Zero Time Technology: 2022 Global Web3 Industry Security Research Report
Original source: Zero Hour Technology
Summary
Summary
2022 is a year of diversified innovation in the encryption world, but behind the innovation, there are also many staggering security incidents. The security team of Zero Time Technology released the "Global Web3 Industry Security Research Report 2022", which reviewed the global policies of the Web3 industry in 2022, the basic concepts covered by the main tracks, security incidents, loss amounts and attack types, and analyzed typical security incidents. A detailed analysis is made, and safety precautions and measures are proposed. We hope to help practitioners and users understand the status quo of Web3 security, improve awareness of network security, protect digital assets, and take security precautions.
In 2022, the total market value of cryptocurrencies in the global Web3 industry will be as high as 2.4 trillion US dollars. Affected by the industry mine explosion, compared with last year's highest total market value of 2.97 trillion US dollars, this year has declined, but the overall asset size is constantly expanding.
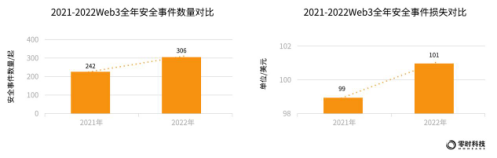
According to statistics from Zero Hour Technology, there will be 306 security incidents in 2022, with a cumulative loss of US$10.1 billion. Compared with 2021, there are 64 new Web3 security incidents this year, a year-on-year increase of 26%.
There were 136 security incidents in the six main tracks of Web3: public chain, cross-chain bridge, wallet, exchange, NFT, and DeFi, causing a loss of more than 4.021 billion US dollars. In addition, emerging fields such as GameFi and DAO have become the targets of hackers, and fraud and running away incidents continue, causing serious losses.
In 2022, typical security incidents with a loss of more than 100 million US dollars will cause a total loss of 2.845 billion US dollars, accounting for 28% of the total loss in 2022. Typical representatives include: Poly Network, a cross-chain interoperability protocol, with a loss of US$625 million; the exchange FTX, with a loss of US$600 million; and the Solona ecological wallet, with a loss of US$580 million.
In 2022, there will be various types of attacks on global Web3 security incidents. From the perspective of the number of security incidents, the top 5 typical attack types are: hacker attacks, asset theft, security vulnerabilities, private key theft, and phishing attacks. In terms of the amount of loss, the top 5 typical attack types are: asset theft, hacker attack, private key theft, price manipulation, and flash loan attack.
The most representative regulatory case this year is: the US Treasury Department's Office of Foreign Assets Control (OFAC) imposed sanctions on the Tornado Cash agreement, prohibiting US entities or individuals from using Tornado Cash services. According to the U.S. Department of the Treasury, since its establishment in 2019, Tornado Cash has helped launder more than $7 billion.
1. Global Web3 Industry Review and Security Situation Overview
Web3 refers to a new generation of networks based on encryption technology, which integrates various technologies and ideas such as blockchain technology, token economics, decentralized organizations, and game theory. It was proposed by Gavin Wood, the co-founder of Ethereum in 2014. Web3 is built on the basis of blockchain. Since 2008, blockchain technology has been developed for more than 14 years. The explosion of the Web3 industry in 2022 is inseparable from years of accumulation in the development of the blockchain industry.
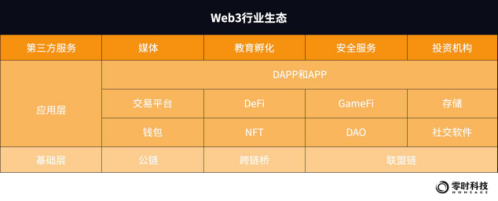
Looking at the Web3 ecosystem from the perspective of users, it can be divided into basic layer, application layer and third-party services. The base layer is mainly based on chains such as public chains, cross-chain bridges, and alliance chains, providing network infrastructure for Web3; the application layer is mainly based on APP (centralized application programs) and DAPP (decentralized application programs). Applications to interact with, including trading platforms, wallets, DeFi, NFT, GameFi, DAO, storage and social software, etc. The basic layer and application layer promote the prosperity of Web3 ecology, but also bring huge security risks to Web3. The service ecology is a third party in the Web3 industry, in which media, education incubation and investment institutions provide assistance to the industry, and security service organizations such as Zero Time Technology are an indispensable part of escorting Web3 security.
As of December 2022, according to statistics from coinmarketcap, the total market value of cryptocurrencies in the global Web3 industry reached US$2.4 trillion at its peak. Affected by the industry's thunderstorm incident, compared with last year's highest total market value of US$2.97 trillion, this year has declined. Although the total market capitalization fluctuates, the overall asset size is constantly expanding. Due to the fast pace of industry innovation, weak security awareness of users, unimproved supervision, and prominent security issues, Web3 is becoming a "cash machine" for hackers.
According to statistics from Zero Hour Technology, there will be 306 security incidents in 2022, with a cumulative loss of US$10.1 billion. Compared with 2021, there are 64 new Web3 security incidents this year, a year-on-year increase of 26%. Among them, 136 security incidents occurred in the six main tracks of public chain, cross-chain bridge, wallet, exchange, NFT, and DeFi, resulting in a loss of more than 4.021 billion US dollars.
In addition to the above six major tracks, there were a total of 170 other security incidents, with a loss amounting to 6.079 billion US dollars. For example, emerging fields such as GameFi and DAO have become the targets of hackers, and fraud and escape incidents are emerging one after another. With multiple giants entering the metaverse and NFT, the scale of assets on the chain will continue to grow in the future, and the number of Web3 network security violations may continue to soar.
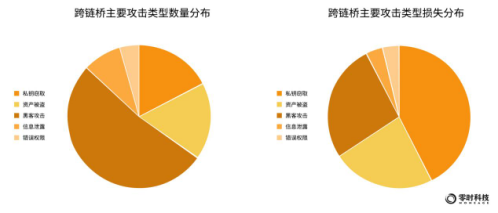
According to the statistics of Zero Hour Technology, in 2022, among the six main tracks of the global Web3 ecology: 10 security incidents occurred on the public chain, with a total loss of about 157 million US dollars; 14 security incidents occurred on the cross-chain bridge, with a total loss of 1.338 billion US dollars; There were 19 security incidents, with a total loss of US$1.192 billion; 25 security incidents in wallets, with a total loss of US$693 million; 25 security incidents in DeFi, with a total loss of US$593 million; 44 security incidents in NFT, with a loss of over US$42.56 million .
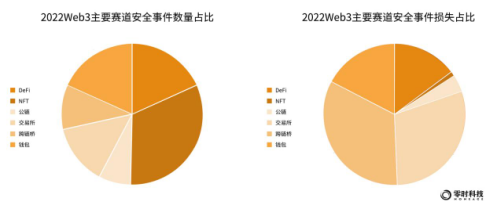
Judging from the number of security incidents that occurred on the main track, NFT has the most security incidents, which is inseparable from its becoming a popular track sought after by the industry in 2022. On the other hand, due to the increase in the number of people entering the Web3 industry, wallets and DeFi have become the hardest hit areas for security incidents. In terms of the amount of losses, the cross-chain bridge ranked first and suffered the most losses.
In 2022, from the perspective of the number of security incidents occurring on the global Web3, the top 5 typical attack types are: hacker attacks, accounting for 37%; asset theft, accounting for 19%; security breaches, accounting for 13%; private key theft, accounting for 9%; phishing attacks, 7%.
In terms of the amount of loss, the top 5 typical attack types of global Web3 security incidents are: asset theft, with a loss of US$5.581 billion; hacking, with a loss of US$3.029 billion; private key theft, with a loss of US$1.25 billion; price manipulation, The loss amount was 232 million US dollars; the flash loan attack, the loss amount was 137 million US dollars.
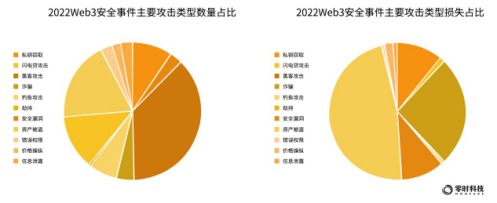
It is worth noting that many security incidents that occurred in 2022 will not be attacked by only one kind of attack, and some incidents may simultaneously involve asset theft, private key theft, hacking, private key leakage, and security breaches.
Note: The main attack types are explained as follows
Stolen assets: stolen virtual currency, stolen platform
Hacking: hackers and other types of attacks
Information leakage: private key leakage, etc.
