Spring Festival Asset Security Handbook: How to Protect Your Tokens While Relaxing with Family and Friends?
- Core Viewpoint: Increased fund flows and divided attention during the Spring Festival may amplify on-chain security risks. Users should conduct a systematic pre-holiday security check-up through three major measures: vigilance against AI scams, cleaning up wallet authorizations, and standardizing daily operations, to proactively manage risks.
- Key Elements:
- AI video and voice scam technologies are now mature. It is necessary to establish an offline verification mechanism independent of online communication and avoid clicking any suspicious links forwarded on social platforms.
- Utilize the pre-holiday time window to check and revoke authorizations for DApps no longer in use. Follow the principle of least privilege and separate the management of large assets from assets used for daily operations.
- When traveling, physically isolate seed phrases and avoid storing them on internet-connected devices. Be wary of prompts to download disguised applications in social settings. Always verify the full address before transferring funds and prioritize using the address whitelist feature.
- Phishing attacks using addresses with similar beginning and ending characters have become industrialized. Attackers cast a wide net by generating addresses in bulk. Users must verify the entire address string, not just the beginning and end.
- Mainstream wallets like imToken have built-in authorization detection and revocation features. Users can directly manage historical authorizations within the wallet, lowering the operational barrier.
As the Lunar New Year approaches, marking a time of bidding farewell to the old and welcoming the new, it's also a moment for reflection:
Over the past year, have you fallen victim to any Rug Pull projects? Have you bought into a project based on a shilling KOL's hype only to be left "holding the bag"? Or have you suffered losses from increasingly rampant phishing attacks by clicking malicious links or signing fraudulent contracts?
Objectively speaking, the Spring Festival doesn't create risks, but it can amplify them—when capital flow frequency increases, when attention is diverted by holiday arrangements, and when trading pace quickens, even a minor mistake can more easily escalate into a significant loss.
Therefore, if you're planning to adjust your portfolio or organize funds around the holiday, it's wise to give your wallet a "pre-holiday security checkup." This article will start from several real and high-frequency risk scenarios to systematically outline specific actions ordinary users can take.
1. Beware of "AI Deepfake" and Voice Simulation Scams
The recent viral SeeDance 2.0 has reminded everyone of a stark reality: in an era of accelerating AGI penetration, "seeing is believing" and "hearing is truth" are becoming obsolete.
It can be said that since 2025, AI-based video and voice fraud technology has become remarkably sophisticated. Techniques like voice cloning, video face-swapping, real-time expression imitation, and tone simulation have entered an "industrialized stage" characterized by low barriers to entry and scalable replication.
In fact, AI can now accurately replicate a person's voice, speech rate, pausing habits, and even micro-expressions. This means such risks are particularly prone to amplification during the Spring Festival.
For instance, imagine you're on your way home for the holidays or during a gathering with friends and family. Your phone buzzes with a message—a "friend" from your contacts sends a voice or video message via Telegram or WeChat. Their tone is urgent, claiming their account is restricted, they need funds for red packets, or require a small token advance for temporary coverage, and they ask you to transfer funds immediately.
The voice sounds perfectly natural, and the video even shows a "real person on camera." With your attention scattered by holiday activities, how would you judge the situation?
In previous years, video verification was almost the most reliable method. But today, even if the other party is speaking to you live on camera, it's no longer 100% trustworthy.
Against this backdrop, relying solely on a glance at a video or a snippet of audio is no longer sufficient for verification. A more secure approach is to establish an independent verification mechanism with your inner circle (family, business partners, long-term collaborators) that exists outside of online communication. This could be an offline passphrase known only to you, or specific detail-based questions that cannot be inferred from public information.
Furthermore, it's essential to re-examine a common pathway risk: clicking links forwarded by acquaintances. Traditionally, during the Spring Festival, campaigns under the guise of "on-chain red packets" or "airdrop benefits" easily become viral entry points for inducement within the Web3 community. Many people aren't scammed by strangers but by clicking on meticulously disguised authorization pages because they trust a forwarded link from an acquaintance.
Therefore, everyone should remember a simple yet critically important principle: Do not directly click on any links of unknown origin via social platforms, and certainly do not authorize anything, even if it comes from an "acquaintance."
