Connext airdrop farce: Bug blunders and endless witch hunts
Original | Odaily
Author | Qin Xiaofeng

After waiting for two weeks, Layer 2 interoperability protocol Connext finally opened the airdrop application tonight (URL: https://airdrop.connext.network/claim/52), but a major mishap occurred.
Half an hour after the application opened, crypto KOL "Piggy Bang" tweeted that there seemed to be a vulnerability in the Connext airdrop contract that "scientists" could exploit to endlessly steal the NEXT airdrop of other users. He attached frequent application records with addresses starting with 0x44Af (click to jump).
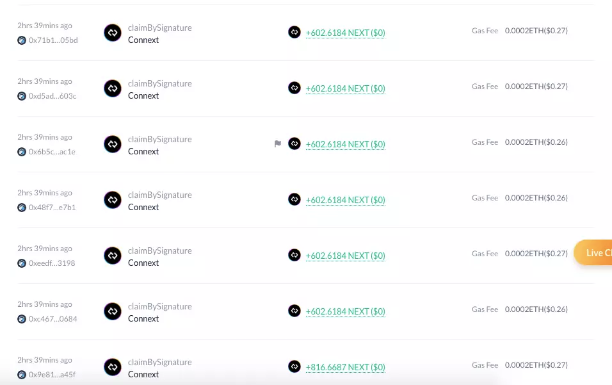
This news has been widely circulated in the community. Later, users analyzed the on-chain information and found that the address starting with 0x44Af was officially created today and has received the airdrop more than 230 times. All the tokens obtained were sold and exchanged for ETH, USDT, and USDC, making a profit of about $39,000.
At this time, the Connext airdrop contract also encountered a malfunction, and some users reported that they were unable to successfully claim the airdrop. There were rumors in the community that the official closed the airdrop due to a vulnerability.
However, the truth is that the Connext airdrop contract does not have any vulnerabilities.
Crypto KOL "Piggy Bang" stated that the Connext airdrop contract is secure and that his initial analysis misled readers. He explained that although the Connext airdrop contract allows the sender and recipient to be different addresses, the original address is required to authorize the signature for calling.
"The method of claiming is using claimBySignature, and the last parameter is to pass the signature information. This 'signature' is obtained by the user calling it through a smart contract or other means. So we can understand that _signature is a kind of credential, and with this credential, the user can obtain the tokens of the _beneficiary address." He added that the address starting with 0x44Af is likely a token aggregation for a studio, not a vulnerability in the contract itself.
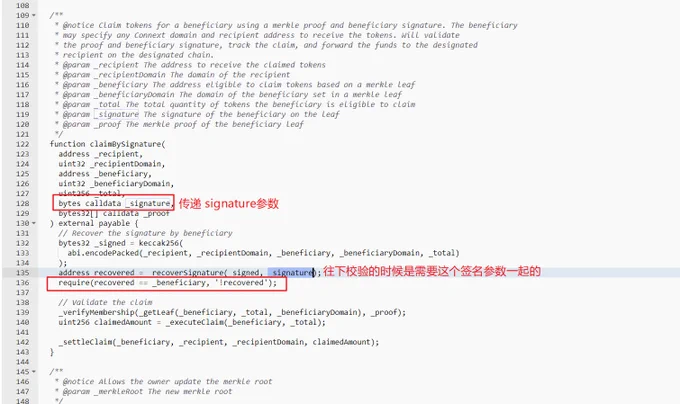
(Partial information of the smart contract)
SlowMist Security Team told Odaily that there is no obvious vulnerability in the Connext airdrop contract that allows others to claim the airdrop.
Users can claim NEXT tokens through the claimBySignature function of the NEXT Distributor contract, which involves the recipient and beneficiary roles: The recipient role is used to receive the claimed NEXT tokens, and the beneficiary role is the address eligible to claim the NEXT tokens, which has been determined when the Connext protocol announced the eligibility for the airdrop. During the NEXT token claim process, the contract performs two checks: first, it checks the signature of the beneficiary role, second, it checks if the beneficiary role is eligible to claim the airdrop.
During the first check, it verifies if the recipient address provided by the user is signed by the beneficiary role. Therefore, it is not possible to pass the check by randomly entering a recipient address without being signed by the beneficiary. Even if a beneficiary address is specified to construct a signature and can pass the signature check, it cannot pass the second check for airdrop eligibility. The eligibility check for airdrop claim is done through Merkle proof, and the proof should be generated by the official Connext protocol. Therefore, users who are not eligible to claim the airdrop cannot bypass the check and claim others' airdrop tokens.
To summarize the above analysis, if User A is eligible to claim, they can authorize User B to claim on their behalf. The reason why the address starting with 0x44Af can claim so many tokens is because this entity has authorized multiple eligible addresses, not because a hacker exploited a vulnerability.
However, interestingly, before the airdrop was opened, Connext took action against witch addresses by inviting the community to help the team screen the witch addresses, and they were willing to offer 25% of the recovered NEXT tokens as a reward.
Gift for the informant. According to official data, a total of 5,725 witch addresses have been identified and removed from the qualification list, and 5,932,065 tokens have been revoked.
However, from tonight's performance, it seems that the anti-witch operation has left behind a considerable number of fish that have slipped through the net, and even added many obstacles to the entire airdrop platform.
Connext core contributor Arjun Bhuptani stated in a post that the address starting with 0x44Af is a witch bot, which has sent a large number of junk requests to Tokensoft's backend, causing its API to crash. This may also be the reason why the airdrop claiming interface cannot be used. (Note by Odaily: Preventing others from claiming may be to obtain a better selling price.)
The good news is that the officials have noticed this issue and the airdrop will be reopened. Connext posted: "We are aware of the issue that affected the airdrop website, causing users to be unable to claim. We have detected robot activity that overloaded the servers of our partner and service provider Tokensoft. They are actively working on resolving this issue to achieve normal claims. Everything should be back to normal soon."



