Slow Mist: Taking stock of typical security incidents in 2021 and reviewing the ecological security situation of the blockchain
first level title
secondary title
Policy, Compliance, Regulation
From the perspective of the domestic environment, on the one hand, the government has increased its emphasis on the R&D and application of blockchain technology. The Ministry of Industry and Information Technology pointed out that the service capabilities of blockchain and other facilities will be significantly enhanced by 2025; on the other hand, the government will continue to tighten regulations on cryptocurrencies. Supervision. In September, multiple departments issued the "Notice on Further Preventing and Dealing with the Risk of Hype in Virtual Currency Transactions", and the National Development and Reform Commission and other departments jointly issued the "Notice on Rectifying Virtual Currency "Mining" Activities." Relevant materials show that policy documents related to blockchain-related content issued at the national level in 2021 cover university research, talent cultivation, technology application standards, intellectual property rights, digital agriculture, shipping transportation, epidemic prevention and control, network security, and social assistance. , digital culture industry, etc.
As can be seen,
As can be seen,secondary title
technology, application, economy
our country"Blockchain + Industry"2021,
2021,Blockchain underlying technologysecurity incident
security incident
Blockchain technology is a double-edged sword. While its decentralization, anonymity, and non-tamperable characteristics promote industrial progress, blockchain security issues have also increased significantly. Cryptocurrency crimes are various, such as money laundering, fraud, Cases of theft, drug trafficking, and mining crimes occur frequently.
image description
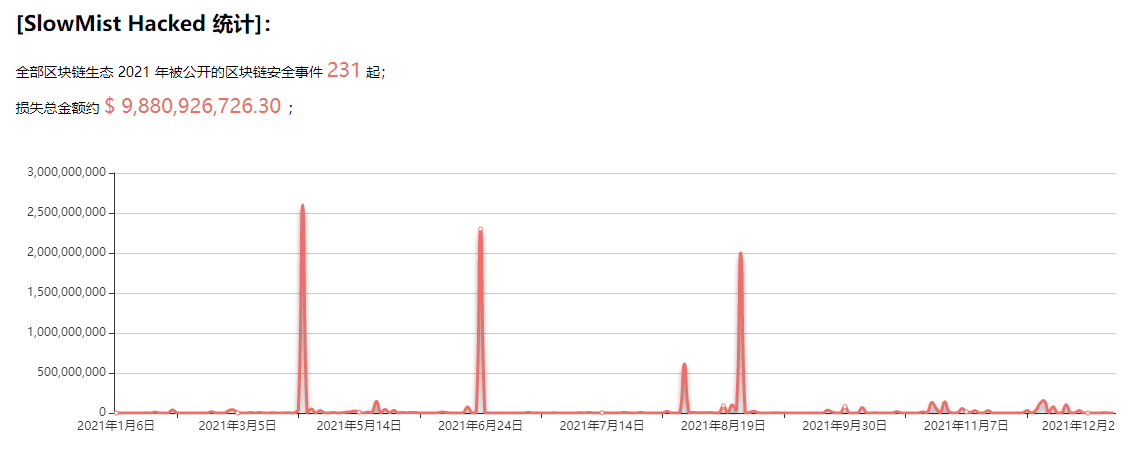
(Source: hacked.slowmist.io)
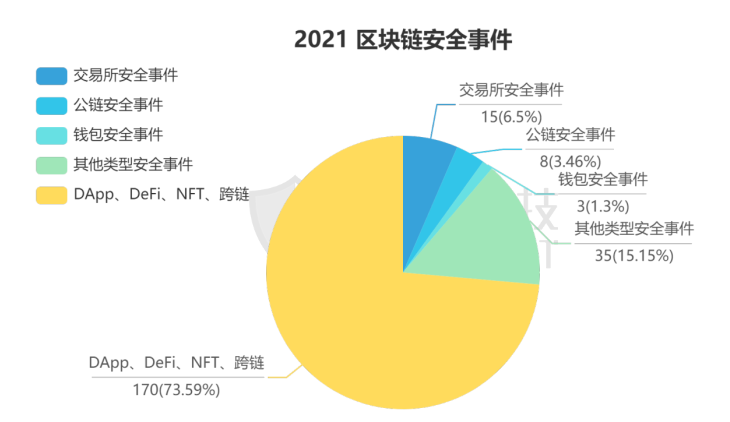
Among them, there were 170 security incidents of various ecological DApps and DeFi, 15 security incidents of exchanges, 8 security incidents of public chains, 3 security incidents of wallets, and 35 security incidents of other types.
