YBB Capital: Looking ahead to the potential track, decentralized computing power market (Part 2)
Original author: YBB Capital Researcher Zeke

Preface
exist《Preview of the potential track: decentralized computing power market (Part 1)》We have learned about the importance of computing power under the expectation of AI, and also deeply discussed the two dilemmas that exist at the current stage in building a decentralized AGI computing power market. This article will start from the basic concepts of zero-knowledge proof, proceed from the shallower to the deeper, and conduct multi-dimensional thinking on more possibilities of the rising track of the decentralized computing power market. (The Bitcoin computing power market was also mentioned in the previous article, but in view of the recent explosive growth of the Bitcoin ecosystem, this part will be described in our future Bitcoin ecology-related articles.)
Zero-knowledge proof overview
In the mid-1980s, three cryptographers at MIT (Shafi Goldwasser, Silvio Micali, and Charles Rackoff) jointly published a paper called The Knowledge Complexity of Interactive Proof Systems. The article describes an innovative cryptographic technique that can verify the authenticity of information without clarifying it. The author calls it zero-knowledge proof and provides a specific definition and framework for this concept.
In the following decades, the zero-knowledge proof technology based on this paper was gradually developed and improved in many fields. Today, zero-knowledge proof has become an all-encompassing term, representing many modern or advanced “Cryptozoology—especially cryptography as it relates to the future of blockchain.
definition
Zero-Knowledge Proof (ZKP for short, used as appropriate below) means that the prover (Prover) can prove the correctness of a certain statement to the verifier (Verifier) without providing any specific information about the statement itself. The three fundamental properties of this approach include completeness, reliability, and zero-knowledge. Completeness ensures that true statements are provable, reliability ensures that false statements cannot be proven, and zero-knowledge means that the verifier cannot obtain any information other than the truth of the statement.
Types of zero-knowledge proofs
Depending on how the prover and verifier communicate, there are also two different types of zero-knowledge proofs, interactive and non-interactive. In interaction, there is a series of interactions between the prover and the verifier. These interactions are part of the attestation process, where the prover proves the truth of its statement by responding to a series of queries or challenges from the verifier. This process typically involves multiple rounds of communication, each in which the verifier poses a question or challenge and the prover responds to prove the correctness of its statement. Non-interactive does not require multiple rounds of interaction. In this case, the prover creates a single, independently verifiable proof and sends it to the verifier. The verifier can independently verify the authenticity of this proof without further communication with the prover.
Interactive and non-interactive popular explanations
1. Interactive: The story of Alibaba and the Forty Thieves is a typical example often mentioned in explaining interactive zero-knowledge proofs. There are many versions. The story below is a simplified version adapted by me.
Ali Baba knew the spell to open the cave where the treasure was hidden, but he was caught by the Forty Thieves and forced to speak the spell. If Alibaba utters the spell, he will be killed because he is of no use. If Alibaba persists, the robbers will not believe that he really knows the spell and will kill him. But Alibaba thought of a good idea. Now the cave has two entrances, A and B, both leading to the center of the cave, but there is a password door in the center. Only people who know the spell can walk from one side to the other. To prove that he knows the secret to opening the cave without revealing the secret, Alibaba enters the cave and chooses one of the entrances, A or B, while the Forty Thieves stand outside unable to see his choice. The forty thieves then randomly call out A or B, asking Alibaba to come out from their designated entrance. If Alibaba really knew the spell, he could use the code to pass through the door in the center and emerge from the designated entrance. This process is repeated several times, and each time Alibaba is able to successfully exit through the entrance designated by the Forty Thieves, thus proving that he does know the password without revealing the secret.

2. Non-interactive: Here is a simple example of a non-interactive zero-knowledge proof in life, imagine that you and a friend both have a Finding Wally book. You claim to know where Wally is on a certain page, but your friend is skeptical. If you want to prove to a friend that you know where Wally is in the picture without revealing the exact location, you can use a piece of opaque paper large enough to cover the entire picture and expose Wally through a small hole in the paper (a single , an independently verifiable proof), so that you can prove that you actually know Wallys location, but your friend still wont know Wallys exact coordinates in the entire picture.

Technical implementation in blockchain
Zero-knowledge proofs are currently implemented in a variety of blockchains, the most well-known of which are zk-STARK (Zero-Knowledge Scalable Transparent Argument of Knowledge) and zk-SNARK (Zero-Knowledge Succinct Non-Interactive Argument of Knowledge) , as the “Non-Interactive” in their names indicates, both are non-interactive zero-knowledge proofs.
zk-SNARK belongs to a type of universal zero-knowledge proof scheme that is widely used (it should be noted here that zk-SNARK belongs to a genre, not a single technology), by converting any calculation process into the form of several gate circuits, and A series of mathematical properties of polynomials are used to convert gate circuits into polynomials, and then compressed to generate very small non-interactive proofs, which can be used in various complex business scenarios. The launch of zk-SNARK requires a trusted setup, where multiple parties each generate a partial key to launch the network and then destroy the key. If the secrets of the keys used to create the trust setup are not destroyed, these secrets could be exploited to forge transactions through false verifications.
zk-STARK is a technical evolution of zk-SNARK, which solves the weakness of SNARKs reliance on trusted settings and can complete blockchain verification without relying on any trust settings, thereby reducing the complexity of launching the network and eliminating any collusion risk. However, zk-STARK also has major problems with generating proofs, and is at a disadvantage in terms of storage, on-chain verification, and generation time. If you have experienced the early version of StarkNet (Layer 2 using zk-STARK), you should obviously feel that the speed and gas cost are much worse than other Layer 2 experiences. Therefore, the zk-SNARK scheme is currently used more. In addition, there are slightly niche solutions such as PLONK and Bulletproofs. Each method has its own advantages and disadvantages in terms of proof size, prover time and verification time. A completely ideal zero-knowledge proof is very difficult to achieve, and several mainstream algorithms usually balance different dimensions.
