OKLink: Security Event Review in June 2023
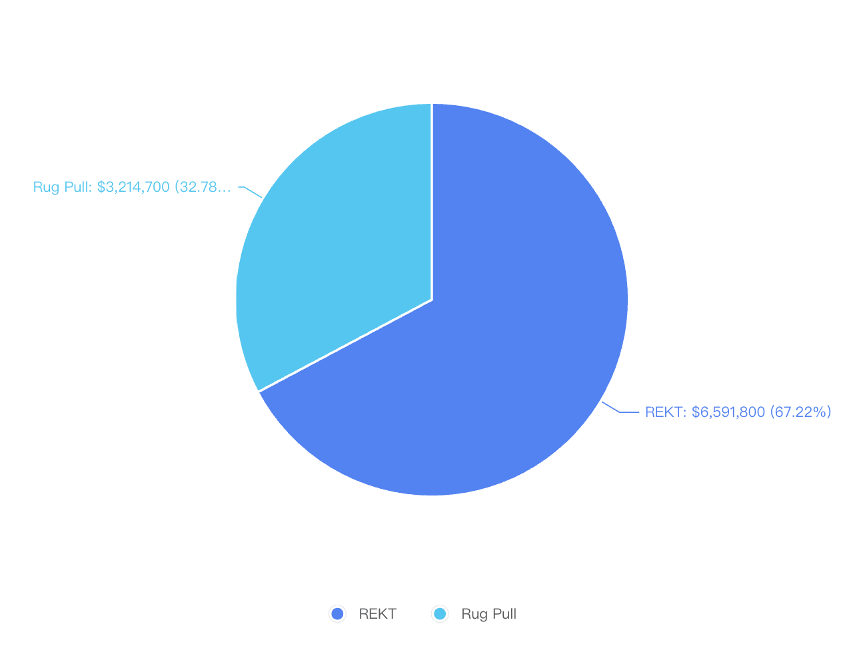
In June 2023, the REKT and RugPull events caused approximately $10 million in losses, a significant decrease compared to last month, but the number of security incidents remains unchanged. Among them, the abandoned Atlantis Loans suffered a governance attack, resulting in a loss of over $2.5 million. Users who have authorized the protocol should revoke their authorization in a timely manner. Additionally, the recent hacking incident of the Atomic wallet has resulted in losses exceeding $100 million, and the project team has not yet disclosed the reason for the hack. Furthermore, social media phishing incidents continue to occur, with the project's Discord and Twitter accounts being compromised and phishing links being frequently posted.
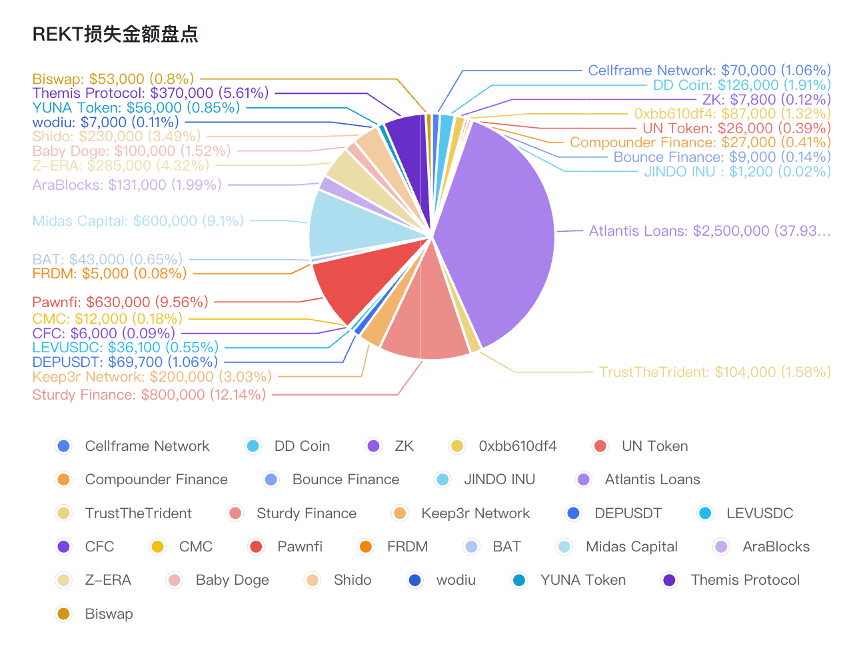
1.1 REKT Inventory
No.1
On June 1, cellframenet was attacked, and the attacker made approximately $70k in profits. The reason for the incident was the manipulation of the prices of the old CELL token and the new CELL token in the PancakeSwap pool, resulting in a miscalculation of the quantity of new CELL token during liquidity migration. The attacker obtained an excessive amount of new CELL token.