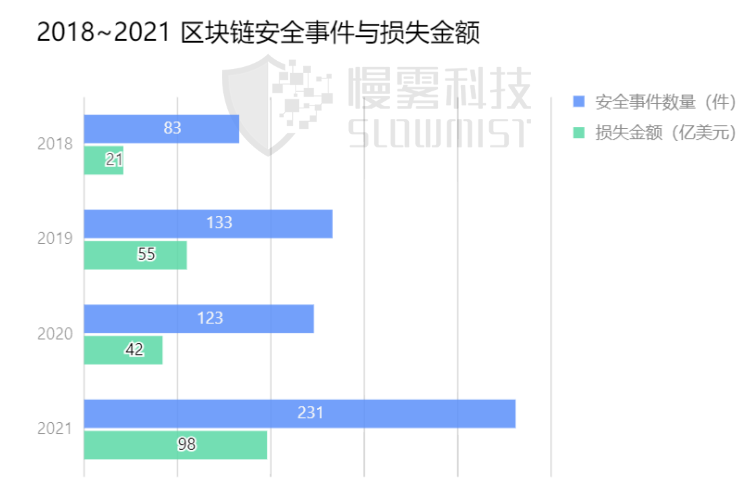
Since 2018, the overall loss trend is still on the rise.
first level title
public chain
public chain
BSV under 51% attack
On August 4, BSV was suspected to have suffered a 51% attack, and nearly 100 blocks were reorganized.
ETC mainnet encounters a fork
On September 4th, Ethereum Classic (ETC) tweeted that the ETC mainnet suffered a fork due to a vulnerability in the Ethereum client Geth.
Solana's mainnet beta suffers denial of service attack
On September 14, the Beta version of the mainnet of the public chain Solana began to experience instability since 19:52 Beijing time. On September 21, Solana officially released a preliminary overview of the network interruption: the Solana network was offline for 17 hours, and there was no loss of funds. Full functionality was restored within 24 hours. The cause of the network downtime is a denial of service attack. At 12:00 UTC, Grape Protocol launched an IDO on Raydium, with bot-generated transactions congesting the network. These transactions created a memory overflow that crashed many validating nodes, forcing the network to slow down and eventually stop.
slow fog view
exchange
exchange
Cryptopia Hacked Again
On February 20, New Zealand exchange Cryptopia was hacked again, and investigations revealed that hackers accessed a wallet that had been dormant since the hack in January 2019. The wallet belongs to Stakenet and is controlled by Cryptopia liquidator Grant Thornton. According to the findings, the dormant wallet held approximately $1.96 million worth of Xtake, Stakenet’s native token.
Liquid Hot Wallet Hacked
On August 19, Japanese crypto exchange Liquid said its hot wallet had been attacked. The SlowMist AML team used its MistTrack anti-money laundering tracking system to analyze and analyze the statistics. Liquid lost a total of about 91.35 million U.S. dollars (based on the price on the day of the incident), and the stolen currencies involved BTC, ETH, ERC20 tokens, TRX, TRC20 tokens, XRP There are more than 70 kinds of currencies, and the amount of money is so high that it is amazing.
slow fog view
Exchange security has become the primary concern of exchanges and users, and has even become the key to the survival of exchanges. Especially in the fourth quarter of this year, various exchanges were attacked one after another, causing heavy losses.
