Crypto’s biggest use case: Building permissionless identities
Original author: KERMAN KOHLI
Original compilation: Deep Chao TechFlow
We are currently in the midst of a trough in the cryptocurrency market, having been hit hard by a bear market so to speak. Everyone is asking what the actual application scenarios and value of these technological products we are developing are. Many people made seemingly good points, but there was no clear reason why these products should be more advantageous than ordinary Web2 applications. I have been thinking about this issue for some time, and based on personal experience and judgment, I am cautiously optimistic about certain perspectives. This article is not about ideology, but about practical issues of technology and standards. Before we dive into that, let’s take a look at how the existing internet works.
Web2, data producers and authentication
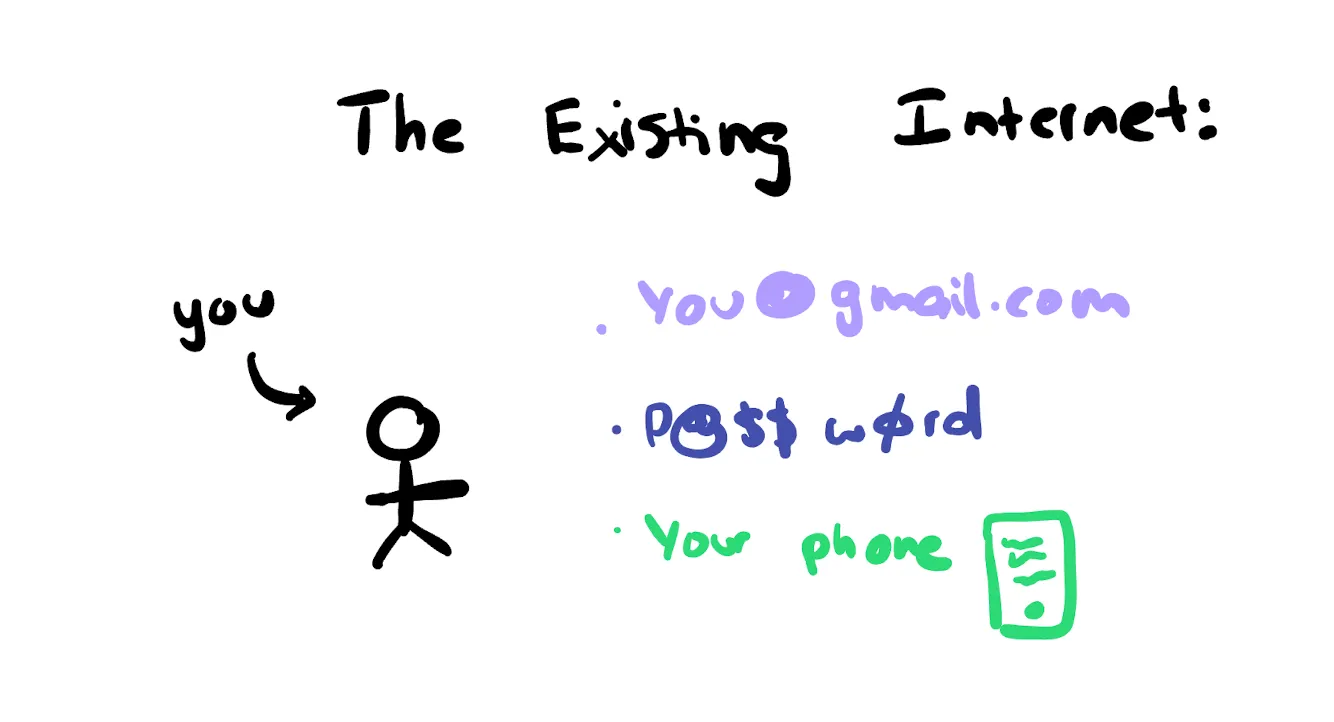
When you sign up for a service on the Internet, the service provider doesnt actually know your true identity because all of your information can be forged. Your IP address, browser cookies, device fingerprints, etc. are only approximate identifiers that can be forged. Everything can be faked.
This has led to the creation of authentication standards that rely primarily on:
email address;
password;
2 FA (two-factor authentication) scheme.
Whenever you use certain services on the Internet, the service provider requires a durable, secure identity to bind your data. Whats more important is to provide a way for you to verify yourself identity.