Attack transaction: https://www.oklink.com/cn/bsc/tx/ 0 x 943 c 2 a 5 f 89 bc 0 c 17 f 3 fe 1520 ec 6215 ed 8 c 6 b 897 ce 7 f 22 f 1 b 207 fea 3 f 79 ae 09 a 6
Attacker address:
https://www.oklink.com/cn/bsc/address/0 x 2525 c 811 ecf 22 fc 5 fcde 03 c 6711 2 d 34 e 97 da 6079
No.2
On June 1st, DD Coin's Marketplace contract was attacked, resulting in a loss of about $126k. The vulnerability was caused by an incorrect authorization of msg.sender in the sellItem() function of the Marketplace contract when selling DD Coin for BUSD, which allowed users to obtain double the amount of BUSD by selling DD Coin.
Attack transaction: https://www.oklink.com/cn/bsc/tx/ 0 xd 92 bf 51 b 9 bf 464420 e 1261 cfcd 8 b 291 ee 05 d 5 fbffbfbb 316 ec 95131779 f 80809
Attacker address:
https://www.oklink.com/cn/bsc/address/ 0 x 0 a 3 fee 894 eb 8 fcb 6 f 84460 d 5828 d 71 be 50612762
No.3
June 2nd, Zk Secure (ZK) token suffered a flash loan attack, causing a loss of about $ 7.8k.
Problem contract address:
https://www.oklink.com/cn/bsc/address/0xc8b77F282B7f83B745514D5ACb70b9E87F5b1A3D
No.4
June 6th, the unverified contract 0xbb610df4c1d9fd8e1dcad9fdd2dc9d685f412919 on BSC was attacked, resulting in a loss of $ 87k. The attacker was able to obtain a large amount of MURATIAI tokens by calling the emergencyWithdraw() function of the contract and finally profit by swapping the obtained MURATIAI tokens to WBNB through PancakeSwap V2.
One of the attack transactions: https://www.oklink.com/cn/bsc/tx/ 0 x 19 c 2 e 5 eaff 096 c 2408 a 11136579 d 81 d 2 f 7 b 2242446 f 51 dc 1 e 8471 fb 56 b 7 c 553 a
Attacker's address:
https://www.oklink.com/cn/bsc/address/0x8887a9387ee149a81a17145065a7b13132f732cd
No.5
On June 6th, the UN Token on BSC was attacked, resulting in a loss of about $26k. Due to a flaw in the _swapBurn() function of the UN Token contract, attackers were able to profit by sending UN Tokens to the UN swapPair contract and then calling the skim() function of the UN swapPair contract to raise the price of UN Tokens inside the contract.
Attack transaction: https://www.oklink.com/cn/bsc/tx/0xff5515268d53df41d407036f547b206e288b226989da496fda367bfeb31c5b8b
Attacker's address: https://www.oklink.com/cn/bsc/address/0xf84efa8a9f7e68855cf17eaac9c2f97a9d131366
No.6
On June 7th, Compounder Finance on Ethereum was attacked, resulting in a loss of about $27k.
Attack transaction: https://www.oklink.com/cn/eth/tx/0xcff84cc137c92e427f720ca1f2b36fbad793f34ec5117eed127060686e6797b1
Attacker Address:
https://www.oklink.com/cn/bsc/address/ 0 x 0 e 816 b 0 d 0 a 66252 c 72 af 822 d 3 e 0773 a 2676 f 3278
No.7
On June 8th, the AdminUpgradeabilityProxy contract of bounce_finance was exploited. The attacker forcefully swapped the ETH held by the contract into Auction Token by calling the claim() function of the contract, thereby driving up the price of Auction Token in the Uniswap pair. The attacker finally profited 4.7 ETH (~$9k) by reverse swapping the Auction Token back to ETH.
Attack Transaction: https://www.oklink.com/cn/eth/tx/ 0 x 88 bb 76 d 9 e 77019 e 309 bb 9 d 5 d 4557 a 1 acc 65 c 6022 a 9 fc 91 f 22 c 72 d 9 bdb 2 b 73 b 02
Attacker Address:
https://www.oklink.com/cn/eth/address/ 0 xb 1 ca 82 a 1 e 6 a 6255 bc 66 b 9330 b 08 b 642 b 07419469
No.8
On June 10th, JINDO INU token was attacked. JINDO INU is a reflection token, and the vulnerability lies in the implementation of the _reflectFee() function in the token, where the update of _rTotal should not subtract rCharity.
Problem contract address:
https://www.oklink.com/en/bsc/address/0x22D6363949E295873D261b812A281D014367e8f9
No.9
On June 11th, abandoned Atlantis Loans suffered Governance attack. The attacker set themselves as the admin of the token proxy contract, gaining control over the contract, and replacing it with a contract that includes a backdoor function to transfer user assets. As of now, the loss exceeds $2.5M.
Attacker's address:
https://www.oklink.com/en/bsc/address/0xEADe071FF23bceF312deC938eCE29f7da62CF45b
No.10
On June 11th, TrustTheTrident SELLC Token was subjected to a price attack, with the attacker profiting around $104k. The issue lies in the sendMiner() method in the miner contract, which has a vulnerability allowing the attacker to manipulate the price and inflate the calculated funds, resulting in profits.
