คีย์ส่วนตัวของ Wintermute ถูก "เจาะโดยเดรัจฉาน" และสูญเสียเงินไป 160 ล้านดอลลาร์สหรัฐ ทรัพย์สินข
เมื่อวันที่ 20 กันยายน Wintermute ถูกขโมยไป
การโจมตีนี้ไม่เพียงแต่ทำให้ Wintermute สูญเสียเท่านั้น แต่ยังเสี่ยงที่อาจถูกมองข้ามได้ง่ายอีกด้วย แฮ็กเกอร์ใช้วิธีการโจมตีที่ค่อนข้างหายาก นั่นคือ "การถอดรหัสคีย์ส่วนตัว" ซึ่งทำให้ผู้ถือสกุลเงินทั้งหมดส่งเสียงเตือน แต่อย่ากังวลมากเกินไป การแคร็กคีย์ส่วนตัวนี้ไม่ใช่ภัยคุกคามต่ออัลกอริทึมการเข้ารหัสแบบ elliptic curve แต่เป็นช่องโหว่ด้านความปลอดภัยในเครื่องมือสร้างคีย์ส่วนตัวเสริม นักลงทุนที่ไม่ได้ใช้เครื่องมือที่มีความเสี่ยงคล้ายกันจะไม่เผชิญกับความเสี่ยงเดียวกันในขณะนี้
ชื่อเรื่องรอง
วิธีการโจมตีนั้นแปลกประหลาด และแฮ็กเกอร์ได้รับรหัสส่วนตัวของกระเป๋าเงินจริง
แตกต่างจากวิธีการโจมตีทั่วไปก่อนหน้านี้เช่น "ช่องโหว่" "เงินกู้ด่วน" และ "การควบคุมราคา" วิธีการขโมยของแฮ็กเกอร์นี้ไม่เป็นที่นิยมมากกว่า - การแคร็กกำลังดุร้าย
ทีมรักษาความปลอดภัยของ Beosin พบว่าผู้โจมตีมักใช้ที่อยู่ 0x0000000fe6a... เพื่อเรียกฟังก์ชัน 0x178979ae ของ 0x00000000ae34... สอบถาม ยืนยันว่าที่อยู่ 0x0000000fe6a มีสิทธิ์ตั้งค่า CommonAdmin และที่อยู่มีการโต้ตอบตามปกติกับสัญญาก่อนการโจมตี จากนั้นจึงยืนยันได้ว่ารหัสส่วนตัวของ 0x0000000fe6a รั่วไหล
