OKX Web3 Security Team: Protect your private keys like you would your eyes.
- 核心观点:私钥安全是数字资产自主保管的核心风险。
- 关键要素:
- 17%-23%比特币因私钥丢失永久沉睡。
- 私钥泄露主因:他人代创建、保存不当、钓鱼攻击。
- 私钥一旦泄露,资产转移仅需数秒且不可逆。
- 市场影响:推动行业加强安全教育和工具防护。
- 时效性标注:长期影响
Not Your Keys, Not Your Coins—Decentralized freedom comes at the cost of absolute "private key security."
A Chainalysis report in July 2025 revealed that 17%-23% of Bitcoin is permanently dormant due to forgotten private keys or damaged devices. Since private keys represent asset ownership, once lost, they cannot be reset, and there is no customer service to help recover them. Once known to others, stolen funds are almost impossible to recover. The on-chain world gives us freedom, but it also places complete responsibility in our hands. As the on-chain ecosystem flourishes, various asset theft incidents occur frequently, but people often only realize it after the fact, and it's difficult to pinpoint where the problem occurred—was the private key leaked? A phishing link clicked? A Trojan program downloaded? Or some other operational error?
The OKX Web3 security team hopes to raise awareness of private key security through this educational campaign, while also reviewing the most easily overlooked security blind spots.
1. Why are private keys or mnemonic phrases leaked?
First, let's correct a common misconception: many users believe that private key or mnemonic phrase leaks (hereinafter referred to as "private key leaks") usually occur during wallet usage. In fact, if you download and use an official version of a wallet from a reputable brand through legitimate channels, your private key generally won't be leaked during normal use. Private key leaks mostly occur due to improper storage, allowing others to obtain them. Once someone has your private key, they can import and control the assets of that account in any wallet.
In reality, there are many reasons for private key leaks, and the specific source is often difficult to trace completely. However, through the analysis of numerous industry cases and assistance in investigations, we have summarized some typical scenarios and clues. (See below)
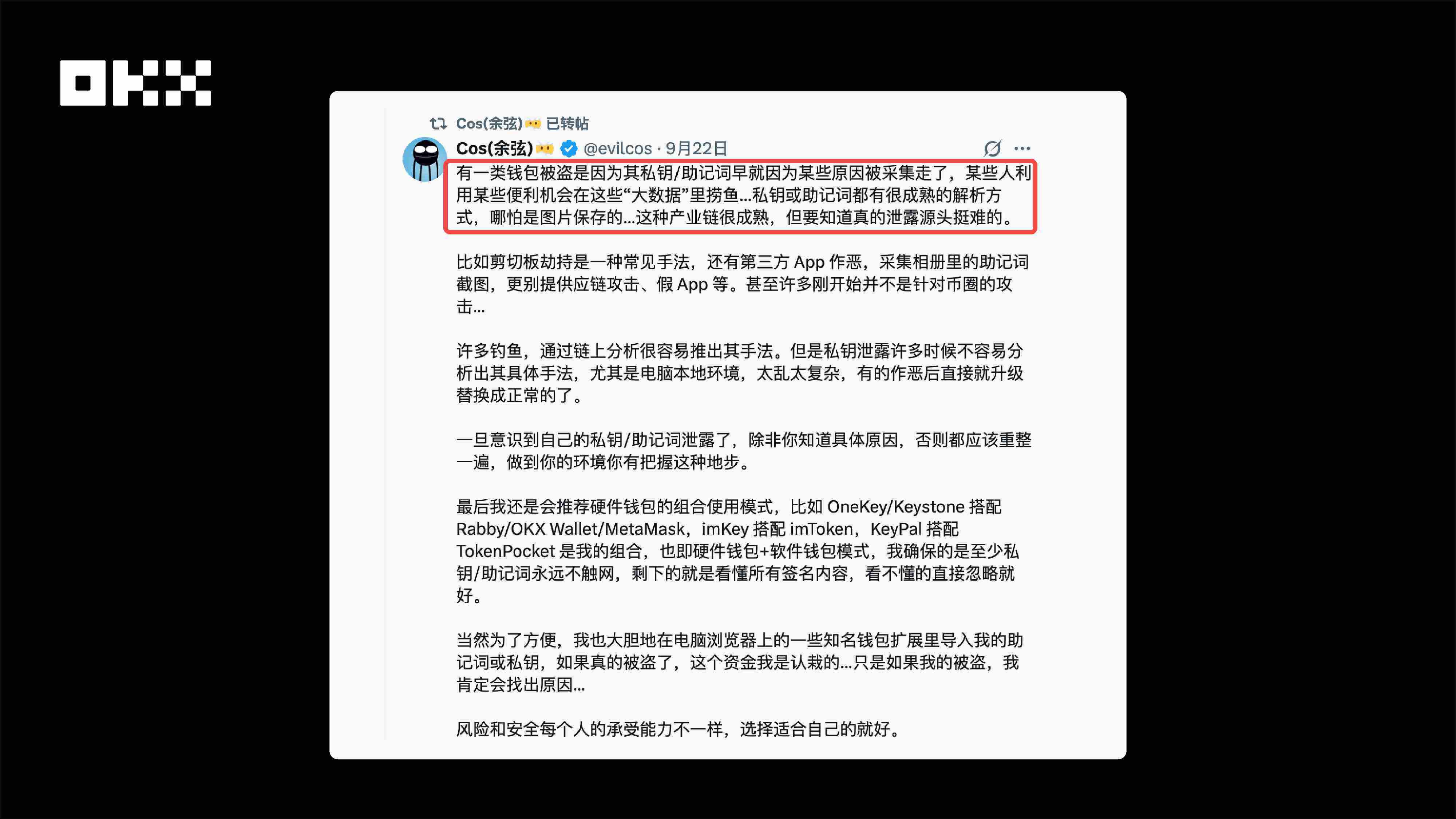
Image: The difficulties in analyzing the reasons for private key theft shared by teacher Yu Xian of SlowMist.
