Safeguarding in 2025: $500 Million and 70 Million Interceptions | OKX Yearbook
- 核心观点:2025年加密安全风险转向隐蔽的日常操作。
- 关键要素:
- 钓鱼与社会工程攻击占总损失70%以上。
- 加密平台类服务被盗金额已超21.7亿美元。
- OKX钱包通过事前拦截,一年挽回超5亿美元损失。
- 市场影响:推动行业安全防护向事前拦截和用户自助工具演进。
- 时效性标注:长期影响。
In the past, people were used to single-point collapses like "hackers breaching a large project and the news dominating headlines for days." But this year, risks are gradually permeating every seemingly ordinary on-chain operation: for example, the convenience brought by on-chain protocol upgrades has become a new phishing entry point; fake websites are disguised to the pixel level; malicious apps on mobile phones can quietly listen to the clipboard in the background; phishing links after social media is hijacked are more "official" than official ones; and those old contracts that were once authorized may be awakened by hackers one night.
A Chainalysis report indicates that by mid-2025, the amount stolen from crypto platform services, including exchanges, wallets, and custody services, had exceeded $2.17 billion, and this figure is likely to continue rising throughout the year if the disclosed trends hold. The core issue in 2025 will no longer be "whether there is risk," but rather, in a risky environment, how can an ordinary user obtain genuine security protection?
Increasing data and events have repeatedly proven that only by preventing risks before they occur, coupled with readily available and easy-to-use self-service tools (such as batch authorization revocation and device scanning), can personal losses be truly reduced, and users truly feel that "security is in their own hands." This is the moment OKX will bring users a sense of security in 2025. In the past year (January 2025 - November 2025), OKX Wallet helped users recover more than $500 million in losses, with an average response time of only 3 seconds for black address tracking, and has cumulatively marked and blocked more than 70 million pieces of various risk information.
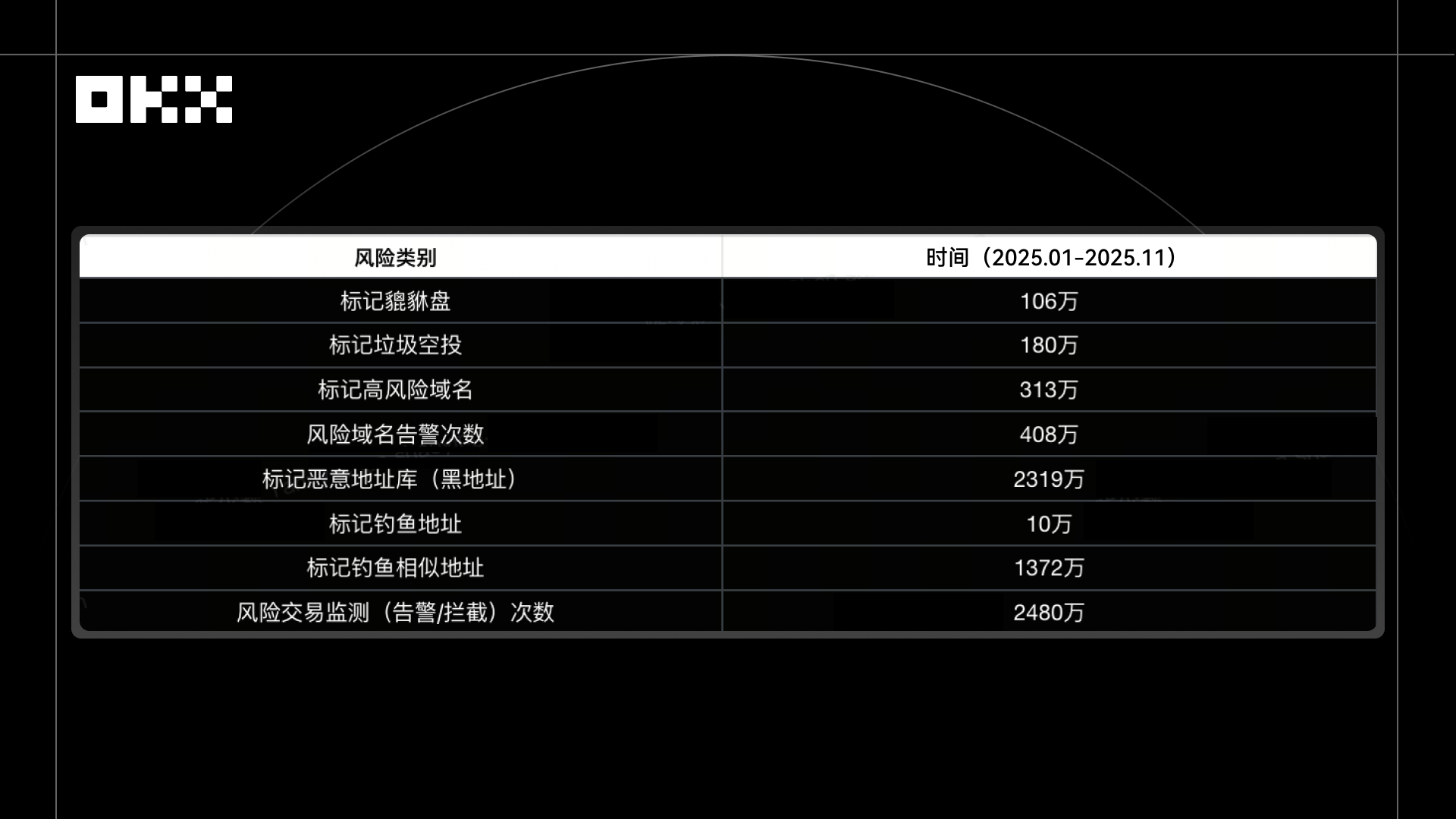
Image: OKX Wallet provides end-to-end security protection.
