SharkTeam: OKX DEX attack event analysis and on-chain asset tracking

SharkTeam conducted a technical analysis of this incident immediately and summarized the security precautions. We hope that subsequent projects can learn from this and jointly build a security defense line for the blockchain industry.
1. Analysis of attack events
OKX: Dex Aggregator Contract: 0x 70 cbb 871 e 8 f 30 fc 8 ce 23609 e 9 e 0 ea 87 b 6 b 222 f 58
UpgradeableProxy contract: 0x55b35bf627944396f9950dd6bddadb5218110c76
Proxy Admin Owner: 0xc82Ea2afE1Fd1D61C4A12f5CeB3D7000f564F5C6
Proxy Admin contract: 0x3c18F8554362c3F07Dc5476C3bBeB9Fdd6F6a500
Attack initiator address: 0xFacf375Af906f55453537ca31fFA99053A010239
Fund flow address 1: 0x1f14e38666cdd8e8975f9acc09e24e9a28fbc42d
Fund flow address 2: 0x0519eFACB73A1f10b8198871E58D68864e78B8A5
Malicious ProxyMain Contract 1: 0x5c4794d9f34fb74903cfafb3cff6e4054b90c167
Malicious ProxyMain Contract 2: 0xF36C407F3C467e9364Ac1b2486aA199751BA177D
Malicious Proxy contract creator: 0x5A58D1a81c73Dc5f1d56bA41e413Ee5288c65d7F
One of the exploit transactions: 0x570cf199a84ab93b33e968849c346eb2b761db24b737d44536d1bcb010bca69d
Attack process:
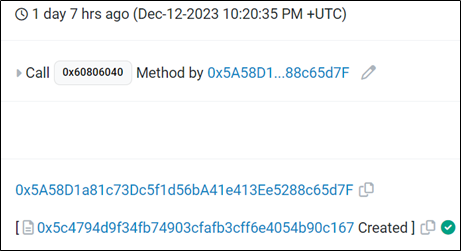
1. At 22:20:35 on December 12, 2023, EOA (0x 5 A 58 D 1 a 8) created the ProxyMain contract (0x 5 c 4794 d 9);
2. At 22:23:47 on December 12, 2023, Proxy Admin Owner (0xc82Ea2af) upgraded the DEXProxy contract to a new execution contract (0x5c4794d9) through Proxy Admin (0x3c18F855);
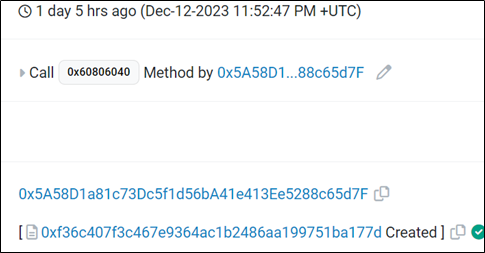
3. At 23:52:47 on December 12, 2023, EOA (0x5A58D1a8) created the ProxyMain contract (0xF36C407F);
4. At 23:53:59 on December 12, 2023, Proxy Admin Owner (0xc82Ea2af) upgraded the DEXProxy contract to a new execution contract (0xF36C407F) through Proxy Admin (0x3c18F855);
5. The purpose of these two contract upgrades is the same. The function of the new contract is to call the claimTokens function of the TokenApprove contract to complete the transfer.
2. Analysis of attack principles
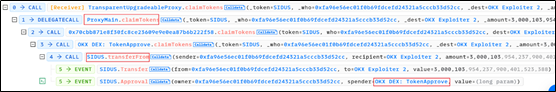
1. When executing the contract ProxyMain, first restrict the caller of the contract to the attackers address (0xFacf375A), and then execute the claimTokens function of the Dex Aggregator contract;
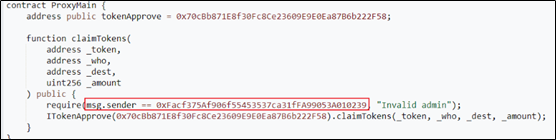
2. In the claimTokens function of the Dex Aggregator contract, since the contract has not yet been open sourced on Etherscan, we obtained its source code through decompilation. As you can see from the code snippet, the claimTokens function verifies whether the agent is trustworthy. Once verified, it will call the OKX DEX: TokenApprove function;
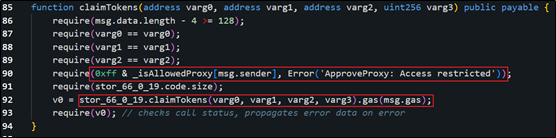
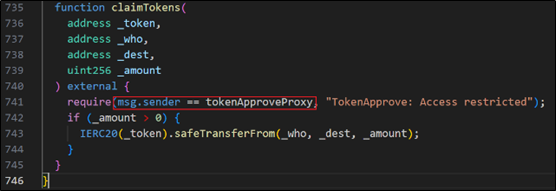
3. In the OKX DEX: TokenApprove function, normally detect whether the caller is a trusted Proxy. The same as the previous trusted Proxy verification, as long as it is a trusted Proxy and the user has authorized TokenApprove, the attacker can steal the authorized users funds.
3. Asset tracking on the chain
Attacks and asset transfers mainly focus on the following 3 addresses:
Attack address: 0xFacf375Af906f55453537ca31fFA99053A010239 (OKX Exploiter);
Payment address: 0x1F14E38666cDd8e8975f9acC09e24E9a28fbC42d (OKX Exploiter 2);
Payment address: 0x0519eFACB73A1f10b8198871E58D68864e78B8A5 (OKX Exploiter 3).
