SharkTeam: Principle Analysis of Exactly Protocol Attack Events
On August 18, Exactly protocol was hacked, and the attackers have made approximately $12.04 million in profits. SharkTeam conducted a technical analysis of this incident immediately and summarized the security prevention measures. We hope that subsequent projects can learn from this and jointly build a security defense line for the blockchain industry.
1. Event analysis
Attacker address:
0x3747dbbcb5c07786a4c59883e473a2e38f571af9
0x417179df13ba3ed138b0a58eaa0c3813430a20e0
0xe4f34a72d7c18b6f666d6ca53fbc3790bc9da042
Attack contract:
0x6dd61c69415c8ecab3fefd80d079435ead1a5b4d
Attacked contract:
0x675d410dcf6f343219aae8d1dde0bfab46f52106
Attack transaction:
0x3d6367de5c191204b44b8a5cf975f257472087a9aadc59b5d744ffdef33a520e
0x1526acfb7062090bd5fed1b3821d1691c87f6c4fb294f56b5b921f0edf0cfad6
0xe8999fb57684856d637504f1f0082b69a3f7b34dd4e7597bea376c9466813585
Attack process:
(1) The attacker (0x417179df) first created multiple malicious market token contracts and multiple uniswapPool contracts through the attack contract (0x6dd61c69).
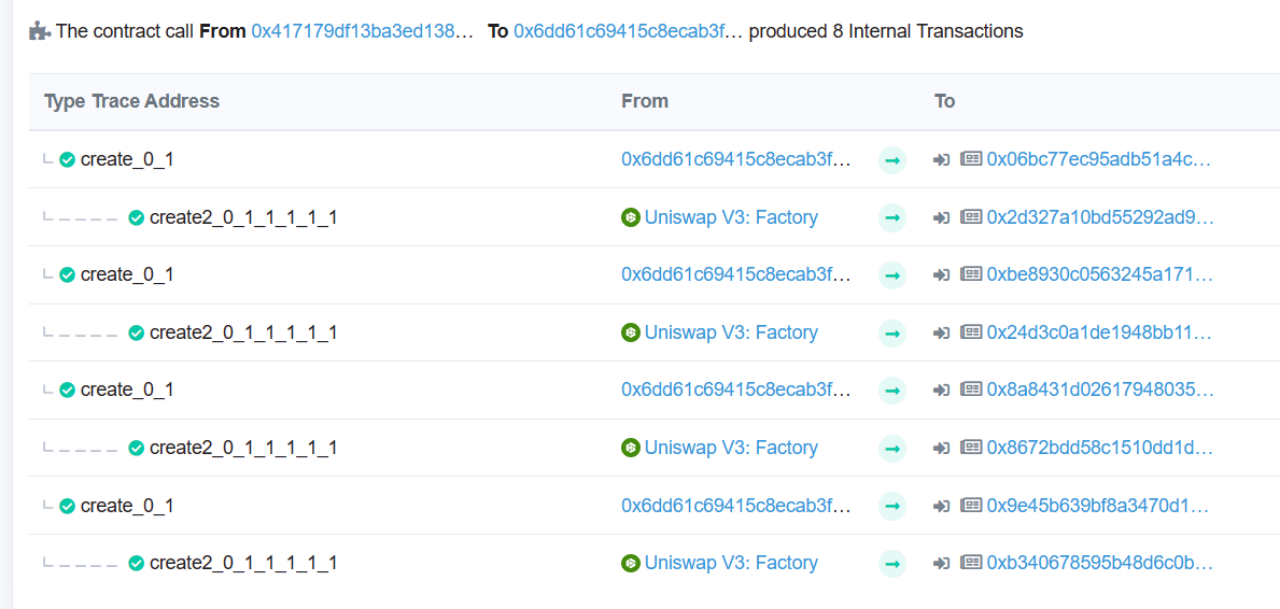

(2) Then call the leverage function of the attacked contract (0x675d410d) and pass in a malicious market token address.