I. Safety Risks of "Transformation"
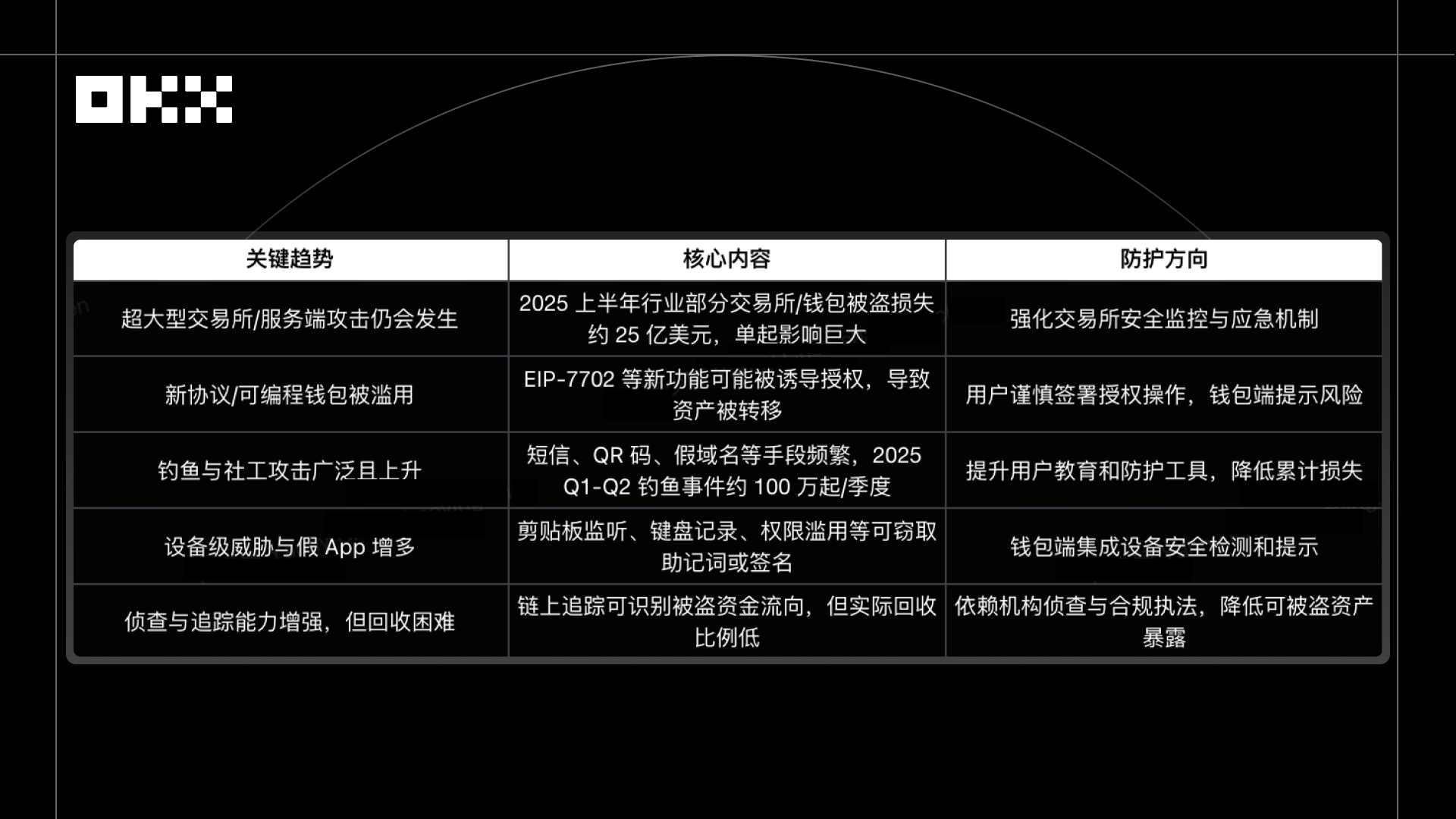
According to a report by CertiK, total losses of crypto assets in the first half of 2025, including wallet theft, phishing, fraud, and server attacks, amounted to approximately $2.47-2.5 billion.