Attack transaction: https://www.oklink.com/en/bsc/tx/0xe968e648b2353cea06fc3da39714fb964b9354a1ee05750a3c5cc118da23444b
Attacker's address:
https://www.oklink.com/cn/bsc/address/ 0 x 0060129430 df 7 ea 188 be 3 d 8818404 a 2 d 40896089
No.11
June 12th, SturdyFinance protocol was attacked, and the attacker made a profit of ~$800k. The root cause of the vulnerability was Balancer's read-only reentrancy issue. Sturdy Finance is a lending protocol, and the attacker borrowed more assets than the collateral by manipulating the price of B-stETH-STABLE tokens.
Attack transaction: https://www.oklink.com/cn/eth/tx/ 0 xeb 87 ebc 0 a 18 aca 7 d 2 a 9 ffcabf 61 aa 69 c 9 e 8 d 3 c 6 efade 9 e 2303 f 8857717 fb 9 eb 7
Attacker's address:
https://www.oklink.com/cn/eth/address/ 0 x 1 e 8419 e 724 d 51 e 87 f 78 e 222 d 935 fbbdeb 631 a 08 b
No.12
June 12th, thekeep 3 r was attacked, and the attacker made a profit of ~$200k. The reason for the attack was the leakage of the governor's private key.
Attack transaction: https://www.oklink.com/en/eth/tx/ 0 xc 749051 b 7 fbc 7294 b 8 fafe 71 b 1 d 06020 b 70 e 151964 f 87 dfdec 0 c 10 c 90 acd 18 ea
Attacker's address:
https://www.oklink.com/en/eth/address/ 0 x 4941 F 075 d 77708 b 819 e 9 f 630 f 65 D 65 c 3289 e 7 C 9 E
No.13
On June 13th, HNC token was attacked by a flash loan attack. The issue was due to a vulnerability in the project's miner contract, which allowed the attacker to manipulate the price for profit.
Problem contract address:
https://www.oklink.com/en/bsc/address/ 0 xe 22 e 857807 a 72 c 47 c 1 e 276 b 3079938 dee 3 b 514 c 9
No.14
On June 15th, DEPUSDT on Ethereum was attacked, and the attacker made a profit of $69.7k. The contract provided a public approveToken() method, allowing the attacker to transfer the tokens held by the contract.
Attack transaction: https://www.oklink.com/cn/eth/tx/0xf0a13b445674094c455de9e947a25bade75cac9f5176695fca418898ea25742f
Attacker's address:
https://www.oklink.com/cn/eth/address/0x7021C1B142eb634Fa0749CDA270c7AFF74Dc3B7f
No.15
On June 15th, the LEVUSDC token on Ethereum was attacked, and the attacker profited $36.1k. The contract provided a public approveToken() method, allowing the attacker to transfer the tokens held by the contract.
Attack transaction: https://www.oklink.com/cn/eth/tx/0x800a5b3178f680feebb81af69bd3dff791b886d4ce31615e601f2bb1f543bb2e
Attacker's address:
https://www.oklink.com/cn/eth/address/0x7021C1B142eb634Fa0749CDA270c7AFF74Dc3B7f
No.16
On June 15th, the CFC token on BSC was attacked through a flash loan, resulting in losses of approximately $6k.
Problem contract address:
https://www.oklink.com/en/bsc/address/ 0 xdd 9 B 223 AEC 6 ea 56567 A 62 f 21 Ff 89585 ff 125632 c
No.17
June 16th, CMC Token on the BNB chain suffered a vulnerability, resulting in approximately $12k in losses. the problem was due to the process of exchanging CMC Token for BUSD through PancakeSwap v2, which would burn a portion of the CMC Token in the pair, thereby raising the price of CMC Token in the pair. Attackers took advantage by repeatedly exchanging CMC Token for BUSD, thus profiting.
Attack Transaction: https://www.oklink.com/en/bsc/tx/0xa92d1f7c2c7c4eda8dcef57d26ec19d26456b1b8fed024f35a149c45dd3d9994
Attacker's Address:
https://www.oklink.com/en/bsc/address/0xcb7f6d5dc871c72bef05d0b25f054b26fdc5354c
No.18
On June 17th, PawnfiOfficial was attacked, resulting in losses exceeding $630k. The root cause of this attack is that the protocol failed to verify whether the specified NFT was actually transferred when used as collateral for borrowing.
One of the attack transactions: https://www.oklink.com/cn/eth/tx/ 0 xe 855 cc 3 bad 87933 bf 742 fd 474 bd 0 ae 0 ec 58 d 45 e 9 c 1 a 0643 b 9700 dafe 8 faf 0864
Attacker's address:
https://www.oklink.com/cn/eth/address/ 0 x 8 f 7370 d 5 d 461559 f 24 b 83 ba 675 b 4 c 7 e 2 fdb 514 cc
No.19
June 17th, Ethereum's FRDM token was hit by a flash loan attack, resulting in a loss of ~$5k.