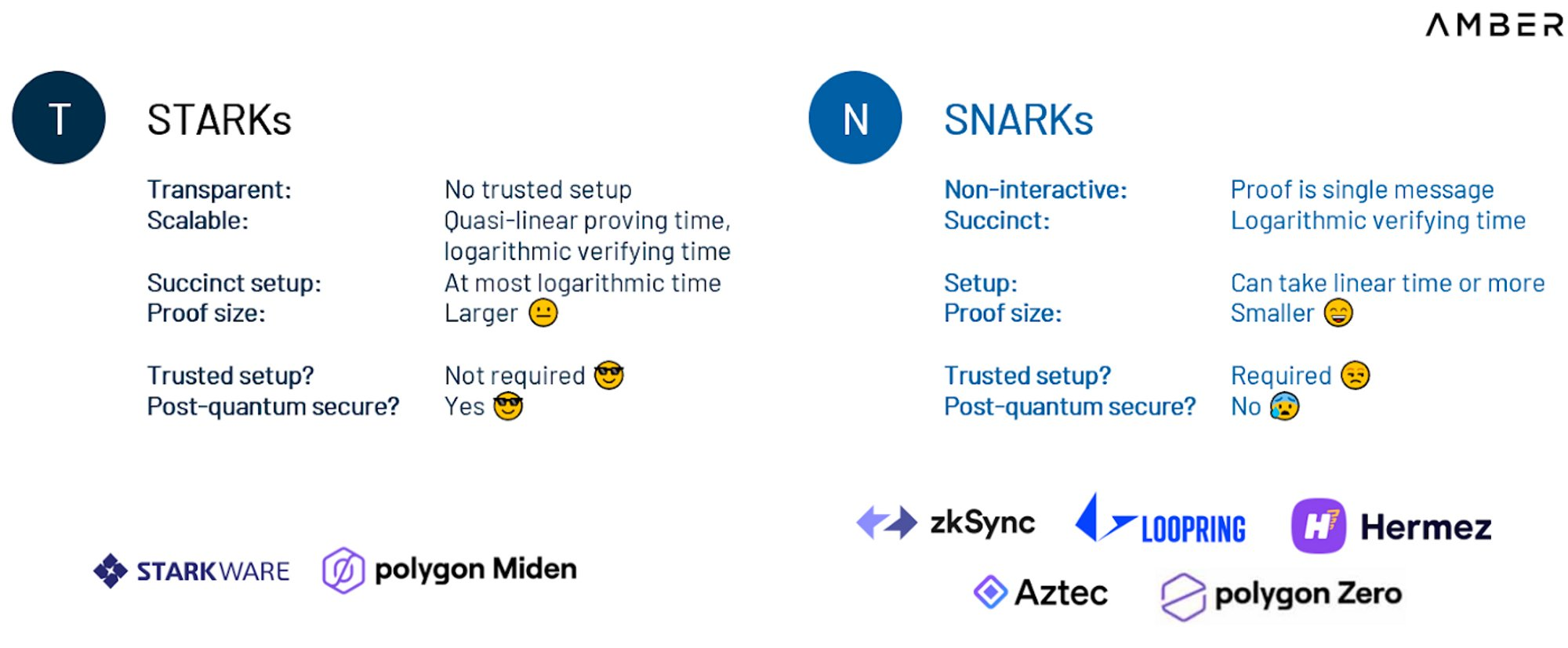 The development of ZK usually requires the use of two key components.
The development of ZK usually requires the use of two key components.
ZK-friendly expression calculation method:This is a domain-specific language (DSL) or low-level library. Low-level libraries such as Arkworks provide the necessary tools and primitives, allowing developers to manually rewrite code directly in lower-level languages. DSLs such as Cairo or Circom are programming languages tailored for ZK applications. The latter can be compiled into the primitives required to generate proofs. More complex operations result in longer proof generation times, while some operations (such as SHA or the bit operations used in Keccak) may not be suitable for ZK, resulting in long proof generation times.
Proof system:The proof system is the core of the ZK application, and it implements two basic functions: Prove (proof) and Verify (verification). The Prove function allows the generation of a proof (requiring a lot of mathematical calculations to generate, and the more complex the proof, the slower the generation) that shows that a certain statement is correct without revealing the details of the proof. The Verify function is used to verify the correctness of the proof (the more complex and larger the proof, the higher the performance and the shorter the time required for verification). Different proof systems, such as Groth 16, GM 17, PLONK, Spartan, and STARK, etc., also differ in efficiency, security, and ease of use.