From 2024 to 2025, the industry's security situation exhibited two parallel trends: a few large exchanges or servers were compromised, resulting in substantial losses; simultaneously, individuals also continuously encountered phishing, malware, and social engineering scams, leading to frequent small losses. The coexistence of high-volume, concentrated losses (platforms) and high-frequency, small-amount losses (users) placed the entire industry under double pressure on security.
Phishing and social engineering attacks remained prevalent in the first half of 2025. APWG data shows over 2.13 million attacks in Q1-Q2, a 13% increase from Q1. The widespread nature of these security incidents is not due to user incompetence, but rather because the risks have been distorted into forms difficult for ordinary people to discern.
- A seemingly normal address may be a highly similar fake address; copying it can lead to accidental transfer of funds.
- A familiar official website link may be a hijacked or disguised phishing mirror, making it difficult to distinguish.
- A seemingly secure on-chain operation may conceal a malicious upgrade request, induce multi-signature or authorization operations, and lead to the theft of funds.
- A seemingly harmless plugin may be recording mnemonic phrases or signature operations in the background.
- A commonly used wallet or contract can also be abused during authorization or upgrades, with hidden risks that allow users to lose assets without triggering the vulnerability.
Security incidents in 2025 revealed that hacker attacks have shifted from directly exploiting code vulnerabilities to exploiting user psychology and operational habits. Annual reports from multiple security organizations, including CertiK, Chainalysis, Ledger, and Kroll, show that such attacks account for over 70% of total losses. While individual losses may be small, they are almost impossible to prevent because users often "haven't done anything wrong" and are already victims. Unlike past large-scale project collapses that were readily apparent, these "modified" risks are insidious, widespread, and have low trigger conditions. They don't rely on vulnerabilities; a single authorization, signature, or click can cause losses. Even experienced users can fall victim. Therefore, relying solely on contract auditing or on-chain monitoring is insufficient; protection must combine local wallet security, contract whitelisting, reputation systems, and visual anti-phishing mechanisms.