Security loopholes: contract loopholes, functional loopholes
Wrong permissions: wrong system permission settings, wrong contract permissions, etc.
Phishing Attack: Phishing
price manipulation: price manipulation
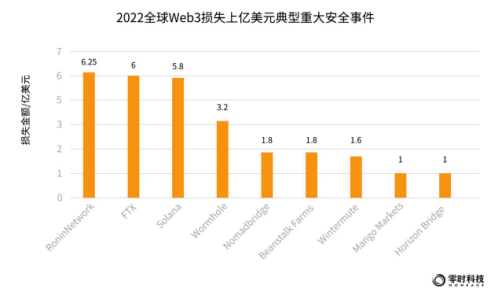
According to the monitoring information of Zero Hour Technology's blockchain security intelligence platform, typical security incidents with a loss of more than 100 million US dollars in 2022 will cost a total of 2.845 billion US dollars, accounting for 28% of the total loss in 2022.
2. Global Web3 Regulatory Policy
In 2022, the blockchain-based next-generation Internet Web3 will usher in a peak of growth. Facing this emerging industry with financial technology characteristics, global governments and regulatory agencies are paying close attention to it. Web3 has a wide range of application fields, global distribution and collaboration, and high technical content. In addition, the development direction of the Web3 industry and the definition of digital assets by various countries and their internal regulatory agencies are not uniform, which has brought huge challenges to global financial supervision. In 2022, financial crimes, hacker attacks, fraud and extortion, and money laundering incidents will occur frequently, with huge amounts, serious losses, and wide-ranging impacts. In order to ensure the security and compliance of Web3, various countries have introduced regulatory policies.
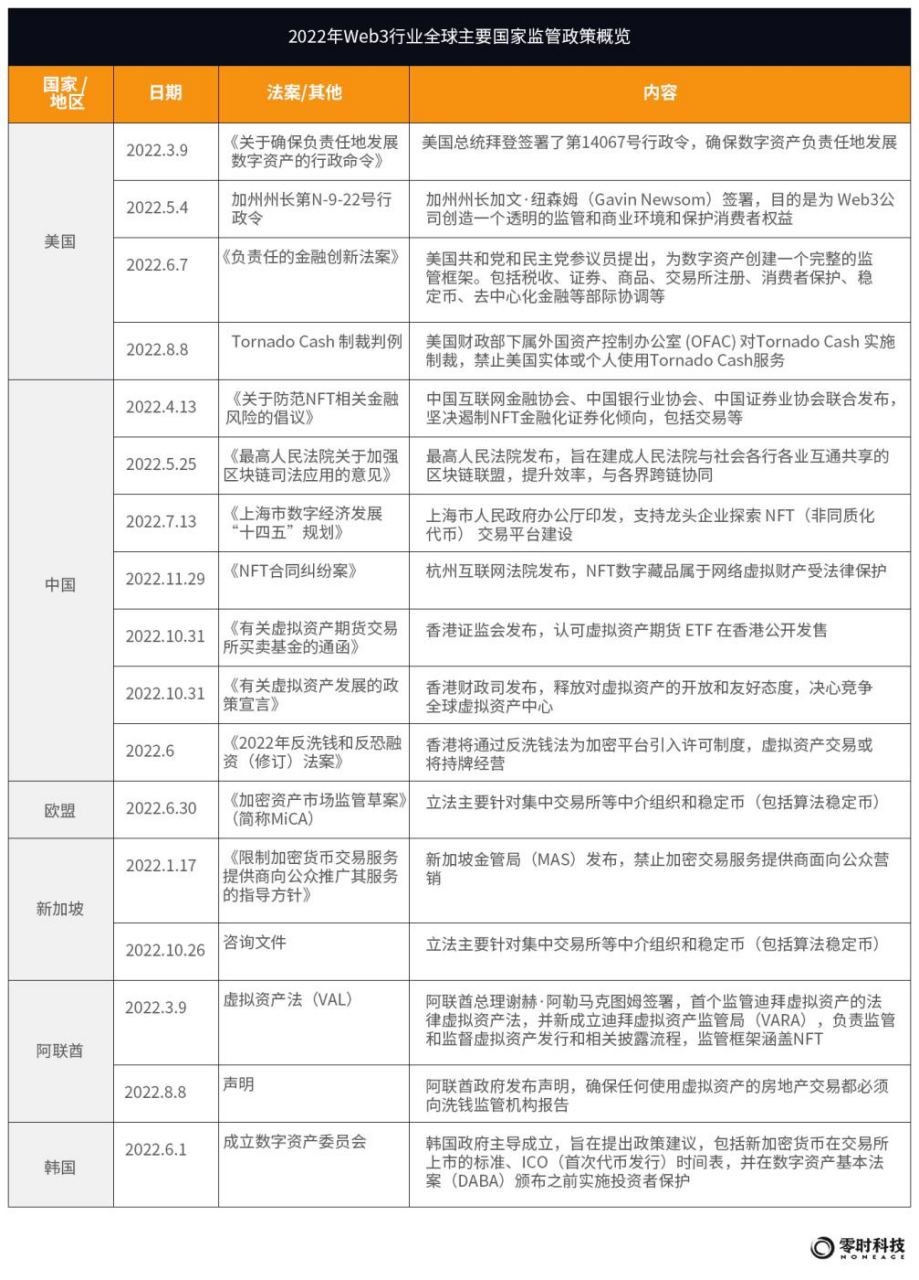
From the perspective of the overall regulatory policy on Web3, investor protection and anti-money laundering (AML) are the global consensus, and the acceptance and supervision of cryptocurrency exchanges vary greatly from country to country. Members of the U.S. Congress proposed "ensure that Web3 takes place in the United States", which is accelerating regulatory innovation; the policies of EU countries are relatively clear and active; Japan, Singapore, and South Korea are affected by the 2022 thunderstorm, and their supervision has become stricter; mainland China still encourages the application of blockchain technology , strictly prohibit financial institutions and payment organizations from participating in virtual currency transactions and illegal fundraising, and increase the crackdown on cryptocurrency crimes. Hong Kong, China fully supports the development of virtual assets and implements a license system; the United Arab Emirates is the most active in the world, embracing encrypted currency assets. For NFT, stable currency, DeFi, asset agreement and DAO fields, the world is in a state of regulatory exploration.
3. The status quo of Web3 ecological security in 2022
Web3 is a relatively special industry. The most prominent feature is the management of a large number of digital encrypted assets. Tens of millions of assets are all stored on the chain, and the rights are confirmed through a unique private key. Whoever holds this private key, Who is the owner of the assets. If an application or protocol in the ecosystem is hacked, it may cause huge losses. With the rapid development of the ecology, various new attack methods and fraud methods emerge in an endless stream, and the entire industry is advancing in the game on the edge of security. The security team of Zero Hour Technology has observed and counted the types of attacks that exist in Web3. At present, the following types of attacks mainly pose threats to Web3 security: APT attacks, social worker phishing, supply chain attacks, flash loan attacks, smart contract attacks, and Web-side vulnerability attacks , zero-day (0 day) vulnerabilities, cyber fraud.
Next, we will analyze the ecological security of Web3 in 2022 from the perspective of infrastructure public chains, cross-chain bridges, application-side APPs and DAPPs: trading platforms, wallets, DeFi, NFT, anti-money laundering in regulatory centers, and web3 security education. The status quo, interpretation of attack events, and suggestions for corresponding security measures for each ecology.
1. Public chain - the lifeblood of Web3 ecological security
The public chain is the infrastructure of the Web3 industry, carrying the protocols, applications and asset accounting of the entire industry. With the industry's strong demand for public chain performance, interoperability, compatibility, and expansion, multi-chain development has shown a strong momentum, and security problem, urgently.
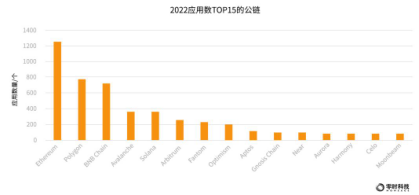
According to the incomplete statistics of Zero Hour Technology, as of December 2022, there are currently 152 public chains. In terms of the number of public chain ecological applications, according to rootdata data, Ethereum has 1,275 applications, Polygon has 767 applications, and BNB Chian has 704 applications, ranking among the top three, closely followed by new public chains such as Avalanche, Solana, and Arbitrum Thereafter, it showed a rapid growth trend.