Problem contract address:
https://www.oklink.com/cn/eth/address/ 0 x 1238 dDA 2319812 c 8 B 405 e 84 D 7 EFf 5 DFB 81783008
No.20
June 17th, BSC's BAT token was hit by a flash loan attack, resulting in a loss of ~$43k.
Problem contract address:
https://www.oklink.com/cn/bsc/address/ 0 xBD 2 f 6 B 7 A 19 F 2449675 F 7432 d 29 d 1 DC 1150 CcD 08 f
No.21
On June 18th, MidasCapitalXYZ suffered an attack, resulting in a loss of $600k. The root cause of the issue was a rounding problem in the Compound V2 lending protocol that it forked. HundredFinance also experienced a similar attack earlier.
One of the attack transactions: https://www.oklink.com/cn/bsc/tx/0x4a304ff08851106691f626045b0f55d403e3a0958363bdf82b96e8ce7209c3a6
Attacker's address: https://www.oklink.com/cn/bsc/address/0x4b92cc3452ef1e37528470495b86d3f976470734
No.22
On June 19th, the AraBlocks project on BSC was attacked, resulting in a loss of $131k. The vulnerability was due to unauthorized contracts (0x7ba5d) lacking access control in swap operations, leading to price manipulation.
One of the attack transactions: https://www.oklink.com/cn/bsc/tx/0xd87cdecd5320301bf9a985cc17f6944e7e7c1fbb471c80076ef2d031cc3023b2
Attacker's address:
https://www.oklink.com/cn/bsc/address/ 0 xf 84 efa 8 a 9 f 7 e 68855 cf 17 eaac 9 c 2 f 97 a 9 d 131366
No.23
June 20th, zera_web private key leaked or rugged, the attacker gained about 1.8 M ZERA Token and sold for a profit of ~$285 k.
Attacker's address:
https://www.oklink.com/cn/bsc/address/ 0 xafe 015 d 862 b 6 e 1 c 54 c 2870 d 89557 a 90 dafb 7 fefe
No.24
June 21st, BabyDogeCoin was attacked, the attacker made a profit of ~$100 k.
One of the attack transactions: https://www.oklink.com/cn/bsc/tx/ 0 xbaf 3 e 4841614 eca 5480 c 63662 b 41 cd 058 ee 5 c 85 dc 69198 b 29 e 7 ab 63 b 84 bc 866 c
Attacker's address:
https://www.oklink.com/cn/bsc/address/ 0 xee 6764 ac 7 aa 45 ed 52482 e 4320906 fd 75615 ba 1 d 1
No.25
On June 24th, the ShidoGlobal project was attacked, and the attacker profited ~$230k. The vulnerability was caused by a price difference between Shido V1 Token and Shido V2 Token in the PancakeSwap pool. The attacker used flash loans to buy Shido V1 Token and then upgraded it to V2 Token at a 1:1 ratio. Finally, they sold all the obtained V2 Tokens to make a profit.
Attack transaction: https://www.oklink.com/cn/bsc/tx/0x72f8dd2bcfe2c9fbf0d933678170417802ac8a0d8995ffa56bfbabe3aa712d6
Attacker's address:
https://www.oklink.com/cn/bsc/address/0x69810917928b80636178b1bb011c746efe61770d
No.26
On June 24th, wodiu_os suffered a flash loan attack, resulting in a loss of ~$7k. The vulnerability was due to a portion of WODIU Token being burned on each transfer in and transfer out in the Uniswap pair, which manipulated the price of WODIU Token in the pair.
Faulty contract address:
https://www.oklink.com/cn/eth/address/0xb2b1ca8a73b3C31bD90dA7AF307D743CEc5BF39E
No.27
On June 27th, BAT YunaToken on Ethereum was attacked by a flash loan, resulting in a loss of ~$56k. The attack caused YunaToken to drop by nearly 90%.
Problem contract address:
https://www.oklink.com/cn/bsc/address/0x1C261D5B5566BBB489d93622D68a7D7964C72b0A
No.28
On June 28th, ThemisProtocol project on Arbitrum was attacked by a flash loan, and the attacker profited ~$370k. The vulnerability was due to the flawed price oracle used by the protocol, allowing the attacker to manipulate the price and borrow assets far exceeding their collateral value.
Attack transaction:
https://www.oklink.com/cn/arbitrum/tx/0xff368294ccb3cd6e7e263526b5c820b22dea2b2fd8617119ba5c3ab8417403d8
Attacker's address:
https://www.oklink.com/cn/arbitrum/address/0xdb73eb484e7dea3785520d750eabef50a9b9ab33
No.29
June 30th, the Biswap_Dex project was attacked. The vulnerability was due to the lack of necessary checks on user-input parameters in the migrate() function provided by the V3 Migrator contract, resulting in losses to user assets authorized for LP Token by the V3 Migrator contract. The attacker profited ~$53k and the attack is still ongoing. Users need to revoke authorization to the V3 Migrator contract as soon as possible.
