A vernacular explanation of the underlying logic of Web3 signature phishing: the difference between authorized phishing, Permit and Permit2
Original author: Spinach Spinach|bocaibocai (X: @wzxznl )
I just signed my name, how come my money is gone? ? "Signature phishing" is currently becoming the favorite phishing method of Web3 hackers. Recently, I saw that the cosine boss @evilcos and major wallets and security companies are constantly promoting the knowledge of phishing signatures, but many people are still phished every day.
Bobo believes that one of the reasons is that most people do not understand the underlying logic of wallet interaction, and the learning threshold is too high for people who do not understand technology. Therefore, Bobo decided to produce a graphic version of the underlying logic of signature phishing, and try to use the most colloquial form so that people who do not understand technology can understand it.
First of all, we need to know that there are only two operations when we use the wallet: "signature" and "interaction". The simplest and most direct understanding is that signature occurs outside the blockchain (off-chain) and does not require gas fees; interaction occurs on the blockchain (on-chain) and requires gas fees.
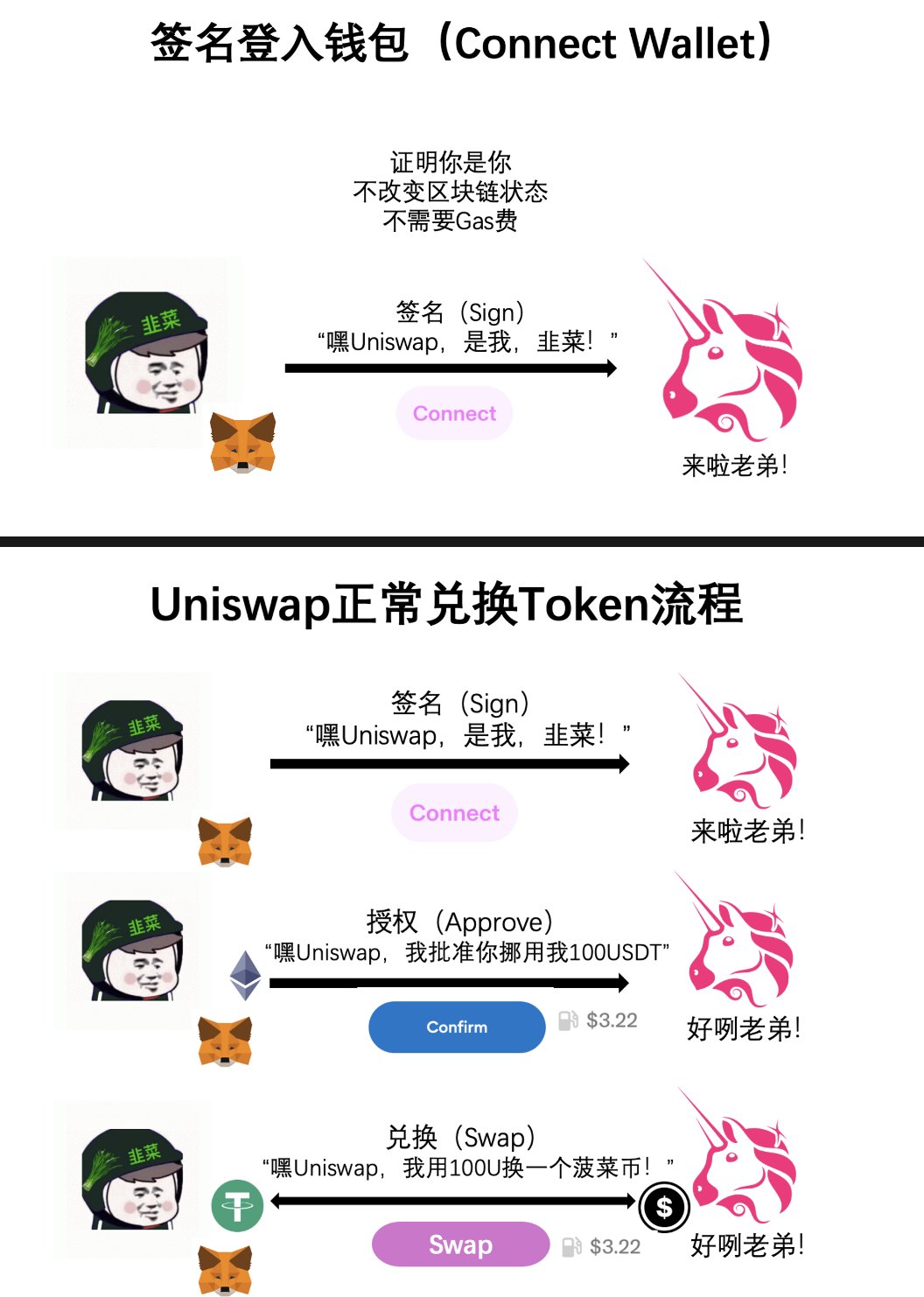
The general use scenario of signature is to verify that you are you, such as logging into a wallet. If you want to exchange tokens on Uniswap, you need to link your wallet first. Then you need to sign a name to tell the website "I am the owner of this wallet", and then you can use Uniswap. This step will not change any data or status of the blockchain, so you don't need to spend money. As for interaction, when you really want to exchange tokens on Uniswap, you need to spend a sum of money to tell the USDT contract: "I want to exchange 100 USDT for a spinach coin, and I approve you to move my 100 USDT." This step is called authorization. Then you have to spend another sum of money to tell the Uniswap smart contract: "I am now going to exchange 100 USDT for a spinach coin, and you can operate now", and then you have completed the operation of exchanging 100 USDT for a spinach coin.
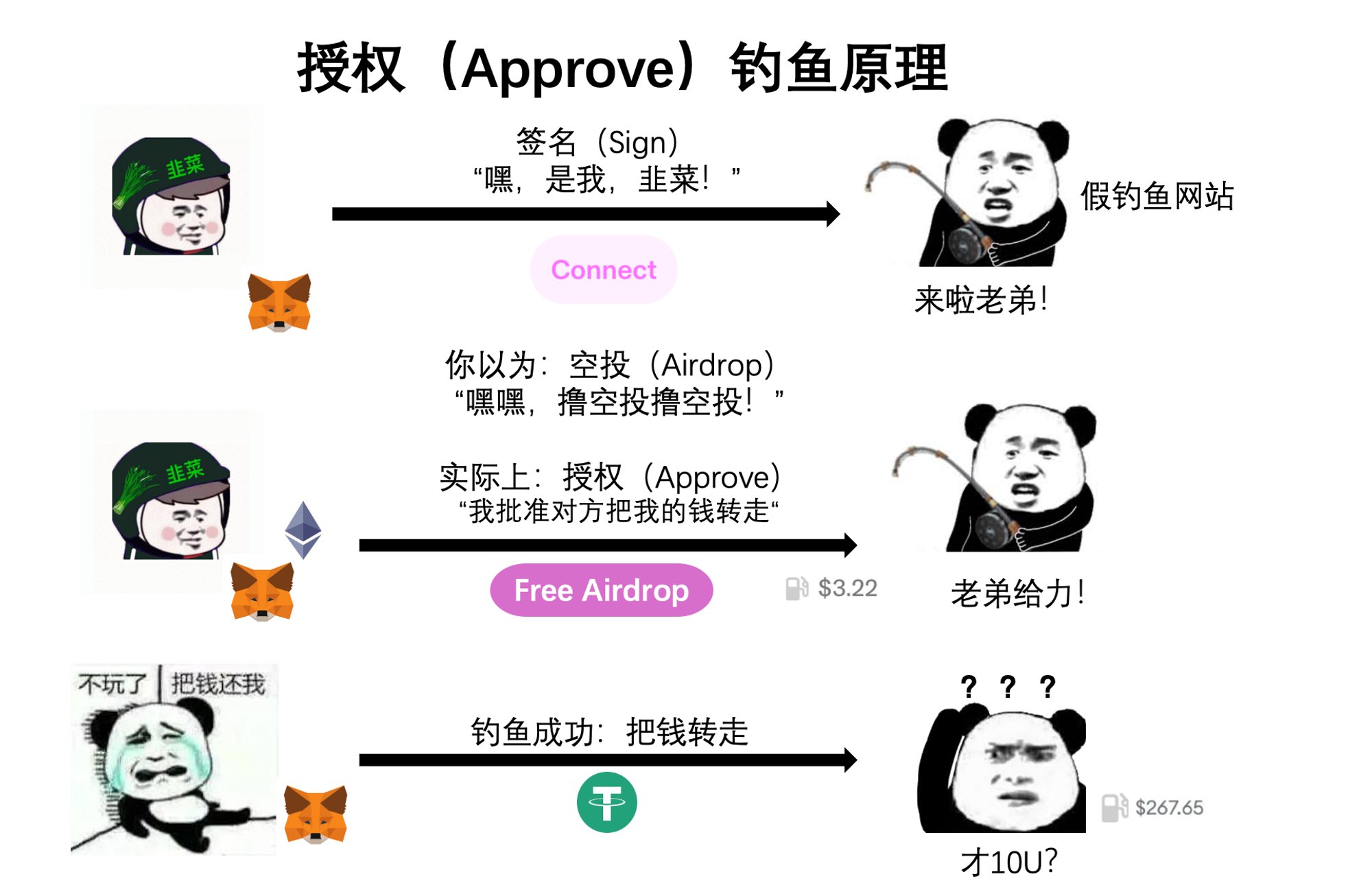
After a simple understanding of the difference between signature and interaction, let's introduce the principles of phishing. We will list three different methods: authorized phishing, permit signature phishing and permit 2 signature phishing. These three are very common phishing methods.
