What risks and opportunities will the rise of the application chain bring?
This article comes from MediumThis article comes from
, the original author: Mohamed Fouda, compiled by Odaily translator Katie Ku.
We have found many optimal application scenarios for Lisk. Additionally, we identified gaps that needed to be filled, and the business opportunities within them.
secondary title
Why can the application chain go out of the circle?Furthermore, this design allows optimization of chain technology architecture, security parameters, throughput, etc. to match application requirements.
secondary title
The application chain is like a small town with a single industry
Universal computing chains like Ethereum and Solana are like metropolises with different infrastructures to support different types of businesses (applications). This makes Universal Chains more popular and more congested, which also results in more expensive and busier systems. But this popularity creates a lot of traffic and opportunity for businesses in the ecosystem. It's easy to switch from one industry to another. It is also possible to combine different businesses to create new and interesting businesses.
On the other hand, Lisk is like a small town with a single business activity. Towns can make their own rules and policies. Less crowded and cheaper, but probably not as well connected to the outside world. Everyone in town is using the only business in town. If it's popular and unique enough, customers will even come to the place for that particular business.
This analogy can also be extended to describe the difference in security between the two scenarios. Big cities have bigger, richer and more powerful people. Having a safe and secure city is in the common interest of all businesses in the city. These factors make large cities more difficult to attack. On the other hand, the safety of a small town is closely linked to the popularity and success of a single industry. If the business is doing well, the number of town residents will increase and become stronger, if the business is bad, people will leave, making the town less safe and more vulnerable to attack.
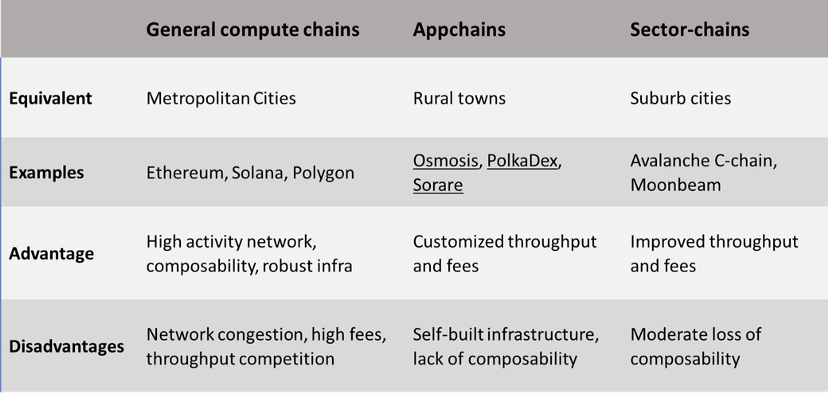
General computing chains, application chains, and industry-specific chains provide the required diversity to coexist and address different needs. It is important to identify which use cases require application chains and which use cases require building smart contracts on general computing chains or industry-specific chains.
first level title
Next we will discuss the most common scenarios where building an AppChain is the best choice.
secondary title
Application builders on the ecosystem, such as Cosmos and Polkadot, basically need to build their applications as application chains. Both protocols focus on building an ecosystem of multiple interconnected chains. The main chains in both ecosystems do not implement an execution engine that supports smart contracts. Therefore, to build any application, either build an application chain, or use a chain that implements a general-purpose computing execution engine.
secondary title
application requirements
Another best way to build an application chain is when the application throughput requirements or fee requirements cannot be met by general-purpose computing chains. Applications that require Web2 performance in a permission-exempt Web3 environment should consider AppChain as a first choice. Gaming applications are the best example of such applications. Most interactive games require extremely high throughput to support user game interaction. Also, transactions should be free, or have negligible fees. These requirements cannot be met using a general computing chain, and a dedicated application chain needs to be launched. for example:
Sorare - Fantasy football game released as StarkEx L2.
secondary title
If the application requires a specific technology that is not available on the L1 chain, then another option is to build an application chain that implements that technology. The best examples are zero-knowledge proofs like zk-Snarks or zk-Starks. Privacy-focused applications such as private payments or private transactions require zk proofs as building blocks. However, generating zk proofs requires a lot of computation, and these computations are too expensive to perform on-chain. In this case, the best way is to implement the required technology on Lisk. Examples of this approach include Aztec, a privacy-preserving payment and transaction application on Ethereum.
secondary title
Improving Applied Economics
Yuga Labs splitting the BAYC ecosystem into an independent chain is the best example. The BAYC community paid huge fees to the Ethereum network during the project NFT mint. The community still has to pay the Ethereum network substantial fees for transactions of these assets. Transferring to their ApeChain will keep these fees in BAYC's economic system.
first level title
Although Lisk has many advantages, risks also need to be considered. Building an application chain is much more complicated than developing a smart contract. There is a need to develop infrastructure that is not related to the core business of the application. Additionally, Lisk increases security and composability risks.
secondary title
Security risks
Smart contract applications derive their security from the underlying L1. As discussed earlier in the metropolitan analogy, L1 security is maintained with a large number of L1 participants since the L1 supports multiple applications. This makes L1 more secure and harder to attack.