Attack transaction: https://www.oklink.com/cn/bsc/tx/ 0x706ea75c763b67e718ee671debaef41c127f5635d4092b476d7be1162994daf7
Attacker's address: https://www.oklink.com/cn/bsc/address/ 0xa1e31b29f94296fc85fac8739511360f279b1976
1.2 RugPull Inventory
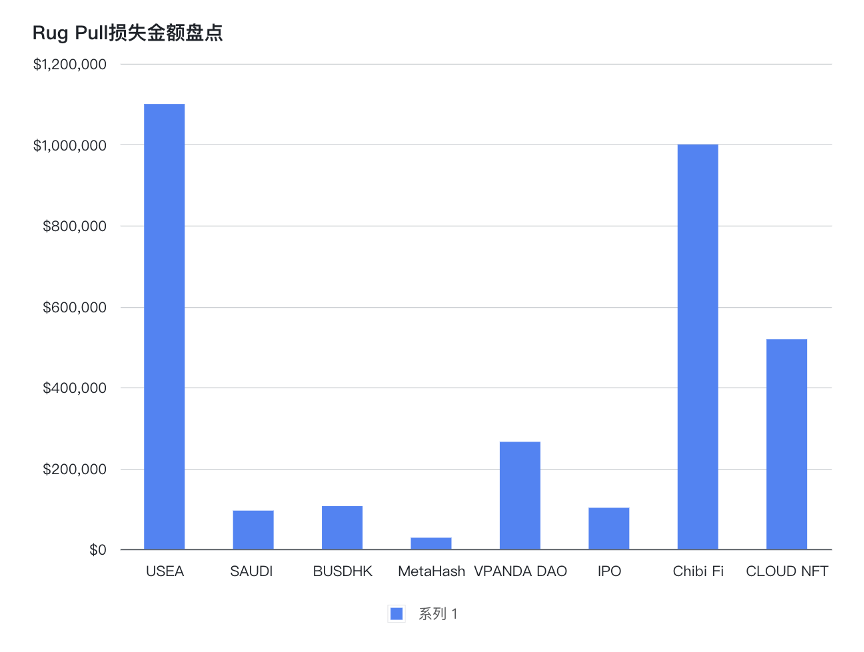
No.1
On June 6th, the deployer of the USEA token, rugged, stole approximately $1.1 million of user funds. To accomplish this, they minted a large number of tokens and removed all liquidity from the USEA token pair on PancakeSwap. This caused $USEA to drop by nearly 99%.
No.2
On June 8th, the MEME token on Ethereum, SAUDI, was rugged, resulting in a profit of around $95K and a 98.5% drop in $SAUDI.
No.3
On June 10th, the scam token BUSDHK was rugged, resulting in a 100% drop in $BUSDHK. The deployer of the token controlled an EOA account and minted a large amount of BUSDHK, which was then swapped for 448 BNB.
No.4
On June 13th, the scam token MetaHash was rugged. The deployer of the token controlled an EOA account and gained around $28K by removing liquidity.
No.5
On June 19th, VPandaCommunity was rugged, stealing approximately $265K in funds. This caused $VPC to drop by 97.4%.
No.6
On June 19th, IPO_web 3 was rugged, resulting in a profit of around $102K. This caused IPO to drop by 32%.
No.7
On June 27th, Chibi_Fi was rugged, and they deleted their Twitter account and website. Cryptocurrency worth around $1 million was stolen, and the stolen funds were converted into approximately 555 ETH and bridged to Ethereum through Arbitrum.
No.8
On June 28th, CLOUD NFT (CLOUDNFT) was rugged, and the deployer of the contract converted the stolen $518.7k BUSD into 1070 BNB and sent it to Tornado Cash.
1.3 Inventory of Social Media Scams and Phishing Attempts
No.1
On June 1st, PinkDrainer stole "The Otherside: OTHR Token" NFT with the ID 65611 through Blur.
No.2
On June 1st, Orbiter_Finance Discord was attacked. Please refrain from clicking any links until the team confirms that they have regained control of the server.
No.3
On June 1st, basenameapp Discord was attacked. Please refrain from clicking any links until the team confirms that they have regained control of the server.
No.4
On June 1st, FlareNetworks Discord was attacked. Please refrain from clicking any links until the team confirms that they have regained control of the server.
No.5
On June 1st, a phishing link was posted in the EquilibreAMM Discord server. Please refrain from clicking any links until the team confirms that they have regained control of the server.
No.6
On June 2nd, a fake Loyal announcement website. Do not interact with hxxps://claim-loyal.org/.
No.7
On June 3rd, PeterSchiff's Twitter account was hacked and promoting a phishing website. Do not interact with hxxps://gold.fo/.
No.8
On June 3, a phishing link was posted in the MantaNetwork Discord server. Please do not click on any links until the team confirms that they have regained control of the server.
