MetaTrust: Raft was attacked and lost 3.6 million, and almost all hacker operations were sent into the black hole
Summary
At 02:59:23 am on November 11, 2023, 8:00 UTC+, MetaScout detected that the stablecoin protocol Raft on Ethereum suffered a flash loan attack. The result was 6.7 million stablecoin $R being minted and the protocol losing $3.6 million. The root cause was a precision calculation issue that occurred when minting share tokens, which hackers exploited to obtain additional share tokens.
MetaTrust Labs conducted in-depth research and analysis of this attack, revealing how hackers exploited the vulnerability.
Stablecoin protocol Raft
Raftis a DeFi protocol that provides a capital-efficient way to lend and borrow by depositing Liquid Staking Tokens (LSDs) as collateral while retaining staking rewards.
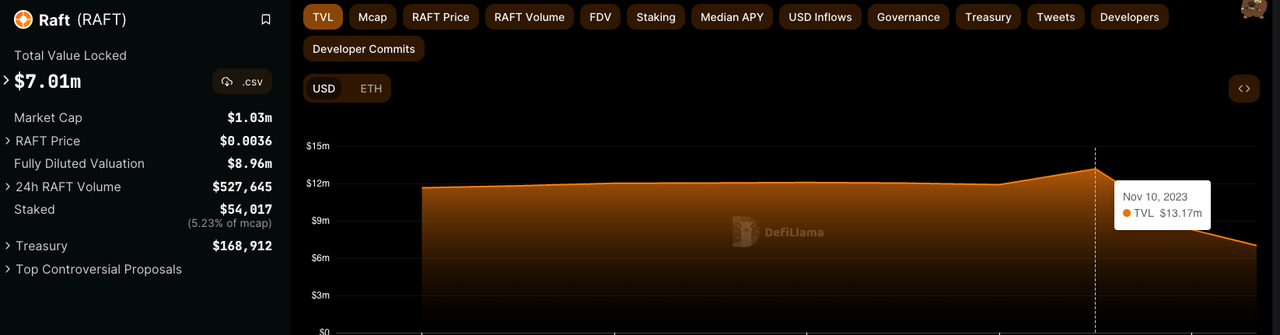
As of this writing, its total value locked (TVL) is down 46% to $7 million following today’s attack. The price of $R is down 99.6% to $0.0036.
trade
https://etherscan.io/tx/0xfeedbf51b4e2338e38171f6e19501327294ab1907ab44cfd2d7e7336c975ace7
attacker
0xc1f2b71a502b551a65eee9c96318afdd5fd439fa
Attack contract
0x0a3340129816a86b62b7eafd61427f743c315ef8
Attacked contract
InterestRatePositionManager: 0x9ab6b21cdf116f611110b048987e58894786c244
Attack steps
1. Borrow 6,000 $cbETH from AAVE through flash loan;
2. Transfer a total of 6001 $cbETH to the InterestRatePositionManager contract;
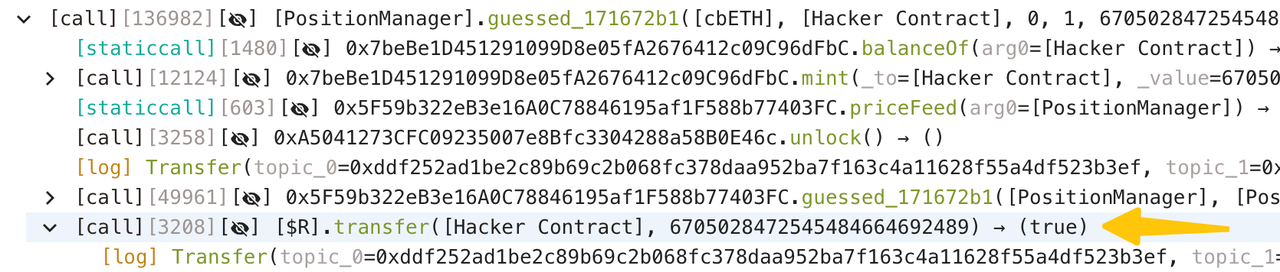