Ideally, all on-chain operations should be conducted through official channels, bookmarked URLs, or trusted entry points, not within chat windows.
2. Conduct a "Year-End Cleanup" for Your Wallet
If the first type of risk stems from trust being forged by technology, the second type arises from hidden risk exposures we accumulate over time.
As is well known, approvals are the most fundamental yet easily overlooked mechanism in the DeFi world. When you interact with a DApp, you are essentially granting a smart contract permission to manage your tokens. This permission could be one-time or unlimited in amount, short-term, or remain valid long after you've forgotten about it.
Ultimately, an approval itself may not be an immediate risk point, but it represents a persistent risk exposure. Many users mistakenly believe that as long as assets are not stored within a contract, there is no security issue. However, during bull market cycles, users often frequently experiment with various new protocols, participate in airdrops, staking, mining, and on-chain interactions. Approval records continuously accumulate. When the hype fades and many protocols are no longer used, the permissions often remain.
Over time, these excess historical approvals become like a pile of uncollected keys. If a contract vulnerability emerges in a protocol you've long forgotten, it can easily lead to losses.
The Spring Festival serves as a natural organizing point. Utilizing the relatively calm pre-holiday window to systematically review your approval records is a highly worthwhile action:
Specifically, you can revoke approvals for protocols you no longer use, especially unlimited approvals. For assets held in large amounts for daily use, consider using limited approvals instead of long-term, open-ended permissions for the entire balance. Additionally, separate the management of long-term storage assets from assets used for daily operations, creating a structural hierarchy between hot wallets and cold wallets.
In the past, many users relied on external tools (like websites such as revoke.cash) for such checks. Today, mainstream Web3 wallets like imToken have built-in approval detection and revocation capabilities, allowing you to view and manage historical approvals directly within the wallet.
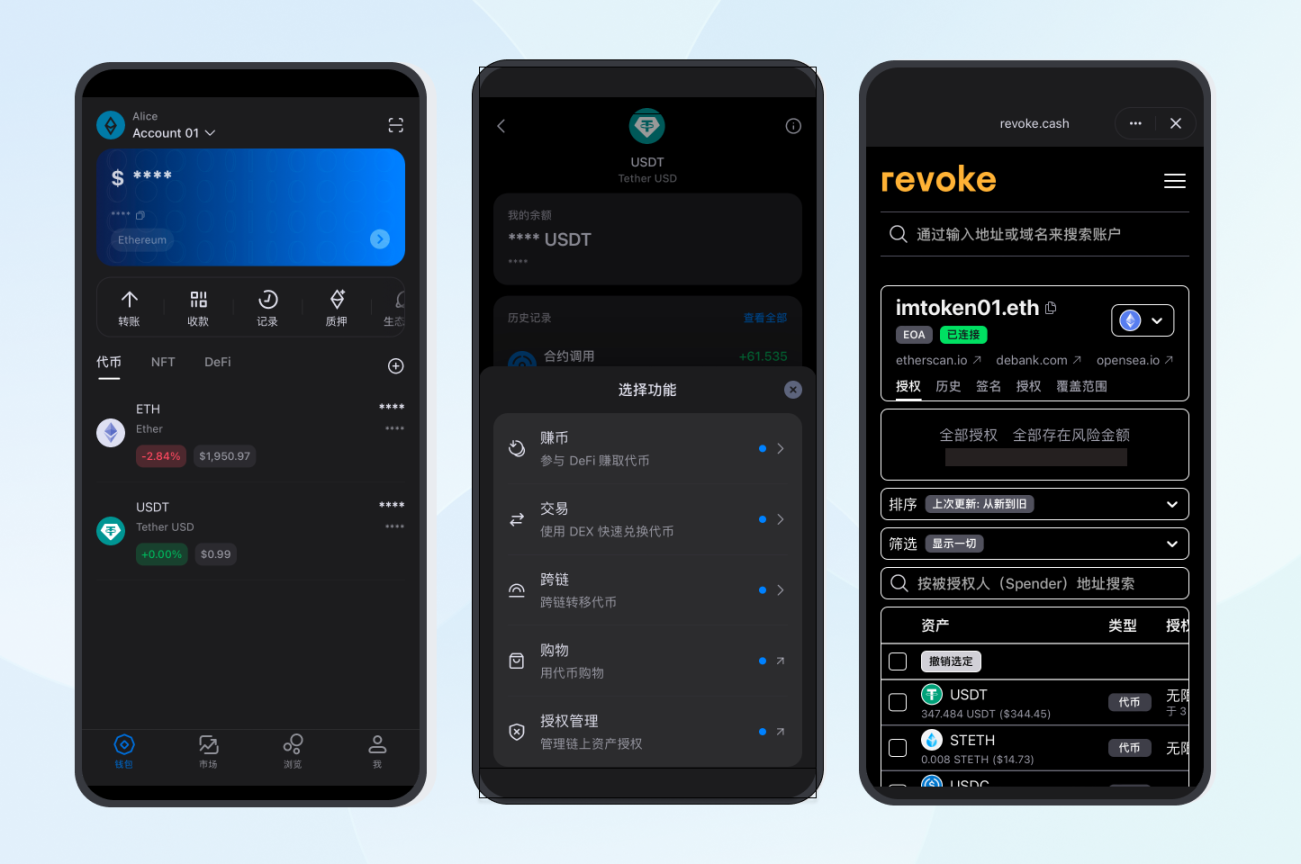
Ultimately, wallet security isn't about never granting approvals; it's about the principle of least privilege—granting only the permissions necessary for the current task and promptly revoking them when they are no longer needed.
3. Don't Let Your Guard Down During Travel, Socializing, and Daily Operations