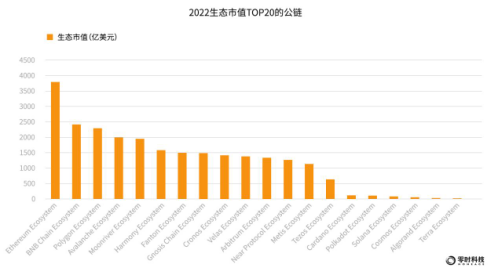
In terms of the market value of the public chain ecology, according to coingecko data, Ethereum, BNB Chain, and Polygon ecology rank in the top three with USD 383 billion, USD 236.6 billion, and USD 219.2 billion, respectively. At present, the total market value of the public chain ecology has exceeded one trillion U.S. dollars. Such a huge temptation of funds has made hackers stare at it.
As of December 2022, according to the statistics of Zero Hour Technology, there have been 10 security incidents on the public chain track, and the cumulative loss of assets has exceeded 157 million US dollars.
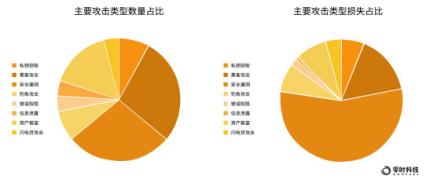
From the perspective of quantity, the attack types of the public chain are mainly: hacker attack, security breach, asset theft, phishing attack and private key theft, and the corresponding proportions are: 28%, 28%, 16%, 8%, 8% . In terms of the amount of losses, security breaches caused the highest losses at $147 million, accounting for 55%; hacking attacks ranked second at $42 million, accounting for 16%. (Note: Some projects are subject to multiple types of attacks)
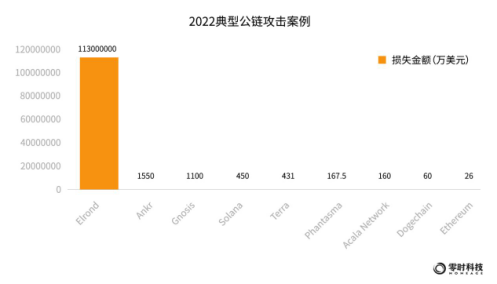
According to the monitoring information of Zero Hour Technology's blockchain security intelligence platform, the following figure shows some typical cases of public chain attacks in 2022:
Public Chain Security Risks and Measures Suggestions
1 )According to the analysis of the security team of Zero Hour Technology, the security risks of the public chain mainly come from the following three points:Technical complexity:
2 )It involves many technical fields and many security risks.Developer Uncertainty:
3 )The code is written by the developer, and it is inevitable that there will be loopholes in the process.Open Source Vulnerability Transparency:
The public chain code is open source, making it easier for hackers to find loopholes.
The security team of Zero Hour Technology has the following three suggestions for the security of the public chain:
1) Before the mainnet goes online, a rich security mechanism needs to be established for each risk point of the public chain:
In terms of P2P and RPC, you need to pay attention to hijacking attacks, denial of service attacks, permission configuration errors, etc.;
In terms of consensus algorithm and encryption, it is necessary to pay attention to 51% attacks, length extension attacks, etc.;
In terms of transaction security, it is necessary to pay attention to fake recharge attacks, transaction replay attacks, malicious backdoors, etc.;
In terms of wallet security, it is necessary to pay attention to the security management of private keys, security monitoring of assets, security risk control of transactions, etc.;
In terms of relevant staff of public chain projects, they need to have a good sense of security, office security, development security and other common sense.
2) Conduct source code and smart contract audits to ensure principled and obvious loopholes are filled:
Source code audit can be full code or partial modules. Zero Hour Technology's security team has a complete set of public chain security testing standards, using manual + tool strategies to test the security of the target code, using open source or commercial code scanners to check code quality, combined with manual security audits, and security vulnerability verification. All popular languages are supported, such as: C/C++/C#/Golang/Rust/Java/Nodejs/Python.
3) After the mainnet goes online, real-time security inspections will be carried out to warn of system risks;
4) After a hacking incident occurs, timely analyze the source through traceability to find out the problem and reduce the possibility of future attacks; quickly track the source and monitor the flow of losses, and recover assets as much as possible.
2. Cross-chain bridge - a new cash machine for hackers
Cross-chain bridges, also known as blockchain bridges, connect two blockchains and allow users to send cryptocurrencies from one chain to the other. Cross-chain bridges enable cross-chain operations of funds by enabling token transfers, smart contracts and data exchanges, and other feedback and instructions between two independent platforms.
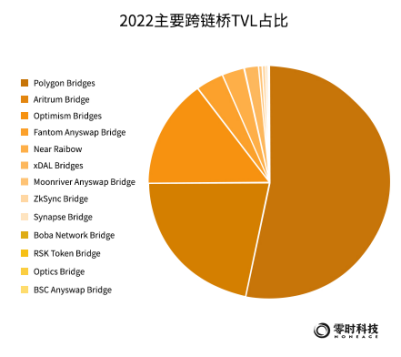
As of December 2022, according to statistics from Dune Analytics, the total value locked (TVL) of major cross-chain bridges in Ethereum is about 5.56 billion US dollars. Polygon Bridges currently has the highest TVL at $2.949 billion, followed closely by Aritrum Bridge at $1.206 billion, and Optimism Bridges ranks third at $834 million.
With the growth of blockchain and programs on the chain, there is an urgent need for multi-chain fund conversion. The synergy feature of the cross-chain bridge can allow each blockchain to exert greater synergy potential. Another door is provided. Due to the characteristics of the cross-chain bridge transfer of assets, once there is a problem in the process of locking, casting, destroying and unlocking, it will threaten the security of user assets. The seemingly uncomplicated cross-chain fund transfer operation, but in multiple cross-chain bridge projects, security vulnerabilities have occurred in different steps.
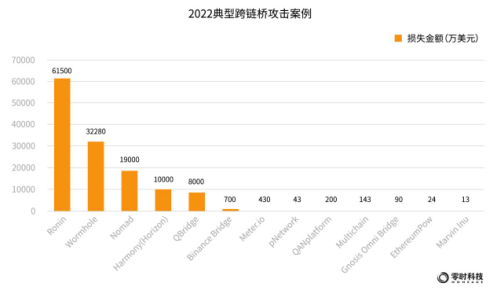
According to the statistics of Zero Hour Technology, as of December, there were 14 security incidents due to attacks on cross-chain bridges, and the cumulative loss of assets amounted to 1.338 billion US dollars.
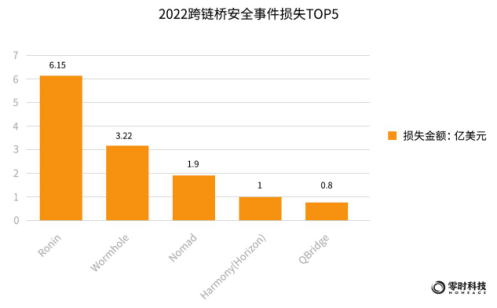
In 2022, the top 5 cross-chain bridges with security incident losses are: Ronin, Wormhole, Nomad, Harmony (Horizon), and QBridge, with respective losses of US$615 million, US$320 million, US$190 million, US$100 million and US$8000 Ten thousand U.S. dollars.
The following figure shows some typical cross-chain bridge attack cases in 2022:
text
Cross-chain Bridge Security Risks and Measures Suggestions
The security team of Zero Hour Technology has learned from multiple attacks on the cross-chain bridge that there are many attacks before the cross-chain and at the signature, and there are stolen incidents caused by official carelessness. For more and more cross-chain projects and project contract security, Zero Time Technology gives the following security measures:
1) Conduct a security audit on the contract before the project goes online;
2) The contract call interface needs to be strictly checked for its suitability;
3) When the version is updated, it is necessary to re-evaluate the relevant interfaces and signature security;
4) Strict review of cross-chain signers is required to ensure that signatures are not controlled by malicious persons.
3. Trading platform - the source of huge temptation
Web3's trading platform, also known as a digital currency exchange or a cryptocurrency exchange, is an important part of the blockchain industry, providing services for transactions between different digital currencies, digital currencies and legal tenders, and is also a digital currency pricing and the main place of circulation.
According to coingecko data, as of December 2022, there are 717 cryptocurrency exchanges, including 553 centralized exchanges with a total 24-hour transaction volume of 54 billion US dollars; 100 decentralized exchanges with a total 24-hour transaction volume There are 64 derivatives exchanges, with a 24-hour trading volume of US$1.78 trillion.