ZKP application map
ZKP cross-chain bridges and interoperability: ZKP can be used to create proofs of validity of cross-chain messaging protocols that can be quickly verified on the target chain. This is similar to how zkRollups are verified on the underlying L1. However, for cross-chain messaging, the complexity is higher because the signature scheme and cryptographic functions that need to be verified may differ between the source and target chains;
ZKP on-chain game engine: Dark Forest shows how ZKP can implement on-chain games with incomplete information. This is crucial for designing more interactive games, where the players actions remain private until they decide to reveal them. As on-chain games mature, ZKP will become part of the game execution engine. This will be huge for startups that successfully integrate privacy features into high-throughput on-chain game engines;
Identity Solutions: ZKP can open up multiple opportunities in the identity space. They can be used for reputation proof or to connect Web2 and Web3 identities. Currently, our Web2 and Web3 identities are separate. Projects like Clique connect these identities through the use of oracles. ZKP can take this approach a step further by enabling Web2 and Web3 identities to be linked anonymously. This enables use cases like anonymous DAO membership, provided they can demonstrate domain-specific expertise using Web2 or Web3 data. Another use case is uncollateralized Web3 lending based on the borrower’s Web2 social status (e.g. number of Twitter followers);
ZKP for regulatory compliance: Web3 enables anonymous online accounts to actively participate in the financial system. In this sense, Web3 enables tremendous financial freedom and inclusivity. As Web3 regulation increases, ZKP can be used to achieve compliance without breaking anonymity. ZKP can be used to prove that a user is not a citizen or resident of a sanctioned country. ZKP can also be used to prove accredited investor status or any other KYC/AML requirements;
Homegrown Web3 Private Debt Financing: TradeFi Debt financing is typically used to support growing startups to accelerate their growth or launch new lines of business without the need for additional venture capital. The rise of Web3 DAOs and anonymous companies creates opportunities for Web3 native debt financing. For example, using ZKPs, DAOs or anonymous companies can obtain unsecured loans and competitive interest rates based on proof of their growth metrics without having to disclose the borrower’s information to the lender;
Privacy DeFi: Financial institutions often keep their transaction history and risk exposure private. However, when using decentralized finance (DeFi) protocols on-chain, meeting this demand becomes challenging due to the continuous advancement of on-chain analytics technology. One possible solution is to develop privacy-focused DeFi products to protect the privacy of protocol participants. One of the protocols trying to achieve this is Penumbra’s zkSwap. Additionally, Aztec’s zk.money offers some private DeFi money-making opportunities by obscuring user participation in transparent DeFi protocols. Typically, protocols that are able to successfully implement efficient and privacy-focused DeFi products can generate significant transaction volume and revenue from institutional players;
ZKP for Web3 advertising: Web3 promotes users to own their own data rights, such as browsing history, private wallet activities, etc. Web3 also enables the monetization of this data to benefit users. Since data monetization can be at odds with privacy, ZKP can play an important role in controlling what personal data can be disclosed to advertisers and data aggregators;
Sharing and Monetization of Private Data: Much of our private data can have significant impacts if shared with the right entities. Personal health data can be crowdsourced to help researchers develop new medicines. Private financial records can be shared with regulators and watchdogs to identify and punish corrupt practices. ZKP enables the private sharing and monetization of such data;
Governance: With the popularity of DAOs (Decentralized Autonomous Organizations) and on-chain governance, Web3 is moving towards direct participatory democracy. A major flaw with current governance models is the non-private nature of participation. ZKP can be the basis for solving this problem. Governance participants can vote without revealing how they vote. Additionally, ZKP can limit the visibility of governance proposals to DAO members, allowing DAOs to build a competitive advantage.
zkRollup: Scaling is the most important use case of ZKP in the blockchain. zkRollup technology aggregates multiple transactions into a single transaction. These transactions are processed and calculated off-chain, that is, outside of the blockchain’s main chain. For these aggregated transactions, zkRollup uses ZKP to generate a proof that can confirm the validity of these transactions without revealing the specific content of the transactions and greatly compresses the size of the data. The generated ZKP is then submitted to the main chain of the blockchain. Nodes on the main chain only need to verify the validity of this certificate and do not need to process each individual transaction. In this way, the burden on the main chain is greatly reduced.
ZKP hardware acceleration
Although the zero-knowledge proof protocol has many advantages, the current problem is that it is easy to verify and difficult to generate. The main bottleneck of most proof system generation is multi-scalar multiplication (MSM) or fast Fourier transform (FFT) and its inverse transform. The composition and advantages and disadvantages of the two are mainly as follows.
Multi-scalar multiplication (MSM):MSM is a key computation in cryptography that involves the multiplication of points and scalars in elliptic curve cryptography. In ZKP, MSM is used to construct complex mathematical relationships about points on an elliptic curve. These calculations often involve a large number of data points and operations and are used to generate and verify key parts of the proof. MSM is particularly important in ZKP because it helps construct proofs that can verify cryptographic claims without exposing private information. MSM can execute on multiple threads, thus supporting parallel processing. However, when dealing with large element vectors, such as 50 million elements, multiplication operations can still be slow and require significant memory resources. Additionally, MSM has scalability challenges and can remain slow even with extensive parallelization.
