products.
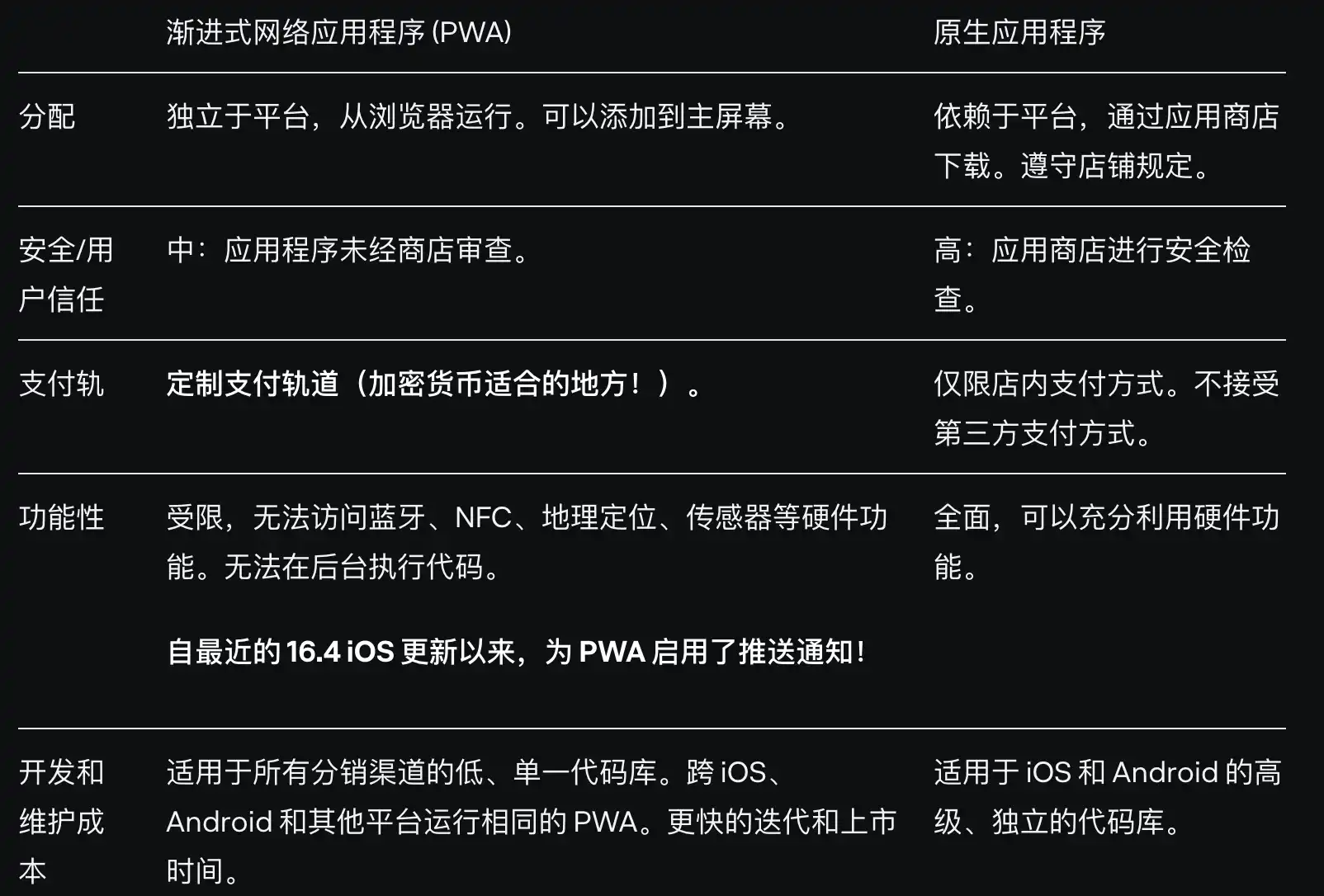
Source: Delphi Digital
At the same time, PWA technology is also a major driving factor for ft to quickly iterate and continuously add new features after its launch.
For a detailed introduction to PWA, you can refer to Rhythm’s previous article “Is the PWA used by friend.tech the best solution for encrypted apps to bypass the application portal?” 》.
Stack 2: Privy – embedded wallet
After the download was completed, ft did not choose the traditional method familiar to encryption users (downloading the wallet, saving the mnemonic phrase, switching networks, connecting the wallet to the application, etc.), but logged in through a Google account and Apple ID. The user creates a new self-hosted wallet, which avoids the experience of saving mnemonic phrases or private keys, simplifies the entry process, and weakens the encryption properties of the product.