II. Common Private Key Leakage Scenarios and Mitigation Methods
(a) The most easily overlooked scenario: the wallet was already leaked when it was created.
Case 1: Wallet Created by Another Person. Mr. Li, new to Web3, created a wallet with the help of a "helpful mentor." The mentor helped him create the wallet, set a transaction password, and guided him through depositing and trading. Although a transaction password was set, the mentor had already obtained Mr. Li's private key during the creation process. A few days later, the 5 ETH Mr. Li deposited was transferred away within a short period. He then realized that the transaction password was only for local verification, and anyone with the private key could import and directly transfer his assets from any wallet.
Security advice : Create your own wallet independently; do not let anyone "help" or "do it for you." If you suspect your private key may have been compromised, transfer your assets to a new wallet as soon as possible.
Case 2: Wallet Creation via Video Conferencing. Ms. Zhang created a wallet via video conferencing under the guidance of a remote "teacher." The teacher demonstrated step-by-step: downloading the wallet, generating a mnemonic phrase, depositing gas, and purchasing tokens. The whole process seemed very "thoughtful," and the teacher even reminded her at the end, "Never reveal your private key to anyone." However, she was unaware that her mnemonic phrase might have been recorded at the moment of the video conferencing. Two weeks later, approximately $12,000 worth of USDT was transferred from her account.
Security Recommendations : When creating a wallet, disable screen sharing, screen recording, or screen mirroring. If you suspect your private key may have been compromised, transfer your assets to a new wallet as soon as possible. Furthermore, OKX Wallet does not allow screenshots, screen recording, or screen mirroring on the page displaying your private key and mnemonic phrase, effectively enhancing security.