Fast Fourier Transform (FFT):FFT is an algorithm for efficiently computing polynomial multiplication and solving polynomial interpolation problems. In ZKP, it is often used to optimize the calculation process of polynomials, which is an important step in generating proofs. FFT speeds up calculations by breaking complex polynomial operations into smaller, simpler parts, which is critical for efficiency in the proof generation process. The use of FFT greatly improves the ability of ZKP systems to handle complex polynomials and large-scale data sets. However, FFT operations rely on frequent data exchange, which makes it difficult to significantly improve efficiency through distributed computing or hardware acceleration. Data exchange in FFT operations requires significant bandwidth, especially when large data sets that exceed the hardware memory capacity need to be processed.
Although software optimization is also an important research direction, the most direct and crude way to accelerate proof generation is to stack hardware with high enough computing power to accelerate generation. In many computing hardware (GPU, FPGA, ASIC), Which one is the best choice? Since we have briefly introduced GPU in the previous part, here we mainly understand the design logic, advantages and disadvantages of FPGA and ASIC.
ASIC:ASIC (Application-Specific Integrated Circuit) is an integrated circuit specially designed to meet specific application requirements. Compared to a general-purpose processor or standard integrated circuit, an ASIC is customized to perform a specific task or application and therefore typically exhibits greater efficiency and performance in the application for which it was designed. In the field of Bitcoin mining that we are familiar with, ASICs are very important computing hardware. Their efficient performance and low power consumption make them an ideal choice for Bitcoin mining. However, ASIC also has two obvious shortcomings. Since it is designed for specific applications (for example, Bitcoin’s AISC mining machines are designed around the SHA-256 hash algorithm), without mass adoption, the design and manufacturing costs are high. It will be very high, and the design and verification cycle will be relatively long.
FPGA:FPGA is the abbreviation of Field Programmable Gate Array (Field Programmable Gate Array). It is a reprogrammable device and is used in PAL (Programmable Logic Array), GAL (General Array Logic), CPLD (Complex Programmable Logic Device), etc. A semi-custom circuit developed on the basis of traditional logic circuits and gate arrays. Like ASIC, it is an integrated circuit used for electronic design and implementation of specific functions. It not only solves the shortcomings of past semi-custom circuits, but also overcomes the original The disadvantage of programmable devices is the limited number of gates. Its important features are re-programmable, low power consumption, low latency, and strong computing power. However, the disadvantage of FPGA is that its functions are completely dependent on hardware implementation, it cannot perform operations such as branch conditional jumps, and it can only perform fixed-point operations. In terms of cost, the cost of FPGA is lower than that of ASIC in design, and the manufacturing also requires a reference scale. Of course, the overall cost of both is much higher than that of GPU.
So going back to the discussion of ZKP hardware acceleration, first of all, we must admit that ZKP is still in the early stage of development. There is still little standardization of system parameters (such as FFT width or bit size of elements) or choice of proof system (there are five proof systems mentioned above alone). Let’s compare the performance of three types of computing hardware in this environment:
Changes in the meta of ZK: As we mentioned above, the business logic on the ASIC is write-once. If any ZKP logic changes, you need to start from scratch. FPGAs can re-refresh any number of times within 1 second, meaning they can reuse the same hardware on multiple chains with incompatible proof systems (e.g. cross-chain MEV extraction) and flexibly adapt to the ZK meta Variety. Although GPUs are not as fast and reconfigurable at the hardware level as FPGAs, GPUs provide great flexibility at the software level. GPUs can adapt to different ZKP algorithms and logic changes through software updates. Even though this update may not be as rapid as with an FPGA, it can still be accomplished in a relatively short period of time.
Supply: ASIC design, manufacturing and deployment typically takes 12 to 18 months or more. In contrast, the FPGA supply chain is relatively healthy, with leading vendors such as Xilinx allowing large volumes of retail orders to arrive within 16 weeks from a website (i.e. without any point of contact). Looking at GPUs, GPUs naturally have huge advantages in terms of supply. Since the merger of Ethereum in Shanghai, there are a large number of idle GPU mining machines in the entire network. Subsequent graphics card series developed by Nvidia and AMD can also be supplied in large quantities.
From the above two points, unless the ZK track reaches a consensus and adopts a standardized solution, ASIC will not have any advantages. Judging from the current diversified development of the ZKP solution, GPU and FPGA will be the two main computing hardware we need to discuss next.
Development cycle: Due to the popularity of GPUs and mature development tools such as CUDA (for NVIDIA GPUs) and OpenCL (cross-platform). The development of FPGA usually involves more complex hardware description languages (such as VHDL or Verilog), which requires longer learning and development time;
Power Consumption: FPGAs generally outperform GPUs in terms of energy efficiency. This is mainly due to the ability of FPGAs to be optimized for specific tasks, thereby reducing unnecessary energy consumption. Although the GPU is powerful in processing highly parallelized tasks, it is also accompanied by higher power consumption;
Customizability: FPGAs can be programmed to optimize specific ZKP algorithms and increase efficiency. And for a specific ZKP algorithm, the general-purpose architecture of a GPU may not be as efficient as dedicated hardware;
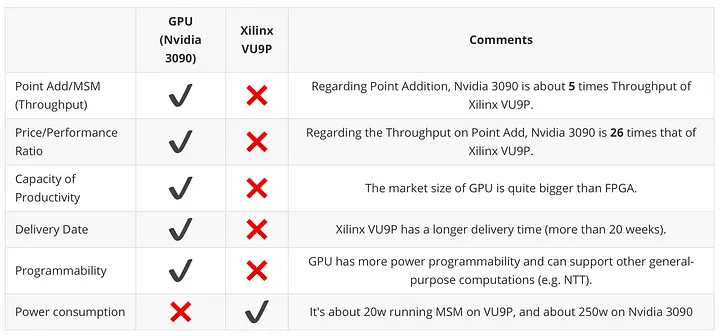
Generation speed: According to Trapdoor-Techs comparison of GPU (taking Nvidia 3090 as an example) and FPGA (Xilinx VU 9 P as an example), the same modular multiplication is used under BLS 12-381 (a specific type of elliptic curve) / Modulo-add algorithm, the generation speed of GPU is 5 times that of FPGA.
