Analysis of the attack on Nomad: Hackers ignite the fire, and many people "take advantage of the fire to rob"
On August 2, Beijing time, public opinion monitoring on the Chengdu Lianan Chain Bing-blockchain security situational awareness platform showed that the cross-chain communication protocol Nomad was attacked, and the hackers made a profit of about 150 million U.S. dollars. As of press time, according to DeFi Llama data, there is only about $5,900 left in the Nomad token bridge.
secondary title
PART 01
The first decentralized heist in the crypto market?
First of all, let’s get to know the protagonist of this story——Nomad.
Nomad claims to provide a secure interoperability solution designed to reduce costs and improve the security of cross-chain messaging. Unlike validator-based cross-chain bridges, Nomad does not rely on a large number of external parties to verify cross-chain communications, but By utilizing an optimistic mechanism, users can safely send messages and bridge assets, and guarantee that anyone watching can flag fraud and protect the system.
On April 13, they also completed a seed round of financing of up to 22 million US dollars at a valuation of 225 million US dollars, led by Polychain. For a start-up project, tens of millions of dollars in seed financing can be said to win at the starting line, but after this attack, it is not known how the project party will deal with it and "save itself".
Nomad's official Twitter account said it was aware of the incident and is currently investigating.
Regarding this incident, it has caused controversy in the Web3 field.
Terra researcher FatMan commented on the Nomad attack on Twitter, saying: "A message popped up on a public Discord server saying that anyone can grab $3k-$20k from the Nomad bridge: all to do All it takes is to copy the first hacker’s transaction and change the address, then click send via Etherscan. This is the first decentralized heist ever to happen in a real crypto market.”
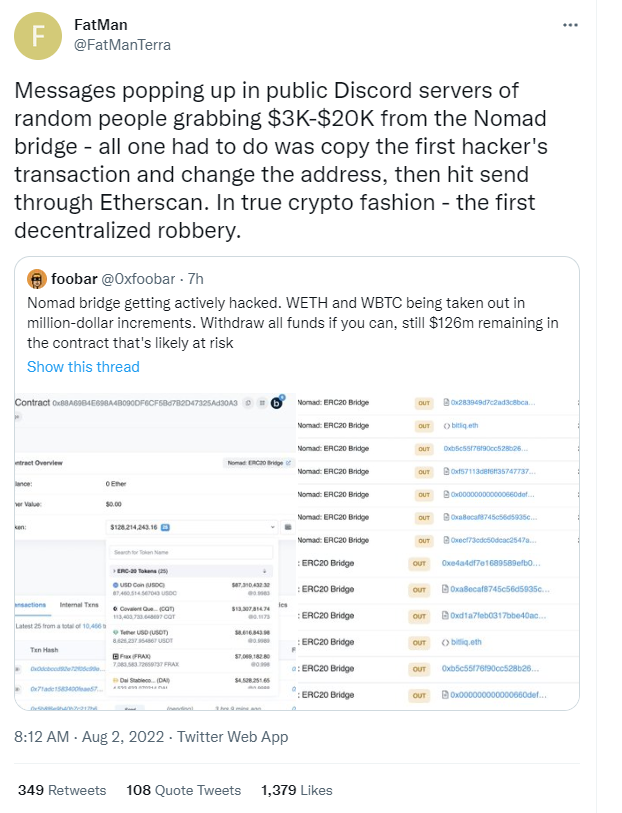
And indeed it is.
According to Odaily's report, after the first hacker's theft was completed, this "successful" experience was also circulated in the encryption community, and was imitated by more users, taking advantage of the fire. The assets of the cross-chain communication protocol Nomad were looted.
secondary title
PART 02
-What mistakes did the project party make when deploying the contract to cause it to be attacked?
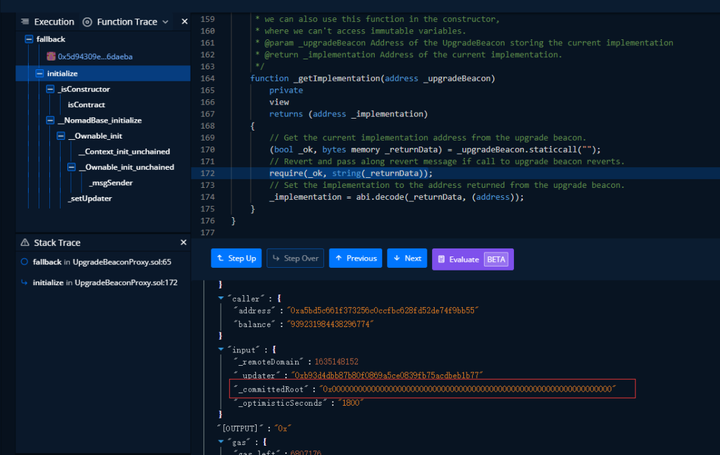
This attack is mainly because the project party sets the confirmAt of zero (0x000000....) to 1 when deploying the contract, so that any unused _message can pass the judgment and extract the corresponding assets from the contract. The technical analysis is as follows:
Attacked contract
0x5D94309E5a0090b165FA4181519701637B6DAEBA (contract with exploit)
0x88A69B4E698A4B090DF6CF5Bd7B2D47325Ad30A3 (vault contract suffering loss)
Due to too many attack transactions, the following uses the analysis of one of the attack transactions as an example to illustrate;
1. Through transaction analysis, it was found that the attacker extracted funds in the (0x88A69) contract by calling the process function in the (0x5D9430) contract.
2. Follow up the process function, you can see that the contract has judged _messageHash. When the input messages[_messageHash] is 0x000000...., the return value is true.
3. Then follow up the acceptableRoot function and find that when the value of _root is zero (0x000000....), and confirmAt[_root] is equal to 1, the judgment is always established, so that the attacker can withdraw the funds in the contract.
secondary title
PART 03
- Can the project party recover the stolen funds?
In response to the loss caused by the cross-chain token bridge attack, the Nomad team stated, "The investigation is ongoing, and major companies in blockchain intelligence and forensics have been contacted for assistance. We have notified law enforcement agencies and will deal with the situation around the clock. Provide timely and up-to-date information. Our goal is to identify relevant accounts and trace and recover funds."
Currently, the security team of Chengdu Lianan is using the Lianbizhui platform to monitor, track and analyze the stolen funds addresses.
PART 04
-Summary: What issues need to be paid attention to in contract deployment?
In response to this incident, the security team of Chengdu Lianan suggested that the project party need to consider whether the configuration is reasonable before deploying the contract. After deployment, you should test the relevant functions to see if there is a risk of being exploited, and contact an audit company to check whether the initial parameters are reasonable.