No.9
On June 4, beware of the fraudulent Loyal claim website promoted on Twitter. Do not interact with hxxps://loyal.gl/.
No.10
On June 5, a phishing link was posted in the mobius_market Discord server. Please do not click on any links until the team confirms that they have regained control of the server.
No.11
On June 5, a phishing link was posted in the Bee_NetworkFP Discord server. Please do not click on any links until the team confirms that they have regained control of the server.
No.12
On June 5, BIFROSTio Discord was attacked. Please do not click on any links until the team confirms that they have regained control of the server.
No.13
On June 6, beware of the fraudulent Finale claim website promoted on Twitter. Do not interact with hxxps://finale.claims/.
No.14
On June 6, a phishing link was posted in the ZKEX_Official Discord server. Please do not click on any links until the team confirms that they have regained control of the server.
No.15
On June 7, a phishing link was posted in the BNBCHAIN Discord server. Please do not click on any links until the team confirms that they have regained control of the server.
No.16
On June 7, the VinodChavdaBJP Twitter account has been compromised and is promoting a phishing website. Do not interact with hxxps://xrpfinance-airdrop.com/.
No.17
On June 7th, the ColeThereum Twitter account was hacked and is promoting a phishing website. Do not interact with hxxps://entertheigloo.com/.
No.18
On June 7th, a phishing link was posted in the SkyweaverGame Discord server. Do not click on any links until the team confirms they have regained control of the server.
No.19
On June 7th, a phishing link was posted in the LodestarFinance Discord server. Do not click on any links until the team confirms they have regained control of the server.
No.20
On June 8th, beware of the fake RICK claim website promoted on Twitter. Do not interact with pickandrick.com.
No.21
On June 8th, a phishing link was posted in the KeplerHomes Discord server. Do not interact with hxxps://claim-kepler.homes/.
No.22
On June 9th, a phishing link was posted in the stellaxyz_ Discord server. Do not interact with hxxps://alpha-token.xyz/.
No.23
On June 9th, a phishing link was posted in the bankercoinada Discord server. Do not interact with hxxps://bankercoinada.site/.
No.24
On June 9th, the franklinisbored Twitter account was hacked and is promoting a phishing website. Do not interact with hxxps://debanklabs.com/.
No.25
On June 10th, a phishing link was posted in the nemesis_dao Discord server. Do not interact with hxxps://helenaclaim.xyz/#.
No.26
On June 10th, a phishing link was posted in the HelenaFinancial Discord server. Do not interact with hxxps://helenaclaim.xyz/#.
No.27
On June 10th, a phishing link was posted in the SafariSurfers Discord server. Do not interact with hxxps://mintjttribe.com/.
No.28
On June 11th, a phishing link was posted in the ether_fi Discord server. Do not click on any links until the team confirms they have regained control of the server.
No.29
On June 11th, a phishing link was posted in the RSTLSSxyz Discord server. Do not interact with hxxps://rstlss-token.xyz/.
No.30
On June 11th, the questify_gg Discord server was infiltrated. Do not connect your wallet as it will connect to a phishing website.
No.31
On June 11th, beware of the fake Layer Zero Labs claim website promoted on Twitter. Do not interact with hxxps://leyerszero.com/.
No.32
On June 12th, a phishing link was posted in the thatMediaWag Discord server. Do not interact with hxxps://wag-media.club/.
No.33
On June 13th, a phishing link was posted in the WickedBoneClub Discord server. Do not interact with hxxps://wickedboneclub.org/.
No.34
On June 13th, beware of the fake Golden Pepe claim website promoted on Twitter. Do not interact with hxxps://mygoldenpp.com/.
No.35
On June 14th, KevinSvenson_ Discord and Twitter accounts were both hacked. Please do not click on any links until the team confirms that they have regained control of the servers.
No.36
On June 14th, beware of the fake ChainGPT claim website being promoted on Twitter. Do not interact with hxxps://chaingpt.claims/.
No.37
On June 15th, a phishing link was posted in the BeamerBridge Discord server. Do not interact with hxxps://beamertoken.com/.
No.38
On June 15th, a phishing link was posted in the L 0 _Corner Discord server. Please do not click on any links until the team confirms that they have regained control of the servers.
No.39
On June 15th, beware of the fake Lido airdrop website being promoted on Twitter. Do not interact with hxxps://lido v 2 finance.com/.
No.40
On June 15th, beware of the fake Finale airdrop website being promoted on Twitter. Do not interact with hxxps://finale.website/.
No.41
On June 16th, a phishing link was posted in the zkxprotocol Discord server. Do not interact with hxxps://zkx-token.fi/.
No.42
On June 16th, a phishing link was posted in the ShellProtocol Discord server. Do not interact with hxxps://claim-shellprotocol.io/.
No.43
On June 16th, a phishing link was posted in the adoptwombat Discord server. Do not interact with hxxps://womtoken.app/.
