Cross-chain bridge has become the biggest security risk in the industry, why and what to do
This article comes from Chainalysis, compiled by Odaily translator Katie Koo.

This article comes from
, compiled by Odaily translator Katie Koo.
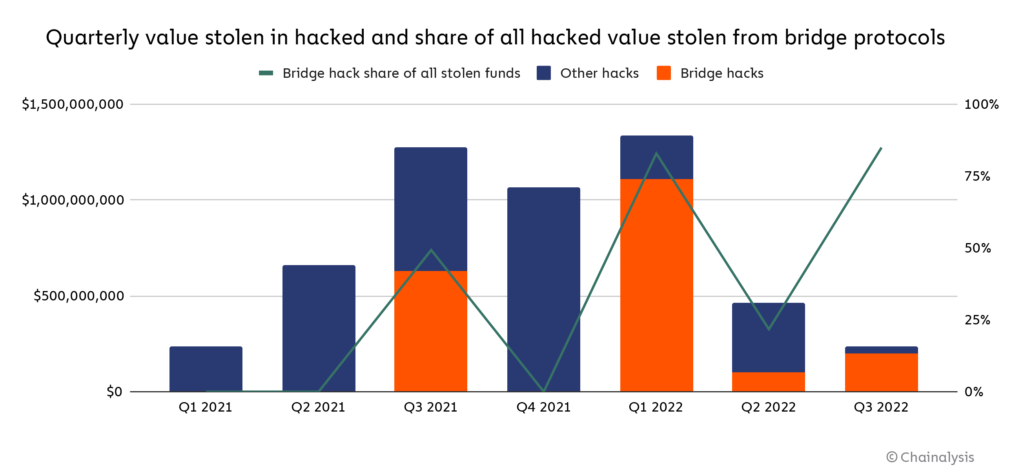
This is a significant threat to the establishment of trust in blockchain technology. As more and more value flows across bridges, they become more attractive targets for hackers. Cross-chain bridges are also now a top target for North Korea-linked hackers, who we estimate have stolen roughly $1 billion worth of cryptocurrency so far this year, all from cross-chain bridges and other DeFi protocols.
The good news is that these platforms can take steps to protect themselves. In the event of a hack, they can use the transparency of blockchain technology to investigate the flow of funds and ideally prevent attackers from cashing out their ill-gotten gains.
secondary title
The purpose of the cross-chain bridge is to solve the interoperability challenges between different blockchains. The cross-chain bridge protocol allows users to transfer assets from one blockchain to another. For example, Wormhole is a cross-chain bridge protocol that allows users to transfer cryptocurrencies and NFTs between various smart contract blockchains such as Solana and Ethereum.
While cross-chain bridge designs vary, users typically interact with cross-chain bridges by sending funds from their assets to the cross-chain bridge protocol, where the funds are then locked in a contract, and the agreement is issued to users to cross-chain to Equivalent funds of equivalent assets on the chain. In the case of Wormhole, users usually send ETH to the protocol, which is held as collateral and issued on Solana in the form of Wormhole-wrapped ETH, which is locked in the Wormhole contract on Ethereum. support.
Why do cross-chain bridges always have accidents?
Cross-chain bridges are an attractive target because they typically have a central point of storage for funds that support receiving "cross-chain" assets on the blockchain. Regardless of how the funds are stored (locked in a smart contract or via a centralized custodian) this storage point becomes a target for hackers. Furthermore, effective cross-chain bridge design remains an unresolved technical challenge, with many new models being developed and tested. As best practices improve over time, these different designs present new attack vectors that can be exploited by hackers.
secondary title
What can the crypto industry do?Just a few years ago, centralized exchanges were the most frequently targeted hacks in the industry. Today, successful attacks on centralized exchanges are rare. This is because the latest and most vulnerable platforms are always on the lookout for attacks.While not foolproof, the
A critical first step in addressing this type of problem could be making extremely rigorous code reviews the gold standard in DeFi, both for protocol builders and investors evaluating protocols.