Here ft chose Privys embedded wallet method to achieve the same experience as many mainstream login methods at home and abroad - authorized login with accounts on mainstream platforms such as WeChat, QQ or Google.
If you think this embedded implementation is dispensable, then imagine another version of ft: download the MetaMask wallet, connect with MetaMask, and then connect Twitter to the account. Every time you want to buy a key from someone else on the app, you have to jump to MetaMask, sign the transaction, and then come back to the app. And ft under this user experience is basically excluded from all traditional users.
Adopting an embedded wallet is not a betrayal of crypto, says Privy CEO Henri Stern. In fact, it is just a very good alternative to certain application experiences - bringing traditional Internet users with email logins and crypto-native users in the same place. On the starting line.
According to Privysintroduce, the embedded wallet uses MPC technology and is implemented through Shamir Secret Sharing: its wallet security data is divided into N parts, and M parts of the N parts can be used to recover. The current Privy allocates wallet security data into three copies, and collecting two of them can access the account.
The end result of the embedded wallet is that Privy cannot reconstruct the mnemonic phrase and access the users private key alone, and the user can access his or her private key at any time without going through Privy. That is, neither friend.tech nor Privy can access the users private key, but the user can obtain a complete cryptocurrency wallet.
However, DefiLlama founder 0x ngmi also posted on social mediaexpress, Currently friend.tech stores the users key on the front end, which is vulnerable to attacks. However, Privys embedded wallet was only launched in March 2023, and it is still updating the product. For example, it recently added a password recovery function. Perhaps in the near future, the now-criticized new address problem will also be solved, and even hardware wallets can be connected to ft in some way. Rhythm will continue to pay attention to the technical updates of embedded wallets and consumer-grade encryption products.
Stack 3: RaaS—Base, (Rollup as a Service)
After completing account registration and login, and binding Twitter, inject Ethereum (including mainnet and Base options) into the new wallet. The Ethereum transferred to the accounts Base chain is the only and universal currency of ft. Since every transaction occurs on the Base chain, fts user transaction fees are extremely low.
It can be seen from the popularity of Bases launch that the market has gradually transformed the fact of one-click currency issuance into the expectation of a one-click chain issuance (RaaS, Rollup as a Service) narrative. Based on the Base built by OP Stack, some data even surpasses Optimism itself. Summarizing previous narratives from major institutions and media, OP Stack has the characteristics of shared security, powerful functions, low cost, and open source. Using RaaS can greatly avoid the wheel-making problem prevalent in the encryption industry and reduce fragmentation.
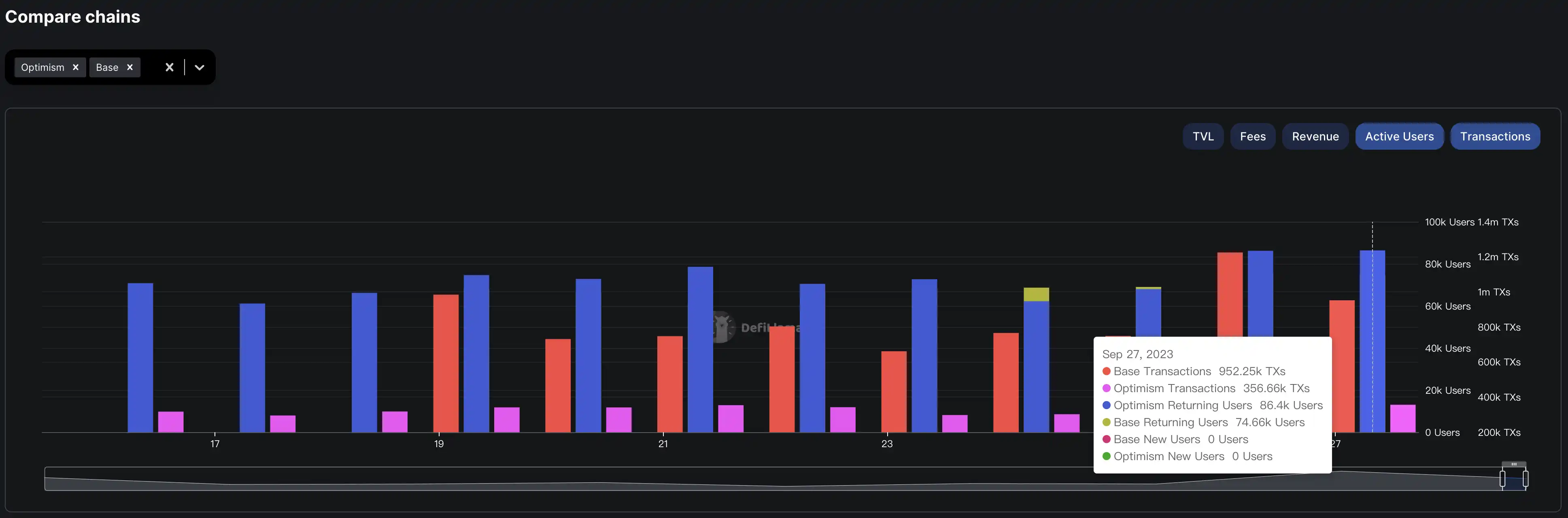
Recently, Base has surpassed Optimism in both the number of users and the number of transactions. Data source: DefiLlama
In the future, more and more RaaS protocols such as Conduit, Caldera and Eclipse will be launched, and perhaps one-click deployment of L2 can soon fly into the homes of ordinary people.
