Overnight, "supply chain attacks" dominated headlines: What happened? How can we mitigate the risks?
- 核心观点:NPM供应链攻击威胁加密资产安全。
- 关键要素:
- 恶意代码静默篡改加密货币地址。
- 受影响包周下载量超10亿次。
- 黑客已通过地址替换获利。
- 市场影响:引发对Web3基础设施安全担忧。
- 时效性标注:短期影响。
Original | Odaily Planet Daily (@OdailyChina)
Author|Azuma (@azuma_eth)

On September 9th, Beijing time, Charles Guillemet, Chief Technology Officer of Ledger, published a warning on X: " A large-scale supply chain attack is currently underway, and the NPM account of a well-known developer has been compromised. The affected packages have been downloaded more than 1 billion times, which means that the entire JavaScript ecosystem may be at risk. "
Guillemet added: "The malicious code works by silently tampering with cryptocurrency addresses in the background to steal funds. If you use a hardware wallet, please carefully check every signed transaction and you will be safe. If you do not use a hardware wallet, please avoid making any on-chain transactions for the time being. It is not clear whether the attackers are directly stealing the mnemonic phrases of software wallets."
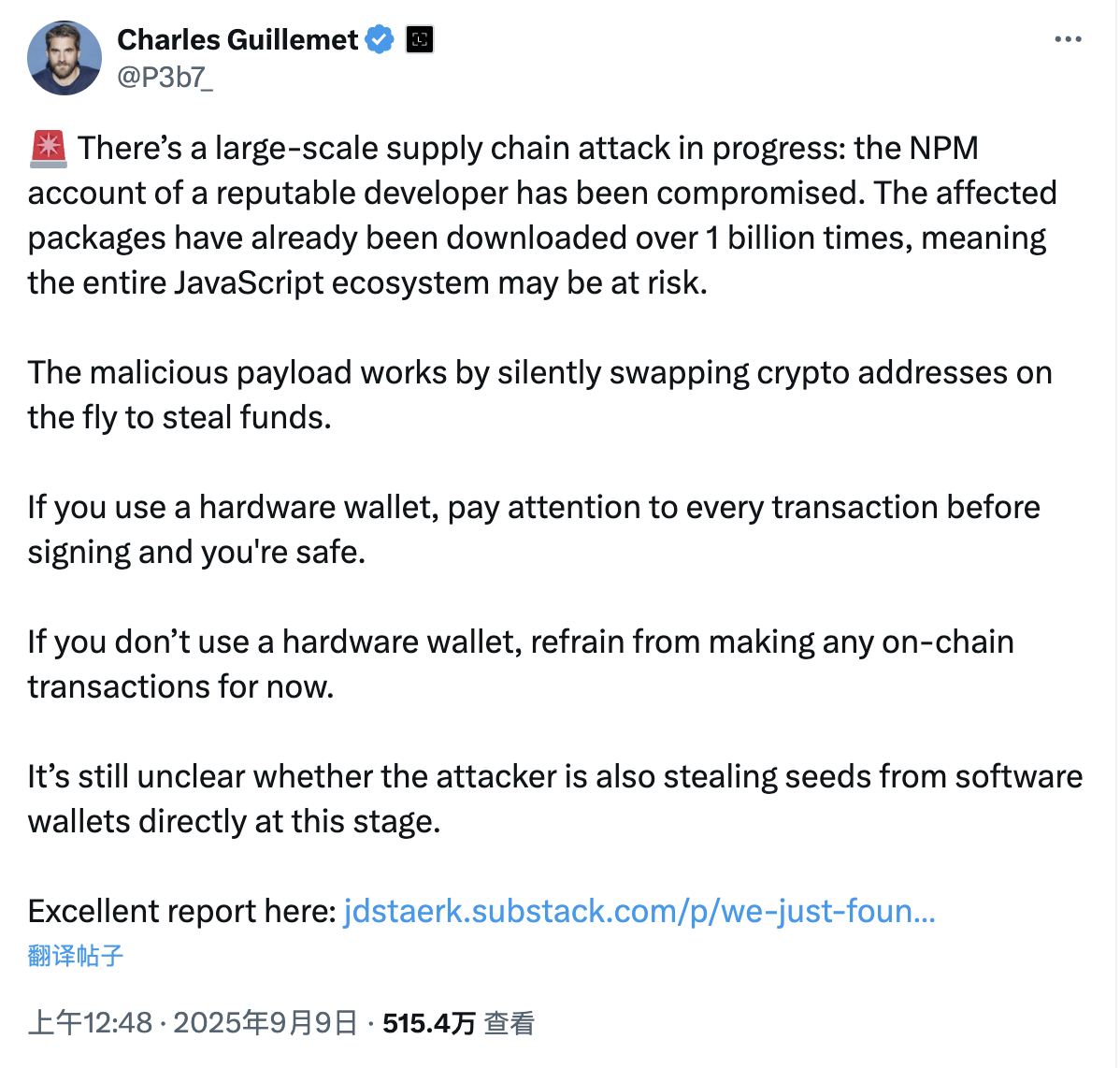
what happened?