Each database creates a different identifier for you. Facebook, Twitter, Instagram create a unique identifier for you in their database.
When you use OAuth to log in to other services, they can reference that identifier, but they will still create a new row in their database to identify you. OAuth providers may share certain data points with external developers, but this is usually very limited. It is then up to the specific developer to bind any information generated in their application to the newly created user identifier in their database.
You may have noticed that in every service you use,"you"are repeated. This is not because there is anything malicious about Web2, but it is the only logical thing to do given the limitations of current hardware. However, as the decades passed on the Internet, this led to a bigger problem:
1. All your identity and reputation data are restricted to the specific ecosystem you signed up for. Your Twitter followers are still Twitter data and you cannot export them.
2. Any information created on the Internet is linked to an identity within the Service. Google Reviews only displays information that Google has about you.
3. Each new service you sign up for requires you to re-establish trust and credibility within that ecosystem, despite what you have done in the past.
This is our environment today:
Our personal data is what uniquely identifies us;
However, our information remains fragmented.
We are starting to see this becoming a bigger and bigger problem as the authenticity and trustworthiness of all information on the internet must be increasingly scrutinized. Whenever I read an article with a strong attitude, I usually:
Find out who the author is;
Follow their Twitter and any other sources I can find about them;
Find references to the article on other websites;
Make an overall judgment about the authors biases and opposing viewpoints.
However, I know I am more of a minority here. Most people will accept the information presented without question, without knowing the identity of the producer of that data (data here is defined as any information presented in the form of articles, tweets, videos, etc.).
The key problem we collectively have is that we have no clear way to deterministically identify who we are online. Every time you visit a website, receive a message from someone, or receive an email, theres a chance youre talking to the wrong person because we identify someone by their unique screen name. This has started to create major problems where we cant even identify ourselves in online communications.
I might be XXX.eth on the chain, XXX on Telegram, or xxx on another platform. However, if someone messages you as xxx on Telegram, you might think its me. Without public key authentication, trust on the Internet is a mess.
The lack of stronger, longer-lasting digital identities over time is a common problem faced by humanity.
Cryptozoology, Crypto timestamps
Part 1: Cryptozoology
This may sound strange, but hear me out. They are two different and similar-sounding concepts.
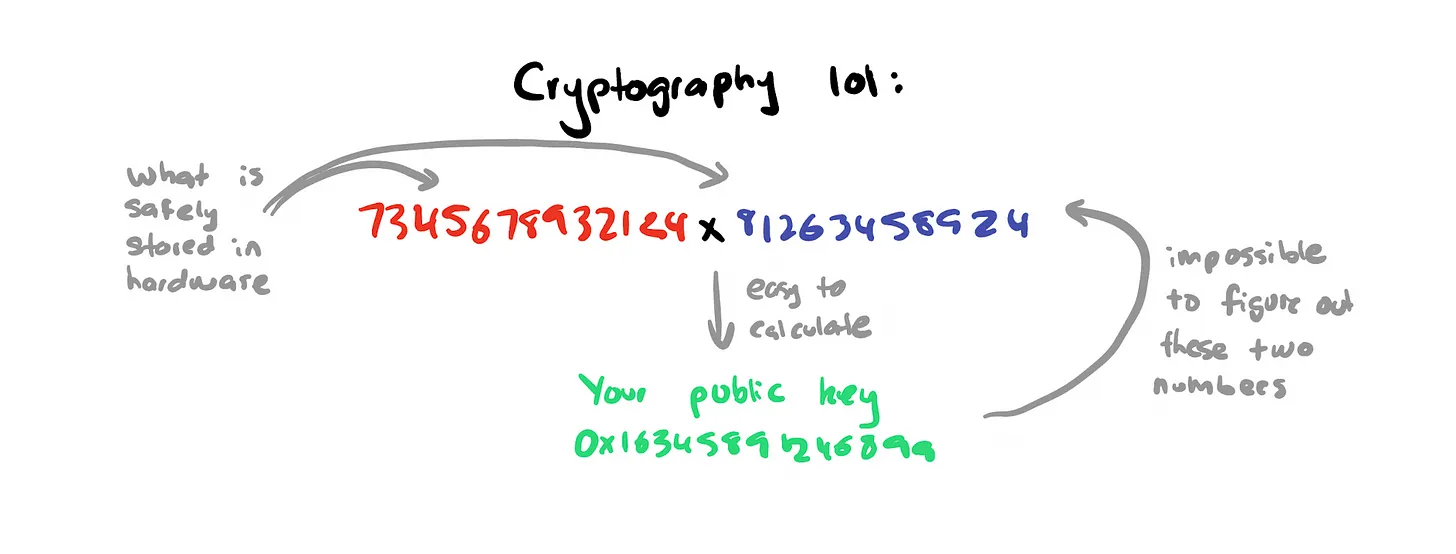
Identity cryptography essentially involves multiplying two large prime numbers to generate a new, larger number. While this sounds simple, the complication is that these primes are essentially impossible to guess, and they are virtually impossible to crack. When you authenticate using a private key, your hardware uses unique information to establish its identity. This approach represents a key shift in managing identities: identity owners know a large number of numbers that are also recognized by common criteria on the part of the recipient.