To sum up, in the short term, considering the development cycle, parallelism, generation speed, cost, and the large number of idle devices on call throughout the network, GPU is undoubtedly the most advantageous choice at present. The current hardware optimization direction is also focused on GPU, and the time for FPGA to completely take over the game has not yet come. So is it possible to build a ZKP computing power market (my personal conception) similar to PoW mining?
Thoughts on building the ZKP computing power market
In terms of thinking about building a ZKP computing power market, we have already drawn conclusions from the above in terms of computing power hardware. The remaining questions are the following three points: Does ZKP need to be decentralized? Is the market size attractive? If all ZK public chains choose to build their own proof generation market, what is the point of the ZKP computing power market?
The meaning of decentralization:First of all, most zkRollup projects today (such as Starkware and zKsync) rely on centralized servers because only Ethereum expansion is considered. Centralization means that user information is still at risk of being censored, sacrificing the most important permissionless nature of the blockchain to a certain extent. Not to mention the adoption of ZKs privacy protocol, the decentralization generated by ZKP is extremely necessary. The second reason for decentralization is cost, which is similar to the AGI part in the previous article. The cost of cloud services and purchasing hardware is very expensive, and proof generation is usually only suitable for large projects. For small projects in the initial stage, a decentralized proof market can greatly alleviate the problem of financial difficulties in their start-up stage. On the other hand, it also reduces unfair competition caused by financial problems.
Market size:Paradigm predicted last year that the ZK miner/certifier market could grow in the future to be equivalent to the size of the PoW mining market in the past. The fundamental reason is that the buyers and sellers of ZKP computing power are extremely abundant in the ZKP computing power market. For those former Ethereum miners, ZK’s large number of public chain projects and Layer 2 projects are far more attractive than ETH’s forked public chains. However, we also need to consider a situation. Most ZK public chains or Layer 2 are also fully capable of building their own proof generation market. If they want to comply with the decentralized narrative, this step must be in the roadmap (the above Starkware and zkSync will also have their own decentralized solutions in the future), so is there still any significance in building the ZKP computing power market?
Meaning of construction:First of all, ZKP is widely used (we have given examples many times above, and we will use a project as a reference below). The second point is that even if each ZK chain has its own proof generation market, the computing power market still has three functions, allowing sellers to consider selling computing power.
1. Divide the computing power into two parts, one part is used for mining and the other part is used for selling computing power contracts. This approach can help hedge the risk of volatility in the cryptocurrency market. When the market falls, the computing power contract sold provides stable income; while when the market rises, the part mined by oneself can bring additional income;
2. It is a more conservative approach to sell all the computing power and obtain a fixed income. This can reduce the impact of market fluctuations on income and ensure the stability of income;
3. Due to differences in cost structures (such as electricity costs), some miners may receive lower operating costs than the market average. These miners can take advantage of their cost advantage by selling computing power contracts at market prices and retaining the price difference due to lower electricity costs to achieve arbitrage.
