Kyberswap被盗4800万美元,戏精黑客却来主动谈判
原创 | Odaily星球日报
作者 | Loopy Lu

11 月 23 日,多链 DEX 聚合器 Kyberswap 近日遭受了严重的网络攻击,导致价值约 4830 万美元的各种加密资产被盗,主要包括 16, 217 枚 ETH(价值 3350 万美元)、 3, 987, 332 枚 ARB (价值 406 万美元)、 591, 441 枚 OP (价值 103 万美元)和 1, 111, 926 枚 DAI。
最新进展(11 月 24 日更新):
KyberSwap 团队在链上向黑客发布谈判信息,表示可以让黑客留下窃取资金的 10% 作为赏金,以安全返还所有用户的资金。KyberSwap 声称已知道黑客实施攻击的方式,限黑客在北京时间 11 月 25 日 14: 00 前将被盗资金的 90% 退还至0x 8180 开头地址,否则将继续追捕黑客信息。
数千万美元被盗
事件发生后,Kyber Network 团队在 X (Twitter) 帖子中提醒其用户,称 KyberSwap Elastic“经历了安全事故”。它建议用户提取资金作为预防措施,并补充说正在调查情况。
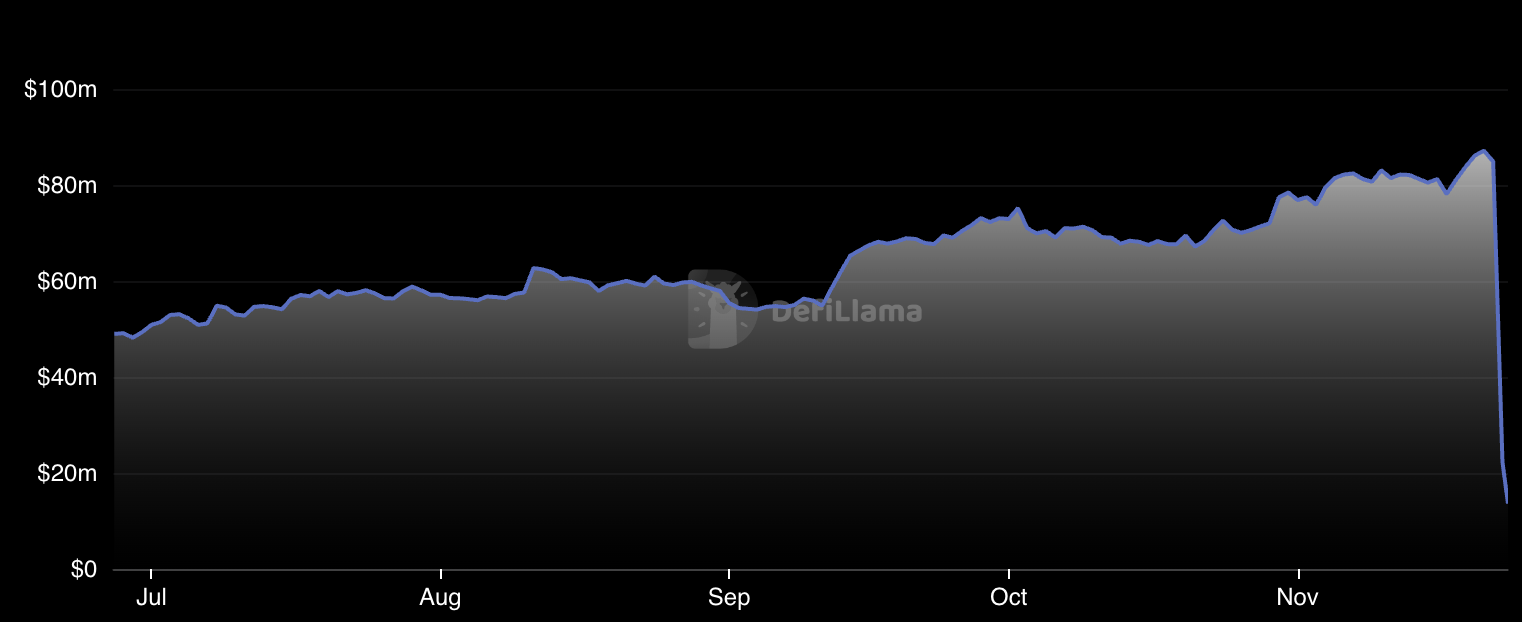
Kyber 于 2018 年推出,在黑客攻击之前的 TVL 约为 8600 万 美元,目前 TVL 已跌至 1300 万美元。
KyberSwap 是一个部署在 15 个区块链上的去中心化 DEX 及聚合器。官方介绍显示,该平台已经进行了超过 100 亿美元的总交易量和超过 200 万总交易笔数,并且集成了超过 100 个 DEX。
(KyberSwap 已在 15 条链上可用)
而链上数据显示,本次 KyberSwap 被盗也发生在了多个网络之上。Spot On Chain 监测,KyberSwap 被盗发生在包括 Arbitrum、Optimism、Ethereum、Polygon 和 Base。
