Foresight Ventures: The integration of DID and wallet will become the super entrance of Web3
first level title
TL;DR
The potential value of DID is very large, and it will capture the huge value second only to the public chain.
Compared with projects such as Defi and gamefi, DID's entry threshold and understanding cost are low enough, and it has a strong Matthew effect. It is expected to become a super entrance for users to enter web3.
DID can provide the same personalized content as web2, and at the same time, it can ensure that we have our own identity, preferences, and account information from being leaked and profited by others.
The identity layer on the chain brings new possibilities. It redefines the rights of identity, re-changes the power of identity, and returns the power of data realization to users.
We divide the DID identity stack into private key management layer-authentication layer-authorization layer-proof layer. The proof layer has unique data advantages and is the product form with the most potential to make a unified DID.
The competition for wallets in the future will be extremely fierce, not only the existing EOA wallet and aa wallet competition, but also cross-track players at the proof level may join the competition to provide users with a better identity account system and DID ecology.
1. What is DID decentralized identity
DID is the abbreviation of Decentralized Identifiers, that is, decentralized identity. The focus of DID is decentralization, and then identity. In the world of web3, how we maintain a unified identity in a decentralized environment and how to use our identity is what we want to discuss in this article.
a. Traditional centralized identity
In the centralized platform of web2, our every sentence, every transaction, and every behavior are collected and recorded by the platform to analyze our preferences and habits to form user portraits. For the web2 platform, this is their tool for harvesting traffic. Fine user portraits plus big data algorithms push articles, videos, and even the next product you may like to your face, so that users can stay on this platform, while the centralized platform has how to control And the way to realize the traffic. this means
Control of platform content: For any creator who wants to provide content for platform users, when their content is deemed to be illegal or does not meet platform standards, they lose the opportunity to share their views.
Control user data: All data generated on the platform is essentially the content written into the platform's database, which is owned by the centralized platform. That is to say, the platform can modify or even delete the user's personal information and account at any time. For example, Gmail once deleted the user's Gmail account and mail due to manual review errors, and the user lost everyone's contact information overnight
b. Classification of Decentralized Identity
DID provides new possibilities, users have complete control over the generation of identities and the use of identities. In the year from the proposal of DID to the crazy discussion in the market, we have seen different solutions based on the understanding of DID-based decentralized identity, from
The data type angle division includes:
VC is the abbreviation of Verifiable Credential Verifiable Data Credentials. It is a standard proposed by W 3 C in March 2022, and its authenticity is proved by verifiers.
In the process of using VC, there will be three roles. The claimer holds the certificate, and the data in it needs to meet the requirements of fields, data types, and data sorting that match the certificate type. The notary Attester checks the data and confirms it is valid. Then use the private key to sign the VC, and then the verifier can verify the authenticity and validity of the certificate without touching the notary and only needs to see the signed data.
VC itself is a standard that provides standards for different subjects to verify data. Although a certain degree of decentralization has been achieved, VC data does not necessarily need to be uploaded to the chain, so the user's data ownership is not guaranteed. At the same time, what VC describes is not the identity of the user, but only a certificate that meets a certain standard, such as education, medical insurance, so in the long run, VC may become the standard for Internet verification, but it is not a decentralized identity
Soulbound NFT, Soulbound NFT does not support on-chain transfer, which means that SBT only belongs to a specific on-chain address
Based on the Soulbound NFT proposed by Vitalik, the data and information carried by NFT are "soulbound" in the user's wallet address, which adds non-transferable attributes and solves the illusion that the user has achievements or experience by purchasing NFT or achievements. , which binds the unity of user behavior and identity
But the other side of soul binding is that it cannot be unbound with NFT and user identity. In addition to the active display of POAP or NFT by the user, the user's address can be maliciously airdropped NFT or maliciously tagged. Under such circumstances, the user can only be forced to accept and will be publicly displayed on the chain, causing the user's reputation loss or even transaction failure, etc.
Onchain reputation The reputation on the chain reflects the user's identity through the interactive behavior on the chain
A successful transaction means that it is written into the block on the chain and can be viewed and verified publicly. Of course, ZKP provides a way to directly verify the transaction result without publishing the specific transaction content. But every transaction and interaction of users on the chain can be recorded and analyzed. Whale alert itself is based on publicly visible data on the chain to track the behavior of large households. Nansen’s Smart Money label can be said to vividly display what Black Swan author Nassim Taleb said Don’t tell me what you think, show me your portfolio . The Degen score goes one step further, by analyzing the data on the chain, extracting the score as the proof of the user's Degen, providing a new identity label,
However, these labels themselves lack reasonable context and background introduction. For example, the address marked by smart money may only be one of the wallet addresses of the institution, and the selling or purchasing behavior of a single address may not fully infer the institution's strategy. Maybe this is just one leg of the delta neutra strategy. The act of an address alone is not enough to form a complete identity. Moreover, the reputation on the chain may be deceptive, because the user can compensate for the interaction after the event, or the illusion of reputation formed by purchasing in the secondary market. Of course, it is also possible to judge whether it is an ex-post compensation through the timeline and NFT transaction records, but This kind of on-chain data itself is a lag proof.