Proof Market
Proof Market is a decentralized ZKP computing power market built by =nil; (Ethereum RD company) (as far as I know, it is also the only computing power market built around ZKP generation). It is essentially an untrusted one. Any data accessibility protocol that enables layer 1 and layer 2 blockchains and protocols to generate zero-knowledge proofs on demand for seamless data sharing without relying on centralized intermediaries. Although Proof Market is not a market built around personal GPUs as I imagined (Proof Market is built around professional hardware vendors, ZKP’s GPU mining can also refer to Roller Network or Aleo in the Scroll architecture), but what about the ZKP computing power market? It is still of great reference significance on the issue of construction and widespread application. The workflow of Proof Market is as follows:
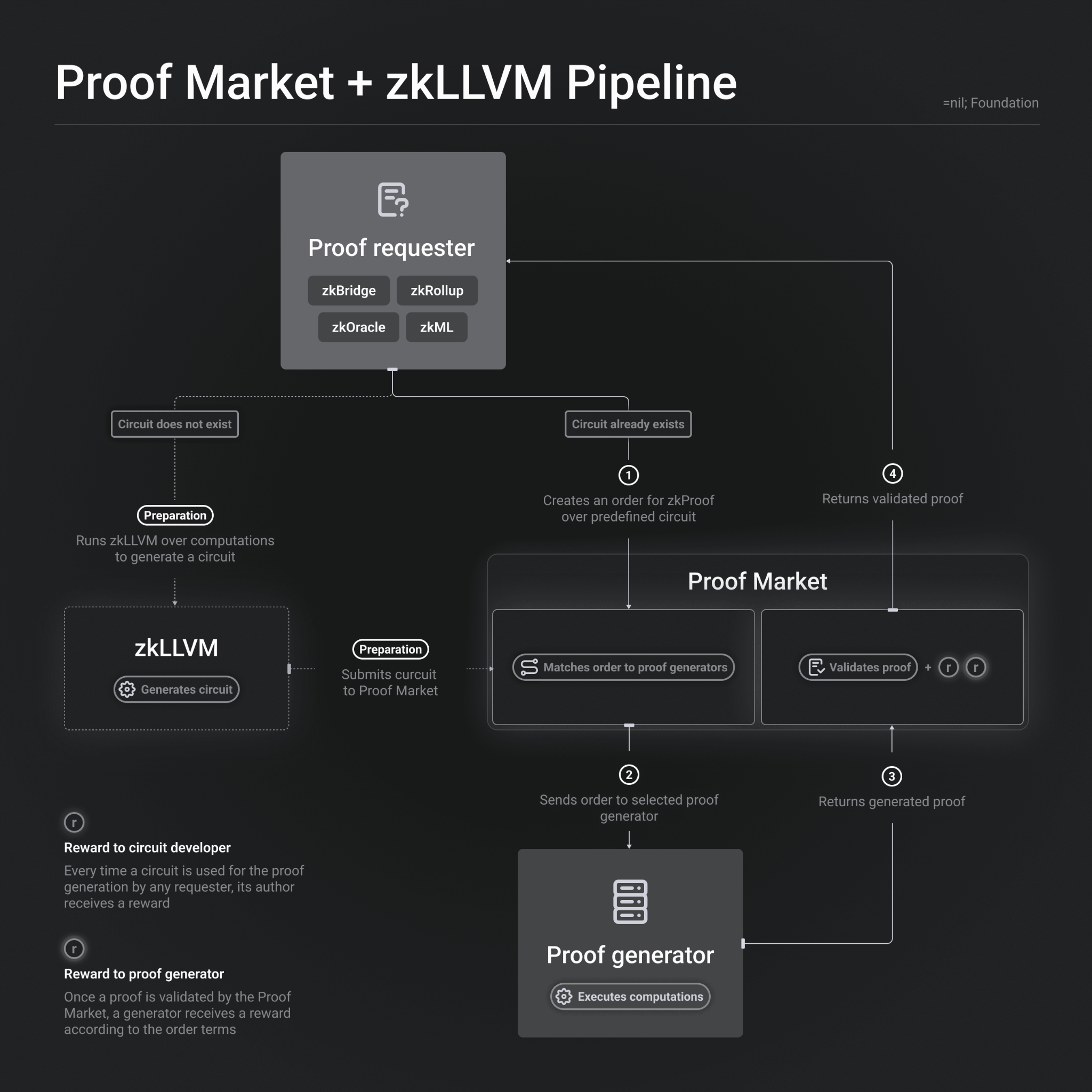
Proof requester:
The entity requesting the certification can be an application such as zkBridge, zkRollup, zkOracle or zkML.
If the circuit does not exist, a preparation phase is required to generate a new circuit by running zkLLVM.
If the circuit already exists, create a zkProof request for the predefined circuit.
zkLLVM:
This component is responsible for generating circuits, which are programs that encode computational tasks.
In the preparation phase, zkLLVM performs preprocessing on calculations to generate circuits and submit them to the Proof Market.
Proof Market:
is a central marketplace that matches orders from proof requesters with proof generators.
Verify the validity of the proof and provide rewards after the proof is verified.
Proof generator:
Perform calculations to generate the required zero-knowledge proofs.
Receive orders from Proof Market and return the generated proof.
bonus system:
Circuit developer rewards: Whenever a proof requester uses a circuit to generate a proof, the author of the circuit is rewarded.
Proof Generator Rewards: Once a proof is verified on Proof Market, generators receive rewards according to the terms of the order.
Throughout the process, the request, generation, verification and reward issuance of proofs all revolve around the Proof Market. This process aims to create a decentralized market where the generation and verification of ZKP is automated and participants can receive corresponding rewards based on their contributions.
Application scenarios
Since its beta launch in January 2023, Proof Market’s main use cases have been protocols operating outside Ethereum’s first layer (L1): such as zkRollup, zkBridge connecting to Ethereum, and public chains using zkP.
With the integration of Ethereum endpoint (referring to a gateway interface that allows other systems or services to connect and integrate), Proof Market will be suitable for more applications, especially those that need to directly request proof from EVM applications. Provide a smoother user experience or applications that need to store data on the chain to work together.