Stack 4: bonding curve
ft founder Racer seems to have a soft spot for DeFi. In the last one he createdImage social sharing product StealcamAmong them, she introduced an automatic transaction matching mechanism, increasing the price of Stealcam drawing rights at a frequency of 10% plus 0.001 ETH, and at the same time paying a certain amount of agreement income to the creator.
In ft, Racer directly constructs all transactions in the bonding curve without any external LP (Liquidity Provider). A trading medium is naturally formed between each Room participant. Everyones room and key prices are reasonable and traceable. The simple and transparent calculation method avoids complicated calculations and transaction loopholes.
ft keys bonding curve curve
Of course, many users are discussing that the current key price under the bonding curve is too high, which will affect the willingness to pay of potential participants. This may also be a problem that the ft team needs to face and solve.
Stack 5: Other
Even though everything in ft comes from smart contracts on the Base chain (users can interact with ft through other front-ends), everyone seems to think that ft is a Web 2.5 product.
For example, PWA itself is a technology that relies on centralized servers. The chat content in each Room in ft is completely centralized and is not encrypted and stored on decentralized storage protocols such as IPFS or Ar. Moreover, user addresses and Twitter user information are also strongly bound, which seems to some users to be a vampire attack or parasitism.
However, a series of derivative activities triggered by ft are all based on smart contracts. For example, what happened beforememory pool leakevent, resulting in the robot being able to purchase a large number of new user keys within the same block. As well as the various robots and derivatives launched today based on the web page or TG bot. Even behaviors and activities such as key-based voting and NFT distribution that may be launched in the future are all based on on-chain data.
As the focus gradually shifts to Mass Adoption and consumer applications, there will certainly be no shortage of controversies about decentralization in encryption. But as mentioned in an article by Privy, todays Web3 is for users, not experts.
Enlightenment
To a certain extent, friend.tech is indeed more like a traditional Internet product, which is clearly reflected in the frequency of product and rule adjustments: fast iteration and low cost.
Product iteration
fts product iteration speed is undoubtedly far beyond the average standard in the encryption industry. This can be felt most intuitively from the navigation bar at the bottom of the product. The first version of ft only had three options: homepage, exploration, and airdrop, but now there are five options: homepage, watch list, chat, exploration, and airdrop. In short, ft is more like a product.
ft function comparison, the upper part is the first version, and the lower part is the version after multiple iterations.