Decentralized domain name, the decentralized domain name opened by ENS can be said to be a decentralized identity in itself, and ENS's ETH-based name positioning and huge wealth effect have become a symbol of identity
ENS can directly reflect the identity through the name of the address by converting the seemingly garbled wallet address into a readable address. At the same time, the first launch effect and brand influence of ENS has basically become the domain name with the most application scenarios. At the same time, ENS can edit the content of websites and subdomain names, providing opportunities for customizing identities. At the same time, ENS is composable as an on-chain contract, and different applications can be combined on the chain. For example, Philand generates a metaverse unique to the user through ENS-related information, and Kola lab generates music NFT based on the user's ENS. The visualization of information can be said to be the representative of the composability of DID
However, the transaction attribute of ENS can untie user identity and domain name identity, losing the continuity of identity. At the same time, the interaction based on the wallet address is still limited to the transaction information on the chain. At the same time, ENS is currently only based on the Ethereum main network. Facing the current Layer 2, Layer 3 and other multi-level networks and multi-chain environments, it may not be comprehensive and not necessarily Can accurately and completely describe the identity of a user, see the discussion of the wallet for details.
Wallet address, as the entrance for users to interact with dapps on the chain, it can be said that for DAPP and other wallet addresses are users, and the transaction records on the chain are the portraits of users.
Taking the wallet on the chain as the identity, such as Nansen smart wallet, can also be understood as the DID of the user in the transaction scenario. But in fact, a user may have multiple wallet accounts, and the transaction behavior of each account is different. For example, one of the wallets of an institution is doing unilateral strategy, and the other wallet is only doing delta neutra arbitrage behavior, so a single wallet It cannot fully represent the actual behavior of a user. Moreover, in a multi-chain environment, each wallet is also an independent account, and users may have different transaction behaviors on different chains, so a single wallet on a certain chain cannot completely represent the user's DID
At the same time, Lens, Galxe, etc. have also derived social graphs and Profile NFT social portraits through on-chain behaviors. However, most of the interactive behaviors on the chain are transactions. At present, there is a lack of social application scenarios to provide social behaviors on the chain. Of course, we think that when the data infrastructure is perfect and the cost of on-chain is reduced, we can see a lot of social data in the future, so as to obtain more valuable social relationships
Stealth address Stealth address, the latest stealth address proposed by Vitalik can separate the right to use and view the wallet address, ensuring the isolation of user identity and assets
The characteristic of the blockchain is openness and transparency. For users, the identity of the user can be deduced through asset information and behavior on the chain. In the latest article, Vitalik proposed a new stealth address, which is temporarily generated by the user who initiates the transfer through elliptic curve encryption. Public key and private key, and then combined with the address of the receiving account to generate a secret address and transfer to this address, the receiving user can use his own private key combined with the temporary public key to see the assets of the secret address and receive money later Talent has the right to control this asset. It is equivalent to cutting off the connection with the user's identity with a one-time new address.
But as Vitalik said, every time a new address is generated, it faces the problem of Gas payment. Although only the payee can control the account assets, the new address does not have enough Gas to pay the transfer fee. At the same time, the privacy of the secret address is only the privacy of the payee on one side, and it is still a transparent operation on the chain for the payer. The problem of Gas can be paid by abstract wallet management or relayer, and Vitalik proposes to use ZKP to prove the ownership of users and secret accounts, and even imagines that different addresses can be used for different DAPPs, allowing users to manage DAPPs. Visible information and assets. Of course, it is still difficult to implement ZKP, cross-chain and wallet design. We look forward to seeing new projects put forward implementation plans.
Cross-platform Avatar, the three-dimensional character image is more in line with our imagination of identity, and cross-platform Avatar can ensure the unity of identity
Although the flat PFP NFT is also used as an avatar as a representative of identity, NFT itself is tradable and it is difficult to form a binding relationship between identity and NFT. The 3D properties of Avatar provide a visual image, and at the same time, as the incarnation of our metaverse, it has a unique identity. Like ready player me and Lifeform's Avatar NFT can support users to edit appearance and image, and can be used across platforms. Like Lifeform's Avatar NFT itself is an NFT on the chain, which can be directly compatible with the metaverse on the chain, and even off-chain meetings including Zoom , Google, etc. ensure the unity of identity. Afterwards, we can even look forward to a personalized metaverse, which will display more information about one's own identity in a customized personal metaverse.
