Vitalik’s new article: If a quantum attack comes tomorrow, how will Ethereum solve the problem?
Original author: Vitalik Buterin
Translator: Odaily Azuma
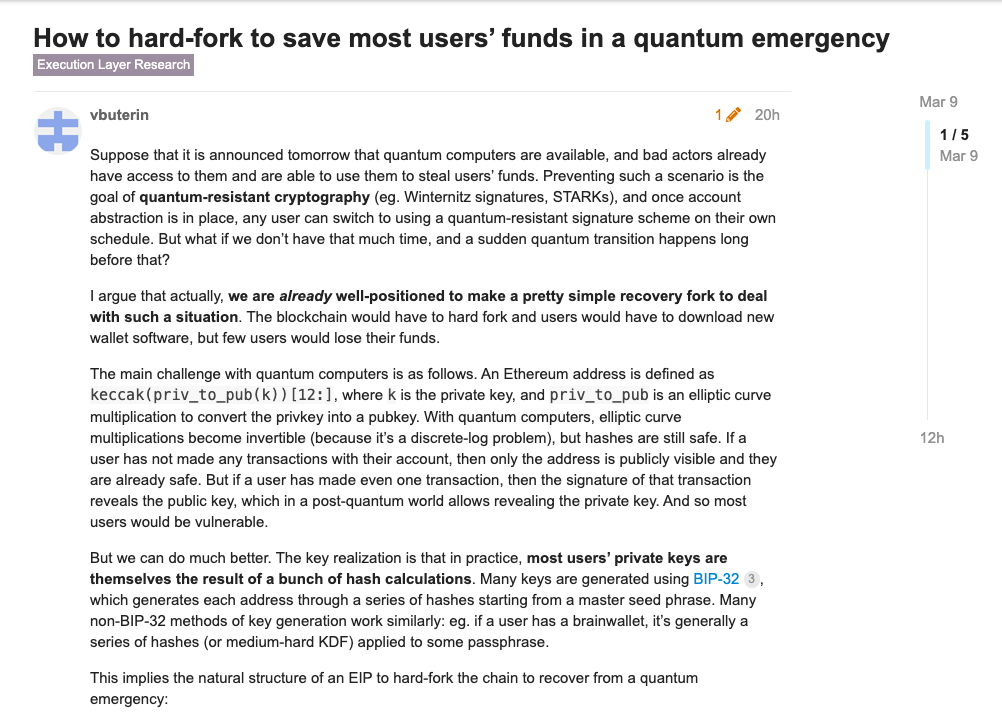
On March 9, Ethereum co-founder Vitalik Buterin published a short article on the Ethereum Research Forum (ethresear.ch) titled How to Rescue User Funds from Sudden Quantum Attacks through Hard Forks.
In the article, Vitalik outlines how Ethereum can minimize the loss of user funds in an emergency if a quantum attack comes tomorrow, and what procedures it should use to switch to a quantum-resistant form and then resume normal operations.
The following is the full text of Vitalik, compiled by Odaily.
What would we do if a quantum computer became available tomorrow and a bad actor somehow gained access to it and wanted to use it to steal user funds?
Quantum-resistant technologies such as Winternitz signatures and STARKs were developed to prevent this from happening. Once the account abstraction is ready, any user can randomly switch to a quantum-resistant signature scheme.But what do we do if we don’t have that much time, and if a quantum attack arrives more suddenly than everyone thinks?
I think,In fact, we currently have sufficient conditions to solve this problem through a relatively simple recovery fork.With this solution, the Ethereum network will have to undergo a hard fork and users will have to download new wallet software, but only a small number of users may lose their funds.
The main threats from quantum attacks are as follows. The Ethereum address is obtained by operating the keccak(priv_to_pub(k))[12:] function, where k corresponds to the private key, and priv_to_pub corresponds to an elliptic curve multiplication, which is used to convert the private key into a public key.
When quantum computing is realized, the above elliptic curve multiplication will become reversible (because this is actually the solution to the discrete logarithm problem), but the hash operation is still safe. If the user has not made any transactions, then only the address information is disclosed, in which case they will still be safe; but as long as the user has made even one transaction, the transaction signature will expose the public key, which is impossible in quantum computers. There is the possibility of exposing the private key. So in this case, most users will be at risk.
But we actually have ways to mitigate this threat. The key point is that in practice, most users private keys are generated through a series of hash operations. For example, many private keys are generated using the BIP-32 specification, which is generated through a series of hash operations based on a set of mnemonic words; many non-BIP-32 private key generation methods are almost similar, for example, if the user uses It is a brain wallet, which is usually generated by a series of hash operations (or a moderately difficult key derivation function) of a password.
This means that a solution to a sudden quantum attack via a restorative fork would take the following steps:
First, roll back all blocks after the large-scale attack;
Second, disable the traditional transaction mode based on EOA addresses;
Third, (if it is not already implemented by then) add a new transaction type to allow transactions through smart contract wallets (such as parts of RIP-7560);
Fourth, add a new transaction type or operation code, through which users can provide STARK proof. If the proof is passed, the code of the users address will be switched to a new verified code, and then the user can use the new code address as a smart contract wallet. .
Fifth, for the purpose of saving Gas and due to the large amount of data required for STARK proofs, we will support batch STARK proofs to conduct multiple above-mentioned types of STARK proofs at the same time.
In principle, tomorrow we could begin development on the infrastructure needed to implement this restorative fork, allowing the Ethereum ecosystem to be prepared in the event of a sudden quantum attack.