II. Moments of "Safety" Brought by OKX
Moment 01: The "mole" in the phone was caught.
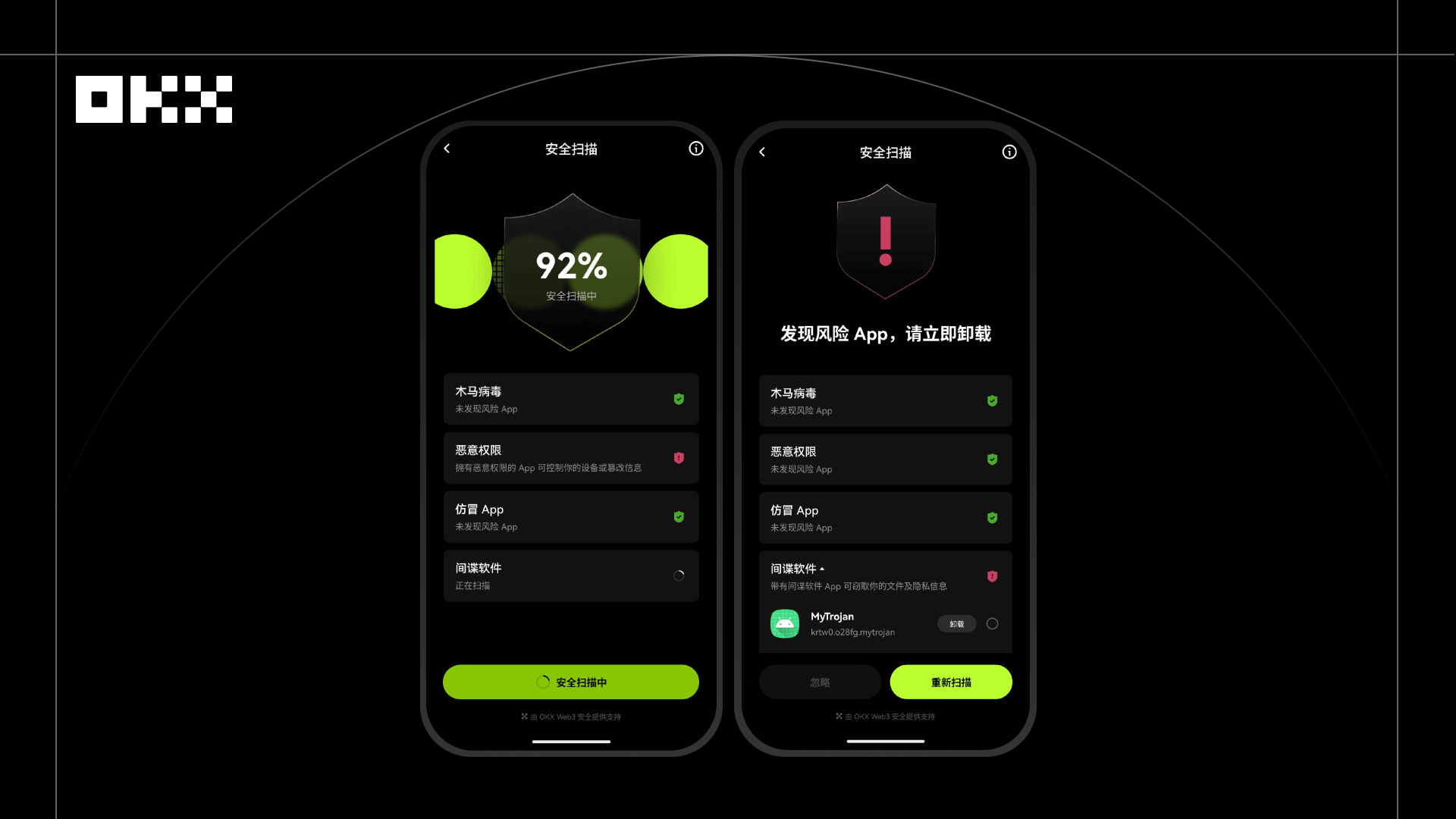
In 2025, an NFT collector downloaded a "Snatch-Up Assistant" app on his Android phone to participate in the snatching of popular NFT items. After downloading, he noticed abnormalities in his wallet's operations, but an initial check revealed no unauthorized transactions. On the surface, this app appeared to be an ordinary auxiliary tool, but in reality, it possessed high-risk behaviors such as stealing clipboard content, monitoring keyboard input, and abusing accessibility permissions. Once activated, it could potentially lead to the theft of mnemonic phrases and private keys, thereby endangering the user's asset security.
After the user enabled OKX Wallet's "Device Security Scan" function, the system performed a real-time proactive scan of the Android device, accurately identifying the plugin's attempt to monitor the clipboard and keyboard input. OKX's device-level protection covers Windows systems, browser plugins, and mobile devices, detecting potential local malware and assessing its threat level to mnemonic phrases, private keys, and transaction security. The scan report showed that the plugin exhibited high-risk behavior, and the system clearly alerted the user to the risk. The user immediately uninstalled the plugin upon receiving the alert, eliminating the potential threat.
Moment 02: Clicking on a fake website? Already blocked.
In 2025, a user preparing to participate in an initial public offering (IPO) of a project accessed the project's page through a social media platform. Unbeknownst to the user, the project's official account had been hijacked and was posting a phishing link to a fake staking platform. Upon clicking the link, before the page had fully loaded, OKX Wallet proactively displayed a red warning box, indicating that the URL had been marked as a high-risk phishing site and advising the user not to connect their wallet or perform any signing operations.