Although Avatar NFT is a more three-dimensional identity, at present, Avatasr NFT shows more about appearance and appearance. It is just a single identity image, and does not include more behaviors or other information that define identity. After that, we can expect Avatar NFT combines metadata or composability to display more information.
c. Key attributes of DID
identity composability
In fact, DID can be more than an identity, just like our identity may consist of ID card, driver's license, education, etc., a single certificate and product form may not be enough to describe our complete identity, but a combination of products applicable to different scenarios form our full identity. The difference is that the identity information under the chain cannot communicate with each other due to the fragmentation of different central communication systems. After the data is uploaded to the chain, it has fluidity and can support different arrangements and combinations, showing the user's identity in a more three-dimensional image, such as imagining various games. The achievements of SBT can be displayed in the user's personal Avatar NFT as a wearable medal, or the assets and transactions on the chain based on the wallet address can obtain lower interest in the lending agreement, which can include the composability of data sources , the composability of different application scenarios, and even the composability between different DIDs
Privacy and Security of Identity Data
At the same time, because the environment on the chain is publicly visible data, we need to pay attention to
1) Privacy: In the dark forest on the chain, it is very unsafe to disclose identities and related bound accounts and asset information, especially for the information on the chain that mainly focuses on financial transaction scenarios, exposing wallet addresses and transaction behaviors is very dangerous. Very dangerous, so DID privacy for associated asset information should be a necessity. At the same time, maintaining anonymity is one of the needs of many encryption-native users. At present, we have seen open source plug-ins such as semaphore and DIDs that provide privacy such as Firstbatch
2) Security: including information security and asset security. Information security mainly refers to the security of personal information, which may include information such as identities, addresses, and academic qualifications under the chain, as well as wallet addresses and transaction behaviors on the chain. It is possible to expose these information It brings about personal safety issues, and at the same time, the authorization behavior on the chain is often prone to the possibility of being hacked or maliciously attacked. Therefore, proper data processing and security must be ensured for the collection, storage, and use of personal information data. Although most project parties now save locally or use AWS, relying on the team's management capabilities, AWS downtime and the endless problems of team management capabilities make us hope that these personal sensitive data can be stored in a more decentralized The modernized database guarantees the user's data security
first level title
2. Why do you need DID
Everyone's needs are different, because different preferences and backgrounds have been embodied in the choice of different financial products due to different risk preferences, different trading habits lead to the use of different trading platforms, different aesthetic standards, so choose to join different NFT community. For the project side, DID can help the team better understand the needs of users and design products. For users, a lot of market noise and dazzling products increase the difficulty of finding products that really meet their needs.
And DID may be the shortest path connecting product and user. To a certain extent, the major platforms of web2 have pushed to us at the fastest speed through the user portraits they have mastered, such as the products you may like, and the tweets that people nearby are watching. Reasons for not being able to leave these platforms. And DID may be the key to bringing the same experience, and more importantly, this is Web3 where users truly have data sovereignty.
a. The value of DID
For DID, we believe the real potential lies in:
Possibility of paying for data due to data ownership
The attribution of data ownership means the option of data charging. When data belongs to a centralized platform, it is up to the platform to choose how to monetize data such as user behavior or personal preferences generated on the platform. For example, Google chooses to auction search results that attract users’ attention to the highest bidder, and Amazon uses user The purchase behavior infers the possibility of the user's pregnancy and sells the news to the seller of maternity and baby products to accurately push advertisements to the user. The user becomes a product sold on the platform to obtain benefits, and we can use the products and services of the platform for free. In fact, it is Because our behavioral data is collected by the platform and generates income, which subsidizes the cost of the platform and even makes a profit.
When users have data sovereignty, users can get back the right to choose data transactions. You can choose to sell the relevant data, or you can choose not to sell it. Different from the centralized platform as an intermediary connecting data producers and users and from it as a data porter to trade data value, we can even imagine a data market connecting data producers and consumers, such as providing a P2P transaction model, or DAPP directly subsidizes users to obtain user usage data and consumption habits, and a new business model for DAPP paying users emerges. These can all be realized through the user data and identity contained in DID, and this also depends on the chain we discuss below. Defi lego-like combination given by DID on