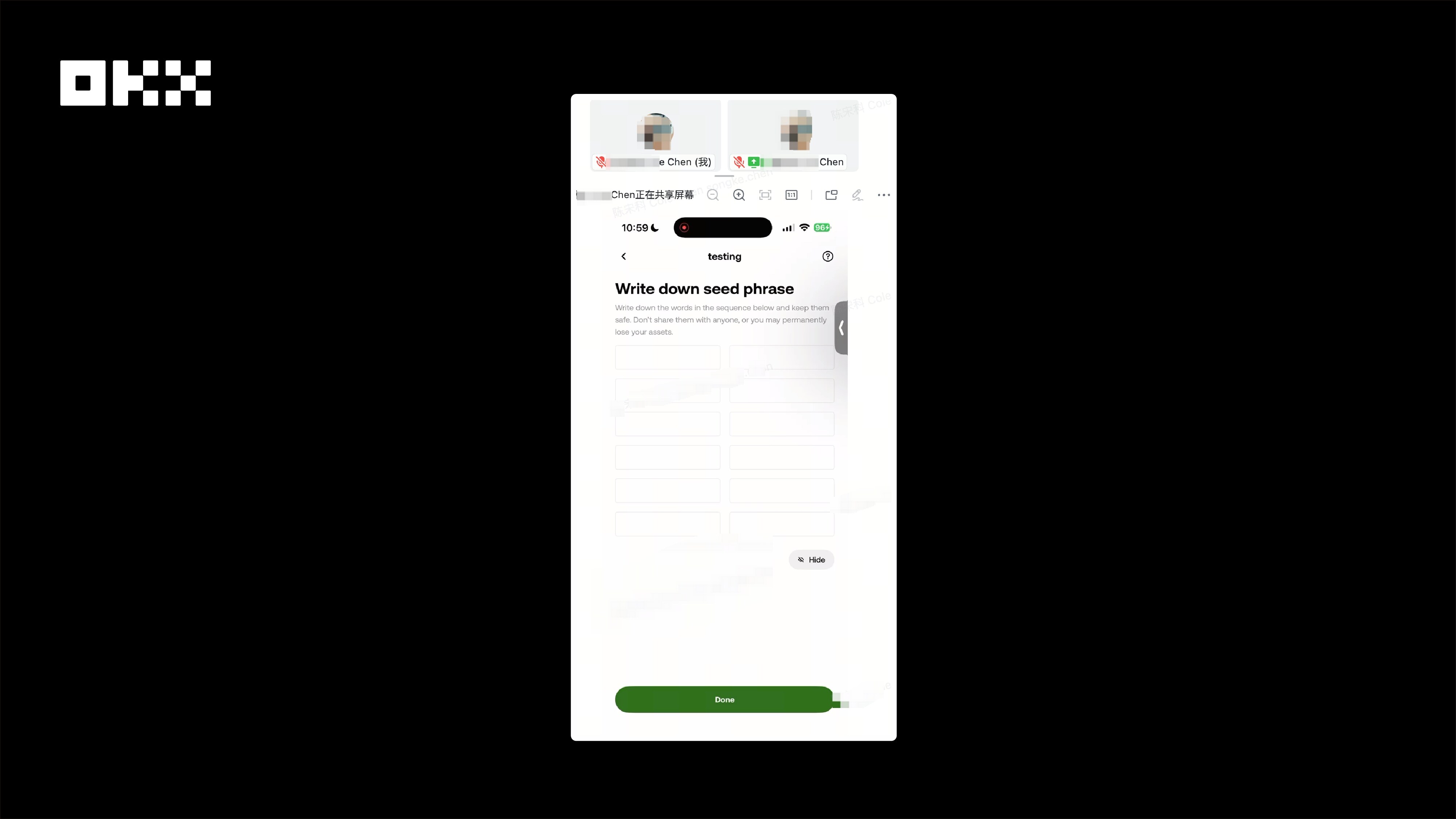
Image: When screen mirroring is detected, OKX Wallet will automatically hide the mnemonic phrase and private key, making the text invisible to others.
(ii) The most common scenario: improper storage of private keys leading to leakage.
Case 3: Fake Apps, a Nightmare for Android Users. Mr. Wang, a cautious user, saved a screenshot of his mnemonic phrase to his local photo album after creating his wallet, never uploading it to the cloud, believing this to be safer. However, he downloaded a so-called "enhanced Telegram" from a forum. This app's icon and interface were almost identical to the official version. In reality, it continuously scanned his phone's photo album in the background, recognizing his mnemonic phrase using OCR (Optical Character Recognition) technology and automatically uploading it to a hacker's server. Three months later, Mr. Wang's account was emptied, resulting in a loss of over $50,000. Technical analysis revealed that his phone also contained several other malicious apps, including fake imToken, MetaMask, and Google Authenticator.

Case 4: BOM Malicious Application Leads to Mnemonic Phrase Leakage. On February 14, 2025, multiple users experienced wallet asset theft. On-chain data analysis revealed that these theft cases all exhibited typical characteristics of mnemonic phrase/private key leakage. Further follow-up with the affected users revealed that most of them had installed and used an application called BOM . In-depth investigation showed that this application was actually a carefully disguised scam. Criminals illegally obtained mnemonic phrase/private key access by inducing users to grant permissions, thereby conducting systematic asset transfers and attempting to conceal their activities.