As the world's largest NFT trading platform, Opensea had the highest transaction volume in January, exceeding US$4.85 billion. Due to market conditions, it fell back in December, with a transaction volume of approximately US$138 million. (For more information on the NFT trading platform, see 2.6)
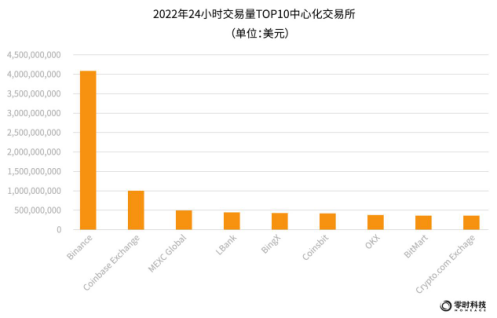
The data shows that the top 10 exchanges by 24-hour trading volume are: Binance, Coinbase Exchange, MEXC Global, LBank, BingX, Coinsbit, OKX, BitMart, Crypto.com Exchange. Among them, Binance ranked first with a trading volume of 4.148 billion in 24.
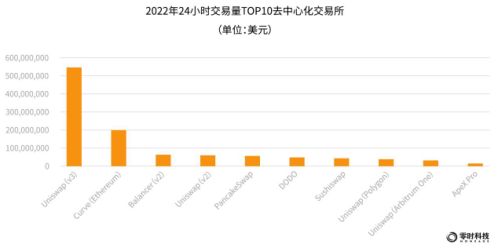
The top 10 decentralized exchanges by trading volume are: Uniswap (V3), Curve, Balancer (V2), Uniswap (V2), PancakeSwap, DODO, Sushiswap, Uniswap (Ploygon), Uniswap (Arbitrum One), Apex Pro, among which Uniswap occupies the top ten by itself.
In 2022, Huobi was acquired, FTX went bankrupt in a confrontation with Binance, and then Binance was revealed to have been under criminal investigation by the US Department of Justice for 4 years, and cryptocurrency exchanges were on the cusp of regulation. Cryptocurrency exchanges bring together encrypted assets from all over the world. Under the huge market influence, whether it is a security crisis or a liquidity crisis, it affects the whole body, and even affects the bulls and bears of the entire encryption market.
According to the statistics of Zero Hour Technology, in 2022, there will be 19 security incidents on cryptocurrency exchanges, and the cumulative loss of assets will exceed 1.192 billion US dollars.
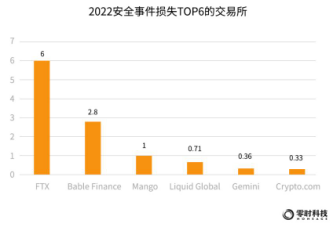
According to the statistics of Zero Hour Technology’s blockchain security threat intelligence platform, in 2022, the top 6 trading platforms with security incident losses are: FTX, Babel Finance, Mango, Liquid Global, Crypto.com, with losses of US$600 million, $280 million, $100 million, $71 million, $36 million and $33 million.
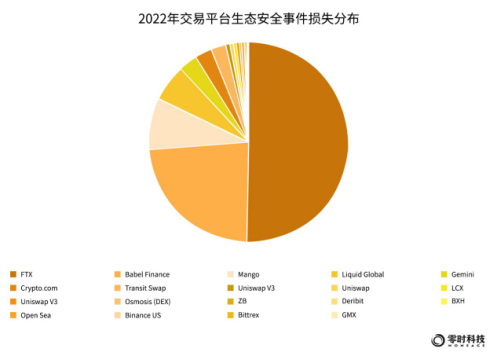
Looking at the distribution of security incident losses on each trading platform, FTX accounted for 50%, Babel Finance accounted for 24%, and Mango accounted for 8%, ranking the top three.
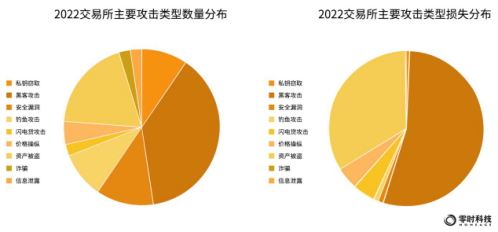
According to the statistics of Zero Hour Technology, from the perspective of the number of security incidents, the types of attacks on trading platforms are mainly hacker attacks, asset theft, security breaches, phishing attacks, and private key theft, accounting for 38%, 19%, 12%, and 10%, 10%. From the perspective of the distribution of the amount of loss, hacker attacks accounted for 54%, which is the main type of security incidents, asset theft accounted for 33%, price manipulation and flash loan attacks accounted for 5% respectively.
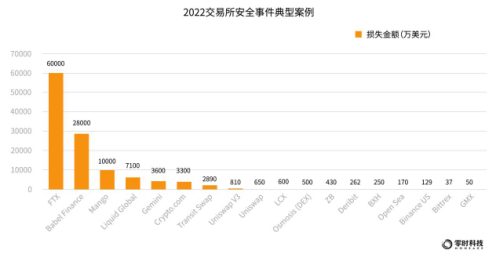
The following figure shows some typical cases of exchange security incidents in 2022:
Trading Platform Security Risks and Measures Suggestions
Reviewing the security incidents of all exchanges in the past, the security team of Zero Hour Technology believes that from the perspective of the overall security structure of a trading platform, the security risks faced by the trading platform mainly include: development, server configuration, operation and maintenance, team security awareness, internal personnel, Market and supply chain risks. The security team of Zero Hour Technology once published "Blockchain Security Introduction and Practical Combat", which conducted a comprehensive and detailed analysis of the security issues of cryptocurrency trading platforms. It includes the steps of penetration testing, such as information collection, social engineering, etc., and also introduces various attack surfaces, such as business logic, input and output, security configuration, information leakage, interface security, user authentication security, App security, etc.
Regarding the security risk of the exchange, the security team of Zero Hour Technology gives the following measures and suggestions:
From the perspective of the trading platform:
1) Cultivate the security awareness of internal personnel, strengthen the security isolation of the exchange's production environment, testing environment and debugging environment, and use professional network security protection products as much as possible.
2) Through cooperation with professional security companies, code audits and penetration tests are conducted to understand whether there are hidden vulnerabilities and security risks in the system, and to establish a complete and comprehensive security protection mechanism. During daily operations, regular security tests are carried out to strengthen security reinforcement.
In addition to using exchanges for transactions, most users more often act as wallets to store digital assets.
therefore,therefore,
From the user's point of view:
1) Do not install software from unknown sources at will.
2) The computer server should avoid opening unnecessary ports, and the corresponding vulnerabilities should be patched in time. It is recommended to install effective and reliable anti-virus or other security software on the host, and install mining script isolation plug-ins on the WEB browser.
3) Do not click on unknown links sent by strangers at will.
4. Wallet - the injury of encrypted asset management
Web3's wallet is a blockchain digital wallet, also known as a cryptocurrency wallet or a digital asset wallet. It is a tool for storing, managing, and using digital currency. It plays a pivotal role in the blockchain field and is the entrance for users to access digital currency. Today, with the development of the ecology, digital wallets have become a multi-chain and multi-asset management platform.
According to statistics from the Zero Hour Technology Blockchain Security Threat Intelligence Platform, as of December 2022, there are a total of 142 digital wallet projects. According to statistics from Blockchain.com, more than 300 million people around the world will be using encrypted assets in 2022. Among them, the number of users with encrypted wallets will reach 68.42 million in 2021, and by July 2022, the number of encrypted wallet users has reached 81 million, and the number is growing exponentially.
As the entrance of Web3, the wallet has already become the "meat and potatoes" in the eyes of hackers. According to the statistics of Zero Time Technology, in 2022, there will be 25 security incidents in digital wallets, and the cumulative loss of assets will exceed 698 million US dollars.
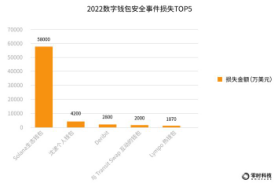
In 2022, the top 5 wallet security incidents that were attacked and lost mainly came from: Solana ecological wallet, Fenbushi founder Shen Bo’s personal wallet, Deribit, wallets interacting with Transit Swap, and Lympo hot wallet. The respective losses were: 580 million US dollars , $42 million, $28 million, $20 million and $18.7 million. Among them, the Solana ecological wallet was attacked and lost the highest amount.