Composability brought by data on-chain
After the data is uploaded to the chain, the data begins to have liquidity, which can be read, used, and verified through the chain contract or API, and the process of data use or verification can be charged through the contract, just like reading and writing chainlink price Feed needs to be paid, and DID may propose a new data charging model for uploading user information to the chain. If DAPP wants to read or verify the personal information or transaction data contained in the user's DID identity, it needs to be paid before it can be obtained. For example, Firstbatch's SBT requires DAPP payment is required when the contract verifies the proof of interest
Moreover, the design of DID can even allow users to choose whether to agree with DAPP to read relevant information, or to selectively disclose personal information. For example, for Defi-related types of DAPP, only choose to display the wallets on a certain chain or the transaction records of one of the wallets To choose the service of DAPP
More importantly, we may not need to have a large and comprehensive identity on the same platform or dapp, but may have different DIDs in different scenarios. On the dapp, it can be a mining OG or an onchain reputation of a trading master who is good at arbitrage, and an NFT of a research master with a novel view is published on the mirror. Just like people are multi-faceted, DIDs in different scenarios can show different aspects of an identity, and the composability of the chain allows different scenarios to obtain information about other identities of users to open new scenarios, or users can choose in different scenarios. Show different DIDs in different scenarios, choose to protect your identity while still being able to obtain products and services that meet your needs
b. DID application scenarios
As identity data, DID mainly depends on how to use data or verify identity information. DAPP can use identity information to understand user needs and provide more personalized products or verify whether users meet the requirements of DAPP. The currently conceivable scenarios include:
Compliance requirements: CEX under the chain requires user KYC based on compliance and security considerations. There are also lending agreements on the chain that start to combine traditional financial KYC data under the chain to help better manage risks, mainly based on compliance and risk control. KYC requirements
Proof of Personhood authentication: The most common is the anti-sybil attack in whitelist and airdrop, that is, the same person can create multiple accounts or wallet addresses or get whitelist and airdrop. For the project side, this increases the cost of acquiring customers, because these rights received by the same user can originally obtain other new users, so for the project side, there is a need to verify the proof of personality of the user
User portrait: This is more similar to the understanding and use of DID in our usual discussions. In the Web2 world we are familiar with, a large amount of personal information and behavioral activities are collected, sorted, and extracted by centralized companies to accurately push content and advertisements for each user, and personalized content will also increase. User stickiness to the platform. This is what we think one of the greatest potentials of DID is that DID can be used to design, recommend, and adjust content for users, including social scenarios and transaction scenarios
Social scenarios: Although the current data on the chain is mainly transaction data, we believe that after EIP 4844 greatly reduces the storage cost on the chain, and after the launch of a large number of data infrastructure projects such as data storage, retrieval, and analysis projects, We can see data-intensive social projects at the application layer, and provide targeted services to users through DID and other messages, providing web2 user experience. There may be different forms in different tracks:
DAO: The topic that was often discussed before was onchain reputation. For DAO members, onchain reputation is one of the options to reflect the degree of member contribution. However, since the working scenarios of DAO are not limited to the chain, a large amount of communication and work results, such as snapshot voting, community proposals, offline activities, etc., all appear in off-chain scenarios. Perhaps VC can be used to prove off-chain education, work experience etc.
first level title
3. The Web3 Identity Stack
The Web3 identity stack can be divided into six layers from bottom to top: storage layer-identification layer-private key management layer-authentication layer-authorization layer-proof layer. The storage and identity layers are the infrastructure, defining the DID standard. Large-scale user interaction starts from the private key management layer:
In order to obtain the web3 DID, the user needs to first have a private key management account (account). The form of web3 private key management account is usually a wallet, which becomes a natural identity information container.
After any authentication procedure of mnemonic/MPC login/biometric verification, the user successfully logs in to the wallet
Different Dapps can connect to wallets and read user information (such as multi-chain addresses, domain names, transaction records, behavioral data, and NFT assets) after obtaining the user's authorized signature.
Finally, all kinds of VC\SBT\Poap, etc. are generated by the project of the proof layer, and stored in the wallet to prove the user's OG identity
image description
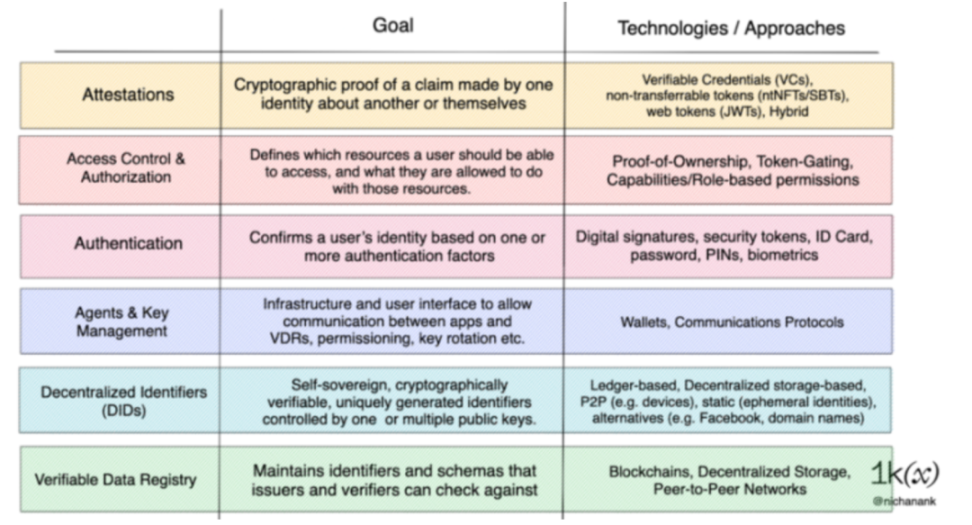
(Reference: 1kx)
a. Private key management account - wallet
The wallet solution provides a natural identity container, which is the traffic entrance connecting application scenarios and credentials held by users.