If the first two types of risks stem from technological advancement and permission accumulation, respectively, the third type arises from environmental changes.
Travel during the Spring Festival (returning home, vacationing, visiting relatives) often involves frequent device switching, complex network environments, and dense social interactions. In such settings, the vulnerabilities of private key management and daily operations become significantly amplified.
Seed phrase management is the most typical example. Saving screenshots of seed phrases in your phone's photo album, cloud storage, or forwarding them to yourself via instant messaging tools is often done for convenience. However, in mobile scenarios, this convenience constitutes the greatest hidden danger.
Therefore, remember: Seed phrases must remain physically isolated, avoiding any form of internet-connected storage. The bottom line for private key security is being offline.
Social scenarios also require boundary awareness. Casually displaying pages with large asset balances or discussing specific portfolio sizes during holiday gatherings, though often unintentional, can lay the groundwork for future risks. Be even more vigilant against behaviors that, under the guise of "exchanging experiences" or "teaching guidance," lead to downloading disguised wallet applications or browser extensions.
All wallet downloads and updates should be completed through official channels, not via redirects from social chat windows.
Furthermore, always confirm three things before making a transfer: the network, the address, and the amount. After all, there have been numerous cases of whales suffering significant losses due to misoperations from similar first-and-last-character address attacks, and such phishing attacks have become industrialized over the past six months:
Hackers often generate a vast number of on-chain addresses with different first and last characters, creating a seed library. Once an address receives a transfer from the outside world, they immediately search the seed library for an address with matching first and last characters. They then initiate an associated transfer by calling a contract, casting a wide net and waiting for a catch.
Since some users sometimes copy the target address directly from transaction history and only check the first and last few characters, they fall victim. According to Cos, founder of SlowMist, regarding first-and-last-character phishing attacks, "Hackers are playing a game of casting a wide net, waiting for willing fish to bite—it's a probability game."
