The clip was caught by the clip, analyzing how the MEV robot became a cash machine for hackers
This afternoon, crypto users3155.ethAccording to the article, some top MEV robots are becoming the target of hackers, and the trading modules in their "sandwich attack" have been replaced, which has caused more than $20 million in losses. This may become a major turning point for the entire MEV ecosystem.
Odaily query found that the hacker attack occurred about 10 hours ago (Ethereum block height 16964664), the hacker used eight wallet addresses (the original funds on the chain came from Kucoin), and attacked five MEV robots, namely:

According to on-chain analysis agenciesLookonchainAccording to statistics, the current total loss is about 25.2 million US dollars, mainly involving five major currencies, as follows: 7461 WETH (13.4 million US dollars), 5.3 million US dollars USDC, 3 million US dollars USDT, 65 WBTC (1.8 million US dollars) and 1.7 million US dollars DAI.
Before understanding this attack, we first need to know what is MEV and how does MEV implement a sandwich attack?
The so-called MEV is the abbreviation of "Miner Extractable Value" or "Maximal Extractable Value". Miners or verifiers have the ability to sort transactions in blocks, so that some transactions can be pre-empted. The usual practice is that some MEV robots will pay high gas fees to get validators to prioritize transactions and make profits through the price difference; of course, there will also be validators who will go directly to package their own transactions without paying high gas fees.
The benign forms of MEV are arbitrage and liquidation, while the ones criticized by DeFi players are "sandwich attacks", that is, they "jump the queue" to conduct their own transactions to purchase assets before the original transaction, and then sell them to the original purchaser at a higher price. Generally speaking, a bundle can be split into three transactions: 1) a large purchase, 2) a transaction of a clamped user; 3) a large sale.
The security company CertiK told Odaily that the reason why this hacking attack was successful was that the hacker himself became a validator and could see the original information of the bundle of the MEV robot, so he replaced the second step with his own transaction and exchanged it with a cheap Token funding for MEV robots.
"Verifiers generally need to access certain information to mine transactions, and malicious verifiers can actually obtain bundle information from such as the public memory pool (mempool). Flashbot verifiers are usually more reliable because they have to pass MevHUB's KYC verification , to ensure that the data source is safe and trusted. In this case, because the verifier has the information, it can initiate a front-running transaction before the MEV seeker or MEV robot.”
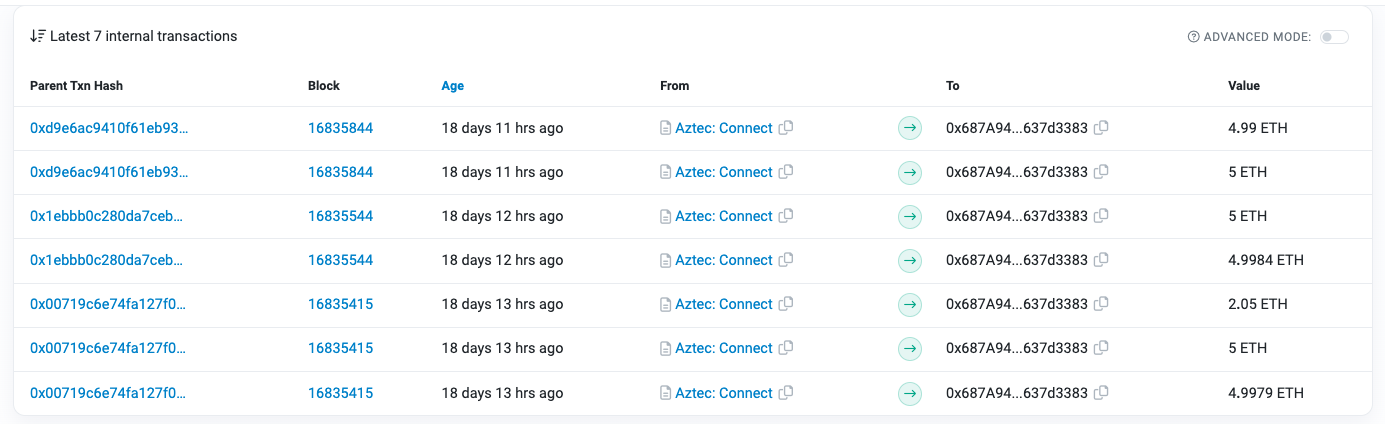
Odaily checked the data on the chain and found that the Ethereum block 16964664 belongs to Slot 6137846, which was proposed by the validator 552061. The validator’s 32 ETH funds were transferred by the hacker through the privacy protection agreement Aztec Network within 18 days, and remitted to the beginning of 0x 873 f 73 address, as follows:
After completing the preliminary preparations, the attacker will test whether the MEV robot will frontrun the transaction. For example, in the figure below, we can see that the attacker used 0.04 WETH to test the MEV robot and seduce the MEV robot for arbitrage; it was found that there was indeed a MEV robot monitoring the ETH/Threshold pool of Uniswap V2, and it would use all its funds Arbitrage. During this period, hackers have also been testing whether MEV uses its own validators for block production.