What should an ideal "DID wallet" look like:
Aggregates the addresses of all mainstream public chains, and integrates the fragmented data of users on different chains while having basic signatures, transfers and other transactions; secondly, it can display various SBT/VC/PoP certificates owned by users, and When the application project interacts, the user can independently authorize which data to disclose to the project, thereby helping the user realize data sovereignty
1) Smart contract wallet
The current mainstream wallets such as Metamask do not have these functions. An important reason is that they are basically EOA wallets, and these wallets basically only support the most native operations of addresses on the chain - query and transfer. In the future, smart contract wallets (such as: Unipass, Argent) are expected to achieve more expansion in wallet functions. We also optimistically predict the final state, functions and applicable scenarios of such products:
No private key: users no longer need to keep mnemonic words or private keys; multiple verification methods such as biometric verification and device verification can be passed
Account recovery: account recovery can be performed through biometrics, social verification, etc., to ensure that social identities will not be lost
Gas-free interaction: users can use the ERC-20 tokens involved in the transaction to pay for gas, or directly specify a fixed account for payment without preparing ETH as gas in advance; or without paying gas fees when the transaction fails
Account mortgage/transaction: The account contains assets and accumulated credit history on the chain, and the account itself can be directly mortgaged and traded in the on-chain market; what needs to be further considered is how the asset lender can effectively punish the increase in breach of trust The cost of doing evil.
Account classification management system: Users use dedicated accounts in different scenarios and have a more reasonable account management system. For example, a certain account only stores ETH as a gas account, and the interaction of all other accounts is paid by the gas account; a certain account only stores blue-chip NFT, which will not be easily used; a certain account is used as a game-specific account
2) Identity Wallet
The main function of the smart contract wallet is to store and manage Crypto keys for sending/receiving assets and signing transactions; another type of identity wallet is dedicated to storing identities, and allows users to create and make claims, and users can display identities across applications/platforms data.
Polygon ID Walllet: An official wallet for managing and storing PolygonID identities, which can realize claim collection, zkp generation and privacy verification; currently there are few applications, and developers can customize use cases
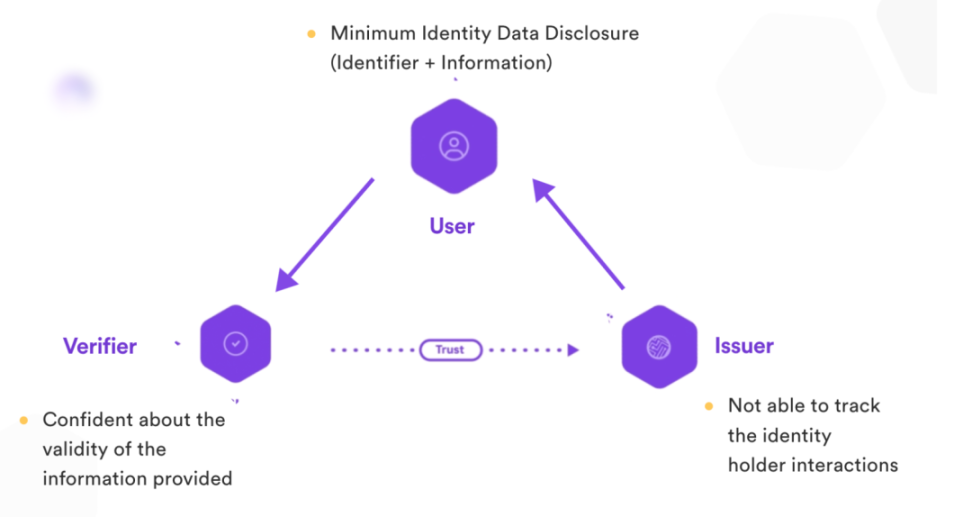
ONTO multi-chain wallet: aims to help users create decentralized digital identities, and fully protect user privacy through encryption algorithms. It integrates on-chain + off-chain identities, NFT, asset management, and information push; ONT ID information is complete but applied The scenarios are limited, and users lack the motivation to verify.
Nugget: It mainly focuses on e-commerce payment scenarios. It uses biometric technology to scan users' faces from multiple angles. By combining ID card scanning technology with optical character recognition technology, it completes the KYC identity verification process and zero-knowledge storage on the chain.
b. Authentication layer - reduce the user threshold on a large scale
At present, most web3 social application authentication methods are connect wallet, and wallets rely on mnemonics for public and private key login, or mpc login. To attract users to use web3 DID on a large scale, a more user-friendly, low-threshold and secure login authentication method is an essential prerequisite.
SIWE
Sign-In with Ethereum (SIWE) is an authentication standard pioneered by Spruce, ENS, and the Ethereum Foundation. SIWE standardized a message format (similar to jwt) for users to use blockchain-based account login services. On this basis, Sign-In with X (CAIP-122) makes SIWE an implementation of SIWx centered on Ethereum, and generalizes the standard to operate across blockchains.
Unipass
The Unipss mailbox login scheme applies zk cryptography to hide the relationship between the user's mailbox and wallet address, while ensuring that the mail operation is on-chain. In contrast, the mailbox login of web3 auth is not more centralized than the on-chain structure, and its private key plaintext is stored in the storage at the front end of the browser, which has certain hidden dangers to account information and assets.