Exchanges are frequently attacked for the following reasons: (1) Exchanges gather a large amount of funds and have always been the target of hackers; (2) In most cases, exchanges have weak defenses, which are prone to security holes, and are easy to be hacked by hackers from weak points (3 ) Users lack sufficient security awareness; (4) Internal crimes.
wallet
wallet
Ledger wallet leaked multiple times
On June 18, Bitcoin hardware wallet provider Ledger reminded users that a series of new types of scams have recently occurred using fake Ledger hardware wallets to defraud users of their assets. Some users whose information was leaked a year ago received requests to replace their hardware wallets. package, which included a fake official letter and a tampered Ledger hardware wallet. Ledger stated that the letter about "need to replace the existing hardware wallet to protect your funds" is a scam, and the attached Ledger Nano is also fake. If the user enters the seed words according to the instructions in the letter, the user's encrypted assets will be stolen .
Multiple Chivo wallets stolen
Chivo Wallet is a national digital wallet released by the El Salvador government on September 7th to implement the Bitcoin Act. To this end, El Salvador promises that users who download and authenticate Chivo Wallet will receive a $30 bitcoin reward. The move brought the official Salvadoran wallet to more than 2 million users within a month. However, between October 9 and October 14, El Salvador-based human rights organization Cristosal received 755 notifications of Salvadorans reporting Chivo wallet identities stolen.
slow fog view
secondary title
DApp, DeFi, NFT, cross-chain
(1) ETH ecology
SushiSwap Hacked Again
On January 27, SushiSwap was attacked again, losing 81 ETH. This attack is similar to SushiSwap's first attack, both by manipulating the exchange price of trading pairs to generate profits. This attack took advantage of the fact that DIGG itself does not have a WETH transaction pair, and the attacker created this transaction pair and manipulated the initial transaction price, resulting in a huge slippage during the fee exchange process. The attacker used a small amount of DIGG and WETH provides initial liquidity to obtain huge profits.
$12.15 million recovered after SIL theft
On March 19, a high-risk vulnerability appeared in the SIL.Finance contract of the DeFi aggregate financial service. Later, SIL.Finance issued a document stating that the incident was caused by a smart contract permission vulnerability, which in turn triggered a general-purpose front-running trading robot to submit a series of transactions for profit. After discovering that the smart contract could not be withdrawn due to high-risk vulnerabilities, after 36 hours of hard work by SlowMist and other parties, USD 12.15 million has been successfully recovered.
(2) BSC ecology
Compound Vulnerabilities and Proposals
On September 30, Compound, a decentralized lending protocol, confirmed via Twitter that after the implementation of Proposition 62, there was an abnormal distribution of COMP tokens in the liquidity mining of the protocol, and Compound Labs and community members are investigating. Compound said that deposits and borrowing funds have not been found to be at risk so far. Compound founder Robert Leshner stated that the problem appears to be that the initial rate of COMP token distribution under Proposition 62 was incorrectly set, resulting in too many COMP tokens being distributed. On October 4th, just as Compound was trying to patch the loophole, another $68.8 million worth of COMP tokens (a total of 202,472 COMP) was injected into the already vulnerable liquidity mining due to the call of the drip() function Token distribution contract.
Cream Finance hit by three attacks
On October 27, Cream Finance, a DeFi lending association, was attacked and lost about $130 million. The stolen funds were mainly Cream LP tokens and other ERC-20 tokens. It is reported that this is the third largest DeFi hack ever. In addition, Cream Finance has suffered multiple flash loan attacks before, losing $37.5 million in February and another $19 million in August.
(3) EOS ecology
The flash.sx smart contract was attacked by reentrancy
Since 11:28 UTC on May 14th, the flash.sx flash loan smart contract suffered from the "re-entry" attack vulnerability, and about 1.2 million EOS and 462,000 USDT were stolen successively. According to official sources, after EOS Nation's Lightning Loan was hacked, the project party initiated a proposal to directly change the hacker's EOS account permissions and transfer back assets.
PIZZA HACKED
At 8:00 p.m. on December 8, the hacker account itsspiderman used the overflow vulnerability to issue additional tripool market-making certificates out of thin air on eCurve, and pledged and lent most of the tokens in the agreement in PIZZA. Afterwards, hackers created more than 1.3 million accounts and dispersed the stolen assets. The loss of the PIZZA protocol in this attack is equivalent to about 5 million US dollars.