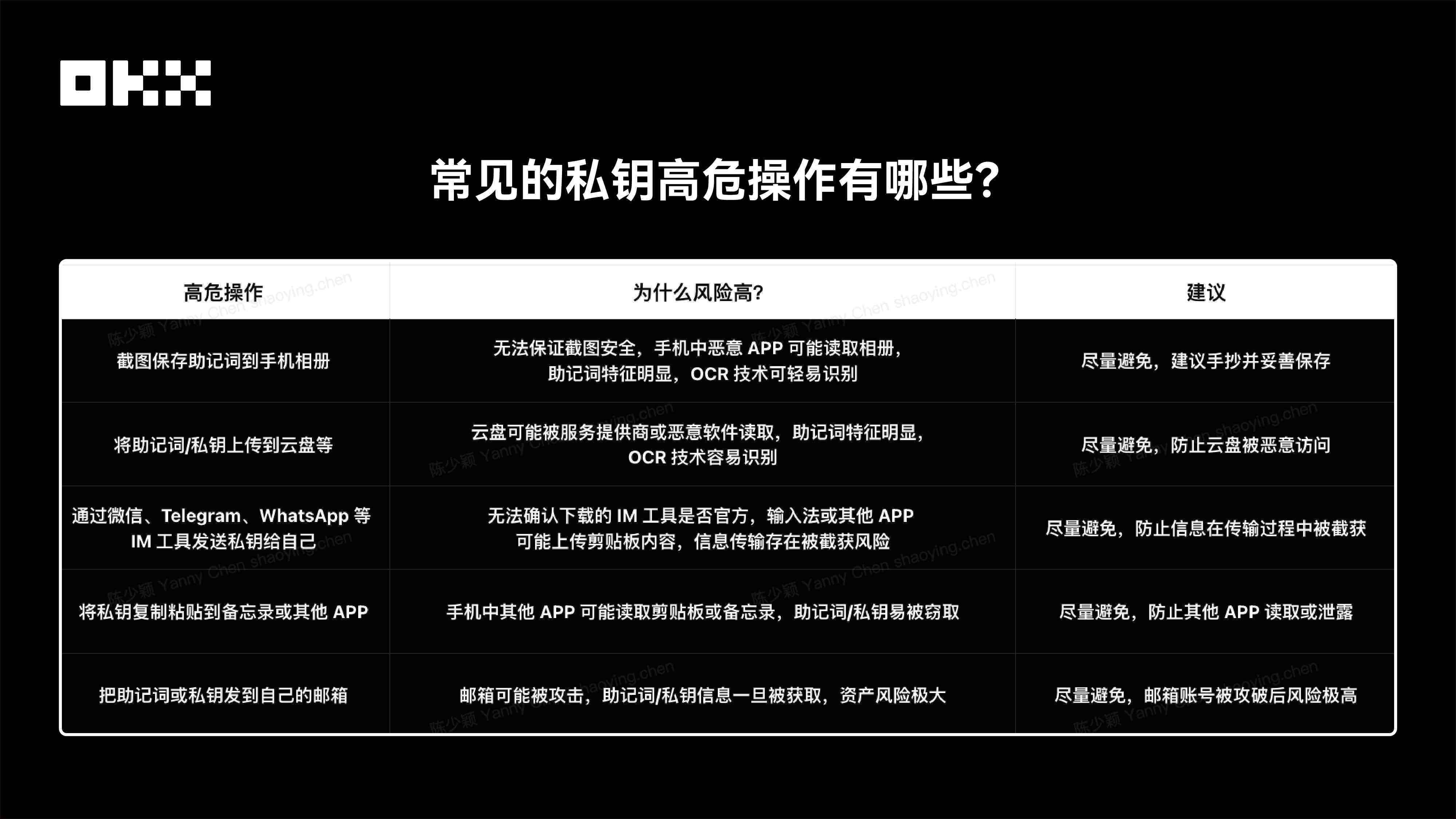
Security Recommendations : Many users develop habits out of convenience, but these are precisely the most dangerous. Therefore, we recommend: 1) Do not take screenshots of your mnemonic phrase! It is recommended to save it by hand on paper and store it in a safe place. 2) When downloading apps, always use official channels . Do not easily try "enhanced versions" or third-party modifications from unknown sources. 3) If you discover any device abnormalities or have previously taken screenshots of your private key , do not take chances; immediately transfer your assets to a new wallet. 4) What has OKX done? To prevent users from taking screenshots on the private key and mnemonic phrase backup pages, we have disabled the screenshot function on these sensitive pages.
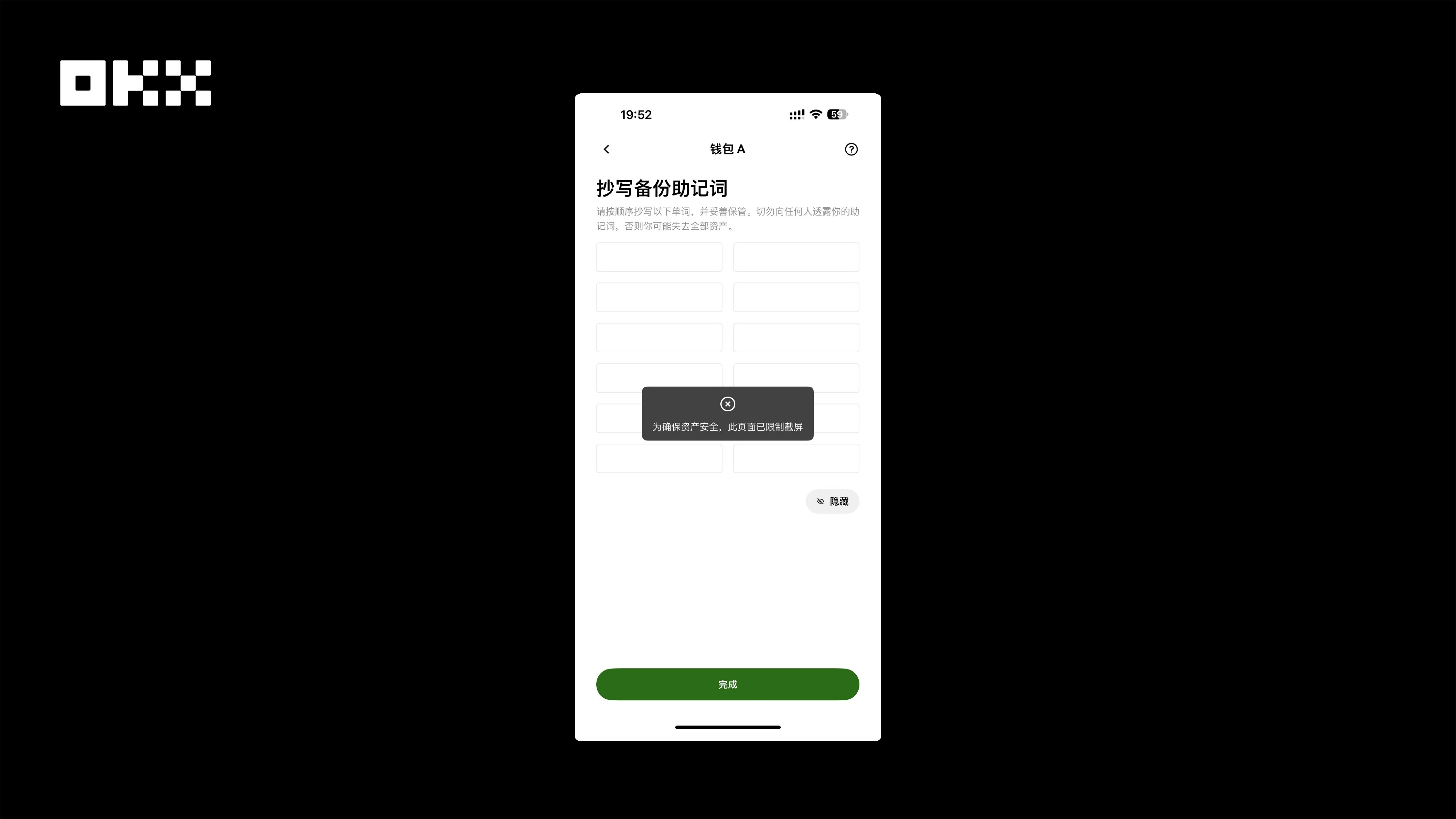
Image: OKX Wallet prohibits screenshots on the private key and mnemonic phrase pages.
In addition, to reduce the risk of users installing fake apps, the Android version also provides a malicious app scanning function.
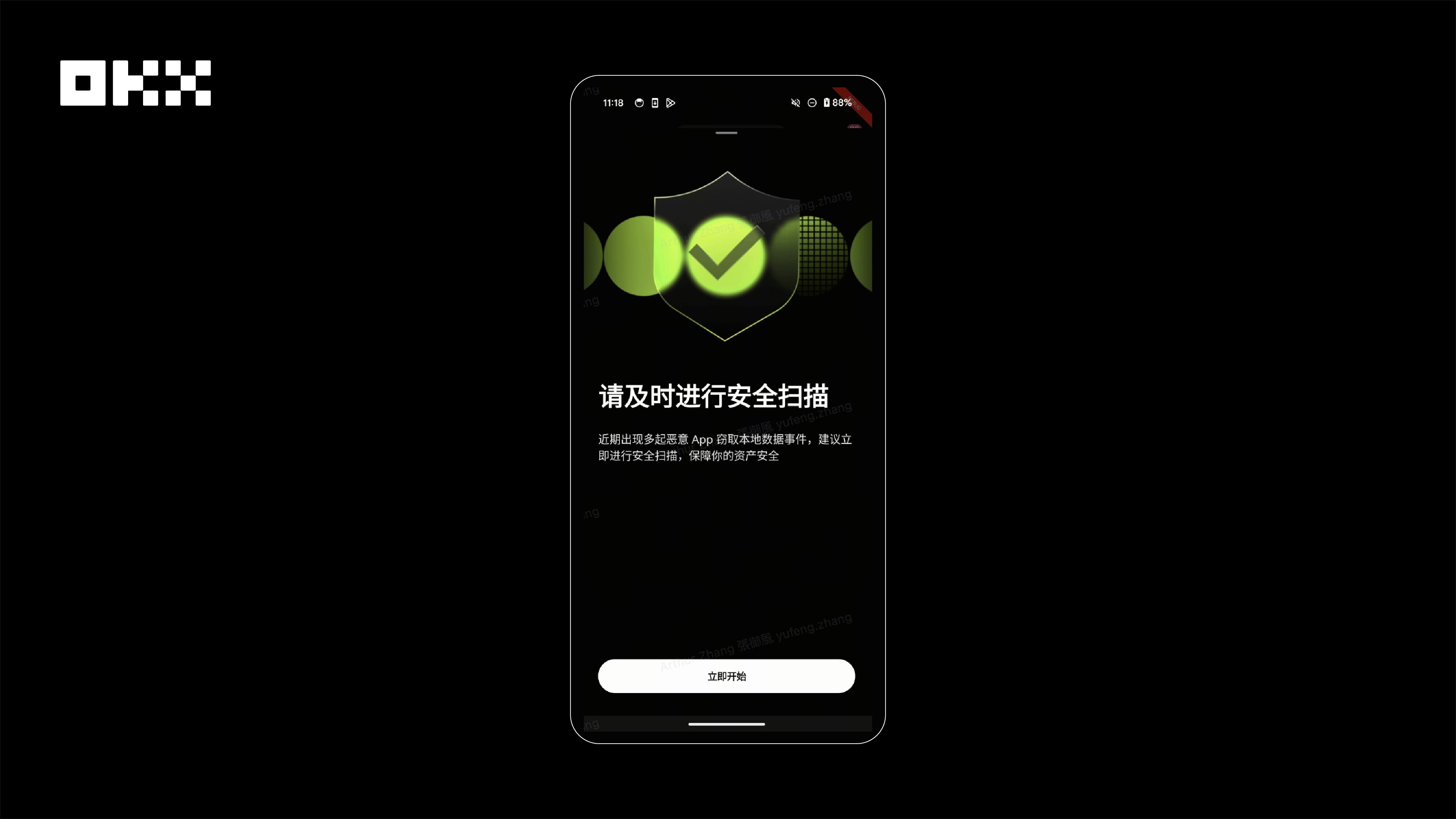
Image: OKX Wallet Android version provides a malicious application scanning function.
(iii) The most common and easiest scenario to fall for: phishing by others using the private key.
Case 5: Phishing via Fake Airdrop. A well-known NFT project announced on Twitter that it would airdrop new tokens to its holders. Just 10 minutes after the announcement, multiple phishing websites appeared at the top of Google search results (promoted through paid advertising). These phishing websites had domain names differing by only one