According to the statistics of Zero Hour Technology, from the perspective of the number of security incidents, the main types of attacks on digital wallets are: hacker attacks, asset theft, private key theft, security breaches and information leakage, accounting for 38%, 30% and 13% respectively , 7%, 6%. Attacks accounted for the highest proportion, ranking first.
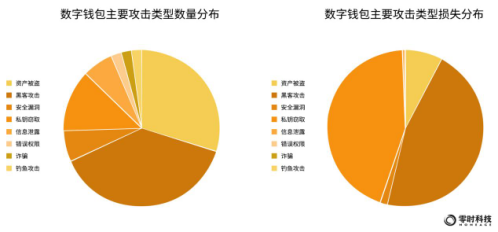
Among them, the proportions of security incident losses corresponding to the main attack types are as follows: hacker attacks caused the highest loss, accounting for 46%; private key theft caused losses second, accounting for 44%; asset theft ranked third, accounting for 8% % .
Wallets are attacked, generally divided into two situations. One is an institutional wallet and the other is a personal wallet. For example, the Lympo hot wallet was stolen, with a loss of US$18.7 million, and the classic personal wallet was stolen recently. Shen Bo, the founder of Fenbushi Capital, had his personal wallet assets worth US$42 million stolen.
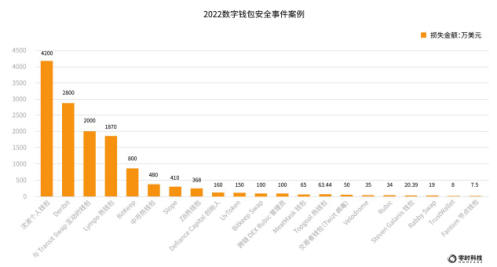
In addition to the stolen case of the Solana ecological wallet, there are many wallet security incidents in the industry, as shown in the figure below.
Digital Wallet Security Risks and Measures SuggestionsAccording to the analysis of the security team of Zero Hour Technology, there are many forms of blockchain digital wallets.
The main security risks include but are not limited to the following aspects:On the institutional side:
Security risks of the operating environment, security risks of network transmission, security risks of file storage methods, security risks of the application itself, security risks of data backup, etc.On the client side:
Facing loss or theft of private keys: For example, pretending to be customer service to cheat private keys, hackers collect user mnemonic words and other information through targeted attacks through wallet upgrades, sending malicious QR codes to guide customers to transfer funds to steal assets, and stealing by attacking the cloud platform where customers store information Take private key/mnemonic phrase, malware, airdrop spoofing, phishing, other phishing (pre-sale, APP download, lottery trap) and other risks.
How to protect wallet security in the face of these risks?
From the institutional side, the security team of Zero Hour Technology recommends:
Whether it is a centralized or decentralized wallet, a software wallet or a hardware wallet must have sufficient security testing in terms of security. For the security audit of digital wallets, the security team of Zero Hour Technology includes but is not limited to the following test items:
1. Network and communication security testing. Network nodes should be able to detect and resist network attacks in a timely manner;
2. The wallet operating environment is safe. The wallet can detect known major vulnerabilities of the operating system, virtual machine detection, and integrity detection; the digital wallet must have a third-party program hijacking detection function to prevent third-party programs from hijacking the wallet to steal relevant user information .
3. Wallet transaction security. All transactions issued by the wallet must be signed. When signing, the private key must be decrypted by entering the payment password. After the transaction signature is generated, the decrypted private key in the memory must be cleared to prevent the private key in the memory from being stolen and leaked wait.
4. Wallet log security. In order to facilitate users to audit wallet operation behavior and prevent abnormal and unauthorized operations, it is necessary to record wallet operation logs. At the same time, wallet logs must be desensitized and must not contain confidential information.
5. Node interface security audit. The interface needs to sign the data to prevent hackers from tampering with the data; interface access needs to add a token authentication mechanism to prevent hackers from replaying attacks; the node interface needs to limit the user connection rate to prevent hackers from simulating users Operation to perform CC attack.
For the client side, the security team of Zero Hour Technology recommends:
1) Do a good job of private key storage measures: For example, try to copy and back up the private key by hand, or use social networks such as cloud platforms and emails to transmit or store the private key.
2) Use a strong password, and enable two-step verification MFA (or 2 FA) as much as possible, and keep security awareness and vigilance at all times.
3) Pay attention to verify the hash value when updating the program version. Install antivirus software and use a firewall if possible. Monitor your account/wallet to make sure there are no malicious transactions.
4) Among them, the hardware wallet is suitable for users with a large amount of digital assets and a higher level of security protection. The usual suggestion is to use software wallets to save your small assets for daily use, and hardware wallets to save large assets, which can achieve both convenience and security.
What if funds are stolen?
If an unintentional authorization operation occurs, transfer the funds out of the wallet as soon as possible before the funds are stolen, and cancel the authorization; if the funds after authorization have been stolen or the private key has been stolen, please contact Zero Time Technology Security immediately The team conducts asset tracking.
5. DeFi-Web3 security hardest hit area
The full name of DeFi: Decentralized Finance, generally translated as distributed finance or decentralized finance. DeFi projects are roughly divided into five categories: oracle machines, DEX, mortgage lending, stable currency assets, and synthetic derivatives.
The full name of TVL: Total Value Locked is the total locked value. The total value of assets pledged by users is one of the most important indicators to measure the development of the DeFi ecosystem. Usually, the growth of TVL means the better the development of the project.
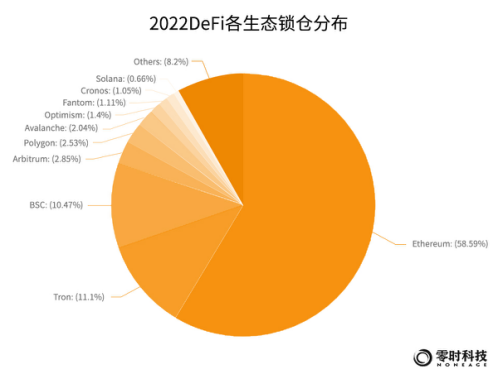
According to the statistics of Zero Hour Technology's blockchain security threat intelligence platform, as of December 2022, there are a total of 1,297 DeFi projects. According to DeFi Llama data, the total lock-up value of DeFi reached 39.051 billion US dollars. Among them, Ethereum accounted for 58.59%, ranking first with a TVL of US$23.02 billion, followed by Tron, accounting for 11.1%, ranking second with a TVL of US$4.036 billion, followed by BSC, accounting for 10.47%, and ranking second with a TVL of 40.12 100 million US dollars TVL ranked third. Many emerging public chains such as Avalanche, Ploygon, Optimism, etc. have rapidly developed the ecosystem on the chain by embracing DeFi, and have also attracted a large number of users and capital accumulation.
DeFi's prominent smart contract security issues have become the biggest challenge for the DeFi industry. Furthermore, no DeFi service provider or regulator can return funds that were transferred in error. When hackers discover loopholes in smart contracts or other aspects of DeFi services to steal user assets, there may not be a DeFi service provider to compensate investors. In addition, many hidden interconnection problems may cause a series of financial accidents.
According to the statistics of Zero Hour Technology, as of December 2022, there have been 25 DeFi security incidents, with a cumulative loss of assets exceeding US$593 million.
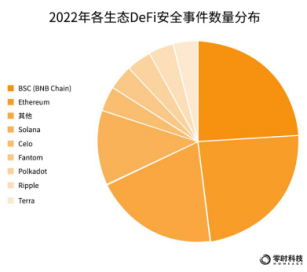
Judging from the distribution of the number of DeFi security incidents that occurred in each ecosystem, the Ethereum and BSC (BNB Chian) ecosystems had 6 incidents each, accounting for 24%, ranking first, and the Solana ecosystem had 3 incidents, accounting for 12%, ranking first. second.
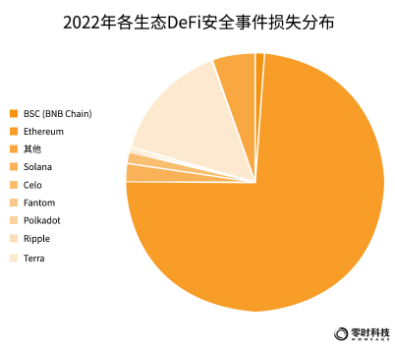
In terms of the loss distribution of security incidents in each DeFi, the top three public chain ecology is that the Ethereum ecological DeFi event lost more than 438 million US dollars, accounting for 74%, ranking first; Terra ranked second, with a loss of 9000 million, accounting for 15%; Solana ranked third, with a loss of US$13.54 million, accounting for 2%. It can be seen that the more active the ecology is, the more hackers pay attention to it, and the losses are the most prominent.