According to the security report cited by Guillemet, the direct cause of this incident was that the NPM account of well-known developer @qix was hacked, resulting in the release of malicious versions of dozens of software packages, including chalk, strip-ansi and color-convert. The malicious code may have spread to the terminal when developers or users automatically installed dependencies.
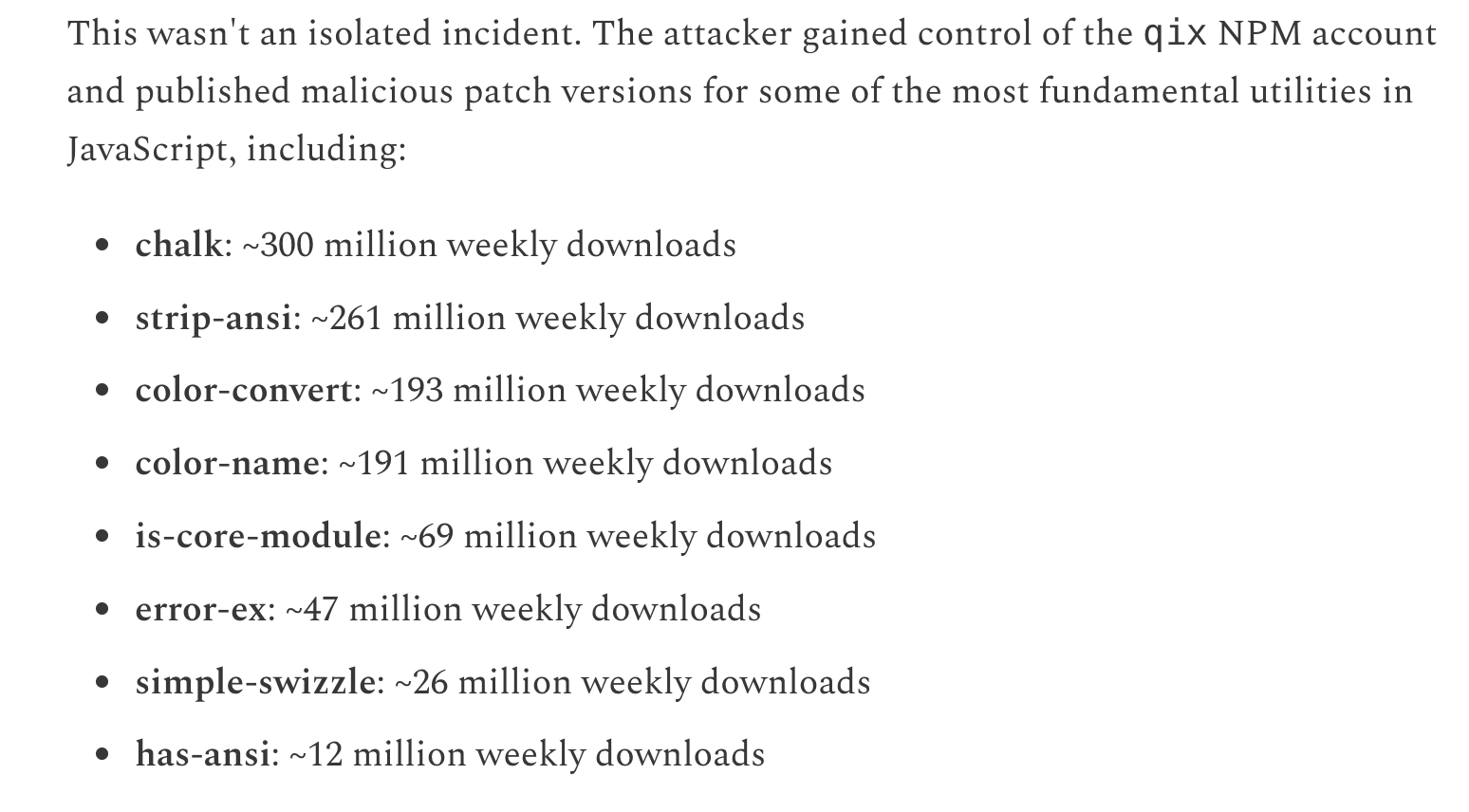
Odaily Note: Weekly download data of compromised software packages.
In short, this is a classic case of a supply chain attack—an attack in which an attacker inserts malicious code (such as NPM packages) into development tools or dependency systems. NPM, short for Node Package Manager, is the most commonly used package management tool in the JavaScript/Node.js ecosystem. Its primary functions include managing dependencies, installing and updating packages, and sharing code.