ทีมรักษาความปลอดภัยหลายทีมได้เปิดเผยต่อสาธารณะว่าสัญญาอัจฉริยะและกระเป๋าเงิน EOA ของ Wintermute นั้นถูกขโมยโดยผู้โจมตี การสังเกตที่อยู่กระเป๋าเงินที่ถูกขโมยไม่ใช่เรื่องยากที่จะพบว่าที่อยู่นั้น "ปกติ" มากโดยเริ่มจาก 7 หลัก 0 การขโมยกระเป๋าสตางค์เกี่ยวข้องกับการใช้คำหยาบคายโดย Wintermute
คำหยาบคายคือเครื่องมือสร้างที่อยู่ EVM vanity ซึ่งผู้ใช้สามารถสร้างที่อยู่กระเป๋าเงินที่มีชุดอักขระที่กำหนดเองได้
ในความคิดเห็น GitHub ของ Profanity เรายังสามารถเห็นนักพัฒนาก่อนหน้านี้พูดคุยเกี่ยวกับโครงการ
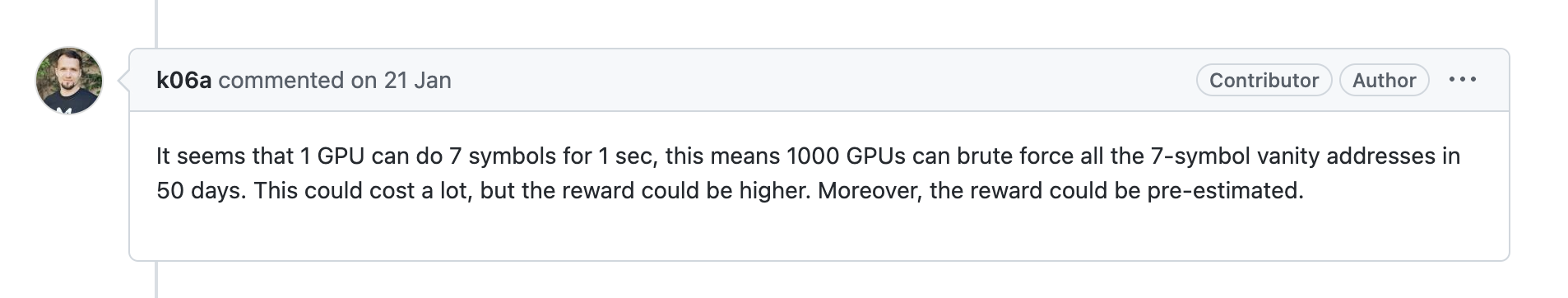
ผู้ร่วมก่อตั้ง 1inch ชี้ให้เห็นว่ามีข้อบกพร่องในการรักษาความปลอดภัยของเครื่องมือนี้ตั้งแต่เดือนมกราคมปีนี้: "GPU หนึ่งตัวสามารถคำนวณ 7 สัญลักษณ์ในหนึ่งวินาที และใช้เวลาเพียง 1,000 GPU ในการคำนวณที่อยู่ทั้งหมดภายใน 50 วัน ” ต่อจากนั้น ผู้พัฒนายังได้เพิ่มคำเตือนด้านความปลอดภัยในคำอธิบาย readme ของโครงการ และบอกผู้ใช้ว่า “ไม่แนะนำให้ใช้เครื่องมือนี้ต่อไปภายใต้สถานการณ์ปัจจุบัน”
ชื่อเรื่องรอง
มีการออกคำเตือนความเสี่ยงแล้วและไม่ได้ดึงดูดความสนใจ