Let’s first talk about authorization phishing, which was one of the most classic phishing techniques in Web3 in the past. As the name suggests, it uses the authorization mechanism. The previous Uniswap example tells us that authorization is to tell the smart contract "I approve you to move so many xxx tokens of mine." Then the hacker can make a fake phishing website with a beautiful front-end disguised as an NFT project. In the middle of the website is a beautiful big button "Get your airdrop." In fact, after you click it, the interface that pops up in the wallet actually asks you to authorize your token to the hacker's address. If you click confirm at this time, then congratulations to the hacker for successfully completing a KPI.
However, there is a problem with authorized phishing: because it costs gas fees, many people are now wary of operations that involve spending money. After clicking on an unfamiliar website, they will find something wrong with a quick glance, so it is relatively easy to prevent.
Now let’s move on to today’s main topic: Permit and Permit 2 signature phishing, which is a major disaster area in the field of Web3 asset security. Why is it so difficult to prevent? Because every time you want to use a Dapp, you must sign and log in to your wallet. Many people may have formed an inertial thinking in their minds: “This operation is safe”, plus it does not cost money and most people do not know what each signature means.
Let's first look at the Permit mechanism. Permit is an extended function for authorization under the ERC-20 standard. For example, the USDT we usually use is ERC-20. In simple terms, you can sign to approve other people to move your tokens. We know that authorization (Approve) is when you spend money to tell the smart contract: "You can move my xxx number of tokens", then Permit is when you sign your name on a "note" to a certain person, and the paper says: "I allow someone to move my xxx number of tokens", and then this person takes this "note" to the smart contract and spends a gas fee to tell the smart contract: "He allows me to move his xxx number of tokens", and then your money can be moved away by others. In this process, you just signed a name, but behind it means that you allow others to call authorization (Approve) and transfer your tokens. Hackers can make a phishing website and replace the button for logging into the wallet with Permit phishing, so they can easily take your assets away.