NPM's ecosystem is extremely large, with millions of software packages currently available. Almost all Web3 projects, crypto wallets, and front-end tools rely on NPM. Precisely because NPM relies on a large number of dependencies and complex links, it is a high-risk entry point for supply chain attacks. As long as an attacker implants malicious code in a commonly used software package, it may affect thousands of applications and users.
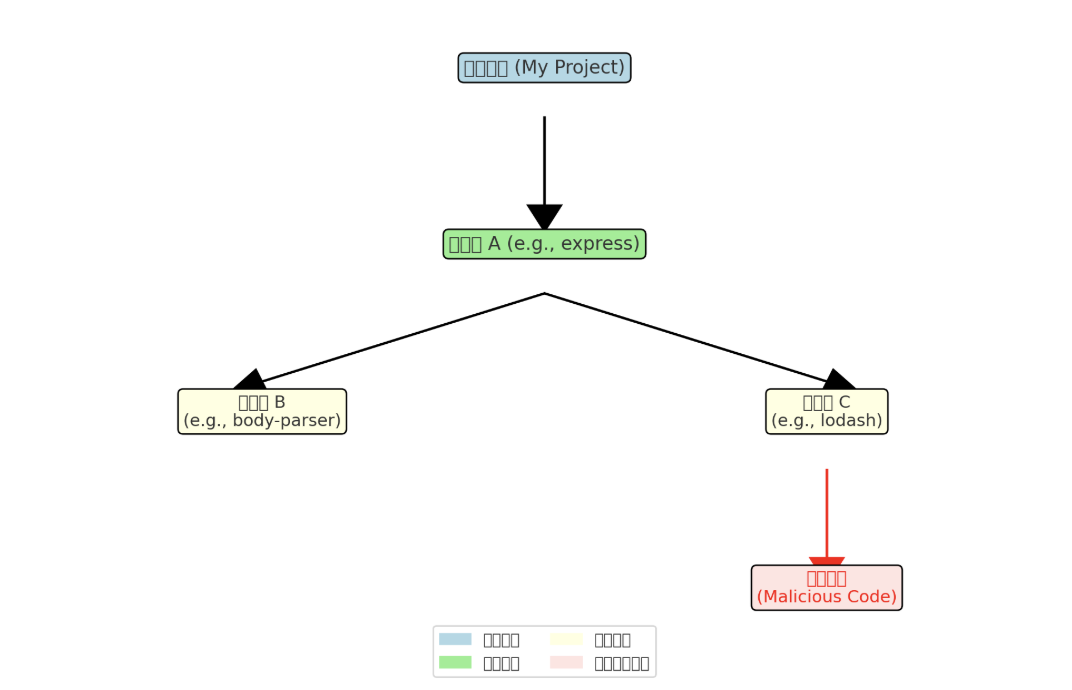
As shown in the malicious code diffusion flow chart above:
- A certain project (blue box) will directly depend on some common open source libraries, such as express.
- These direct dependencies (green boxes) in turn depend on other indirect dependencies (yellow boxes, such as lodash).
- If an indirect dependency is secretly implanted with malicious code (red box) by an attacker, it will enter the project along the dependency chain.
What does this mean for cryptocurrencies?
The direct relevance of this security incident to the cryptocurrency industry lies in the fact that the malicious code implanted by hackers into the above-mentioned contaminated software package is a sophisticated "cryptocurrency clipboard hijacker" that steals crypto assets by replacing wallet addresses and hijacking transactions.