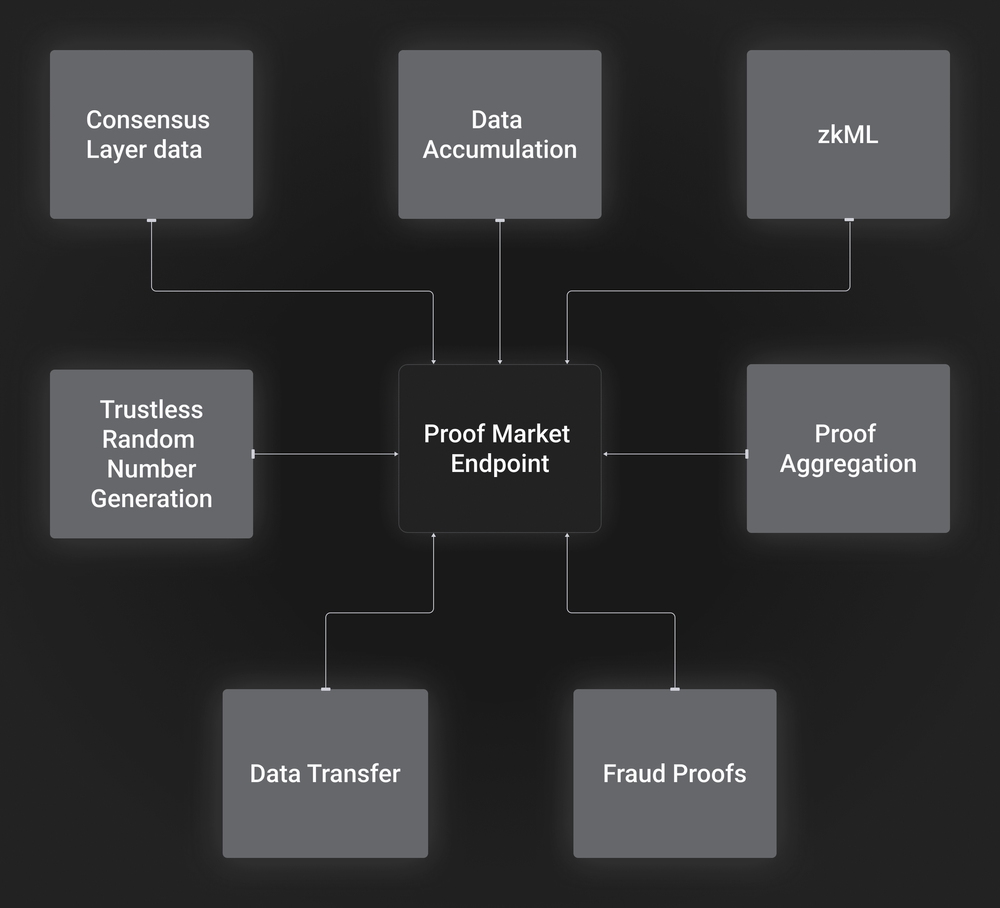
Here are some potential application scenarios:
Machine Learning (ML): Inference requests can be made to zkML applications on-chain. Applications such as fraud detection, predictive analytics, identity verification, etc. can be deployed on Ethereum.
Ethereum data processing (zkOracles): Many applications require Ethereum’s historical or processed data. Using zkOracles, users can obtain execution layer data from the consensus layer.
Data transfer (zkBridges): Users can directly request data transfer and pay proof fees, eliminating the need for a bridge operator to act as an intermediary between the user and the market.
Fraud Proof: Some fraud proofs can be easily verified on-chain, while others cannot. Fishermen (network participants who focus on validating the main protocol and looking for possible fraud) can focus on validating the main protocol and point to the required proofs provided by Proof Market.
Data updates and accumulation: Applications can store the latest updates directly at the first level and later accumulate them into a Merkle tree with proof of correct root updates.
Random number generation: Applications can order random numbers generated via a trustless hash-based VDF.
Proof aggregation: If applications send their proofs independently (without verification), the verification cost of the proof can be reduced by aggregating them into a single proof and then verifying it all at once.
Practical combat session
Lido, the LSD project we are familiar with recently, is also building a solution to enhance the security and credibility of the Lido Accounting Oracle contract through Proof Market. The Lido Accounting Oracle relies on an Oracle committee of trusted third parties and a quorum mechanism to maintain its state, which creates potential attack vectors. The solution process of Proof Market is as follows:
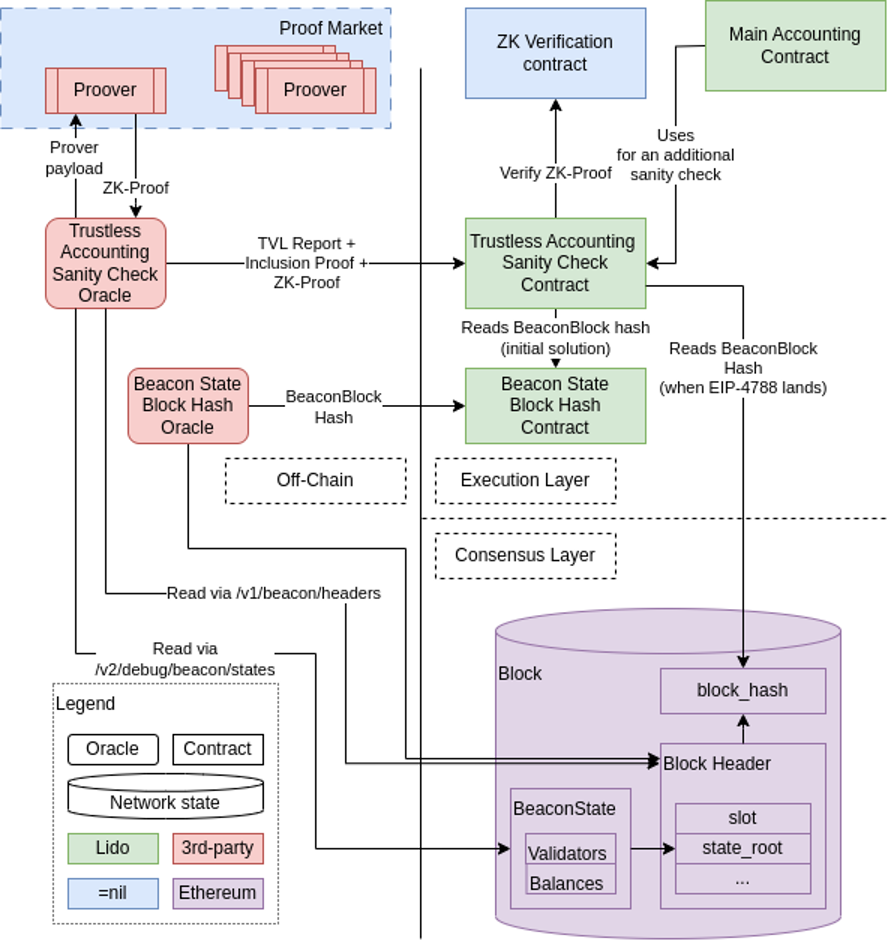 problem definition
problem definition
Lido Accounting Oracle contract: handles complex reporting, including consensus layer (Consensus Layer) data (such as Total Value Locked (TVL), number of validators, etc.).