letter (e.g., opensae.io instead of opensea.io), and their page designs were almost identical to the official website. When users connected their wallets, the page displayed a message: "Network congestion, connection failed, please manually enter your mnemonic phrase to claim the airdrop." More than 50 users fell for the scam that day, with total losses exceeding $200,000. The fastest victim's assets were transferred out in just 3.7 seconds after entering the mnemonic phrase.
Case Six: Social Engineering Attack. Ms. Zhao encountered an operational problem in a Discord group for a certain project. An administrator with a very "official" profile picture and nickname proactively messaged her privately, claiming to be customer service and offering to help her. The administrator sent her a link to a "verification page." Ms. Zhao believed it and clicked the link, entering her mnemonic phrase as prompted. The page looked exactly like the official website. A few minutes later, multiple transactions were suddenly and continuously transferred from her wallet. She then realized that the so-called administrator was actually a scammer, and any "customer service" that asks users to enter mnemonic phrases or private keys on a webpage is definitely a scam. It's worth noting that besides impersonating official administrators, scammers may also impersonate friends, project employees, or other trustworthy individuals.

Security advice : A legitimate DApp will never ask you for your private key, and a reliable person will never ask for it. Remember: your private key is the key to your assets; keep it safe and do not disclose it easily.
3. Why is there so little that wallet vendors can do once their private keys are leaked?
When users discover that their private keys have been leaked or their assets have been transferred, they immediately contact the wallet team, hoping we can provide more assistance. However, in reality, once the private keys have been exposed, the wallet vendors have very limited room for intervention.
Here's a brief overview of our basic handling process when we receive feedback about "stolen assets," and also an explanation of why we often cannot directly "recover" on-chain assets:
First, we will assist users in tracing the flow of funds and analyzing whether the on-chain funds may be related to known hacker groups or address clusters. Simultaneously, we will advise users to transfer any assets that have not yet been stolen as soon as possible to reduce the risk of further losses. For cases involving large sums of money stolen, we will advise users to contact their local police immediately and seek assistance through legal channels. Our internal team will also conduct an in-depth analysis of the incident, summarizing the hackers' modus operandi to provide a reference for future user protection.
As the tool provider, the wallet itself has neither the ability nor the authority to freeze or roll back on-chain assets. Once the private key is obtained by a hacker, they can typically use automated scripts to transfer funds within seconds—a process that is extremely fast and difficult to intervene in. Only when the stolen funds ultimately flow into a centralized exchange can a temporary freeze be requested through legal channels.