(4) Polygon ecology
Algorithmic stablecoin project SafeDollar under attack
On June 28, SafeDollar, an algorithmic stablecoin project on Polygon, was suspected of being hacked, and an unconfirmed contract seemed to have stolen $250,000 in USDC and USDT.
PolyYeld Finance contract exploited
Yield farming protocol PolyYeld Finance was attacked, and the project contract was used to mint 4.9 trillion YELD tokens and dump them in the secondary market.
(5) HECO ecology
HSO swept away 30,000 HT and ran away
On March 10, the oracle project HSO on the Huobi ecological chain HECO ran away with 30,000 HT after IDO, and the website and Telegram could not be opened. Afterwards, under the full promotion of relevant parties such as the HECO core code contribution team Star Lab, the HECO technical community, and the HECO White Hat Security Alliance, 24,823 HT have been recovered.
XDX Swap under attack
On July 2, XDX Swap (DDEX) on the cross-chain decentralized exchange DDEX on the Heco chain was attacked. The attacker made a profit of 85.17 ETH (about 176,000 US dollars) and cross-chained all of it to Ethereum. The DDEX code is suspected to have a backdoor. With the support and cooperation of DDEX, Star Labs, HECO White Hat Security Alliance, etc., XDX Swap has successively recovered most of the funds involved in this attack, with a total value of more than 5 million US dollars.
(6) Other ecology
NEAR ecosystem Ref.Finance was exploited due to a contract error
On August 15th, the Ref.Finance team of the NEAR ecosystem tweeted that at around 2:00 pm UTC on August 14th, the Ref team noticed the abnormal behavior of the REF-NEAR trading pair, and then found that the patch in the recently deployed contract A bug, which has been exploited by multiple users, affected approximately 1 million REFs and 580,000 NEARs.
Solana Ecosystem Solend Hacked
On August 19th, Solend, the Solana ecological lending agreement, tweeted that the agreement was hacked at 20:40 on August 19th, Beijing time. The attacker cracked the check for unsafe identities in the UpdateReserveConfig function, allowing it to liquidate all accounts . Additionally, the hacker set the APY of borrowed funds at 250%. During this period, 5 users' funds were misliquidated. Solend said that no funds were stolen from the attack and that it will increase the size of the bug bounty and build better monitoring and alerting systems.
The Polkadot ecological IDO platform Polkatrain was arbitraged
On April 5, an accident occurred on Polkatrain, the Polkadot ecological IDO platform. According to the analysis of SlowMist, the problematic contract this time is the POLT_LBP contract of the Polkatrain project. This contract has a swap function and a rebate mechanism. When the function purchases PLOT tokens, a certain amount of rebate will be obtained, and the rebate will be forwarded to the user through the _update function call transferFrom in the contract. Since the _update function does not set the maximum amount of rebates for a pool, and does not judge whether the total rebates are used up when rebates are made, malicious arbitrageurs can continuously call the swap function to exchange tokens to extract the value of the contract. Rebate rewards.
Avalanche On-Chain Lending Protocol Vee.Finance Hacked
On September 20, the Vee.Finance team of the Avalanche chain lending agreement noticed multiple abnormal transfers. After further monitoring, a total of 8804.7 ETH and 213.93 BTC were stolen (total value over 35 million US dollars). The stablecoin portion was not affected by this attack.
GrimFinance on the Fantom chain was attacked by flash loans
On December 19, GrimFinance, the compound income platform on the Fantom chain, suffered a flash loan attack, and the loss exceeded 30 million US dollars. The attacker uses the function named "beforeDeposit()" in GrimFinance's vault policy to attack and enter the malicious Token contract.
(7) Cross-chain system
Cross-chain transaction protocol THORChain was attacked three times
On June 29th, THORChain was attacked by "fake recharge" and lost nearly 350,000 US dollars; on July 16, THORChain was attacked by "false recharge" for the second time and lost nearly 8 million US dollars; on July 23, THORChain was attacked again, Losses of nearly $8 million.