Goal: To make reporting trustless, reporting needs to be extended to include proof of computational validity.
Solution specification
Preliminary goal: In the first phase, only a subset of the Lido CL balance (referring to the asset balance related to the consensus layer in the Lido protocol), the number of active and exited balances, etc., will be reported.
The main participants:
Lido: It is necessary to make certain data from the consensus layer state available in the execution layer (Execution Layer).
Oracle: Report TVL and number of validators to the TVL contract.
Proof Producer: Produces computational integrity proof.
Proof Verifier: Verifies the proof in the EL contract.
Technical realization
Oracle: Standalone application, obtains input data, calculates Oracle reports, and produces containment proofs.
zkLLVM circuit: A program for building zero-knowledge proofs of computational integrity.
Trustless accounting audits for Oracle contracts: verify binary proofs, verify computational validity information.
Deployment phase
Current status: When enough trusting Oracle members submit a report and a quorum is reached.
Dark launch phase: A trust quorum is reached, but trustless reports are also accepted and necessary verifications are performed.
Transition period: Trust quorum is reached, at least 1 valid trustless report is received, and reports are consistent.
Full launch: The accounting contract only uses trustless reporting to determine TVL and number of validators.
Final state: Completely abolish quorum reporting and only use trustless reporting.
Conclusion
Compared with the grand blueprint of the AGI computing power market, the ZKP computing power market is currently more limited to applications in the blockchain. But the opposite benefit is that the development of the ZKP computing power market does not need to consider extremely complex designs such as neural networks, and the overall development difficulty is lower and the capital requirements are less. Combining the above projects, it is not difficult to find that while the AGI computing power market is still confused about how to implement it, the ZKP computing power market has already penetrated multiple application scenarios in the blockchain in multiple dimensions.
From a market perspective, the ZKP computing power market is still in an extremely blue ocean stage, and the Proof Market mentioned above is not the most ideal design in my mind. Combining algorithm optimization, application scenario optimization, hardware optimization and Regarding the choice of different computing power seller markets, the design of the ZKP computing power market still has a lot of room for imagination. Thinking from a development perspective, Vitalik has repeatedly emphasized that ZK’s impact on the blockchain field in the next ten years will be as important as the blockchain itself. However, from the perspective of ZK’s versatility, as the design matures, ZK’s future importance in non-blockchain fields may not be inferior to that of current AGI, and its prospects cannot be underestimated.
references:
1.Hardware Acceleration for Zero Knowledge Proofs:https://www.paradigm.xyz/2022/04/zk-hardware
2.Use of elliptic curves in cryptography ( 1988):https://link.zhihu.com/?target=https%3A//link.springer.com/content/pdf/10.1007% 252 F 3-540-39799-X_ 31.pdf
3.ZKLLVM + Lido Trustless Accounting oracle: solution spec:https://docs.google.com/document/d/1d5 Ru 7 WWae-yilXzOVgNS5DNweAMj6FNJrZllvD00mB0/edit
4.DIZK: A Distributed Zero Knowledge Proof System:https://www.usenix.org/conference/usenixsecurity18/presentation/wu
5.Proof Market Developer Guide:https://docs.nil.foundation/proof-market/proof-producers/proof-producer
6.IOSG Weekly Brief -ZKP acceleration:https://mirror.xyz/0x5Eba828AB4999825D8416D7EAd9563b64FD90276/8 DGPafCg 1 oLZ 0 T-cXSbcu5q1dYxhFDuilR1brWfLZXM
7.ZK Proof Computing: A new journey for computing hardware? :https://mp.weixin.qq.com/s/gInQOIJyLZwzzgmFkbaFwQ
8. A new era of ZK driven by hardware acceleration:https://mp.weixin.qq.com/s/3I-gz4O57_crS7_KZSA8KA