The cross-chain bridge Nomad was hacked, and some users with "real names" took advantage of the fire to rob

On the morning of August 2, Beijing time, encryption KOL foobar tweeted that the cross-chain solution Nomad was hacked in the early hours of this morning, and the WETH and WBTC in the smart contract were being transferred out, worth about one million dollars each time.
As of press time, the total lock-up volume (TVL) of the Nomad token bridge is only 3,941 US dollars, while yesterday its TVL was about 190 million US dollars. According to preliminary analysis, the loss of Nomad is about 190 million US dollars. Users are advised not to associate with Nomad and its related assets for the time being. Item interaction.
Following the attack, Moonbeam's ongoing Ultimate Harvest Moon activity was suspended due to the attack (Moonbeam is now fully functional and operational). Multichain, a cross-chain routing protocol, tweeted that the TVL of Moonbeam and Moonriver has more than 160 million US dollars in assets, and the safety of assets has not been affected.
Evmos tweeted that the Evmos chain is running normally; in addition, Nomad has been suspended, so users cannot withdraw their ERC20 encapsulated assets from Evmos to Ethereum, and the team will promptly notify how this affects Evmos users and users with Nomad encapsulated assets.
The official Nomad response stated, “We are aware of incidents involving the Nomad Token Bridge. We are currently investigating and will provide updates when we have one. We understand that impostors are posing as Nomad and providing fraudulent addresses to collect funds, we have not yet Provide instructions for returning bridge funds, please ignore messages from all channels other than the official Nomad channel."
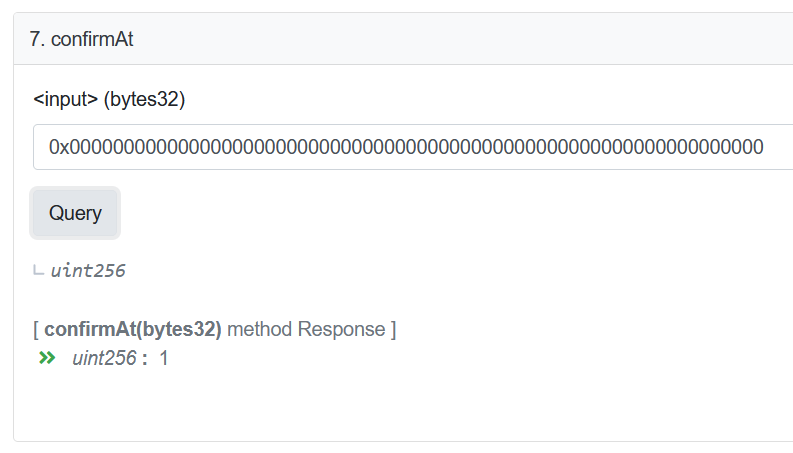
The root cause of this theft is that an error occurred when Nomad officially upgraded the smart contract.Paradigm security researcher samczsun said its replica contract was fatally flawed, a routine upgrade marked zero hash as a valid root, which had the effect of allowing information to be spoofed on Nomad; attackers exploited this to copy/paste transactions and quickly drain the bridge assets on.
"During a routine upgrade, the Nomad team initializes the root of trust to 0x00. To be clear, it is a common practice to use a value of zero as the initialization value. Unfortunately, in this case it has automatic validation every A tiny side effect of a message. This is why hackers are so confusing - you don't need to know Solidity or Merkle Trees or anything like that. All you have to do is find a valid transaction, find/replace the other party's address with yours, Then rebroadcast it."
Contract design loopholes are only one of the problems. The Nomad official’s response to this incident was also quite “slow” and lacked risk control.When foobar tweeted, there were still $130 million in assets in the cross-chain bridge, and there were still $75 million in assets until the official tweet was released, but Nomad officials did not seem to take any urgent action, watching the asset loss return to zero.
Mo Dong, the co-founder of Celer Network, explained in the community that the official reason for being "indifferent" is mainly because the contract upgrade has a time lock, which makes it impossible to respond immediately. "There is a time lock for contract upgrades, and there is no risk control, so I can only watch + masturbate myself."
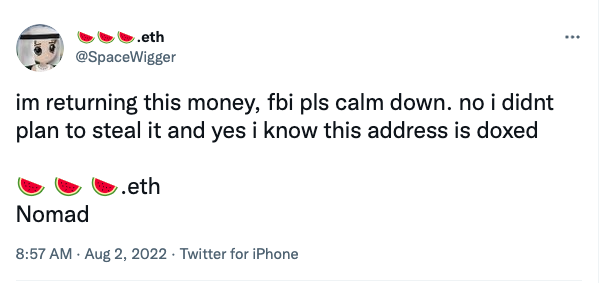
In fact, after the first hacker's theft was completed, this "successful" experience was also circulated in the encryption community, and was imitated by more users to take advantage of the fire.Perhaps because of being too impatient, some users forgot to use vests to disguise, and directly used their usual ENS domain names, fully exposed (this may reduce the burden on Nomad's follow-up recovery). At present, some users have begun to refund spontaneously in order to avoid being sued. Odaily will continue to pay attention to the follow-up progress.
Related Reading
Related Reading
Over $150 million loss, cross-chain bridge protocol Nomad hacking analysis analysis