其中,价值约 2000 万美元的代币从 Arbitrum 网络中被盗, 1500 万美元从 Optimism 网络中被盗,超过 700 万美元从以太坊被盗。
需要注意的是,这并不是 KyberSwap 首次被盗。2022 年 9 月,KyberSwap 前端漏洞导致 265, 000 美元用户资金被盗 。
KyberSwap 被盗事件,再一次引起了加密行业对 DEX 安全性的的广泛关注。Odaily星球日报提醒广大用户,安全风险发生时,用户应及时提取资金并 revoke 权限。
“我先歇会,晚点联系”
而本次事件与以往的攻击事件有所不同的是,黑客对在链上进行的操作加入了丰富的注释。这种行为让本次攻击充满着别样的意味,我们很难评价这究竟是嘲讽,抑或是教学。
黑客操作较为复杂,我们截取了主要流程如下:
1、开始行动
2、找到流动性请求源
3、构建虚假流动性
4、完成攻击
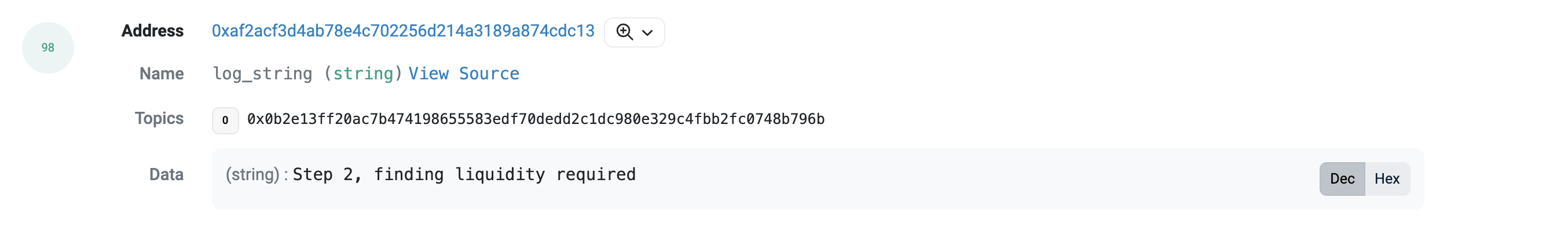
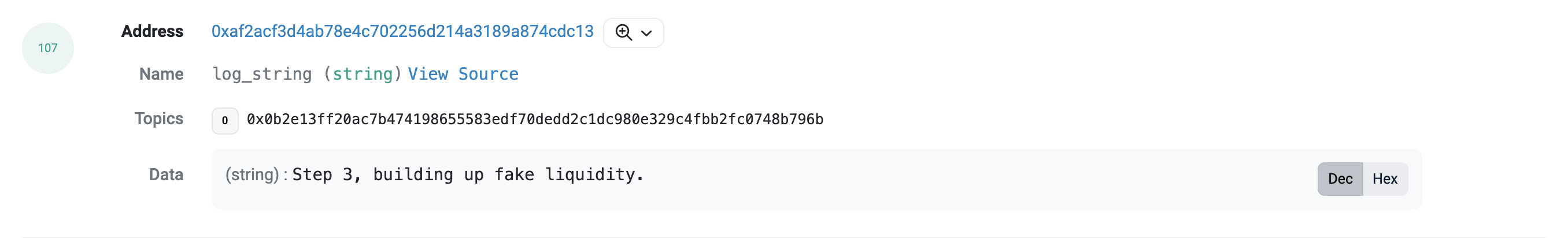
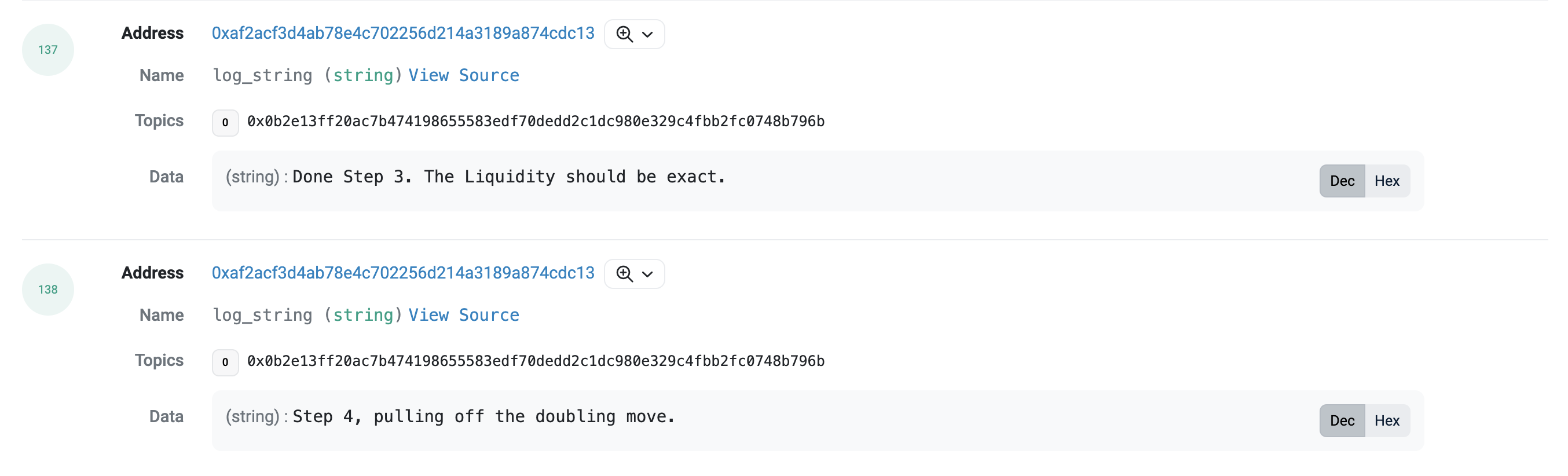
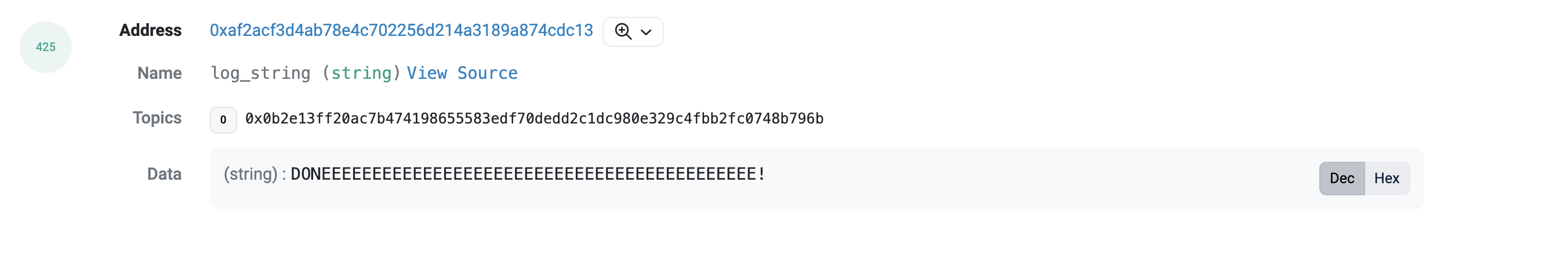
我们看到,黑客在最后发出一条 DONEEEEEEEEEEEEE 的信息,拖长的尾音直抒了黑客心中的欣喜之情。
更有趣的是,此次黑客的目标似乎并不在于耗尽 Kyber 的流动性,而是意图通过谈判来获得自己本次攻击的成果。
攻击者给协议开发者和 DAO 成员留下了一条链上消息,称“当我休息好后,谈判将在几个小时内开始”。
社区推测,这意味着黑客似乎并不想背负着司法风险拿走全部的被盗资产。黑客很可能会以谈判和解的方式与项目团队达成共识,仅拿走部分被盗资金,以此换取项目团队的不再追究。
