Brief analysis of DVT technology: How to make ETH staking more secure?
Original author -DeFI Saint
Compile - Odaily 0xAyA

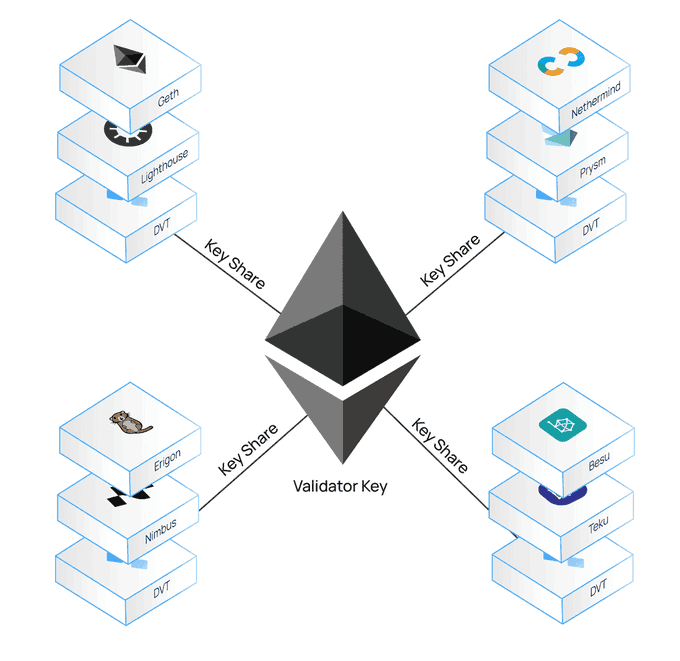
One of the key ways to increase the resiliency of validators and reduce any points of failure for Node Operators (NOs) is through Distributed Validator Technology (DVT).
@staderlabs_ethis applying DVT to its multi-pool architecture to make the Ethereum staking ecosystem more secure and decentralized.
Here’s what you need to know about DVT, compiled by Odaily:
Why is DVT needed?
When securing a POS network, validators/node operators are needed to perform this task, as any single point of failure can alter the activity of the network. Just like the navigation system, it needs to be online 24/7, and not only does it need to be online, the system must be robust and able to withstand any form of attack. What do you think would happen if a single point of failure in the navigation system caused inactivity could cause serious chaos in an area that requires constant communication?
This is the same situation in blockchain, where the system needs to be online 24/7 and resistant to any form of attack.
There can be many reasons why a node goes offline, and sometimes it can be reasons beyond the control of the node operator, but we dont need to make excuses. Therefore, we need a technology to deal with this situation, even if a node goes offline, it will not interfere with the activity of the blockchain it protects, and these node operators can resist such attacks.
Why do you need to defend against attacks?
If an entire system relies on a single node for key management and signing, and an attacker gains access to the system, the entire system is doomed. Therefore, key management and signing need to be spread across multiple parties/computers in the cluster so that it is not easy for an attacker to gain access to the system. Even if a node is offline, machines in each subnet of the cluster can perform signing operations.
Imagine a missile is controlled to hit a specific target, but at any moment the system is offline, or another malicious entity gains access to the system.
Advantages of 𝐃𝐕𝐓
Safety
Initially, a validator generates two public-private key pairs: a validator key to participate in consensus and a withdrawal key to access funds. Validators’ private keys need to be online 24/7, while withdrawal keys are always stored and securely kept in cold storage.
Therefore, DVT protects the validator’s private key by allowing the staker (in this case, the validator) to participate in staking while keeping the validator’s private key in cold storage (offline). The master key is encrypted and stored securely offline and split into shares across multiple nodes.
This generally improves safety and reduces penalties.
Decentralization
Ethereum is known for its decentralization, which improves security and reduces single points of failure.
DVT will allow significant network operators to hold large amounts of staked assets while keeping staking decentralized as keys are distributed across multiple nodes.
No single point of failure
DVT will allow validators to remain stable in the face of any challenge, even if individual nodes are offline or inactive. It also extends resiliency to other failure points caused by software or hardware failures.
It achieves this by using diverse software and hardware configurations in the cluster so that even if one of them fails, other validators can continue to provide the required services.
The size of the cluster is calculated mathematically using the following formula:
3 n+ 1 , where n = the number of failed nodes the cluster can tolerate.
Therefore, for n = 2 , two failed nodes can be tolerated, but at least five nodes are required to be online to validate the network.
Other aspects of DVT
The core components that make up DVT:
• Threshold Signature Scheme (TSS)
• Shamir’s Secret Sharing
• Multi-party computation (MPC)
• Distributed Key Generation (DKG)
• Consensus protocol
DVT is mainly used in the following areas:
• Separate pledge
• Staking as a Service (SaaS)
• Staking pool
Some disadvantages of DVT:
• Potential increase in latency
• Operating costs
• Requires additional components
Risks and challenges of using DVT:
• MEV theft: It is possible for a cluster to steal the MEV of the validators it runs.
• In a permissionless DVT cluster, if an entity controls a threshold number of key shares, it can gain influence on behalf of a validator, and any malicious behavior may result in penalties and compromise the security of stakers assets.