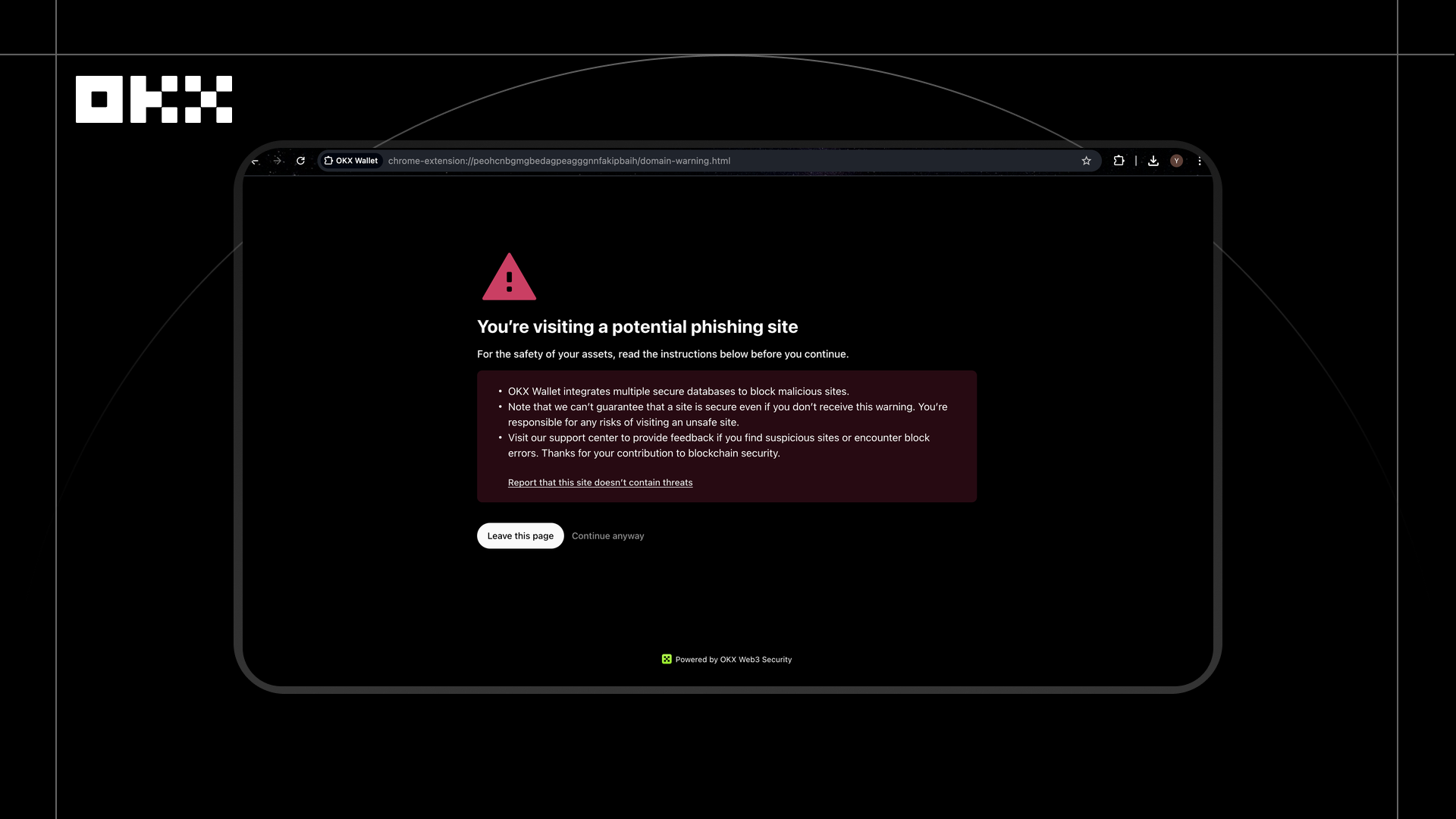
This interception is based on OKX's malicious DApp and URL detection system. Before a user accesses the site, the system performs static and dynamic security scans on links and DApp pages, identifying page spoofing features, malicious redirects, high-risk contract calls, and abnormal script activity. It also uses a real-time updated URL risk database for tiered assessment. When phishing websites or fraudulent content are detected, the system immediately blocks access before the user interacts with the page, preventing asset theft due to incorrect authorization.
Moment 03: One-click revocation of risk authorization
In 2025, a user who had long participated in various on-chain projects discovered while reviewing historical records that a contract from an early project they had used was at risk of having its authorization stolen. Due to years of frequent participation in airdrops, DeFi, and NFT projects, this user had accumulated a large number of idle authorizations, which needed to be cleared as soon as possible to prevent potential asset misuse. For example, a protocol you've authorized might cease operation at any time, absconding with your authorized funds, or be hacked, resulting in the transfer of your funds. Therefore, canceling idle authorizations is essential. However, canceling each authorization individually is not only time-consuming but also incurs high gas costs, making the process extremely inefficient.