KyberSwap 在 2022 年 9 月曾遭受价值 26.5 万美元的黑客攻击,后来得到币安的协助解决。当时 KyberSwap 向黑客提供了 15% 的赏金,约 4 万美元。
黑客或为累犯
这次攻击被认为是针对 LP 的直接攻击,而非 DEX 授权代码的漏洞。黑客通过精心设计的攻击策略,成功绕过了交易所的多层安全防护。
安全团队 BlockSec 认为,KyberSwap 通过价格操纵和双重流动性计数实现攻击。攻击者借入了闪电贷,并耗尽了流动性较低的资金池。通过执行 Swap 和改变头寸,他们操纵了受害池的实时价格和价格变动。最终,攻击者触发了多个交换步骤和交叉报价操作,导致双重流动性计数,从而耗尽资金池。
而另一个“彩蛋”是:该名黑客似乎并不是第一次作案。
派盾监测,标记为 Kyber Network 攻击者的地址已将 1, 000 枚 WETH(206 万美元)转移到 Arbitrum 上尾号为“adb4”的一个地址。该地址 705 天前在以太坊上与 Indexed Finance 攻击者进行了交互。
2021 年 10 月,被动收益协议 Indexed Finance 遭到攻击,损失达 1600 万美元。
Kyberswap 事件是对整个加密货币交易领域的一次严重警告,提醒所有参与者必须提高警惕,加强安全措施。随着加密市场的不断发展,确保交易平台的安全将成为行业持续关注的重点。Kyberswap 安全事件引起了整个行业对于去中心化交易平台安全性的深刻思考。
面对日益复杂的安全挑战,DEX 仍需不断创新和完善其安全技术。这包括加强智能合约的安全审计,提升异常交易检测能力,以及开发更加高效的应急响应机制。同时,加强用户教育和意识提升也是预防安全事件的重要环节。用户需要了解相关风险,并采取适当措施保护自己的资产安全。
而等待黑客睡醒之后,KyberSwap 的谈判是否顺利?黑客又要如何收场?Odaily星球日报将持续追踪报道。