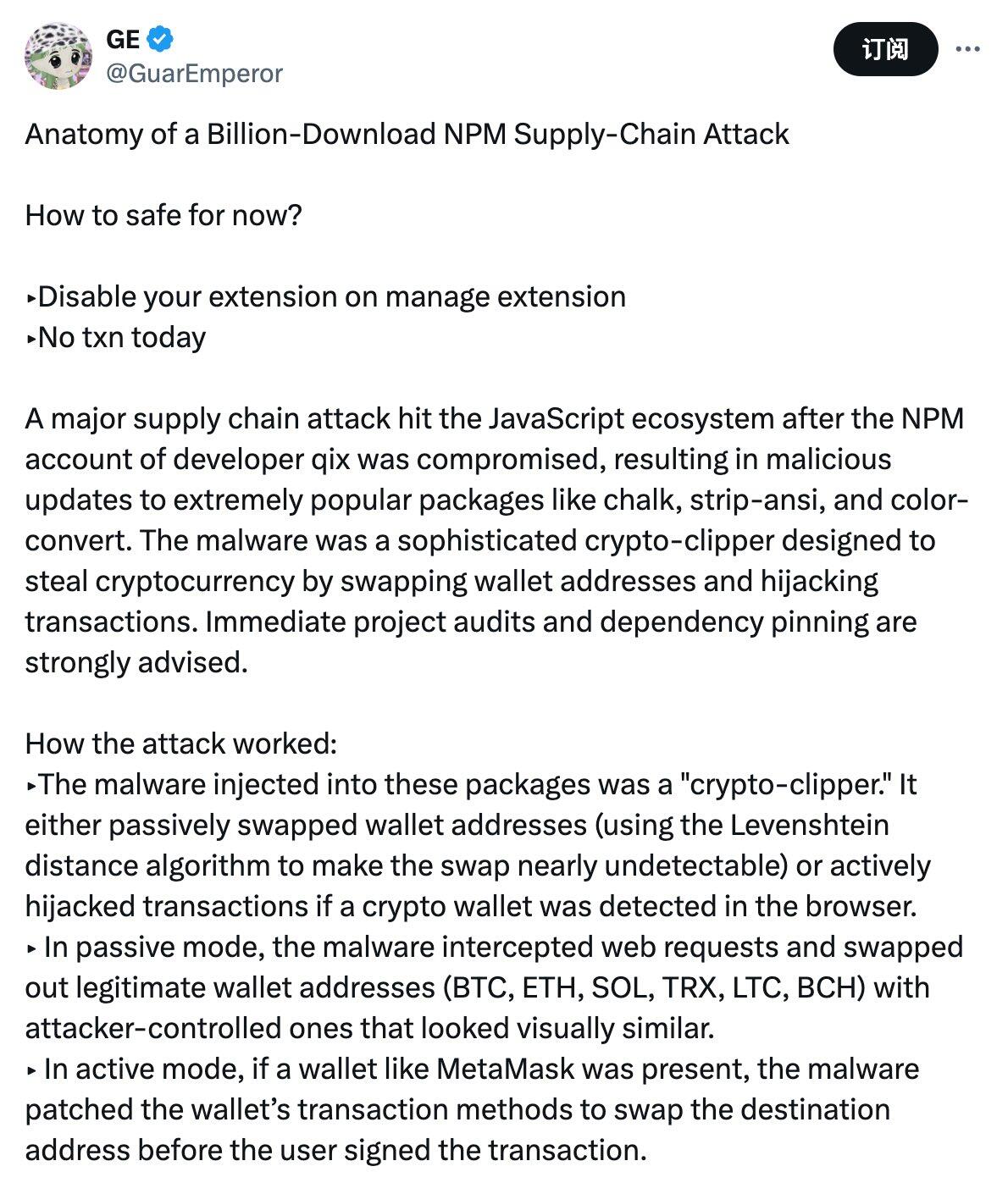
Stress Capital founder GE (@GuarEmperor) explained this in more detail on X. The "clipboard hijacker" injected by the hacker uses two attack modes: passive mode uses the "Levenshtein distance algorithm" to replace the wallet address, which is extremely difficult to detect due to its visual similarity; active mode detects the encrypted wallet in the browser and tampered with the target address before the user signs the transaction.
Since this attack targets JavaScript project base-layer libraries, even projects that indirectly rely on these libraries may be affected.
How much profit do hackers make?
The malicious code implanted by the hacker also disclosed its attack address. The hacker's main attack address on Ethereum is 0xFc4a4858bafef54D1b1d7697bfb5c52F4c166976, and the funds mainly come from the following three addresses:
- 0xa29eEfB3f21Dc8FA8bce065Db4f4354AA683c0240
- x40C351B989113646bc4e9Dfe66AE66D24fE6Da7B
- 0x30F895a2C66030795131FB66CBaD6a1f91461731
Arkham has created a tracking page for this attack, where users can check the hacker's profit and transfer status in real time.
As of this post, the hackers have only profited $496 from the attack, but considering that the extent of the malicious code's spread has not yet been determined, it is expected that this figure may continue to rise . The developer has now been notified and is actively working with the NPM security team to resolve the issue. The malicious code has now been removed from most of the affected packages, so the situation is under control.
How to avoid risks?
Defillama founder @0xngmi Yu X said that although this incident sounds dangerous, the actual impact is not that exaggerated - because this incident will only affect websites that have pushed updates since the hacked NPM package was released, and other projects will still use the old version; and most projects will fix their dependencies, so even if they push updates, they will continue to use the old security code.
However, since users cannot really know whether a project has fixed dependencies or whether it has some dynamically downloaded dependencies, the project party is currently required to conduct self-inspection and disclose it first.
As of this posting, multiple wallet or application projects, including MetaMask, Phantom, Aave, Fluid, and Jupiter, have disclosed that they are not affected by this incident. Therefore, in theory, users can safely use confirmed secure wallets to access confirmed secure protocols. However, for other wallets or projects that have not yet made security disclosures, it may be safer to temporarily avoid using them.