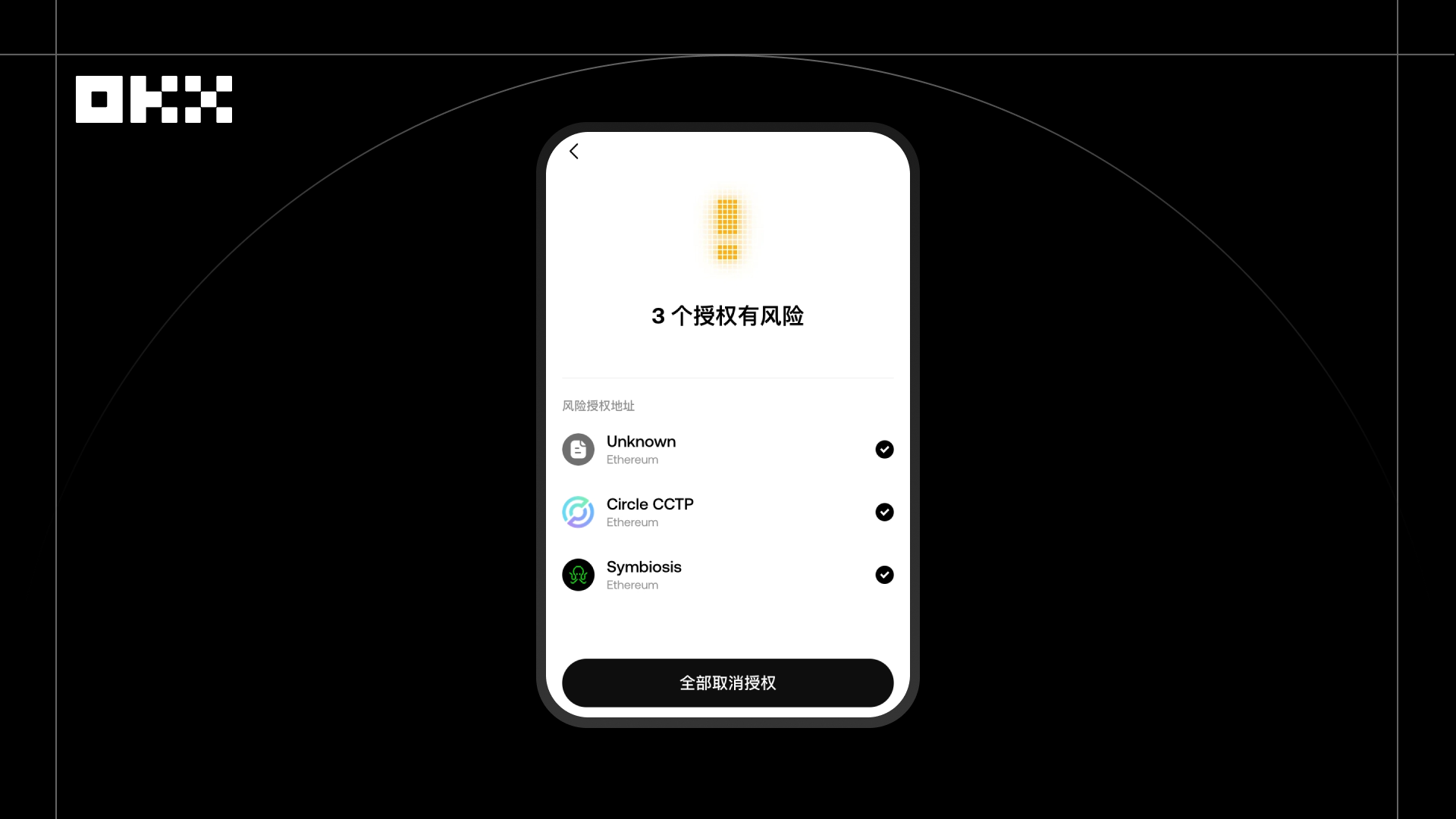
After using OKX Wallet's authorization management tool, the system automatically scans the user's historical authorization list and provides batch revocation capabilities. Users can select multiple risky authorizations and complete all revoks with a single on-chain operation. For users who have upgraded to support EIP-7702 delegation contracts, this feature allows for free cancellation of all authorizations without the need for individual processing. Compared to traditional single-revocation methods, batch revoking not only significantly improves processing efficiency but also reduces gas costs by an average of over 30%.
Moment 04: Before paying the gas fee, your wallet says "stop".