Hexlink
As an identity oracle, Hexlink encrypts the user's identity data and transmits it to the identity server. The server decrypts the data and constructs a merkle proof of zero-knowledge proof to verify the user's identity. It can be compatible with both web and mobile applications, and supports the verification of web2 Social accounts and web3's EOA account and AA's abstract wallet provide a zero-threshold web3 account experience
Notebook
User identity KYC+ login scheme, after registering a notebook account and completing the verification of real person's biological information, zkp can be generated to prove the user's identity. Recently, it is cooperating with near on Notebook Auth.
c. Authorization and access control layer
Authentication confirms the identity of the user, while authorization determines which resources an entity should be able to access and what they are allowed to do with those resources. Such items fall into two categories:
1) Access Control Management
Instead of manually assigning access, the community can programmatically grant access based on a visitor's Token holdings, on-chain activity, or social verification.
Lit
Based on the MPC key management and access control protocol, the public/private key pair is represented by a PKP (programmable key pair) NFT. When the specified conditions are met, the owner of the PKP can trigger the aggregation mechanism of the network, so that they identities to decrypt documents or sign messages. Examples of applications include: Token-gated meeting and Gathertown spaces, live streaming, and Google Drive access.
Collab.land
Discord automates management bots and manages membership based on token ownership.
2) User authorization management
When interacting with application projects, users should be able to independently authorize which data to disclose to the project, and manage the authorization status and permissions of each Dapp through a unified interface.
EverRise wallet
Launched the EverRevoke wallet authority management tool, which can aggregate the token & NFT authorization status of 5 blockchains. Users can see and manage the token authority that has interacted on multiple blockchains before, so that they can be revoked at any time.

The authorization management experience is expected to be further improved in the AA account, such as setting different read-write and asset permissions for different private keys, or setting the minimum transaction threshold and automatic trigger conditions for a certain trascation.
d. Proof layer
Serialize the data on the chain through the address and produce "proof", "reputation" and "certificate". Based on verifiable on-chain data, this reputation is not limited to a certain platform and can be used in different scenarios. We believe that the proof layer is the closest to the C-end users, and its energy source continuously generates high-value data. It is the product form with the most potential to make a unified DID.
1. Data Ecosystem
The biggest feature of the social ecology protocol is that it can attract users to generate new data. Based on the data link, a 2b 2 c network effect is established, which naturally becomes the industry's unified identity standard. Although most data protocol projects do not have clear token incentives, they also run out of a benign user interaction model.
Galxe- From chain certificate network to DID data ecology
Galxe ID tags each address by issuing credentials, and integrates user data on different chains, on-chain and off-chain, Web 2 and Web 3; there are currently more than 4.2 million Galxe ID users.
In the first half of 23, Galxe Protocol, a license-free data protocol product, will be launched for developers to build applications on it.
It is planned to launch a standard system for Galxe certificates, including storage modules, verification modules, usage modules and privacy management.
Lens Protocol—Social Gardens Emerge
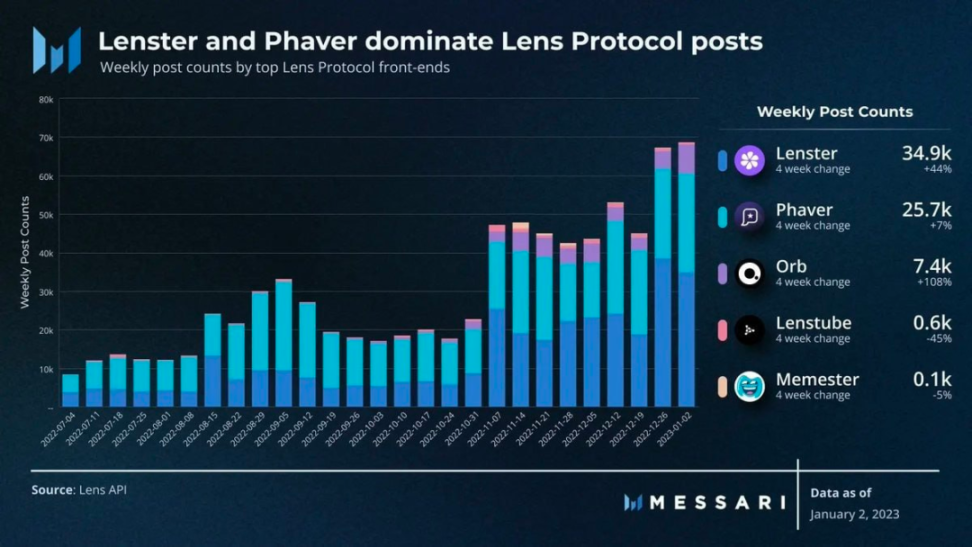
Lens Protocol is a decentralized social graph protocol built on Polygon, launched by lending protocol Aave. Regarding the goal of betting on Web 3 social media, Stani, the founder of Aave, has publicly stated that the ultimate goal is to combine Web 3 social and DeFi, turn the social graph into a trust graph, and provide low-payment loans through the Aave protocol.
Through the hackathon LFGrow and two rounds of donation programs so far, Lens has a total of more than 100,000 users, and the level of project innovation is good, including Phaver, Orb, SteamDAO, etc.