Practical application cases of DVT
Let’s now dive into the utilization of staking pools using Stader Ethereum as a case study following the launch of their DVT solution for $ETHx. Looking at the current Ethereum staking ecosystem with Stader Ethereum we can see that the main challenges currently faced are:
• Decentralization
• Capital requirements
• Single point of failure
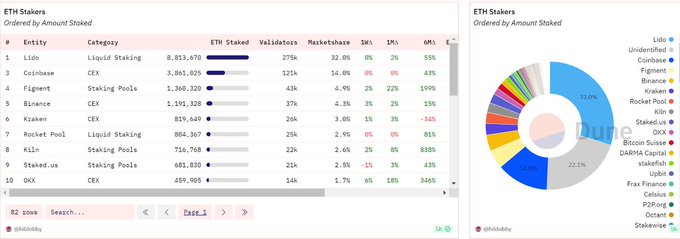
Observing the current situation, we can see that only a few entities hold the majority of the staked ETH.
This is not conducive to decentralization, as Ethereum’s ideal situation is to have as many independently operating validators as possible.
These entities control over 50% of all Ethereum pledged.
This also introduces centralization risk, as a single point of failure in any one of these entities could cause downtime in terms of network security.
Additionally, it does not promote capital efficiency in terms of capital requirements, which are higher for normal permissionless nodes.
Stader Ethereum has addressed this issue with its 4 ETH + 0.4 SD bond requirement.
Faced with the risks and challenges in DVT, Stader Ethereum mitigates this risk by running a 3rd pool in a DVT cluster.
The 3rd pool consists of:
• Split the validator key into a cluster of 4 or 7 nodes, where taking 1 or 2 nodes offline will not impact the system.
• Licensed and unlicensed clusters
For a 4-node cluster, there are 2 licensed and 2 unlicensed Node Operators (NOs).
For a 7-node cluster, there are 4 unlicensed NOs and 3 licensed NOs.
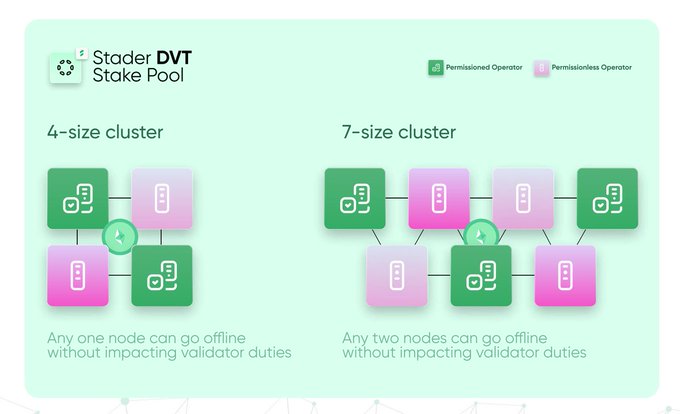
This setup ensures that a single entity cannot control the network and requires 3 NOs together to behave maliciously in the case of 4 nodes and 5 NOs together in the case of 7 nodes.
Additionally, in the event of a single point of failure, at least 3 nodes are required online to verify the network in a 4-node cluster, and at least 5 nodes are required online in a 7-node cluster.
Stader Ethereum has also added the following security measures to protect staked funds:
Validator ownership risk
In a 4 node cluster, there are 2 unlicensed and licensed NOs, so if one entity owns all the unlicensed NOs, improper use of MEV or reducible violations cannot occur as 3 NOs are required to be reached Consensus, while lacking a licensed NOs.
The same is true for licensed NOs, also in a 7-node cluster.
MEV theft
A single NOs in the cluster cannot control the withdrawal and EL reward addresses, in which case individual NOs cannot steal MEV.
Even if any licensed or unlicensed entity decided to change the address, they would not be able to do so as consensus cannot be reached.
Reduce the possibility of validators going offline
The risk of validators going offline is reduced.
Stader Ethereum has also introduced these features in its DVT solution.
Since the risk of slashing is reduced in DVT, this is more beneficial for permissionless NOs as the bond requirement for validators is now a combination of 2 ETH, which includes ETH and SD
This in turn lowers the barrier to entry for NOs and helps decentralize the Ethereum ecosystem.
Returns for NOs
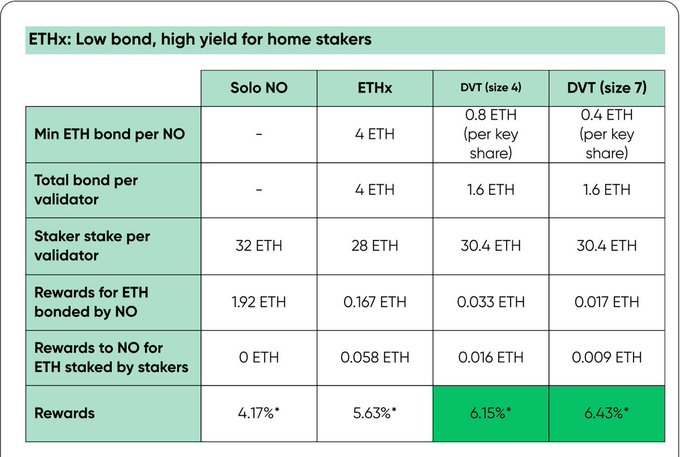
Since DVT reduces the bond amount of NOs, for a 4-node cluster, the return on NOs will be 47% higher than independent staking and 9% higher than ETHx rewards.
For a 7-node cluster, rewards will be 54% higher than independent staking and 14% higher than ETHx rewards.