No.44
On June 16, be wary of the false Psyop airdrop website being promoted on Twitter. Do not interact with hxxps://psyopgifts.com/ and hxxps://xn--psop-625 a.com/.
No.45
On June 16, be wary of the false Apecoin airdrop website being promoted on Twitter. Do not interact with hxxps://apecoin.gl/.
No.46
On June 17, a phishing link was posted in the polarbearsnft Discord server. Do not interact with hxxps://polarbearsnft.org/.
No.47
On June 17, a phishing link was posted in the SteadyStackNFT Discord server. Do not click on any links until the team confirms they have regained control of the server.
No.48
On June 18, be wary of the false Layerzero airdrop website being promoted on Twitter. Do not interact with hxxps://enter-layerzero.org/.
No.49
On June 19, be wary of the false zkSync airdrop website being promoted on Twitter. Do not interact with hxxps://enter.zkzync.org/.
No.50
On June 19, be wary of the false Optimism airdrop website being promoted on Twitter. Do not interact with hxxps://airdrop.optimism.sx/.
No.51
On June 20, a phishing link was posted in the CandyCollectiv Discord server. Do not interact with hxxps://collab-land.ac/.
No.52
On June 20th, a phishing link was posted in the rlmverse Discord server. Do not click on any links until the team confirms that they have regained control of the server.
No.53
On June 20th, a phishing link was posted in the Inf_Skies Discord server. Do not interact with hxxps://accessprotocol.live/.
No.54
On June 20th, a phishing link was posted in the Popcorn_DAO Discord server. Do not interact with hxxps://popclaim.network/.
No.55
On June 21st, a phishing link was posted in the YouSUI_Global Discord server. Do not interact with hxxps://yousui.live/.
No.56
On June 21st, an exit scam was detected on a fake Crypto Legion token. The website hxxps://cryptolegions.net/ promoting this fake token is not the official website of the project.
No.57
On June 21st, a phishing link was posted in the btcordinal Discord server. Do not click on any links until the team confirms that they have regained control of the server.
No.58
On June 22nd, a phishing link was posted in the GamioNFT Discord server. Do not interact with hxxps://mint-galxe.com/ventory/campaign/GCmwbUQaM 7/.
No.59
On June 22nd, be cautious of fake PEPE airdrop websites promoted on Twitter. Do not interact with hxxps://pepecoin.guru/.
No.60
On June 22nd, be cautious of fake Evermoon airdrop websites promoted on Twitter. Do not interact with hxxps://evermoonerc 20.com/.
No.61
On June 23, a phishing link was posted in the Dogami Discord server. Do not interact with hxxps://dogami.gift/.
No.62
On June 23, a phishing link was posted in the ObolNetwork Discord server. Do not interact with hxxps://obol.store/.
No.63
On June 23, a phishing link was posted in the optyfi Discord server. Do not interact with hxxps://optyfi.net/.
No.64
On June 24, a fake airdrop token was sent to multiple EOA accounts. Users were tricked into granting authorization to their token holdings by visiting hxxps://apdom.site/ to "claim the reward".
No.65
On June 25, a phishing link was posted in the ontropy Discord server. Do not interact with hxxps://ontropy.co/.
No.66
On June 25, a phishing link was posted in the AltitudeDeFi Discord server. Do not interact with hxxps://altitudedefi.net/.
No.67
On June 25, a phishing link was posted in the lifiprotocol Discord server. Do not interact with hxxps://lifi.bar/.
No.68
On June 25, a phishing link was posted in the BrainlesSpikes Discord server. Do not interact with hxxps://brainlesspikes.app/.
No.69
On June 25, the OptyFi Discord server was compromised. Do not click on any links until the team confirms that they have regained control of the server.
No.70
On June 25th, beware of the fake Chainlink airdrop website being promoted on Twitter. Do not interact with hxxps://claim-chainlink.net/.
No.71
On June 26th, the Dackie_Official Discord server was attacked and phishing links were posted. Do not click on any links until the team confirms they have regained control of the server.
No.72
On June 26th, the thesoftdao Discord server was attacked and phishing links were posted. Do not click on any links until the team confirms they have regained control of the server.
No.73
On June 26th, beware of the fake Golden Pepe claim website being promoted on Twitter. Do not interact with hxxps://my-goldenpepe.com/.
No.74
On June 26th, the MyCopilotBae Discord server posted phishing links. Do not click on any links until the team confirms they have regained control of the server.
No.75
On June 26th, the lightyear_game Discord server posted phishing links. Do not click on any links until the team confirms they have regained control of the server.
No.76
On June 26th, beware of the fake Loyal Airdrop website being promoted on Twitter. Do not interact with hxxps://loyaltylabs.gg/.
No.77
On June 26th, beware of the fake Pepe Staking website being promoted on Twitter. Do not interact with hxxps://staking-pepe.com/.
No.78
On June 26th, the oasys_games Discord server posted phishing links. Do not click on any links until the team confirms they have regained control of the server.
