SharkTeam: Analysis of the principles of KyberSwap attack incident
On November 23, 2023, due to Tick manipulation and liquidity double counting, KyberSwap was hacked on multiple networks such as Ethereum and Arbitrum, and the attackers have made approximately $48 million in profits.
SharkTeam conducted a technical analysis of this incident immediately and summarized the security precautions. We hope that subsequent projects can learn from this and jointly build a security defense line for the blockchain industry.
1. Attack transaction analysis
This attack event is relatively complex, and the attack implementation is also relatively clever. We select one of the attack transactions for detailed analysis and explanation.
Attack transaction:
0x09a3a12d58b0bb80e33e3fb8e282728551dc430c65d1e520fe0009ec519d75e8
Attacker address:
0x50275E0B7261559cE1644014d4b78D4AA63BE836
Attacker contract:
0xaF2Acf3D4ab78e4c702256D214a3189A874CDC13
In this transaction, the attacker performed a series of operations against 3 different liquidity pools to drain the funds in the pools. We selected a pool for attack flow analysis that exists independently of each other.
Attack process:
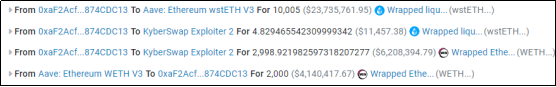
1. The attacker first borrowed 10,000 wstETH through flash loan, then added approximately 2,998 wstETH into the pool, and swapped out approximately 2,842 WETH;
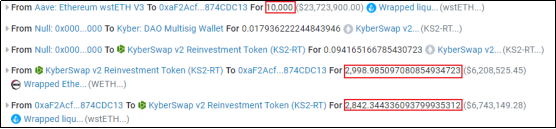
2. At this time, the corresponding Tick status in the pool is -110, 910, and the price of wstETH changes from 1.05 ETH to 0.000015257. At this time, the liquidity of the pool is 0, paving the way for the subsequent creation of false liquidity;
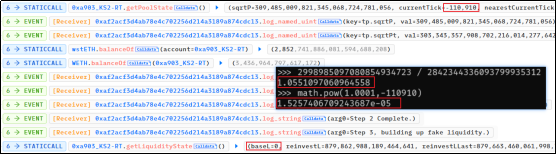
3. The attacker added 3.4 wstETH liquidity in the [0.000014659, 0.000015260] range, and removed 0.56 wstETH;
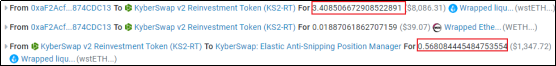
4. Next, the attacker performs two swaps, namely WETH->wstETH and wstETH->WETH. After the first swap, the price was pushed to 0.000014657, which is slightly lower than 0.000014659. After the second swap, the price is raised to 0.000016368;
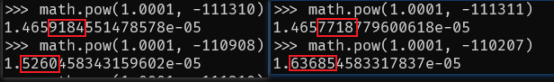
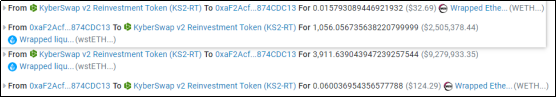
5. At the beginning, there was about 3 wstETH liquidity in the pool (mint 3.4 wstETH - burn 0.56 wstETH). Now there are about (1,056 + 3,911) coins in the pool, obviously more;
6. After the attack returns the flash loan, the funds are transferred from the attack contract.
2. Vulnerability Cause Analysis
The root cause of this attack: In the computeSwapStep function, there is a loss of accuracy when calculating Tick. Since the Tick can be manipulated, the _updateLiquidityAndCrossTick function is successfully bypassed, allowing the liquidity to be increased repeatedly.