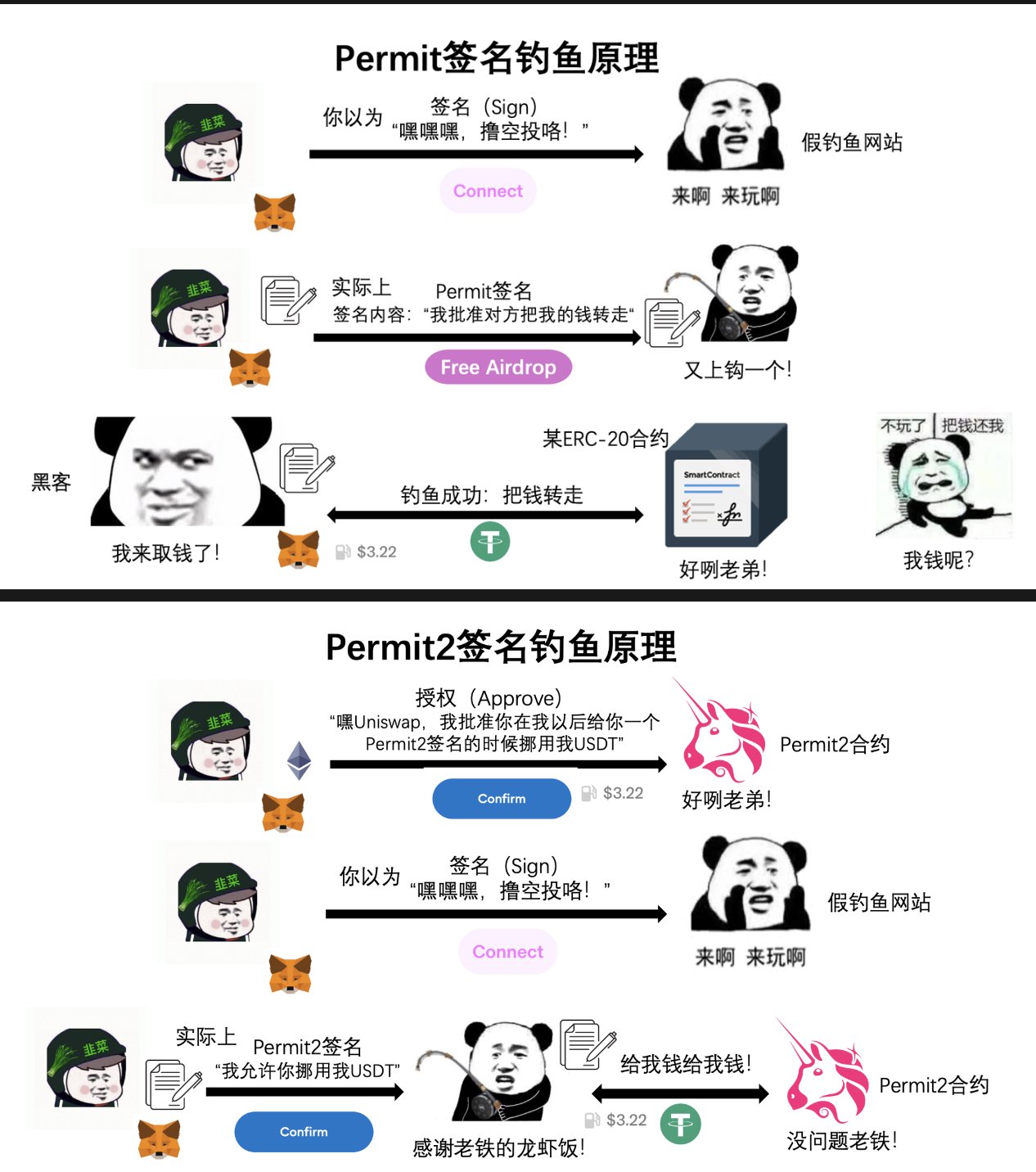
So what is Permit 2? Permit 2 is not actually a function of ERC-20, but a function launched by Uniswap for the convenience of users. In the previous example, if you want to exchange USDT for Baccarat on Uniswap, you need to authorize (Approve) once, and then exchange it, which requires two gas fees, so Uniswap came up with a solution: "You authorize me all the quotas at one time, and I will handle it for you every time you exchange it." This function helps Uniswap users only need to pay the gas fee once, and this step is signing, so the gas fee is not actually paid by you, but paid by the Permit 2 contract, but it will be deducted from the token you finally exchanged.
However, the condition for Permit 2 phishing is that you have used Uniswap before and have authorized an unlimited amount to the Permit 2 smart contract. Since the current default operation of Uniswap is unlimited authorization, the number of users who meet this condition is actually quite large. Similarly, hackers can transfer your tokens as long as they trick you into signing your name (only for those who have given authorization).
To sum up, the essence of authorization phishing is that you spend money to tell the smart contract: "I approve you to embezzle my tokens to the hacker", and the essence of signature phishing is that you sign a "note" to allow others to move your assets to the hacker, and the hacker spends money to tell the smart contract: "I want to embezzle his tokens and transfer them to me". Permit and Permit 2 are currently the hardest hit areas of phishing signatures. Permit is an authorization extension function of ERC-20, and Permit 2 is a new function launched by Uniswap.
Now that we understand the principle, how can we prevent it?