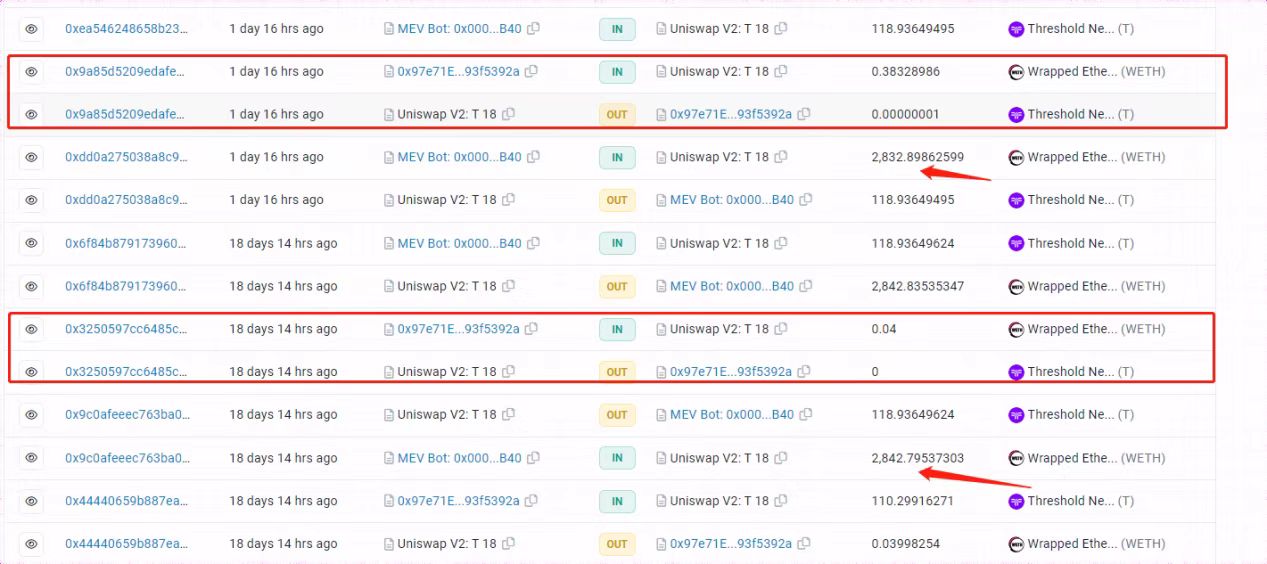
After the test is successful, the hacker will use a large number of tokens exchanged in Uniswap V3 in advance to perform exchange operations in the low-liquidity V2 pool, and seduce MEV to use all WETH to buy worthless Threshold tokens; Tokens are exchanged for all WETH invested by MEV robots. Since the WETH that MEV preempted has been exchanged by the attack transaction, the operation of the MEV robot to exchange back to WETH will fail.
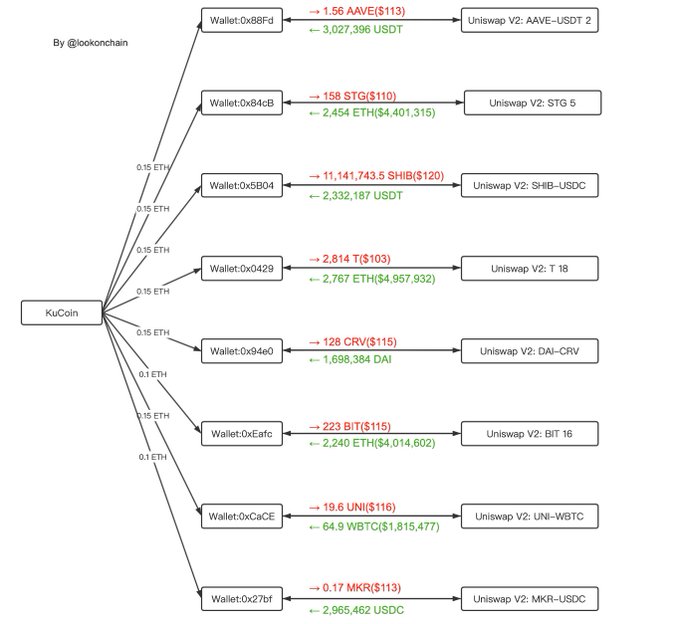
In addition to the Threshold token mentioned above, the hacker also manipulated seven other addresses to manipulate the prices of seven tokens in the Uniswap V2 pool, including AAVE, STG, SHIB, CRV, BIT, UNI, and MKR, to achieve profits, as follows Shown:
Security company Beosin believes that there are three main reasons why hackers can succeed: First, MEV will use all its own funds every time it arbitrages in a low-liquidity pool, without risk control; second, the V2 pool has low liquidity and is manipulated by hackers ; The third is to have the authority to verify the node and can modify the bundle.
This attack incident also reminded MEV searchers that in order to avoid "sandwich attack", it is necessary to adjust the transaction strategy in time and select some "reliable" verifiers with verification history. The data on the chain shows that the malicious verifier who attacked the MEV robot has been punished by Slash and kicked out of the verifier queue. The relevant funds have been pooled in the following three addresses, waiting for the next step. Odaily will continue to pay attention to the follow-up trend:
0x3c98d617db017f51c6a73a13e80e1fe14cd1d8eb;
0x5B04db6Dd290F680Ae15D1107FCC06A4763905b6;
0x27bf8f099Ad1eBb2307DF1A7973026565f9C8f69