When the funding chain is linked to the hacker cluster we have already identified, we will start from their common modus operandi to help users recall whether they have recently performed any high-risk operations, and then determine at what stage their private key may have been exposed.
OKX has always prioritized user fund security, investing heavily in building a risk control system and designing multiple verification mechanisms over the years. While these processes may seem cumbersome, they are all designed to better protect user assets. It's fair to say we are one of the teams in the industry that invests the most heavily in security.
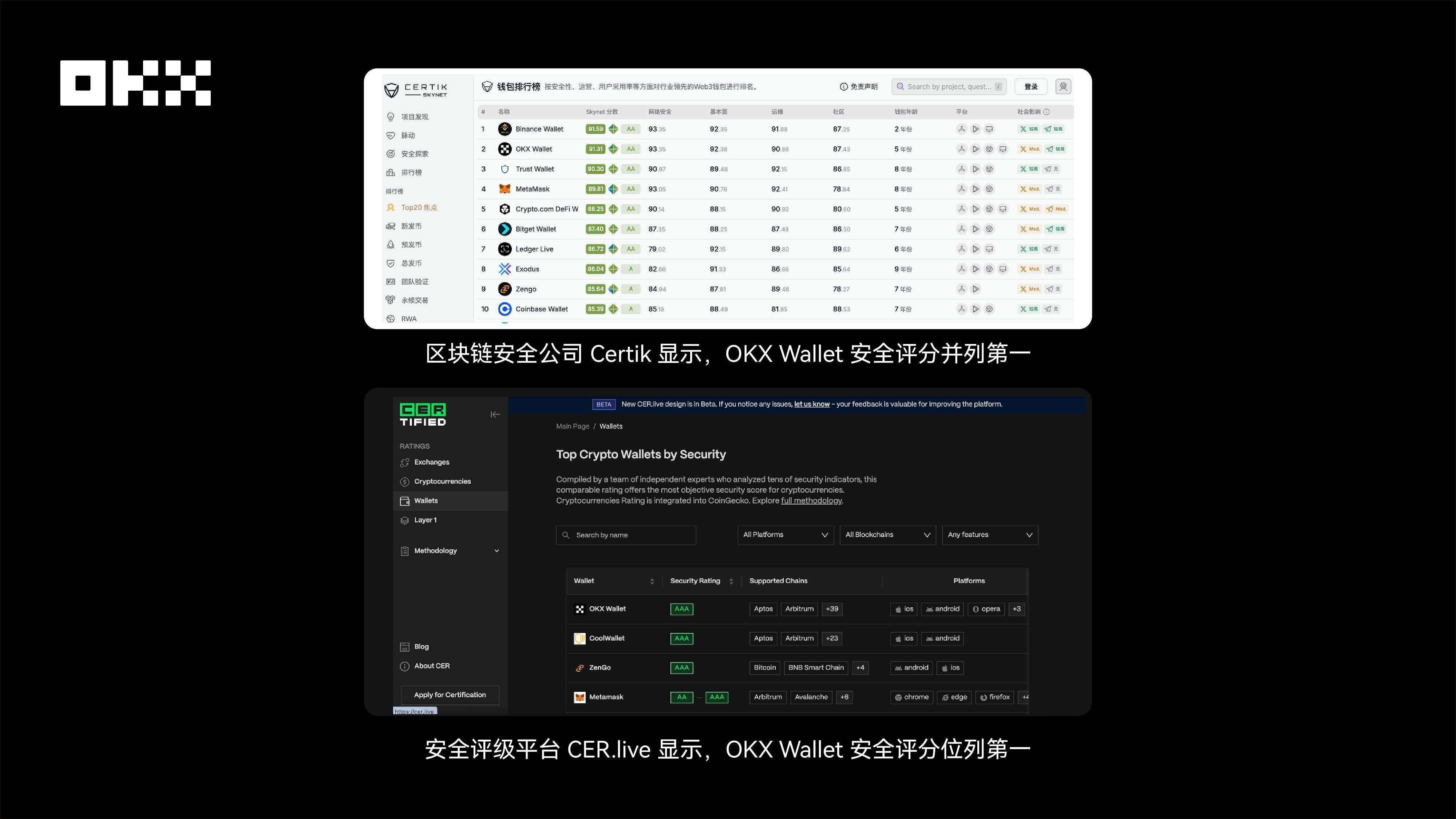
Image: OKX Wallet ranks first in security score
As mentioned earlier, if users lack security awareness or have improper usage habits, they may still suffer losses due to phishing, private key leaks, or other reasons, regardless of which wallet they use. Therefore, properly safeguarding private keys remains the most critical security foundation. In addition to continuously improving the security capabilities of our products, we also continuously strengthen case studies and share security tips to help users better identify potential risk scenarios.