3. Liquidate the pre-created position 0x011992114806e2c3770df73fa0d19884215db85f on the InterestRatePositionManager contract;
4. Set the index of the raft mortgage token to 6, 003, 441, 032, 036, 096, 684, 181, which is the $cbETH balance of the InterestRatePositionManager contract, and amplified by 1000 times due to the donation in step 2;

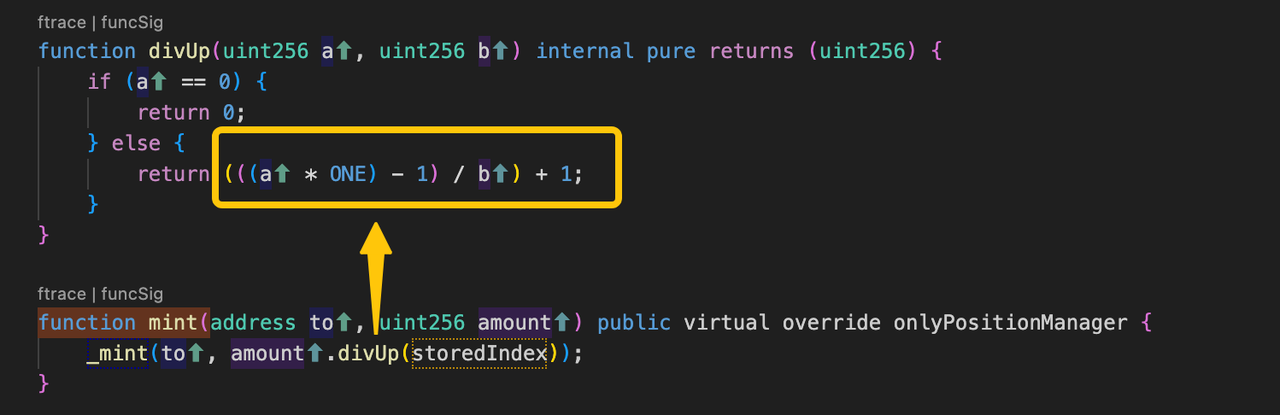
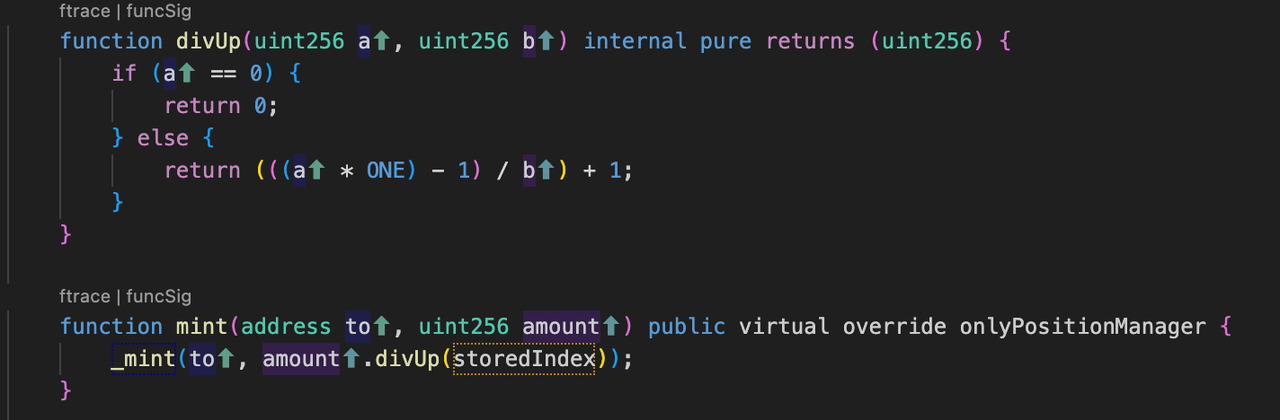
5. When calculating shares by using the divUp function, 1 wei share is minted by just 1 wei of $cbETH. Note that when the numerator is non-zero, the minimum return value of the divUp function is 1, no matter how big the denominator is:
6. Repeat step 5 60 times to obtain 60 wei shares, which is 10,050 $cbETH;
7. Exchange 6003 $cbETH with only 90 wei $rcbETH-c;
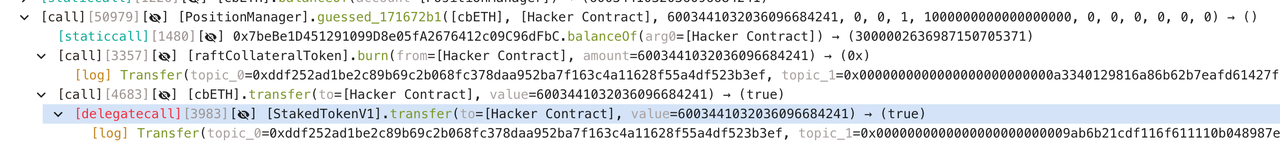
8. Borrow 6.7 million $R, the profit, and eventually exchange it for 1575 $ETH worth $3.6 million in different Dapps, including:
Convert 2.1 million $R to 2 million $sDAI on Balancer
Convert 1.2 million $R to 1.15 million $DAI on Balancer
Convert 200,000 $R to 86,000 $USDC on Uniswap
9. What is shocking is that the hacker burned 1570 $ETH to the black hole address, which means that the hacker did not get any profit.

root cause
The root cause was a precision calculation issue that occurred when minting share tokens, which hackers exploited to obtain additional share tokens. Since the donation of $cbETH enlarges the index, causing the hackers share to be worth more, the hacker only used a little $rcbETH-c to exchange 6003 $cbETH and borrow a large amount of $R.