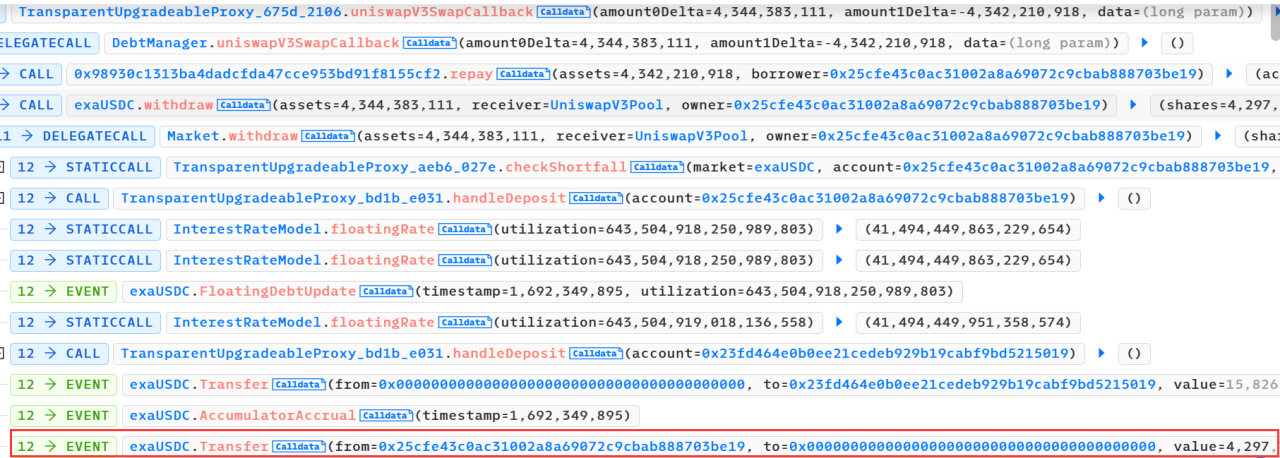
(3) In the leverage function, add the liquidity of USDC and malicious market tokens to the pool contract through the deposit function and re-enter the crossDeleverage function of the attacked contract (0x675d410d).
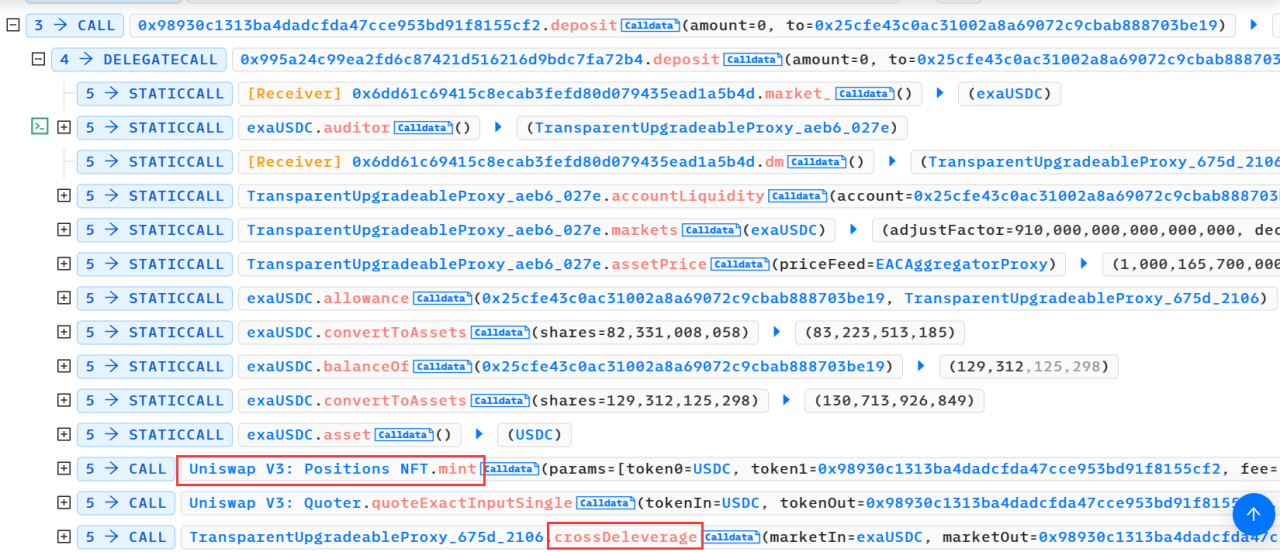
(4) The attacked contract (0x675d410d) in the crossDeleverage function will use USDC to exchange malicious market tokens in the pool contract.

(5) After the function call is completed, the attack contract (0x6dd61c69) removes the liquidity in the pool and then proposes profit from the exchanged USDC tokens.