1. In the first swap, the attacker used the calcReachAmount function to calculate the amount of wstETH, and finally calculated 1, 056.056735638220800000;
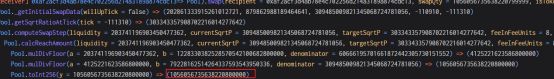
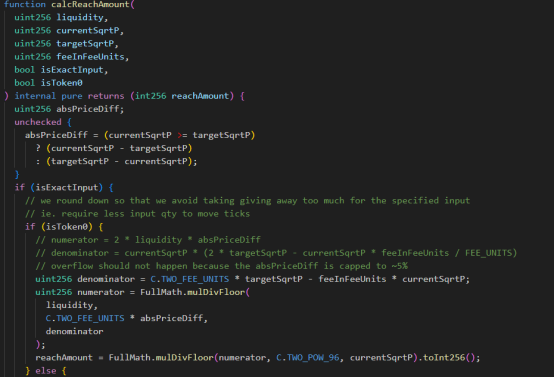
2. After calling the estimateIncrementalLiquidity and calcFinalPrice functions, the quantity passed in is 1, 056.056735638220799999. After round up and round down processing, the Tick at this time is -111311, and the lower limit Tick is -111310. Therefore, by using nextTick = currentTick+ 1 and using != to judge the two sqrtP parameters, the _updateLiquidityAndCrossTick function is successfully bypassed and liquidity updates are avoided;
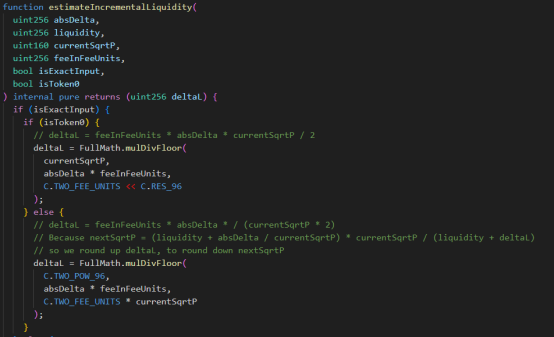
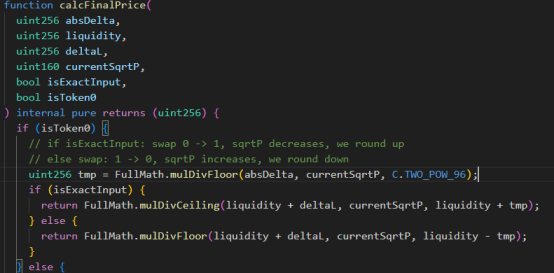
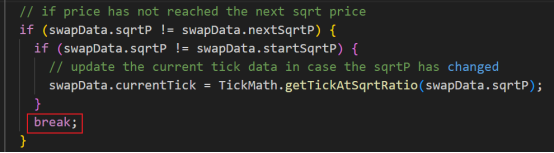
3. During the second swap, _updateLiquidityAndCrossTick was called to increase liquidity. Due to the loss of accuracy in the quantity calculation during the first swap, the liquidity was not updated and removed, resulting in a double situation in the second liquidity calculation.
3. Safety Suggestions
In response to this attack, developers should take the following security measures in daily development:
1. Pay attention to correctly calculating the invariants and mathematical logic in the business to avoid loss of accuracy.
2. Before the project is released, it is necessary to cooperate with a third-party professional audit team to conduct a contract audit.
About Us
SharkTeams vision is to secure the Web3 world. The team consists of experienced security professionals and senior researchers from around the world, who are proficient in the underlying theory of blockchain and smart contracts. It provides services including on-chain big data analysis, on-chain risk warning, smart contract audit, crypto asset recovery and other services, and has built an on-chain big data analysis and risk warning platform ChainAegis. The platform supports unlimited levels of in-depth graph analysis and can effectively fight against Advanced Persistent Threat (APT) risks in the Web3 world. It has established long-term cooperative relationships with key players in various fields of the Web3 ecosystem, such as Polkadot, Moonbeam, polygon, Sui, OKX, imToken, ChainIDE, etc.
Official website: https://www.sharkteam.org
Twitter:https://twitter.com/sharkteamorg
Discord:https://discord.gg/jGH9xXCjDZ
Telegram:https://t.me/sharkteamorg