EIP-7702 Phishing Attack Interception Incident. In 2025, during the launch of EIP-7702, a user saw someone "generously" share a mnemonic phrase on a social media platform. Out of curiosity, the user imported it into their EVM wallet and attempted to transfer a small amount of gas fees to withdraw USDT assets. On the surface, the address appeared to be a normal EVM wallet, and the user believed it was safe. However, in reality, the address used the EIP-7702 standard to disguise itself as a normal receiving address. The deployer of the delegated contract possessed advanced privileges, and once the user transferred the gas fees, the funds could be immediately transferred away.
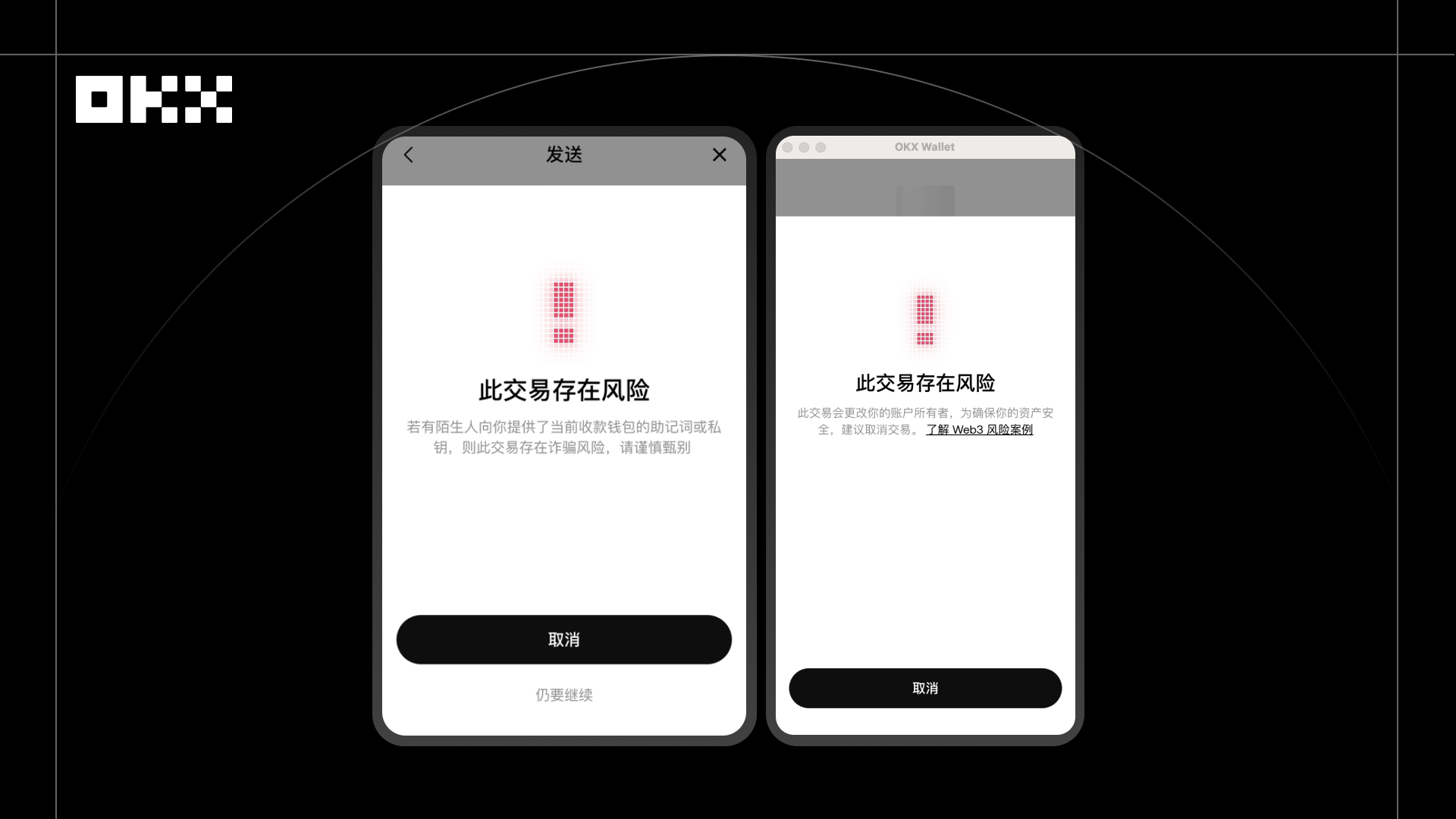
When a user attempted to transfer funds, OKX Wallet's real-time risk control system immediately identified the transaction as high-risk and triggered an interception. Through on-chain behavior analysis, transaction history, and smart contract logic detection, the system accurately identified potential risks, including EIP-7702 phishing attacks that use contracts to impersonate ordinary addresses and induce users to authorize or pay gas fees, as well as abnormal contract interaction behavior inconsistent with user operating habits. Simultaneously, with the rise of Move-related public chains such as Aptos, OKX Wallet can analyze MoveVM interaction behavior in real time to proactively interrupt transactions when it detects key tampering risks, preventing asset theft. The transaction was blocked during the confirmation phase, and the interface clearly prompted the user that "this receiving address is a high-risk address, your transferred funds may be transferred away," effectively preventing financial loss. After the incident, the user not only avoided financial loss but also learned about attack principles and risk patterns through the prompts, enhancing their awareness of cutting-edge on-chain threats.