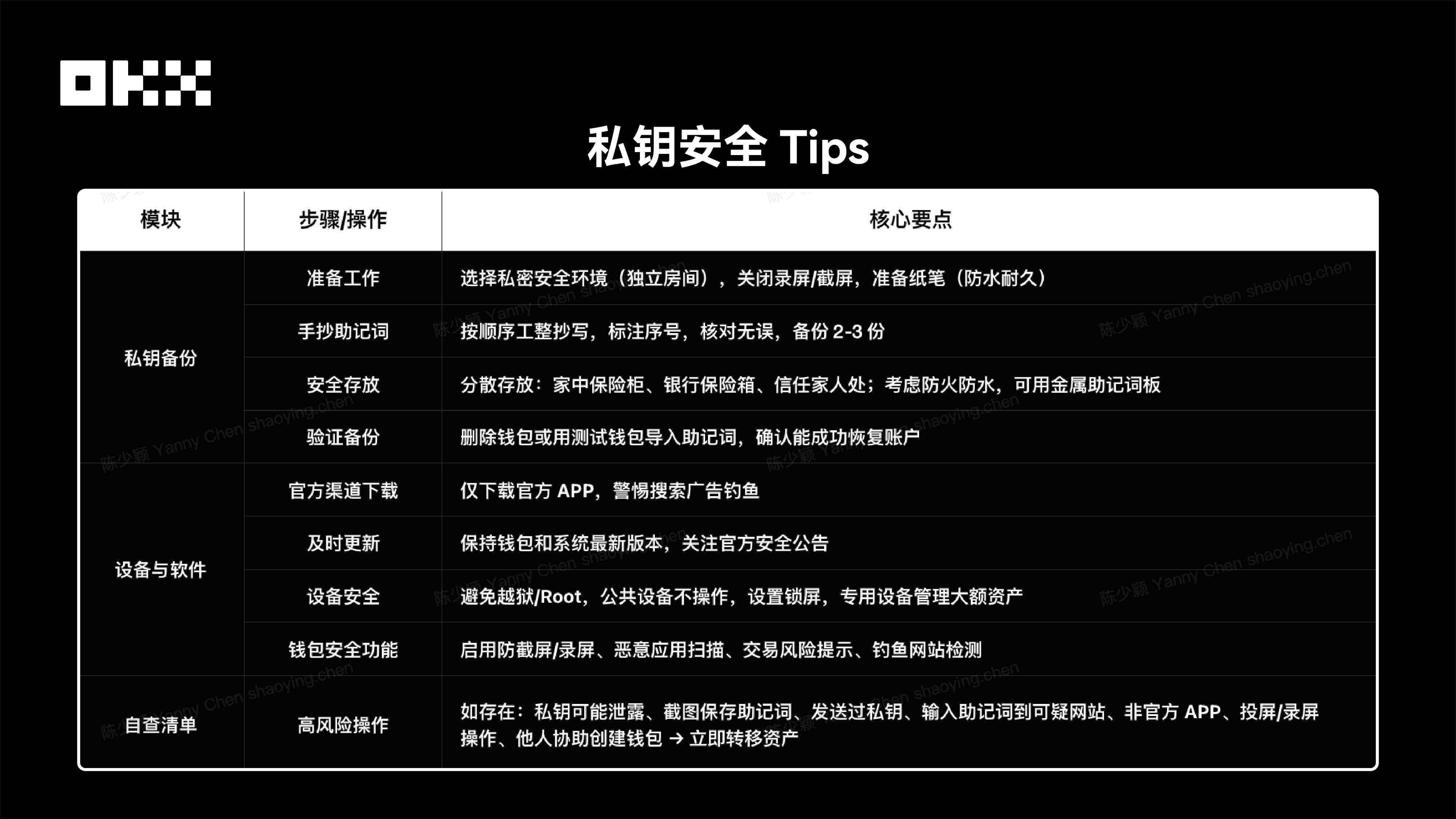
IV. In summary, here are some tips for private key security.
Disclaimer:
This article is for informational purposes only. It is not intended to provide (i) investment advice or recommendations, (ii) an offer, solicitation, or inducement to buy, sell, or hold digital assets, or (iii) financial, accounting, legal, or tax advice. Digital assets (including stablecoins and NFTs) are subject to market volatility, involve high risk, and may depreciate. For questions regarding whether trading or holding digital assets is suitable for you, please consult your legal/tax/investment professional. OKX Web3 Wallet is merely a self-custodied wallet software service that allows you to discover and interact with third-party platforms. OKX Web3 Wallet has no control over the services of such third-party platforms and assumes no responsibility for them. Not all products are available in all regions. You are responsible for understanding and complying with applicable local laws and regulations. OKX Web3 Wallet and its related services are not provided by the OKX Exchange and are subject to the OKX Web3 Ecosystem Terms of Service.