In Lisk, security depends heavily on the adoption of the application and the price of the application's native token. The application chain can be an L2 sequencer or an independent PoS validator. In both cases, validator incentives are often expressed in native application tokens.
Validators must hold native tokens and run complex infrastructure for a long time to participate in the network. Validation rewards need to be higher than the operational costs and token risks borne by validators. The risks of this model are:
Staking exposure can complicate attracting professional validators to the network and instead attract amateur validators, which can compromise network security and uptime;
If application adoption is low and token prices are low, the network is less secure and malicious actors can obtain enough stake to attack the network at low cost.
secondary title
High initial investment cost
In general, building Lisk requires larger teams, adding costs that startups cannot afford, especially in the early stages. Deviating from core application logic can be a barrier to rapid application adaptation and product-market fit.
secondary title
One of the main advantages of building applications as smart contracts is atomic composability (which happens automatically). Applications can build on each other, and users can seamlessly interact with multiple protocols in the same transaction. Lisk lacks this atomic composability, as each application is isolated from other applications. Interaction between applications requires cross-chain bridging or messaging, requires several blocks, and cannot be done atomically. However, this lack of atomic composability has given rise to startups that address this pain point.
secondary title
Cross-chain bridge riskIn these scenarios, Lisk may resort to using a centralized cross-chain bridge, such as a centralized exchange, or develop its own cross-chain bridge.
first level title
The challenges of the Lisk ecosystem create many opportunities for startups. Here we provide 8 major business opportunities for the project party.
secondary title
DeFi protocols in order to compete with Web2 performance need to be implemented as application chains. The Central Limit Order (CLOB) exchange is the first choice for this. The dYdX derivatives exchange kicked off this trend, and we expect spot and commodity exchanges to be built as Appchains in order to benefit from low fees and low latency. The key enabler is the use of a customizable technology stack that can be adjusted to the needs of the DeFi protocol.
secondary title
One of the issues limiting the adoption of AppChain for performance-constrained applications such as games is the limited implementation options. In this regard, StarkEx is a popular choice. We hope to see startups building new effective architectures for on-chain games that support more than 100,000 TPS.
secondary title
Launching a sidechain or rollup with the appropriate architecture to support a specific application is a complex task. If a developer platform can accomplish this task, it will be very valuable, such as Alchemy of Lisk.
secondary title
Similar to zk proofs, AI is a transformative technology that is also computationally intensive. Therefore, AI-enabled applications cannot be built on-chain. There are many successful Web2 AI products that require users to pay substantial subscription fees. AI applications can be made available to the public through the application chain. Consider building applications that run trained AI models, such as Dall-E or GPT3, which are available to the public.
secondary title
5. Composability solves abstract cross-chain communication
The lack of atomic composability in Lisk presents an opportunity for startups to abstract cross-chain messaging and create composability.
Build a wallet for secure multi-chain accounts through multi-party computation (MPC), and natively handle cross-chain activities by executing transactions on multiple chains simultaneously. For example, cross-chain arbitrage.
secondary title
While Lisks have some advantages in terms of throughput, they also lead to decentralized liquidity, which leads to increased latency and a degraded user experience. Cross-chain DeFi protocols can automatically divide transactions between different chains for better pricing, and will have a better user experience and a larger customer base.
secondary title
There are Cosmos, Polkadot and EVM L2 for running application chains. One possible way to improve composability is to build a general-purpose trustless cross-chain messaging protocol that can connect EVM L2, Cosmos Zone, Polkadot parachains, etc. This product could replace existing cross-chain bridges and bring billions of dollars in traffic every year.
secondary title
The security challenges of Lisk can be alleviated by using products that support cross-chain security. Similar to merge-mining of PoW chains, we envision ways to achieve shared security between unrelated PoS chains, e.g. validators secure AppChains with ETH instead of native AppChain tokens. Liquidity staking protocols could play an important role in this process.
secondary title
Promote application chain landing projects
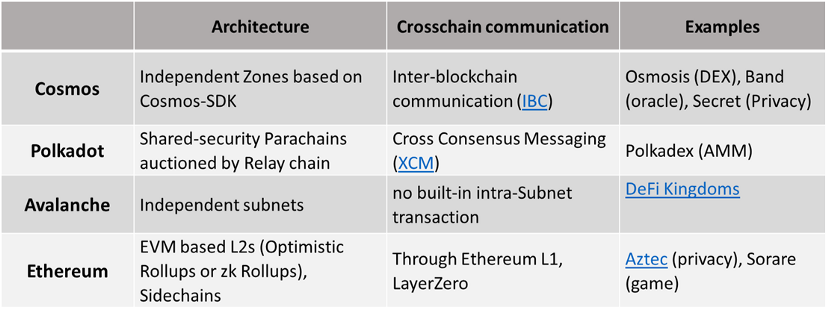
Cosmsos Zones
Lisk can be implemented in a number of ways, varying in complexity and security. There are four projects to promote the implementation of application chain.
secondary title
Ethereum L2
Summarize
Summarize