Time 05: Address tampered with, withdrawals abruptly halted!
In addition to the OKX wallet, this sense of "security" is also reflected in the OKX exchange.
In 2025, a user received an on-chain payment address from a friend on a social media app, unaware that malicious software lurking on their phone had subtly altered the message content. The address the friend should have sent was ABC123**456DEF , but the user saw it as ABC234**567DEF . When the user attempted to transfer funds to this incorrect address, the OKX system promptly detected the anomaly. With OKX's persistent reminders, the user was guided to discover the address error, thus preventing a loss and raising awareness of on-chain scams.
To combat this highly sophisticated tampering attack, the OKX platform has implemented a dedicated address tampering protection strategy. Before a user initiates a withdrawal, the system uses on-chain behavior analysis and risk models to monitor the receiving address in real time, accurately identifying the risk of address tampering. Once an anomaly is detected, the platform will temporarily restrict the withdrawal and provide a risk guidance process to inform the user of the source of the risk and how to investigate, assisting the user in verifying and correcting the address to prevent assets from accidentally ending up in a hacker's account.
Time 06: Account under receivership? Restrict transfers and conduct security checks.
In 2025, a user's account was identified by the system as "suspected of being involved in a fraud scheme" before any abnormal transactions occurred. The account's fund flows, behavioral characteristics, and device connections exhibited typical patterns of a victim of a cross-border e-commerce scam. OKX immediately implemented a protective freeze, and customer service proactively contacted the user to verify the risk.
These types of scams have become increasingly common in recent years. Scammers lure users with the promise of "cross-border e-commerce entrepreneurship," attracting them through advertising and then guiding them to register on OKX. They claim that "operating a store requires an overseas wallet," and then, under the guise of managed account management, request verification codes and other critical security information. Once the user completes their deposit, the scammers immediately take over the account and transfer all funds. In response to these scams, OKX has established a risk identification model and deployed automated handling strategies. When it detects that a user may be being manipulated externally, it immediately restricts key account functions, blocks potential transfers, and simultaneously notifies the user to complete risk confirmation and security checks. In this case, the user was included in the protection process on the day of identification. Customer service confirmed that the user was being induced to entrust their account to the scammers, and the system's interception helped prevent losses before funds were transferred.
III. Security services are evolving from "post-incident remediation" to "pre-incident prevention".
The blockchain world is like a fast-paced city, where assets, permissions, contracts, DApps, and addresses are constantly flowing. Risks, in turn, become smarter and more insidious, lurking in every click, every confirmation, and every moment of hesitation. Security doesn't lie in the aura of technology or features, but in those moments tangible at your fingertips—the certainty when no mistakes are made, the peace of mind when potential threats are quietly averted, and the tranquility of being silently protected by a complex system.
Over the past year, OKX Wallet has continuously strengthened its security protection and proactive defense, covering the entire chain of monitoring from high-risk domains and spam airdrops to phishing addresses and blacklisted addresses. It has not only developed a large-scale capability for real-time risk monitoring and identification, but also, through multi-dimensional and multi-strategy protection mechanisms, has proactively intercepted potential losses and fraud risks before they affect user assets, realizing the security concept of "protection before anomalies occur."
Recently, OKX Wallet has also launched a new security landing page audit report and made its security protection system public: https://web3.okx.com/zh-hans/security ; users can view it anytime, anywhere.
In this world, protection is no longer an occasional reminder, but a normalized capability: real-time risk identification, layer-by-layer threat blocking, and early interception of potential losses, making security a perceptible and reliable presence. In 2026, perhaps more users will pause in this fascinating yet complex city, not out of fear, but because of visible protection, to explore the infinite possibilities of the blockchain world.