1. First and foremost, the most important thing is to develop your security awareness. Every time you operate your wallet, you should check what you are doing.
2. Separate large funds from wallets on the blockchain to minimize losses in the event of phishing.
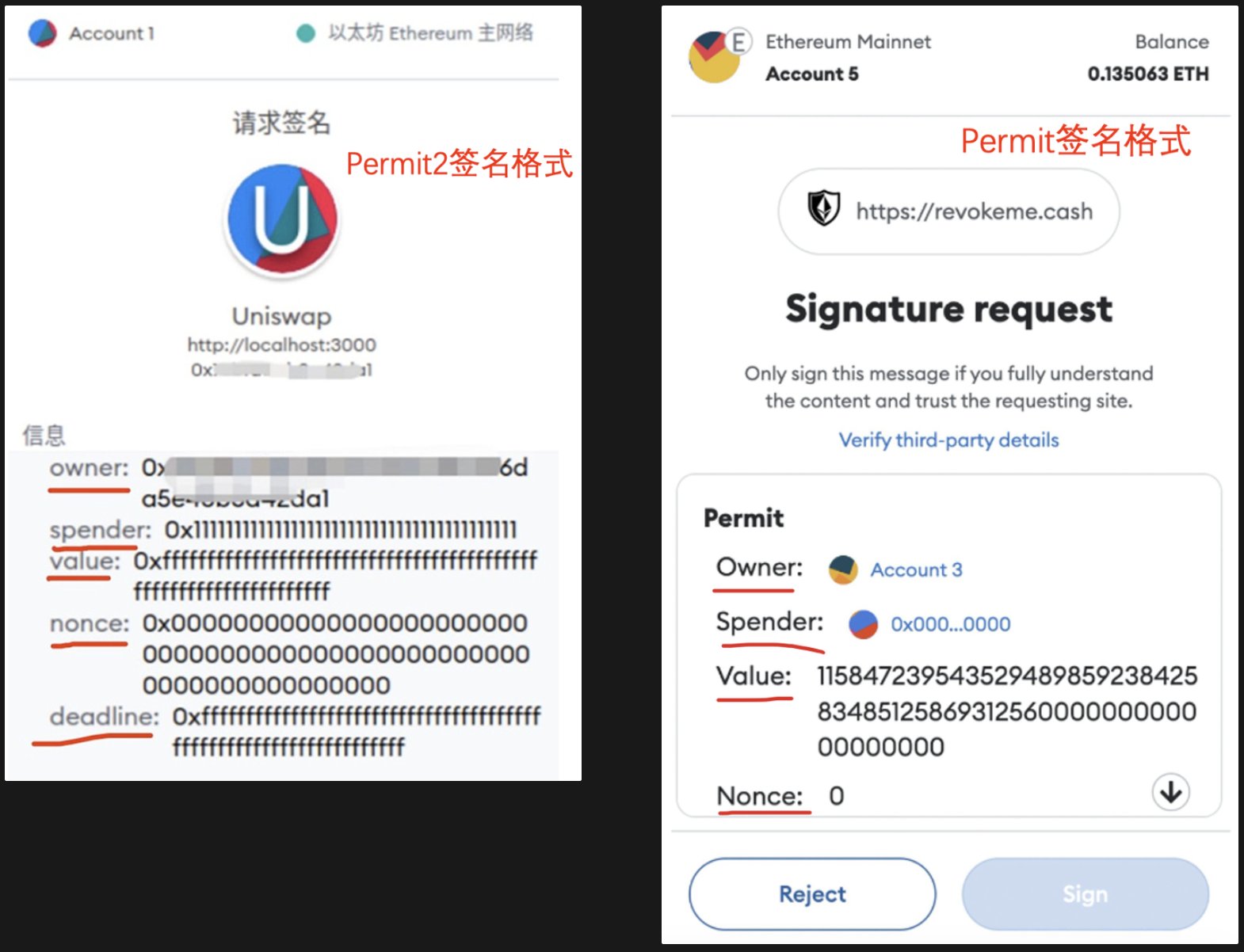
3. Learn to recognize the signature formats of Permit and Permit 2. If you see the following signature formats, you should be alert:
Interactive: Interactive website
Owner: Authorizing party address
Spender: authorized party address
Value: Authorized quantity
Nonce: Random number
Deadline: expiration date