In contrast to this approach, traditional web infrastructure requires us to re-establish identities for each new service used, resulting in a different ID for each joined database.
Part 2: Crypto
So how does blockchain work? The second tricky part of the puzzle is, how do you verify when this information was broadcast? If you just sign a message with todays date, how do you know you have the correct date? Maybe you delegate responsibility for your time to another party, but what if they get compromised? You end up with recursive logic.
In an innovative sense, blockchain is a database that records expiration date information. They dont have the concept of time that humans rely on, they rely on block numbers to determine when something happens. I dont think we really realize how groundbreaking this is. You wouldnt send a transaction with a This is when the transaction occurred field. You simply submit your transaction to the network and when miners mine it, it is included in a block and then assigned a timestamp.
Think about it, what system exists that you give it information and it tells you when that information actually occurred. We always expect that when we say something or communicate online, thats when it happens. Not in the cryptocurrency space. When we want to convey information on-chain, we just express what we want to convey and the blockchain will tell us when it happened.
To summarize again:
Cryptography creates a shared authentication standard that we can all agree on;
Crypto, powered by blockchain, creates a shared time standard that we can all agree on.
Why is identity important?
In all of our frenzy for wealth, we forget that blockchain represents two key fundamental innovations. It also means that we can start changing the world by introducing one innovation and slowly adding a second innovation when it makes sense. You don’t need to apply both to have an impact.
By 2023, with the advent of AI, the world will need stronger identity standards. Information is the foundation of our society, but when trust and verification of information go downhill, we end up in some dangerous places.
Sending stablecoins and playing casino games are fun, but cryptocurrencies can address a greater good and solve larger problems facing society today. Since cryptocurrency is built on the foundation of cryptography, it has a larger ecosystem than elsewhere in terms of cryptographic standards. You can already see cryptography becoming the gold standard with Apples adoption of PassKeys and the rise of one-time passwords to enable 2 FA authentication.
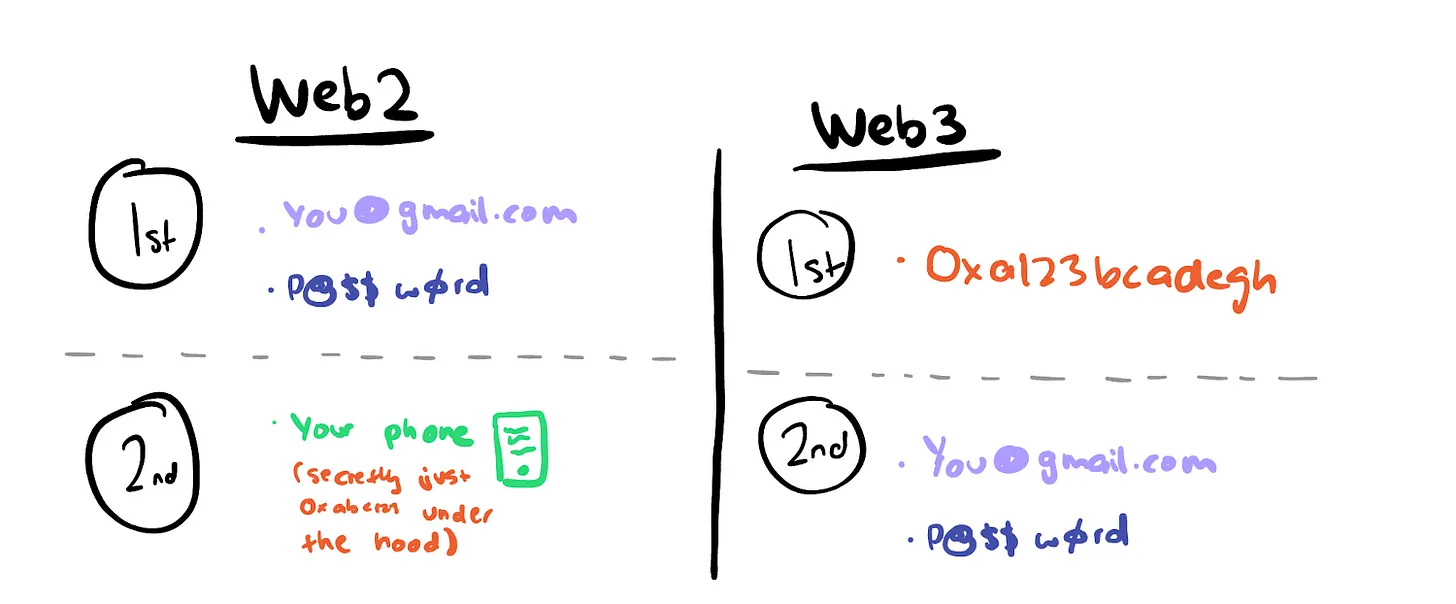
In Web2, cryptography is a second-class citizen.
In Web3, cryptography is a first-class citizen.
Okay, now that we’re all on the same plane, let’s talk about cryptocurrencies and identity. Ive been deeply involved with this problem over the years, and I think Ive identified some key links that werent obvious before. The biggest use case for cryptocurrency isn’t “decentralized identity” or some lofty ideal, it involves:
“Own your own data and profit from it”
“Upload passports on blockchain for better KYC”
“Create a new identity by combining your Twitter, Facebook and Ethereum addresses”.