No.79
June 27th, beware of the fake Mystery box airdrop website being promoted on Twitter. Do not interact with hxxps://web 3-limited.xyz/.
No.80
June 27th, a phishing link was posted on the ZigZagExchange Discord server. Do not click on any links until the team confirms that they have regained control of the server.
No.81
June 27th, a phishing link was posted on the Entanglefi Discord server. Do not click on any links until the team confirms that they have regained control of the server.
No.82
June 27th, the AOFVerse Discord server was attacked and a phishing link was posted. Do not click on any links until the team confirms that they have regained control of the server.
No.83
June 27th, the Meowcoin 2023 Discord server was attacked and a phishing link was posted. Do not click on any links until the team confirms that they have regained control of the server.
No.84
June 28th, the MantaNetwork Twitter account was attacked and a phishing link was posted. Do not interact with hxxps://manta.money/.
No.85
June 28th, the WINRProtocol Discord server was attacked and a phishing link was posted. Do not click on any links until the team confirms that they have regained control of the server.
No.86
June 28th, beware of the fake Loyal airdrop website being promoted on Twitter. Do not interact with hxxps://loyaltylabs.eu/.
No.87
June 28th, the cilistia p 2 p Discord server was attacked and a phishing link was posted. Do not click on any links until the team confirms that they have regained control of the server.
No.88
On June 29th, the UmbNetwork Discord server was attacked and phishing links were posted. Please do not click on any links until the team confirms they have regained control of the server.
No.89
On June 29th, the BitKingz Discord server was attacked and phishing links were posted. Please do not click on any links until the team confirms they have regained control of the server.
No.90
On June 29th, be cautious of the false Layer Zero airdrop website promoted on Twitter. Do not interact with hxxps://layerzero.global/.
No.91
On June 29th, phishing links were posted in the Syntropynet Discord server. Do not interact with hxxps://syntropy-net.com/.
No.92
On June 30th, the radixdlt Discord server was attacked and phishing links were posted. Please do not click on any links until the team confirms they have regained control of the server.
No.93
On June 30th, the ASETPay Discord server was attacked and phishing links were posted. Please do not click on any links until the team confirms they have regained control of the server.
No.94
On June 30th, the Dworfz Discord server was attacked and phishing links were posted. Please do not click on any links until the team confirms they have regained control of the server.
No.95
On June 30th, the swellnetworkio Discord server was attacked and phishing links were posted. Please do not click on any links until the team confirms they have regained control of the server.
No.96
On June 29th, be cautious of the false airdrop website promoted on Twitter. Do not interact with hxxps://earndrops.com/.
1.4 Other
No.1
On June 1, unsheth_xyz disclosed that one of the private keys of its unshETH contract deployer was leaked, causing a -23% decrease in USH price.
No.2
On June 3, multiple Atomic Wallet users reported on social media that their wallet assets were stolen. Atomic Wallet later confirmed the reports and stated that they were investigating and analyzing the cause. As of now, Atomic Wallet users have collectively lost over $100 million in this attack.
No.3
Cryptocurrency brokerage firm Floating Point Group was hacked on June 11. The estimated total loss from the attack is between $15 million and $20 million.
No.4
On June 14, Hashflow suffered from a white hat attack. An unverified contract, Hashflow Router, had an authorization vulnerability. The white hat hacker exploited this vulnerability to send funds authorized to the Hashflow Router contract to the address 0xddb19a1bd22c53dac894ee4e2fbfdb0a06769216 and provided interface functions for users to recover their transferred assets from the contract.
One of the attack transactions: https://www.oklink.com/cn/eth/tx/0xdedda493272b6b35660b9cc9070d2ea32ee61279b821184ff837e0a5752f4042
Attacker's address: https://www.oklink.com/cn/eth/address/0xBDf38B7475Ff810325AA39e988fb80E0aA007E84
No.5
On June 28, unagiidotcom detected a vulnerability in its code and initiated a white hat transaction to transfer the affected funds.
II. Security Summary
In June 2023, security incidents in the DeFi sector continue to occur frequently, with multiple token projects being attacked. These token projects, due to their complex economic models, are more susceptible to attacks. Investors should pay attention to whether these projects have been audited by authoritative institutions to reduce investment risks when investing in these tokens. The governance attack on the abandoned Atlantis Loans project serves as a reminder that for Defi protocols that are no longer being interacted with, authorizations should be revoked in a timely manner to avoid unnecessary asset losses. In addition, the Midas Capital project, a Compound V2 Fork, had already experienced two similar security incidents before being attacked. This indicates that risk control awareness and operational capabilities of the team are also crucial for the healthy operation of Defi protocols. Furthermore, social media phishing projects remained prevalent this month, with several project official Discord or Twitter accounts being compromised to spread phishing links. Additionally, cases of NFT phishing scams have also occurred, so users need to remain vigilant and avoid clicking suspicious links when participating in related projects.