Farcaster - Decentralized Trusted Neutral Social Protocol
An open social protocol that supports many clients. Farcaster adopts an on-chain + off-chain hybrid architecture, in which identities are stored on the Ethereum chain, and Ethereum is used to ensure its security, composability and consistency.
Identity is controlled through Ethereum addresses, and off-chain messages are signed through Ethereum accounts. The user's data is encrypted and signed by identity and stored on the server controlled by the user (Farcaster Hubs). The reason why the data is not stored on the chain is because the settlement cost on most L 1 and L 2 networks is too high and the speed is too high. slow.
Web 3 wallet-based identity, soul-bound tokens, and the reputation role played by NFT in interacting with social content will make it possible for Farcaster users to interact across DAOs and communities, but there are no identity-related products in its ecosystem . V God has settled in, and there are many projects in the ecosystem including: Instacaster, Searchcaster, CastRSS, Configcaster, etc.
Nostr - Message relay protocol banned by Twitter
The full name of Nostr is "Notes and Other Stuff Transmitted by Relays", a relay transmission protocol for social media information. Judging from the Github commit record, Nostr was established in November 2020. As an Internet general-purpose infrastructure, it is still in its early stage.
Nostr is divided into two components: clients and relayers. The client is used to sign and verify information and is run by the user; the repeater is responsible for delivering messages and can be run by anyone setting up a server. The client stores the user's key internally. Each message must be signed and sent to the relay. The relay does not change the data. The verification of the authenticity of these messages is done by the client, so the user does not need to trust the relay , more in line with the spirit of decentralization.
Nostr originated from the BTC community and has a close relationship with the encryption community. In the future, a certain token incentive may be released for the storage function. In terms of marketing, Jack Dorsey, who served as the CEO of Twitter twice during the development process, carried the banner, but some time ago it was Twitter officially banned.
2. Domain name service
Both the domain name and the wallet can be regarded as identity management containers: the wallet can use a domain name as a substitute for the wallet account name, and use it as the "name" when interacting with the application side, and the domain name can integrate multiple chain addresses or even multiple wallets account, which is also a natural identity aggregator.
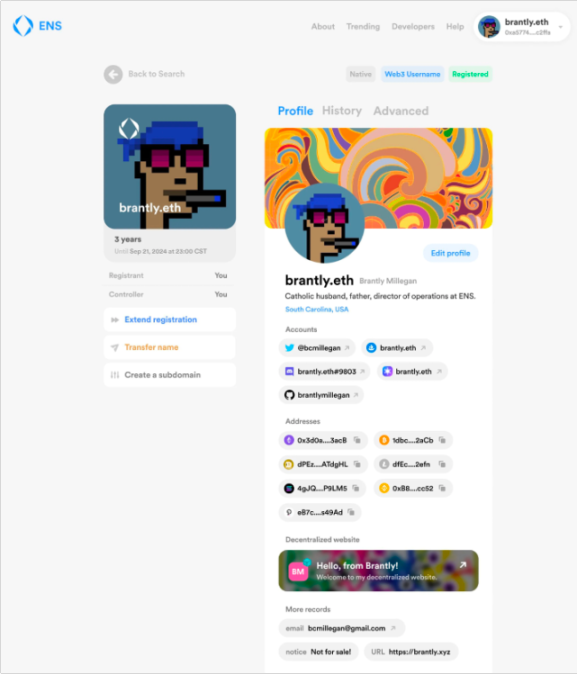
ENS-Sign In With Ethereum
With 1.8 million registrations currently, it is working with SpruceID to advance EIP-4361: Sign In With Ethereum. If the proposal is successfully implemented, this will replace Connect Wallet, allowing the domain name to become the entrance of Web 3 above the wallet address. In addition, ENS also hopes to complete its vision of "Web 3 Names" through the integration of a series of identities in the domain name.
Space ID- Universal Domain
Space ID: Provides registration services for domain names with .bnb suffixes. Space ID also hopes to link .bnb domain names with users' multiple addresses on different chains, users' Web 2 accounts such as Twitter, and become a Web 3 Universal Domain. Compared with ENS, Space ID's product iteration and landing speed are faster.
3. 3D visual identity
People are always pursuing a more extreme sensory experience, and the evolution from 2D identities to 3D identities will also be an important trend. The immersive experience and playability of Metaverse will be much better than 2D web page interaction. Games are also a natural social fission scene, but the difficulty of landing requires more time and technical precipitation.
Philand- metaverse pixel style identity system
Users can visualize the behavior on the chain through Phi, and receive corresponding components based on the behavior on the chain (donation, protocol interaction, etc.), small parts similar to Lego blocks, and build their own Metaverse world. Users holding ENS domain names can automatically generate land, and freely combine their web 3 worlds according to the behavior components on the chain they hold, and link with other ENS players.
Phi previously won ETH Global's hackathon NFTHACK 2022 and BuildQuest, has also received a grant from Uniswap, and is also one of the winners of the second round of the Lens donation program.