ความเสี่ยงด้านความปลอดภัยของคำหยาบคายได้รับความสนใจจากอุตสาหกรรมเพียงไม่กี่วันก่อน Wintermute
เมื่อวันที่ 15 กันยายน บล็อกอย่างเป็นทางการของ 1inch Network ได้เผยแพร่บทความที่ระบุว่าคำหยาบคายมีความเสี่ยงด้านความปลอดภัย "หากที่อยู่กระเป๋าเงินของคุณถูกสร้างขึ้นด้วยเครื่องมือหยาบคาย ทรัพย์สินของคุณจะไม่ปลอดภัยอีกต่อไป ย้ายทรัพย์สินทั้งหมดของคุณไปยังกระเป๋าเงินอื่นโดยเร็วที่สุด!"
การวิจัยของ 1inch พบว่าแฮ็กเกอร์ใช้ช่องโหว่ Profanity ด้วยวิธีต่อไปนี้:
1. รับรหัสสาธารณะจากที่อยู่ปลอม (กู้คืนจากลายเซ็นการโอน)
2. ปรับขนาดตามกำหนดเป็น 2 ล้านคีย์สาธารณะ
3. ลดและจำกัดขอบเขตซ้ำๆ จนกว่าจะได้รับคีย์สาธารณะของเมล็ด
ด้วยวิธีนี้ แฮ็กเกอร์สามารถรับรหัสส่วนตัวของที่อยู่ใดๆ ที่สร้างขึ้นโดยใช้ Profanity
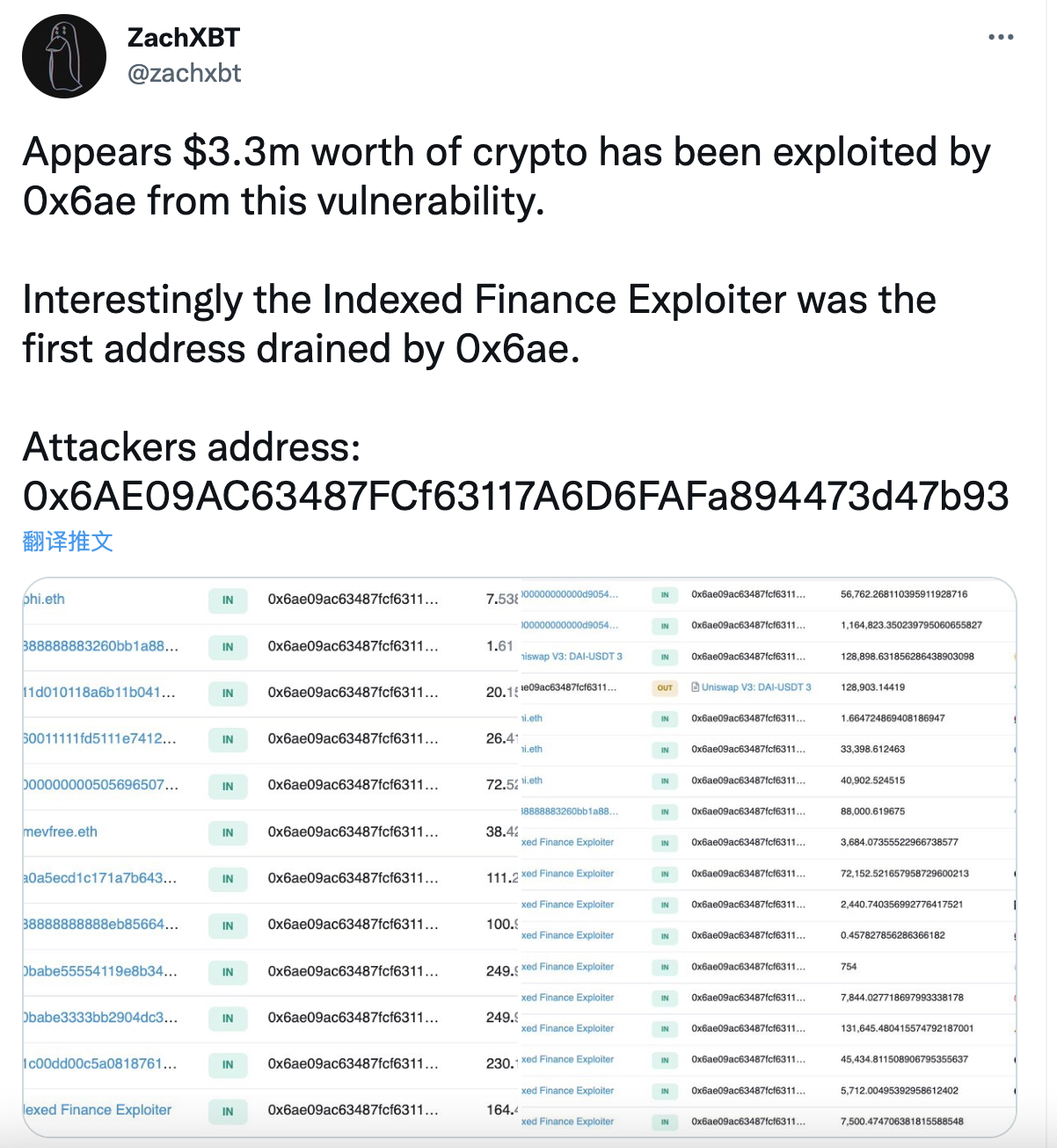
การสำรวจครั้งต่อมาที่จัดทำโดยนักวิจัยบล็อคเชน ZachXBT แสดงให้เห็นว่าแฮ็กเกอร์ได้ขโมยทรัพย์สินมากกว่า 3.3 ล้านดอลลาร์ผ่านทางช่องโหว่นี้
ชื่อเรื่องรอง
Wintermute กล่าวว่ากิจกรรมนี้จะไม่เข้าสู่ตลาด
ได้รับการยืนยันจากหน่วยงานด้านความปลอดภัยหลายแห่ง ที่อยู่ของผู้โจมตีถูกล็อกเป็น "0xe74b28c2eAe8679e3cCc3a94d5d0dE83CCB84705" สัญญาอัจฉริยะของผู้โจมตีคือ "0x0248f752802b2cfb4373cc0c3bc3964429385c26"