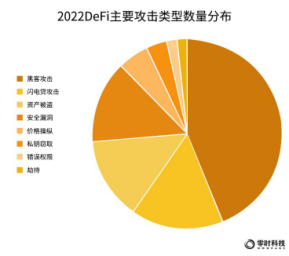
According to the statistics of Zero Hour Technology, from the perspective of DeFi attack types, the main types are: hacker attacks, flash loan attacks, asset theft and security breaches. Among them, the distribution of the number of security incidents corresponding to each major attack type is as follows: hacker attacks accounted for 44%, ranking first; lightning loan attacks accounted for 16%, ranking second; asset theft and security breaches both accounted for 14% , tied for third.
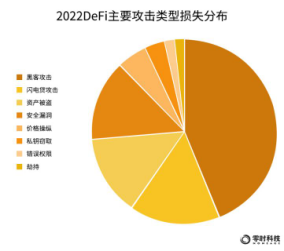
From the perspective of the distribution of losses by major attack types, hacker attacks caused the highest losses, accounting for 53%, followed by security breaches, accounting for 25%, and assets ranked third, accounting for 17%.
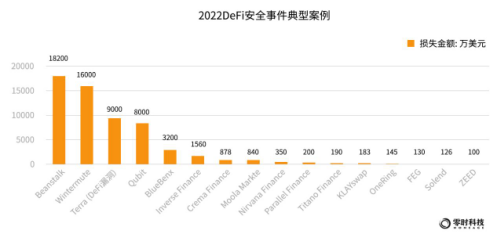
The figure below shows some typical cases of 202 2DeFi security incidents:
DeFi Security Risks and Measures Suggestions
DeFi projects face multiple security risks. From the group, they are the project side (protocol execution) and the user side; from the security type, they are the combined security between the protocols, including some defects between the combinations, Smart contract security, open source security, high returns are accompanied by high risks, and some security issues caused by lack of supervision.
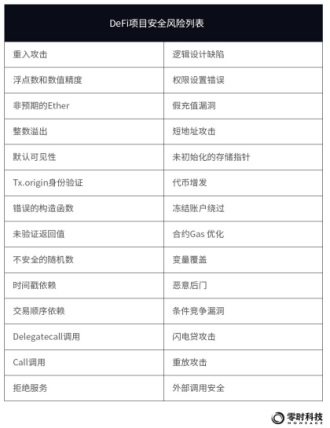
From the perspective of security audit, the risks faced by DeFi projects are shown in the figure below:From the protocol execution process, DeFi risks include:
Smart contract attack risk, design issues in economic incentives, custody risk, reconstruction of the original protocol, lack of privacy and other risks.From a user perspective, the risks faced by DeFi users include:
Technical risk: There are loopholes in the smart contract, which are subject to security attacks; Liquidity risk: The liquidity of the platform is exhausted; Key management risk: The master private key of the platform may be stolen. Security awareness risks: being phished, encountering arbitrage and fraudulent projects, etc.
The security team of Zero Hour Technology recommends that as a project party and user, you can deal with risks from the following five points:
1) When the project party launches a DeFi project, it must find a professional security team to do a comprehensive code audit, and try to find as many joint audits as possible to find as many project design defects as possible, so as to avoid unnecessary problems after the launch. Loss.
2) It is recommended that users must do a good job of checking when investing in these projects. They must have a certain understanding of this project, or check whether it has passed a security audit before going online.
3) Increase personal security awareness, including habits such as surfing the Internet, saving assets, and using wallets, and develop good security awareness habits.
4) Projects are high-yield and high-risk. Participation needs to be cautious. If you don’t understand the project, try not to participate to avoid losses.
6. NFT - the pond of phishing attacks
NFT is the abbreviation of Non-Fungible Token. It is a non-homogeneous token based on the blockchain. At the same time, it is a unique digital asset stored on the blockchain. It is often used as an electronic certification or certificate of virtual commodity ownership. Can be bought or sold. On December 15, 2022, former US President Trump announced the launch of a series of NFT digital collections printed with Trump's portrait, and 45,000 pieces were sold out in less than 24 hours.
According to NFTgo data, as of December 31, 4,624 NFT projects have been included, with a total of 38,693,506 NFTs. At present, the total market value of NFT has reached 21 billion US dollars, and the number of holders has reached 3.7338 million. Judging from the market value distribution of various projects, PFP (Picture for proof), that is, the market value of personal profile picture NFT is far ahead. This is also the NFT with the most usage scenarios at present, followed by collectibles. Looking at NFT assets and contracts from the current eight mainstream public chains, Polygon is far ahead in the number of assets and contracts.
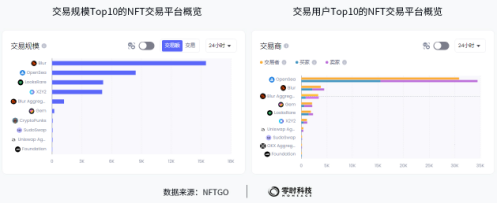
From the perspective of transaction scale: Among the top 10 NFT trading platforms by sales within 24 hours, Blur ranks first, followed by Opensea, and LooksRare ranks third. From a trader perspective, among the top 10 marketplaces by number of traders, buyers and sellers within 24 hours, Opensea is number one, Blur is number two, and Blur aggregator is number three.
As the value of NFT becomes prominent, hackers are also eyeing this piece of fat. Although the entire encryption market is currently experiencing a violent downward trend, the popularity of NFT has not diminished.
According to incomplete statistics from Zero Hour Technology, as of December 2022, there have been a total of 44 security incidents on the NFT track, with a cumulative loss of assets of approximately US$42.56 million.
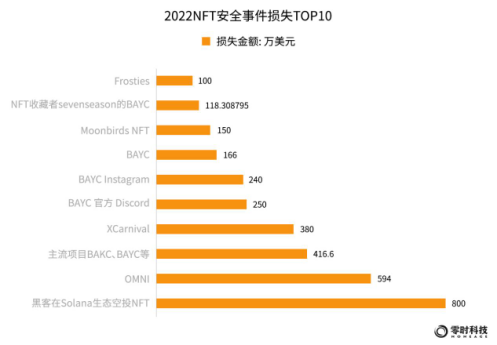
In 2022, among the top 10 NFT security incident losses, BAYC and BAKC series have become the main targets of hackers, and collectors holding such NFTs have suffered greater losses. Among them are hot events such as the theft of Jay Chou's NFT and the loss of 540,000 US dollars.
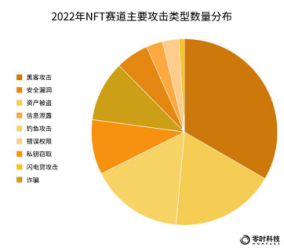
From the perspective of the types of attacks on the NFT track, they are mainly: hacker attacks, asset theft, phishing attacks, and private key theft. The corresponding security incidents accounted for 33%, 18%, 16%, and 10% respectively.
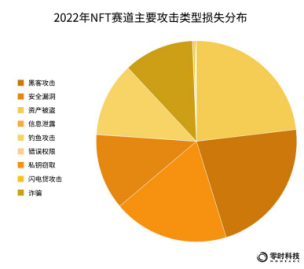
From the perspective of the proportion of losses in the main types of NFT attacks, asset theft caused the most losses, accounting for 23%; hacking attacks took second place, accounting for 22%; private key theft ranked third, accounting for 19%. It is worth noting that, in terms of personal theft incidents, most of them are due to hackers posting phishing links after Discord/Twitter and other media platforms were hacked.
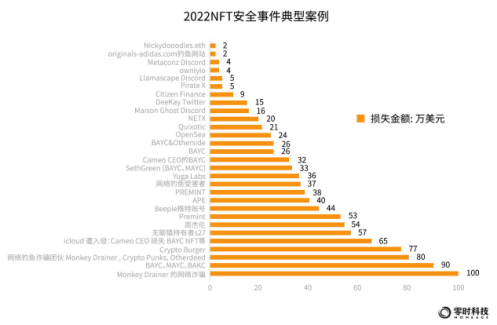
In addition to the top 10 NFT security incident cases, typical NFT security incident cases in the industry are as follows:
NFT Security Risks and Measures Suggestions
At present, in the NFT track, there are various ways of hacking. Divided by groups, the objects at risk are generally platforms and users.For the centralized platform side, the possible security risks are:Account risk, commercial competition risk, security awareness risk, insider risk, market risk, etc.