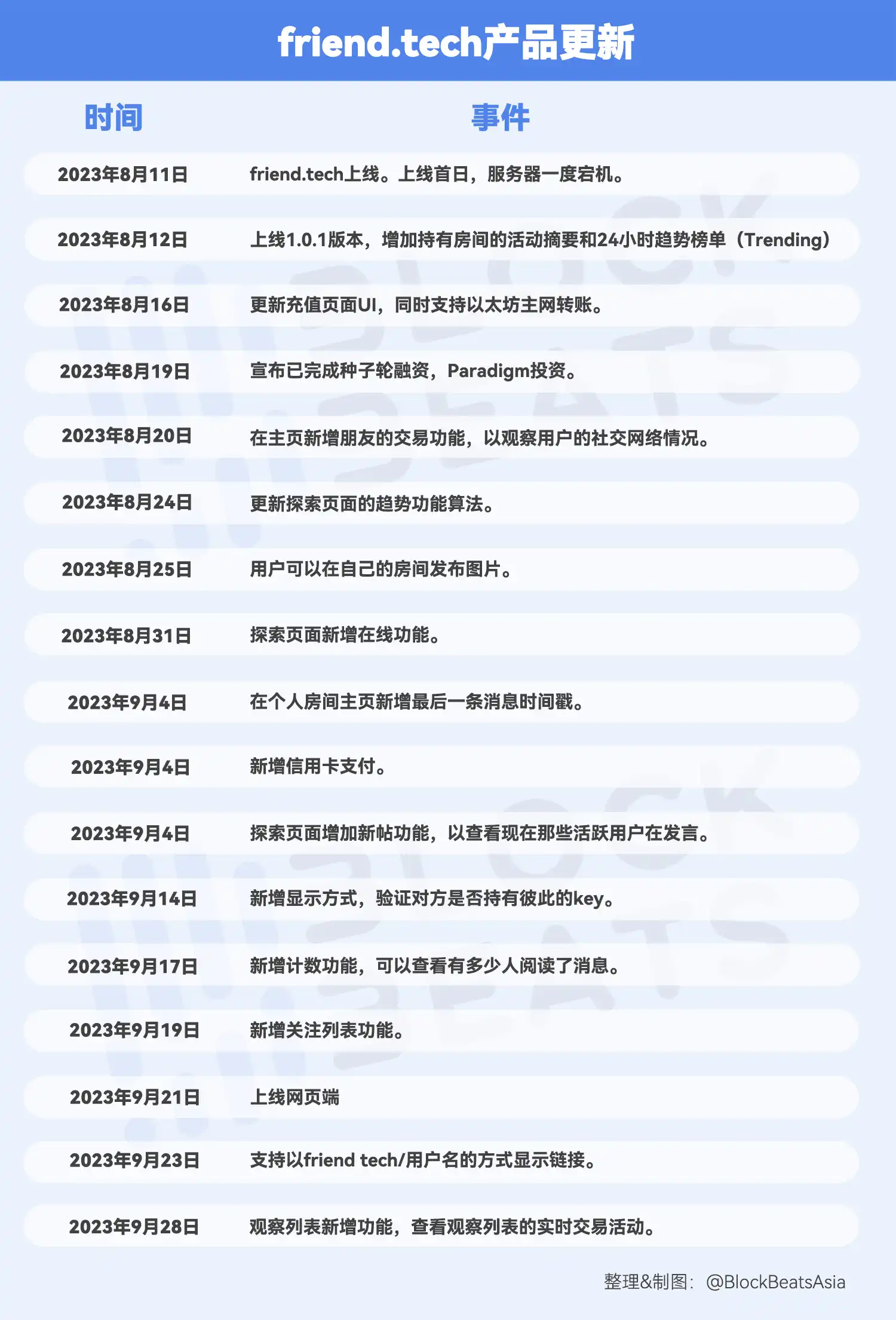
Rhythm also organizes the update events announced by ft to display the content and frequency of product updates in a more intuitive way. If, as rumored in the community, the ft team only has three members, the frequency of updates to this product is enough to surprise many users in the encryption circle.
Refined operations
Ever since airdrop hunters became major users in the crypto industry, project parties’ game against Sybil attacks has become a focus. However, fts black box and high-frequency adjustments to the points rules do not seem to have triggered a large-scale centralized discussion in the community, and many users even expressed their approval.
Rapid iteration is difficult to achieve in code is laws smart contract, but fts contract only fixes the transaction level, while points and product functions are at the data level. How to adjust variable rules can attract more users, reduce loopholes, stimulate user vitality, and achieve the goal of promoting high-quality growth of smart contract data. Centralized adjustment is undoubtedly a good way.
Just like traditional Internet products that are familiar to users, it takes a lot of internal data analysis, research, and AB experiments to find out the appropriate PMF (Product Market Fit).
The ft team is also very methodical in market operation strategies. For example, in the launch of the product, the first wave of popularity came from a large-scale cold start promoted by KOL, and the influence spread to the vast majority of crypto users. When the products rising momentum faded, the Paradigm financing announced by ft increased endorsement of its product, and also attracted a wide range of short hunters and more interested institutions. At the same time, the ft team also made dynamic adjustments to the product, which not only catered to the (3, 3) strategy of the ft community, provided assistance for mutual purchases, but also significantly weakened the points of self-purchasers.
Wang Huiwen, co-founder of Meituan, said in his product class that humans love innovation at an abstract level, but fear innovation at a concrete level.
In fact, most of todays success stories are not the first products in the industry. We hope that the emergence of friend.tech will inspire more new ideas and creative products in the industry, and look forward to the emergence of more cryptographic consumer applications.