Cross-chain bridge Chainswap is stolen and affects multiple platforms
On July 11, the cross-chain bridge project Chainswap was hacked again. More than 20 project tokens that deployed smart contracts on the bridge were hacked. The total loss is estimated to be 4 million US dollars, which has almost caused the scope of influence in DeFi history. Biggest safety incident ever. According to the Chainswap survey, due to a bug in the token cross-chain quota code, the on-chain exchange bridge quota is automatically increased by the signing node, which aims to be more decentralized without manual control. However, due to a logic flaw in the code, this led to a vulnerability that automatically increased the number by allowing invalid addresses that were not whitelisted. Previously, on July 2, Chainswap was also attacked by hackers, and some user tokens were actively withdrawn from wallets interacting with ChainSwap, with an estimated total loss of $800,000.
Poly Network's $610M Stolen Returned
The Aug. 10 Poly Network attack may be the largest cybersecurity incident in history, with more than $610 million in crypto assets stolen and returned within 15 days. The entire blockchain industry and all relevant parties have experienced this ups and downs together with Poly Network. At present, all the assets involved have been returned to the users, and the system functions have basically returned to the level before the incident.
(8)NFT
NFT Fraud Spreads
On Aug. 2, a scammer dubbed “cryptopunksbot” posted on CryptoPunk’s Discord server, offering NFT investors the chance to win 10 NFT avatars. NFT project founder Stazie lost 16 CryptoPunks, worth at least $1 million, for accepting posters with false offers. The fraudster then sold 5 CryptoPunks for 149 ETH ($385,000).
slow fog view
Since the birth of DeFi, it has been accompanied by countless risks. Although the value of many DeFi projects has been explosively doubling, hacking incidents have also intensified. According to statistics from SlowMist, DeFi usually has the following attack methods: (1) flash loan attack; (2) contract loopholes; (3) compatibility or architecture issues; (4) private key leaks or front-end attacks; (5) internal crimes, Run away.
other types
other types
blackmail
On May 7, Colonial Pipeline, the largest oil and gas pipeline operator in the United States, was forced to suspend operations due to a targeted ransomware attack. Afterwards, it paid 75 bitcoins, a ransom of more than $4 million, to restore operations to normal. The ransomware attack has caused global shock and widespread concern because it involves national-level critical infrastructure. In response to this incident, officials of the US Department of Justice stated that they have successfully recovered more than 2 million US dollars in ransom. However, U.S. government officials did not specify the detailed process of "how to obtain the private key and recover the ransom." They only said that this action shows that the United States will spare no effort to deal with blackmail attacks.
fraud
fishing
fishing
On October 15, Sophos released a report claiming that crypto fraud app CryptoRom stole $1.4 million by exploiting the "Super Signature Service" and the Apple Developer Enterprise Program. Bitcoin addresses associated with the scam have sent over $1.39 million to date, and there may be many more addresses connected to the scam. Most of the victims were iPhone users, the report said. According to the report, CryptoRom bypasses all App Store security checks and remains active on a daily basis. The report also said that Apple "should warn users about installing apps, either through ad-hoc distribution or through enterprise provisioning systems, that have not been reviewed by Apple."
slow fog view
Summarize
Summarize
Although the market value of many cryptocurrencies represented by BTC has been refurbished, and the overall development trend of the blockchain industry is getting better and better, cryptocurrency crimes are also more rampant.From the statistical point of view, the months with more security incidents and larger losses are mainly in April, June and August; from the perspective of various ecology, the losses on Ethereum are the most, exceeding 1.3 billion US dollars, followed by BSC Ecology; From the perspective of attack areas, exchanges and DeFi are more attacked.
For the project party, it is recommended to improve the internal management and technical mechanism, and internal security personnel to check and fill in the gaps in security-related content in a timely manner. The most important and most effective way is to conduct a comprehensive and in-depth security audit on the project before it goes online to minimize the possibility of causing security problems.
For users, it is necessary to treat the blockchain correctly and rationally, establish correct currency concepts and investment concepts, and effectively improve risk prevention awareness. For example, before investing, you should pay attention to whether the smart contract is open source and whether the platform itself has a security audit. The most important thing is to keep your private key mnemonic and not disclose it to anyone.
Finally, I look forward to the new year of the blockchain that will burst out with greater energy, more landing applications will appear, and greater value will be created.