In this attack, the attack address is only responsible for continuously calling the claimTokens function of the TokenApprove contract to initiate transfers and complete the collection through two payment addresses.
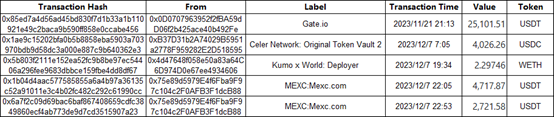
1. Attack address: 0xFacf375Af906f55453537ca31fFA99053A010239 (OKX Exploiter) historical transactions before launching the attack:
Inflow:
Outflow:
Transfer 20419 USDT and 1173 USDT to 0x4187b2daf33764803714D22F3Ce44e8c9170A0f3 respectively, and transfer to 0x7A through the intermediate address 0x4A0cF014849702C0c3c46C2df90F0CAd1E504328, Railgun:Relay and multiple intermediate addresses. 20527ba5a749b3b054a821950Bfcc2C01b959f, this address has a high frequency of transfers worth more than a thousand, and then transfers 300,000 USDT each to 0x6b8DEfc76faA33EC11006CEa5176B1cec2078DfE, followed by multiple addresses with OKX labels, eg
0x3D55CCb2a943d88D39dd2E62DAf767C69fD0179F(OKX 23)
0x68841a1806fF291314946EebD0cdA8b348E73d6D(OKX 26)
0xBDa23B750dD04F792ad365B5F2a6F1d8593796f2(OKX 21)
0x276cdBa3a39aBF9cEdBa0F1948312c0681E6D5Fd(OKX 22)
....
In addition, this address also transfers some USDT through Railgun:Relay and exchanges coins through Uniswap.
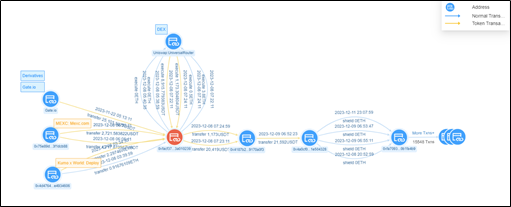
2. Payment address 1: 0x1F14E38666cDd8e8975f9acC09e24E9a28fbC42d (OKX Exploiter 2):
Inflow:
Outflow:
Via 4 addresses:
0xBbEa72B68138B9a1c3fec2f563E323d025510A4c
0x141F12aB25Fcd1c470a2ede34ad4ec49718B5209
0xFD681A9aA555391Ef772C53144db8404AEC76030
0x17865c33e40814d691663bC292b2F77000f94c34
Spread the funds, then use the address labeled Railgun:Relay Railgun: Treasury to transfer, and finally transfer 410204.0 USDT to the BNB Smart Chain through the address labeled Stargate.
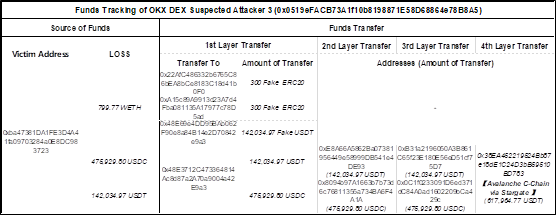
3. Payment address 2: 0x0519eFACB73A1f10b8198871E58D68864e78B8A5 (OKX Exploiter 3)
via intermediate address 0x48E3712C473364814Ac8d87a2A70a9004a42E9a3
Transfer 620,000 USDT to
0xE8A66A5862Ba07381956449e58999DB541e4DE93
and 0x8094b97A1663b7b73d6c76811355a734BA6F4A1A,
Then these two addresses were transferred to two new addresses respectively:
0xB31a2196050A3B861C65f23E180E56eD51cf75D7
and 0x0C1f0233091D6ed371dC84A0ad1602209bCa429c,
Finally, 617964.77 was transferred to Avalanche C-Chain through the address labeled Stargate.
The hacker may have opened accounts and conducted transactions on multiple exchanges such as OKX, Gate.io, and MEXC, and can conduct targeted KYC evidence collection. Moreover, the project contract deployment address of Kumo x World also has direct transfer transactions with the hackers address.
4. Safety suggestions
The root cause of this attack was the leakage of the private key of the Proxy Admin Owner (0x c 82 Ea 2 af), which led to the upgrade of the malicious Proxy deployed by the attacker. Due to the upgrade of the new malicious execution contract, this contract is listed as a trusted proxy. TokenApprove detects that the malicious execution of the contract is trustworthy, so the attacker can steal funds that the user has authorized too much to TokenApprove. Therefore, please be sure to keep the private keys of important account addresses.
About Us
SharkTeams vision is to secure the Web3 world. The team consists of experienced security professionals and senior researchers from around the world, who are proficient in the underlying theory of blockchain and smart contracts. It provides services including on-chain big data analysis, on-chain risk warning, smart contract audit, crypto asset recovery and other services, and has built an on-chain big data analysis and risk warning platform ChainAegis. The platform supports unlimited levels of in-depth graph analysis and can effectively fight against Advanced Persistent Threat (APT) in the Web3 world. It has established long-term cooperative relationships with key players in various fields of the Web3 ecosystem, such as Polkadot, Moonbeam, polygon, Sui, OKX, imToken, ChainIDE, etc.
Official website: https://www.sharkteam.org
Twitter:https://twitter.com/sharkteamorg
Discord:https://discord.gg/jGH9xXCjDZ
Telegram:https://t.me/sharkteamorg