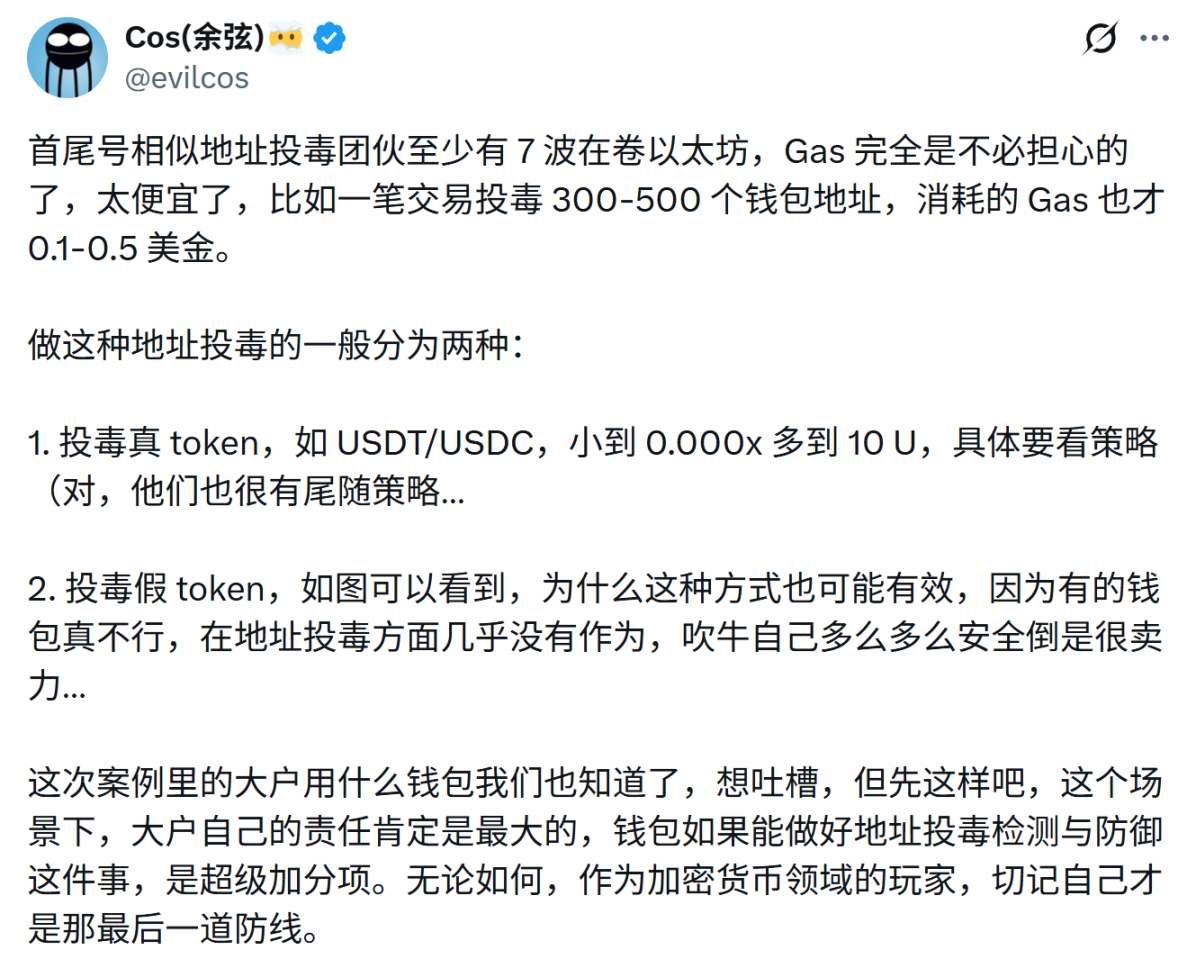
With extremely low Gas costs, attackers can poison hundreds or even thousands of addresses in batches, waiting for a minority of users to make mistakes during copy-paste actions. One successful hit yields returns far exceeding the cost.
These issues don't lie in technical complexity but in our daily operational habits:
- Verify the full address string, not just the first and last characters.
- Avoid copying transfer addresses directly from transaction history without checking.
- When transferring to a new address for the first time, conduct a small test transaction first.
- Prioritize using address whitelisting features to manage frequently used addresses.
In the current decentralized system dominated by EOA accounts, users themselves remain their own first responsible party and final line of defense (Further reading: The $3.35 Billion "Account Tax": When EOA Becomes a Systemic Cost, What Can AA Bring to Web3?).
In Conclusion
Many people often feel the on-chain world is too dangerous and not user-friendly for ordinary participants.
To be realistic, Web3 indeed struggles to offer a zero-risk world, but it can evolve into an environment where risks are manageable.
For instance, the Spring Festival is a time to slow down and is also the most suitable window of the year to organize your risk structure. Rather than rushing through operations during the holiday itself, it's better to complete security checks in advance. Instead of remedying issues after the fact, proactively optimize permissions and habits beforehand.
Wishing everyone a safe and smooth Spring Festival, and may all your on-chain assets remain stable and worry-free in the new year.