These concepts are so far from reality that they are just empty narratives that do not create products that help real users. This narrative is primarily used to secure huge financing from investors without adding value to the end consumer. To clear up these misinformation, its important that we use better language to describe what were talking about. I think people draw the wrong conclusion when they even say things like on-chain identity because it means you have to do things on-chain. This isnt true either.
way forward
Permissionless Identity: “Portable, Persistent, Cryptographically Backed Identity”
They are what we know today as public keys. It doesn’t matter whether the data is on-chain or off-chain. The point is that you are identified/authenticated on the digital service via your public key. All information is tied to your public key, allowing for interoperability.
However, heres why they have a clear advantage over any other Web2 system we have today:
Build in one environment, use in another. All your activities and data in one ecosystem are accessible in a completely unrelated ecosystem.
Permanent. Once private keys are derived, they never disappear. You cannot delete private keys or on-chain data.
Can be used on-chain or off-chain. Your identity is a combination of all the places you authenticate as a public key, on or off the chain. The key is innovation, not blockchain.
Ability to create new identities (or shards) with the click of a button next to an existing identity. Unlike web2, all identities in web2 are ultimately tied to your passport (phone number, internet service provider). Permissionless identities do not require permission to be created or fragmented.
Anyone with an internet connection and access to the right hardware can use it. There is no issuing authority to generate an identity. As long as you have the right infrastructure in place to protect your identity, you can create one. Due to its borderless nature, the things you can do with this identity are limitless.
in conclusion
Permissionless identity fundamentally enables a whole new class of applications that are 10 times better than what you see on the existing Web. A world where one app improves the experience of every other app. Youll see the beginning of a flywheel effect, and Ive seen it develop as follows:
As applications like crypto consumers rise, they will all naturally rely on permissionless identity as a natural authentication standard.
These apps will be able to start sensing the context of your past behaviors and actions as well as those in other apps.
The ability to import environments from the past and elsewhere creates a better user experience.
Users are demanding that more applications support public key-based authentication in order to log in and use applications.
As the number of applications that support public key authentication increases, the more utility users gain from their permissionless identities.
My bet is that the main use case for encryption is already here: permissionless identity-based applications. The sooner we realize this, the faster we can move forward creating apps that people actually need.