On the client side, Discord attacks have become the main attack method this year.
Regarding the above security risks, Zero Hour Technology security team gives the following suggestions:for normal users
, to protect your own Discord, you need to pay attention to the following points:
Make sure your passwords are strong enough, create long random passwords with alphanumeric special characters; turn on 2 FA authentication, passwords themselves are complex enough but cannot be relied upon to be secured in one way; do not click on links from unknown senders or that look suspicious, consider Limit who can private message you; don't download programs or copy/paste codes you don't recognize; don't share or screen share your authorization token; don't scan any QR codes from people you don't know or whose legitimacy you can't verify .For server owners:
Audit your server permissions, especially for higher level tools like webhooks; keep official server invites updated and visible on all platforms when making any changes, especially as most new server members come from communities outside of Discord; Likewise, don't click on suspicious or unknown links! If an account is compromised, it may have an even greater impact on the managed community.For projects:
It is recommended that the contract should strictly judge the rationality of the purchase quantity entered by the user; it is recommended that the contract limit the possibility of purchasing NFT with zero funds; it is recommended to strictly distinguish the NFT Token of the ERC 721 and ERC 1155 protocols to avoid confusion and fake Discord official cases. At present, many chat software will find malicious mint links, and many users' funds have been stolen. In order to avoid such coin theft incidents, it is recommended that you verify the reliability of the source of the link when performing mint operations, and at the same time ensure that the content of the actual signed transaction and As expected.
7. Virtual currency - a breeding ground for illegal activities
In September 2022, the police in Hengyang County, Hunan Province cracked the "9.15" extraordinarily large virtual currency money laundering case involving 40 billion yuan. In December 2022, the Horqin Branch of the Public Security Bureau of Tongliao City, Inner Mongolia successfully uncovered a money laundering gang that used the blockchain network to exchange digital virtual currency, and arrested 63 suspects, involving a total amount of 12 billion yuan. On August 8, 2022, the Office of Foreign Assets Control of the US Department of the Treasury (OFAC) announced sanctions on the Tornado Cash agreement. According to the disclosure of the US Department of the Treasury, since its establishment in 2019 , Tornado Cash has helped launder over $7 billion.
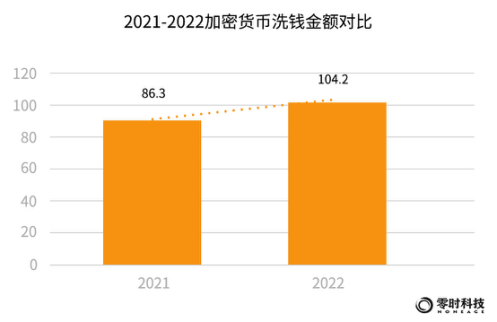
According to incomplete statistics from Zero Time Technology, the amount of money laundered through cryptocurrencies will reach US$10.42 billion in 2022, a year-on-year increase of 20.7%. In 2022, the domestic public security departments cracked a number of virtual currency money laundering cases, and the number of cases showed an increasing trend. Money laundering, fraud, pyramid schemes, and theft are the main types of cryptocurrency crimes.
How to combat and defend against crimes based on virtual currency?
Zero Hour Technology has independently developed a virtual currency traceability analysis platform, which has four major systems: intelligence system, monitoring system, KYC&KYT and traceability system. Based on the data on the chain and the security intelligence of the blockchain, the platform enables the traceability of the entire virtual currency chain to be automatically operated and visualized through technologies such as big data, graph computing, and machine learning. It can effectively assist in case investigation, combat virtual crimes, and provide virtual asset tracing services for victims in the industry. Currently, the platform has analyzed 1.77 billion transactions, marked over 80 million addresses, and analyzed over 850 million addresses. And assisted Shenzhen Public Security Bureau, Chongqing Municipal Public Security Bureau, Tongchuan Municipal Public Security Bureau, Shangluo City Public Security Bureau and Shangzhou Public Security Bureau, etc., to crack many cases of virtual currency gambling, pyramid schemes, and fraud, which aroused strong repercussions in the industry.
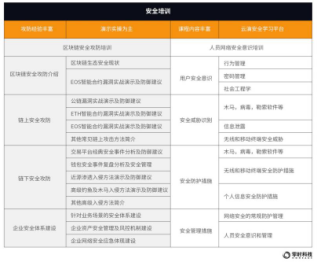
8. Security Education - Web3 Security Shield
The well-known case of all Sohu employees suffering wage subsidy phishing email scams has made many companies realize that if the awareness of network security is not improved, various security incidents such as commercial secrets in the future will inevitably affect the development of enterprises. Web3's decentralized and self-organized participation method makes individuals realize that if they do not improve their security awareness, they will become cash machines for hackers.
In addition, Zero Hour Technology has also self-developed a security awareness assessment management platform, mainly for industry organizations including government, public security, education, finance, electric power, etc. that have needs for network security awareness. The network security awareness assessment platform is based on phishing technology. , to help enterprises build a private cloud-based network security awareness assessment and management platform, integrating theoretical systems, phishing drills, host detection, management assessment, and scene customization systems, so as to realize the continuous and systematic improvement of the network security awareness of all employees in enterprises. In addition, based on the professional strength of the zero-hour technology security team, it also provides enterprise network security consulting and training services, and builds a solid security shield from the source.
first level title
4. Detailed analysis of attack methods of Web3 hotspot security incidents and suggestions for measures
1 Ronin Network side chain stolen 625 million US dollars flow analysis
0x1 event overview
Zero Hour Intelligence Station reported that on March 29th, the Axie Infinity sidechain Ronin validator node and the Axie DAO validator node were compromised, resulting in the bridging of 173,600 Ethereum and $25.5 million from Ronin in two transactions USDC, the current Ronin Bridge and Katana Dex have been discontinued. The following is the attacker’s wallet address: https://etherscan.io/address/0 x 098 b 716 b 8 aaf 21512996 dc 57 eb 0615 e 2383 e 2 f 96 . At present, the hacker has converted all USDC into ETH, distributed 6250 ETH, transferred 3750 ETH to Huobi, transferred 1220 ETH to FTX, and transferred 1 ETH to Crypto.com. The source of 1 ETH is Binance, and the remaining fund balance still stays in the hacker's address. The source of funds for the hacker's attack was the withdrawal of Binance.
0x2 event principle
Ronin adopts a simple asset cross-chain mode. Users transfer Ethereum assets to Ronin through the Ronin cross-chain contract. The contract is confirmed and released to the user's corresponding assets on Ronin. When the user destroys the corresponding assets on Ronin, the Ethereum side will unlock the initially locked assets and return them to the user.
The Ronin chain of Sky Mavis currently consists of 9 validators. In order to identify a deposit event or a withdrawal event, five of the nine validator signatures are required. The attackers managed to take control of four of Sky Mavis's Ronin validators and a third-party validator run by Axie DAO.
The validator key scheme is set to be decentralized, which limits attack vectors similar to this one, but the attacker found a backdoor through Ronin's Gasless RPC node to obtain the signature of the Axie DAO validator.
Back in November 2021, when Sky Mavis asked Axie DAO to help distribute free transactions due to the huge user load. Axie DAO allows Sky Mavis to sign various transactions on its behalf. This was discontinued in December 2021, but allowlist access was not revoked.
Once the attackers gained access to the Sky Mavis system, they were able to obtain signatures from the Axie DAO validators by using gasless RPC.
Officials have now confirmed that the signatures in the malicious withdrawals match five suspicious validators.
0x3 Source and destination of funds
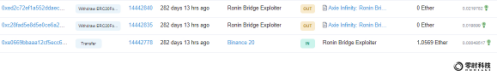
The attacker obtained the initial fund of 1.0569 ETH through the Binance exchange address, and then called the Ronin Bridge cross-chain bridge contract to obtain 173,600 ETH and 25,500,000 USDC.
whereabouts of funds
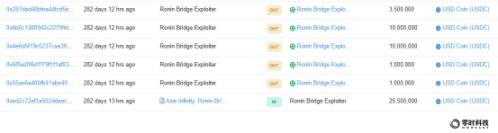
The attacker transferred 25,500,000 USDC to addresses 0xe708f... 7ce10 and addresses 0x66566... 55617 in five separate transactions, and exchanged them to obtain about 8564 ETH.
