Private key leakage caused 160 million sky-high losses. You need to know these things about private keys
The modern cryptography of cyberpunk is not as simple as knocking on the glass and saying "there is an insider, terminate the transaction".
Two days ago, crypto market maker Wintermute was hacked. Due to a loophole in the way Profanity was used to generate Ethereum addresses, the private key was leaked, and $160 million was missing.
As early as January of this year, someone raised a problem on GitHub that Profanity might generate vanity.
Since then, it has also been demonstrated that all 7-character vanities can be brute-forced within 50 days by using 1,000 powerful graphics processing units (GPUs).
In our analysis article last week【Wintermute's $160 million sky-high price loss, or private key leak due to Profanity], we also mentioned that on September 15 this year, 1inch published an article on Medium disclosing the Profanity vulnerability, and introduced in detail how they used vanity to generate private keys for users.
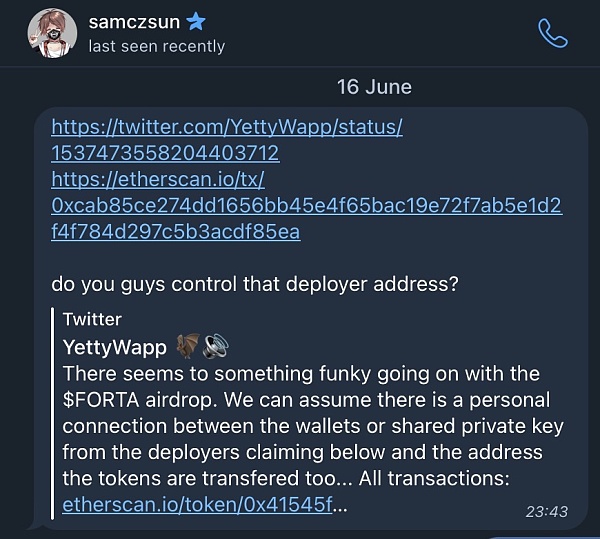
In June 2022, a 1inch participant received a strange message from @samczsun about suspicious activity from one of the 1inch deployed wallets as well as Synthetix and a few others.
secondary title
So what exactly is a private key?
How is the public key that often appears in "pairs" with the private key formed?
Cryptography
Cryptography
When cryptography first appeared, the military and academia had an encrypted version of the process-encoding information and decoding it with a set of code words. But the design also has a flaw: Once the encrypted and decrypted phrases are known to others, they can interpret and send the information at will.
Early encryption techniques were called "symmetric encryption" because the encoding and decoding phrases were the same.
It wasn't until the 1970s that cryptographers invented "asymmetric encryption" -- creating public and private keys that split the encryption process in two.
In this system, the private key is a multi-digit, random prime number that can be used as an ID to encrypt and decrypt information.
This private key is then used to generate a public key through a mathematical function called "elliptic curve multiplication". The elliptic curve multiplication function is one of the main technologies for implementing cryptocurrencies. It is a cryptographic scheme based on the difficult problem of addition order.
private key
private key
A private key is like a credit card PIN — in crypto, you don’t even need to know the card number to access the funds on the card and make transactions. This means that private key = asset, and its importance is self-evident.
The private key can choose to be kept by yourself or handed over to other organizations for the responsibility⬇️
1. Users who place assets in escrow wallets and centralized exchanges entrust the responsibility of keeping their private keys to these institutions.
secondary title
The relationship between public and private keys
Public and private keys are mathematically interrelated extremely large prime numbers. Association means that anything encrypted by a public key can only be decrypted by the associated private key. The public key is derived from the private key, which is a long sequence of numbers that acts as a passport to send funds to an address, like a bank card number.
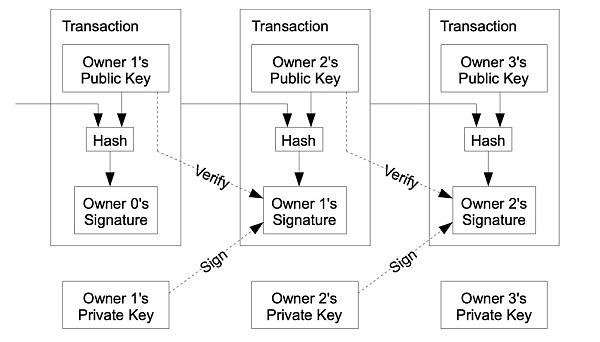
This function is very similar to an address in reality. For example, if I know your home address, I can send you a letter. Similarly, if in the encrypted world, I know your public key, I can send you encrypted currency or NFT. When Satoshi Nakamoto designed the operation of blockchain transactions, he introduced in detail how public and private keys can implement transactions through digital signatures.
In the white paper, Satoshi Nakamoto wrote: "Each owner transfers tokens to the next by digitally signing the hash of the previous transaction and the public key of the next owner and adding them to the end of the token. owner."
image description
secondary title
Web3.0 security
The Wintermute attack tells us: If the wallet address is generated with the Profanity tool, then the assets in the wallet will no longer be safe, please transfer all funds as soon as possible. In addition, if you use Profanity to obtain a vanity smart contract address, please ensure that the owner of the smart contract can be changed.
For other users, understanding private and public keys, and how they interact is fundamental to understanding Web 3.0. When it comes to staying safe, the CertiK Security Team hereby recommends:
1. Do not disclose the private key under any circumstances
2. Carefully choose to hold the private key yourself or entrust it to relevant institutions such as wallets or exchanges
Never import keys from one wallet to another
Use a hardware wallet
Use a software wallet that offers advanced security features
The transparency of the blockchain allows for things likeas well asas well asSkyTraceSuch blockchain analysis tools come in handy.
This is critical to Web 3.0 security - when an attack occurs, it helps us understand what happened, where the stolen funds went, and how to mitigate the damage.
In particular, SkyTrace can track and visualize the flow of funds between wallets through the public key, which in turn provides a way for the project to track stolen funds and potentially lead to information about hackers.
The same is true for the Skynet dynamic scanning system, which can generate real-time insights based on project liquidity, token distribution, and any abnormalities by actively monitoring on-chain activities.
But transparency helps us track down relevant information, and it also helps hackers choose targets. Because of this, some platforms such as Coinbase will generate a new address for users every time they trade, so that third parties cannot just view users' transactions through blockchain explorers. This also guarantees the privacy of Web3.0 to a certain extent.