key code
asset loss
$3.6 million.
Capital flows
1570 $ETH was burned due to hackers mistake.
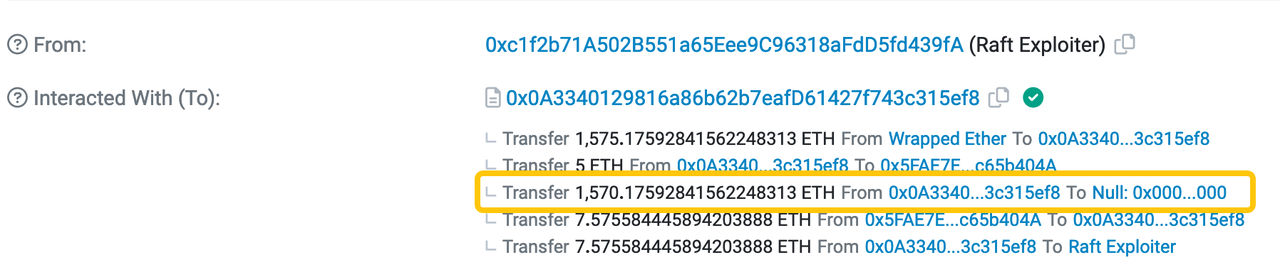
As of this writing, the attacker has 1.4 million $R tokens (worth $4.6k) in his wallet.
Security advice
Consider checking for potential rounding issues in the context of interest rate calculations, such as whether they can be manipulated by malicious users in edge cases, as in the Raft attack case scenario.
It is recommended that measures be taken to monitor the system and suspend protocols in the event of an emergency. Alternatively, it would be beneficial to incorporate a memory pool blocking system. This system can effectively detect attack transactions in the memory pool when an attacker performs an attack, so as to perform preventive blocking and avoid losses.
About MetaTrust Labs
MetaTrust Labs is a leading provider of Web3 artificial intelligence security tools and code audit services incubated by Nanyang Technological University in Singapore. We provide advanced AI solutions that empower developers and project stakeholders to secure Web3 applications and smart contracts. Our comprehensive services include AI security scanning, code auditing, smart contract monitoring and transaction monitoring. By integrating AI, we ensure a secure ecosystem and enhance trust between users and developers.
Website: https://metatrust.io/
Twitter: https://twitter.com/MetatrustLabs