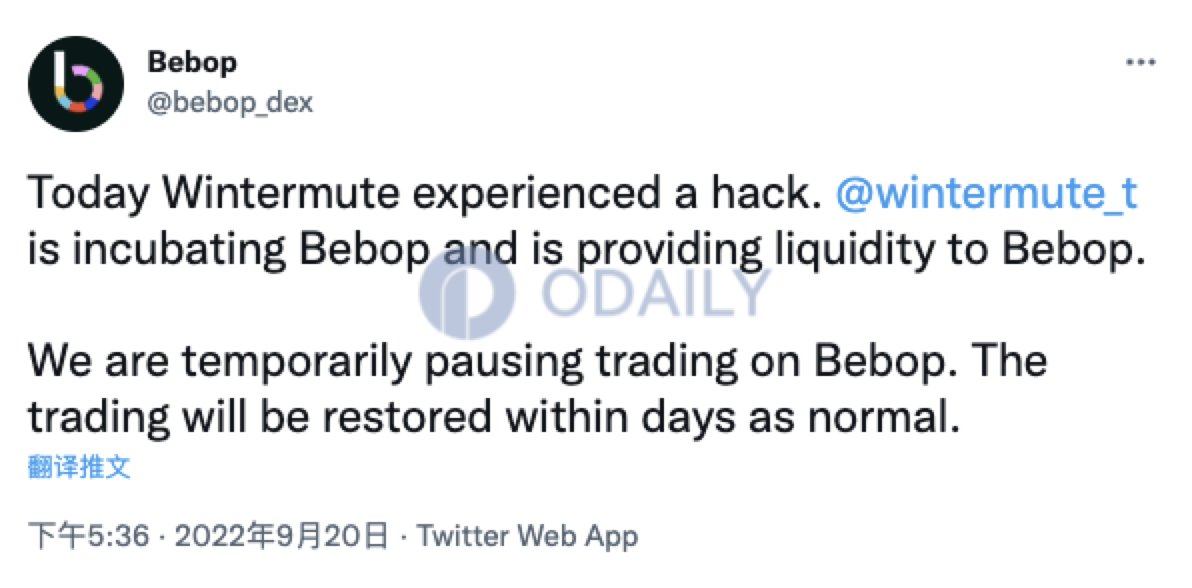
หลังจากการโจมตีครั้งนี้ นอกจากกระเป๋าเงินที่ได้รับผลกระทบแล้ว Bebop ซึ่งเป็นการแลกเปลี่ยนแบบกระจายอำนาจที่เปิดตัวโดย Wintermute ก็ได้รับผลกระทบเช่นกัน Twitter อย่างเป็นทางการของ Bebop ประกาศว่าแพลตฟอร์มได้ระงับการทำธุรกรรมและจะกลับมาทำงานอีกครั้งภายในสองสามวัน นอกจากนี้ยังระบุด้วยว่าสัญญาจะไม่ได้รับผลกระทบ และเงินของผู้ใช้และคีย์ส่วนตัวจะปลอดภัย
จากสินทรัพย์ 90 รายการที่ถูกแฮ็ก มีเพียง 2 รายการเท่านั้นที่มีมูลค่าตามสัญญามากกว่า 1 ล้านดอลลาร์ (และไม่เกิน 2.5 ล้านดอลลาร์) Wintermute กล่าว ดังนั้นจึงไม่คาดว่าจะสร้างแรงกดดันขายในตลาดมากนัก นอกจากนี้ ธุรกิจ CeFi และ OTC ของบริษัทยังไม่ได้รับผลกระทบ
ในเวลาเดียวกัน Evgeny Gaevoy ยังกล่าวด้วยว่าความสามารถในการชำระหนี้ของ Wintermute ในปัจจุบันเป็นสองเท่าของส่วนของผู้ถือหุ้นที่เหลืออยู่ และบริการของ Wintermute อาจหยุดชะงักในวันนี้และอีกไม่กี่วันข้างหน้าก่อนที่จะกลับสู่สภาวะปกติ
ปัจจุบัน วินเทอร์มิวท์ยังคงเต็มใจที่จะถือว่าผู้โจมตีเป็น "แฮ็กเกอร์หมวกขาว" และเรียกร้องให้ผู้โจมตีติดต่อวินเทอร์มิวท์