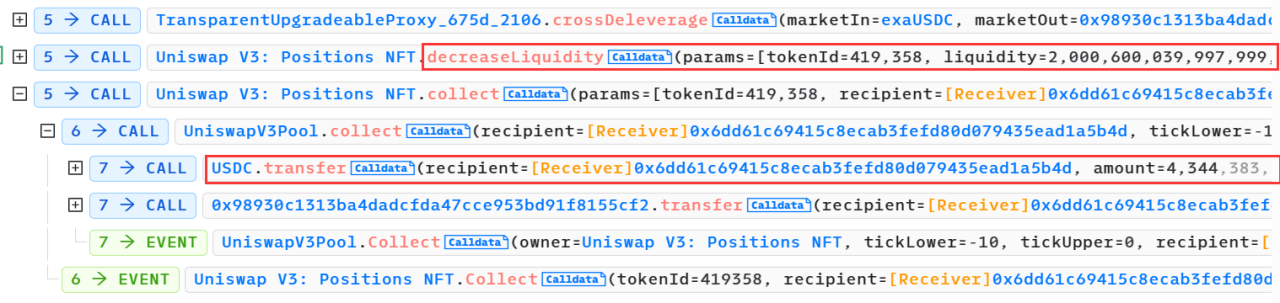
(6) Loop through the above operations multiple times, and each attack will replace the attacked user address and the malicious market token address.
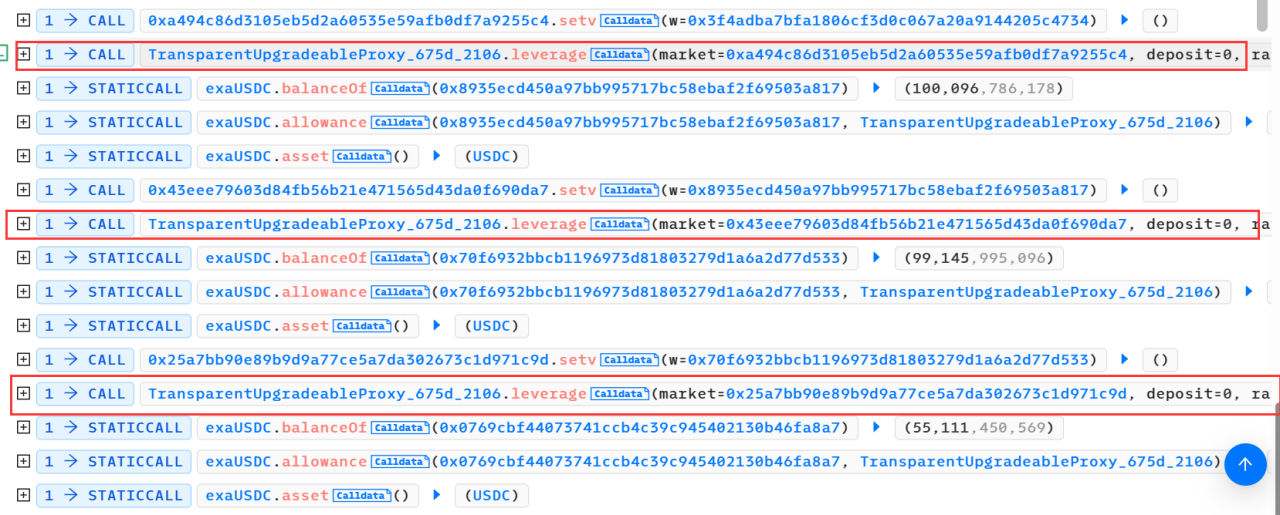
(7) Then send the obtained USDC to the attacker (0xe4f34a72).
(8) Perform the same operation multiple times to make a profit
2. Vulnerability Analysis
This attack exploits a vulnerability in the DebtManager (0x675d410d) contract. The leverage function does not verify whether the incoming market parameter is a trusted market contract. As a result, the state variable _msgSender can be modified in the permit function decorator to be the attackers. Arbitrary reference address.

Finally, when exchanging with the pool, the users exaUSDC balance will be used to offset the amount of USDC paid to the pool contract.
3. Security Recommendations
In response to this attack, we should follow the following precautions during the development process:
(1) When it comes to parameter transfer and calls from external addresses, it should be strictly verified whether the parameter transfer address is a trusted address.
(2) Before the project goes online, a smart contract audit needs to be conducted with a third-party professional audit team.
About Us
SharkTeams vision is to comprehensively protect the security of the Web3 world. The team is composed of experienced security professionals and senior researchers from all over the world. They are proficient in the underlying theory of blockchain and smart contracts, and provide services including smart contract audits, on-chain analysis, emergency response and other services. Long-term partnerships have been established with key players in various areas of the blockchain ecosystem, such as Polkadot, Moonbeam, polygon, OKC, Huobi Global, imToken, ChainIDE, etc.
Official website:https://www.sharkteam.org