Lifeform- 3D Visualization DID
Lifeform is a 3D digital identity solution provider that has received investment from Binance’s seed round, focusing on the development of integrated solutions for visual DID. Core products include 3D hyper-realistic virtual human editor, visual DID protocol, secure smart contract suite, native decentralized identity SaaS system service, and metaverse underlying engine suitable for Web 3 cross-application development.
4. Other
Unirep
Unirep is an undeniable reputation protocol built on Ethereum. Users are allowed to anonymously give positive or negative reputation to others, and at the same time cannot refuse to accept the reputation (non-repudiable), and voluntarily prove that they have a certain reputation through zk technology, but do not disclose the specific amount. Such schemes can also be abstracted into smart contracts, using the composability of blockchain to provide encryption schemes for other project parties.
Firstbatch
Use AI to analyze off-chain web 2 data and formulate data labels, and use ZK to verify users' interests while ensuring user privacy. 1. Content recommendation 2. Offline activities 3. Authority activities can be carried out for users.
AspectaAI
The developer's linkedin uses some AI algorithms to process, classify, and label Github user data to generate user portraits for each Github user. Developer identities may have more utilities than general-purpose identities, including online job hunting, code contribution management, offline hackathons, developer communities, etc.
e. Privacy issues
We cannot discuss identity infrastructure without considering the technical primitives that enable privacy because privacy is important at all layers of the identity stack. Over the past decade, blockchain adoption has accelerated the development of cryptographic primitives such as zk-proof, which, in addition to scaling techniques such as rollup, allow identities to nuance and protect publicly verifiable information. Privacy Statement.
Iden 3
The zk-native identity protocol, which provides a zk framework and open-source libraries for zk identity primitives, authentication, and proof-of-claims generation. The protocol generates a key pair for each identity using a Baby Jubjub elliptic curve designed to work efficiently with zk-SNARKs, which are used to prove identity ownership and claims in a privacy-preserving manner. PolygonID is currently leveraging this protocol to build its identity wallet.
Polyhedra
zk is a full-stack protocol, and its cross-chain bridge zkbridge can solve the problem of user identity multi-chain calls. Launched the zkbridge relay network + two-layer recursive solution, while ensuring cross-chain security, while compressing gas costs and time costs. Developed a DID container for the Gamefi scenario, packaged the assets under the user account with one click, and embedded it into the game in the B 2 B 2C mode to become an official cross-chain bridge. In the future, it is planned to make user interaction simple or even insensitive.
Semaphore
The Ethereum ecosystem’s zero-knowledge protocol for developers was first proposed by Ethereum community members Kobi Gurkan, Koh Wei Jie, and Barry Whitehat to release V1 in 2019. Ethereum users can prove their group membership and send signals such as votes or support without revealing the original identity. Semaphore is not a user-facing application, but aims to provide powerful and simple tools for Ethereum developers and build DApps.
Applied zkp has also received great attention, as follows:
ZKP platform: Sismo
Private Airdrop: Stealthdrop
Anonymous communication: heyanon
first level title
4. Identity will be the entrance to Web3
When we look back at the changes in Web2 portals, the sequence of development is: portals - search engines - PC-side social platforms - mobile social platforms. It can be seen that traffic portal products are all from single-function, passive, complex to comprehensive , initiative, simplicity of change. Although at this stage, the project party cuts the identity and account system from different angles, presenting a trend of flourishing, as users, we cannot enter through complicated and complicated entrances for a long time, and the traffic will always tend to be convenient and one-stop integrated entrances.
We optimistically predict that this traffic portal will have the following characteristics:
Unified identity: a unified and interoperable identity layer, with records similar to the Sesame Credit scoring system, all user interactions on the chain form a web3 unified identity certificate
Super traffic front-end: We believe that one or several super account systems similar to WeChat will be formed in the future, and the most reasonable form of this system is the wallet
Decentralized backend: Relying on the composability of the blockchain, the backend of the wallet can integrate various protocols such as social/game/Defi/identity/payment for safe use by users
Privacy protection: Multiple privacy middlewares are combined to provide powerful end-to-end communication encryption, identity authorization and personal information protection measures
Multiple security: With the development of cryptography and AA, better and more multiple security mechanisms can be selected; the future key management mechanism (MPC/multi-signature/no mnemonic) should also allow users to choose independently to meet different types of customers need
User-owned: personal information/social data/identity credentials are stored in decentralized storage solutions such as Arweave or IPFS, and are only controlled by the user's own key.
Native commercialization: support native encryption payment, simplify cross-chain interaction gas fee
first level title
Reference
https://www.w 3.org/TR/vc-data-model/#what-is-a-verifiable-credential
https://www.odaily.news/post/5181202
https://medium.com/1kx network/towards-digital-self-sovereignty-the-web3-identity-stack-874d5e015bae
https://www.w 3.org/TR/did-core/
https://www.dock.io/post/decentralized-identity
https://vitalik.ca/general/2023/01/20/stealth.html