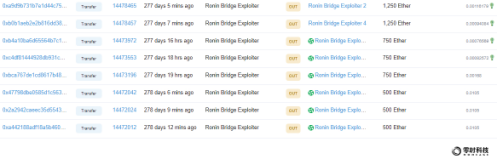
The attacker then transferred 6250 ETH to 5 addresses, and other funds are still in the attacker's wallet address.
To track the wallet funds that have been transferred out so far:
The hacker transferred 3,750 ETH to the Huobi Huobi address.
The hacker transferred 1250 ETH to the FTX Exchange exchange address.
The hacker transferred 1 ETH to the Crypto.com address.
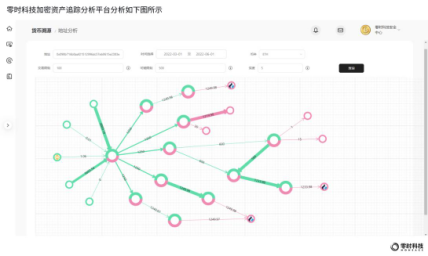
The analysis of Zero Hour Technology's encrypted asset tracking and analysis platform is shown in the figure below:
Summary and Recommendations:
The security team of Zero Hour Technology will continue to monitor the transfer of stolen funds, and once again remind exchanges and wallets to pay attention to strengthening address monitoring to prevent related malicious funds from flowing into the platform.
2 Beware of malicious chat software! Chat records were hijacked and lost tens of millions of assets tracking analysis
event background
Recently, the security team of Zero Time Technology received a large number of users who caused the theft of encrypted assets due to the same reason. After investigation, it was all due to the use of malicious Whatsapp in the process. Through communication with the victims, the situation is as follows:
When using malicious Whatsapp to communicate, the victim sends the wallet address to the chat software, and the other party directly copies the wallet address for transfer, but at this time the copied wallet address has been maliciously replaced by the chat software Whatsapp, resulting in the transfer of encrypted assets to the wrong address. It then replaces the correct cryptocurrency address entered or received by the user when the user chats with the malicious WhatsApp.
On December 6, 2022, more than $80,000 was stolen due to the use of malicious WhatsApp;
On November 21, 2022, more than $1.4 million was stolen due to the use of malicious Whatsapp;
On October 6, 2022, more than $13,000 was stolen due to the use of malicious WhatsApp;
other……
Malware Analysis and Countermeasures
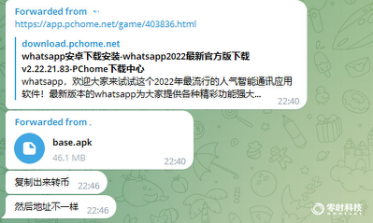
Through communication with the victim, the Android mobile phone they used, and after searching the WhatsApp software from Baidu, downloaded the software directly from a third-party website and installed it.

The download address is as follows:
Through communicating the cause and effect of this incident, we suspected that there was a problem with the WhatsApp installed by the victim, so in order to restore the incident, we obtained the malicious WhatsApp installation package at the time of the incident and analyzed it.
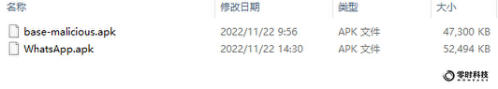
First, the size of the installation package of the malicious WhatsApp software is inconsistent with the size downloaded from the WhatsApp official website:
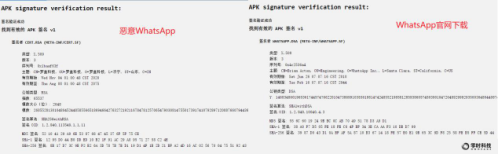
And by looking at the signature messages of the two software, it can be seen that the signature time and the signature subject message are also obviously inconsistent:
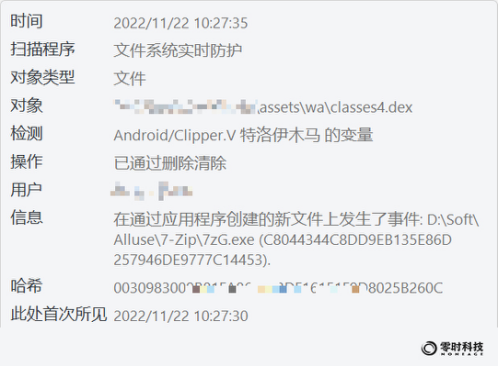
Scanning this malware with security tools found that there is indeed a problem and is marked as a malicious Trojan:
Then, after decompiling the malware, it was found that the malware had the function of replacing the encrypted currency address in the user’s chat message, and communicated through the remote server to regularly change the replaced hacker address. The analysis process is as follows:
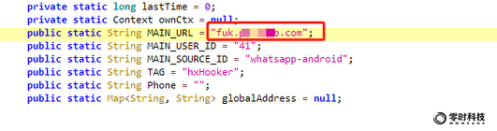
First, we found the domain name of the background server controlled by malware and hackers:
Then, by auditing the malware code, it was found that the malware obtained the encrypted currency address from the server controlled by the hacker, and then replaced the correct encrypted currency address entered or received by the user when the user chatted with the malicious WhatsApp.
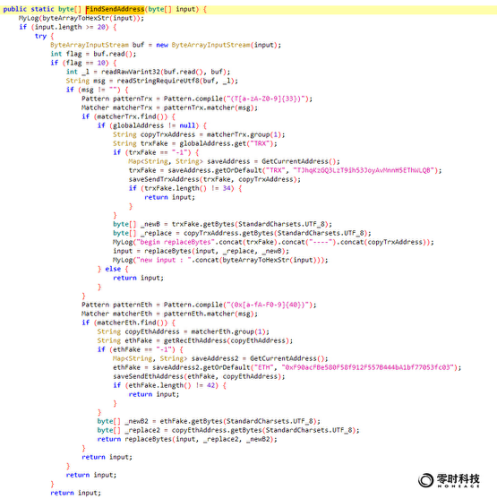
Let's take a look at the process of replacing the address message entered by the user when chatting. The code is as follows:
As can be seen from the FindSendAddress function above:
The first step is to match whether there is a trx or eth address in the chat message entered by the user;
The second step is to obtain the address through the GetCurrentAddress function;
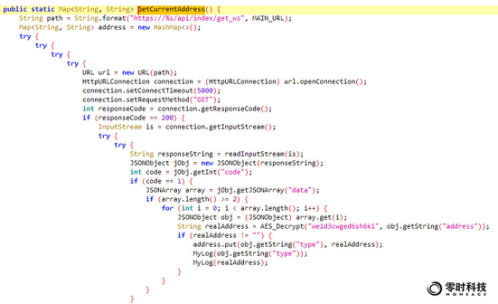
To follow up, the content of the GetCurrentAddress function is as follows:
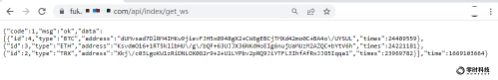
Obtain the address controlled by the hacker through the /api/index/get_ws interface of the malicious site.
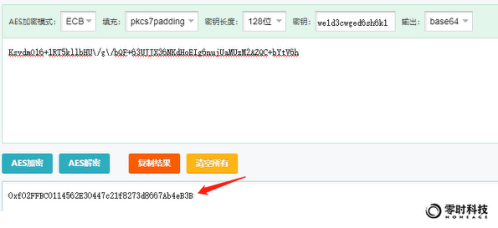
The return address is encrypted. Through the encryption key in the app, the hacker's address can be decrypted directly using the AES algorithm. Taking the ETH address as an example, the decryption is as follows:
The third step is to replace the address entered by the user with a malicious address controlled by the hacker through the replaceBytes function.
Through testing, it is found that the malicious address obtained through the /api/index/get_ws interface of the malicious domain name will change irregularly. The currently obtained address has been updated and is not the address of the victim when transferring money. The currently obtained new address is 0xf02FFBC0114562E30447c21f8273d8667 Ab 4 eB 3 B No funds received from victim
As of now, this malicious interface /api/index/get_ws is still working and will cause more victims.
Lost funds tracking analysis
After receiving the victim's request for assistance, the security team of Zero Hour Technology immediately analyzed and monitored the addresses related to the hacker.
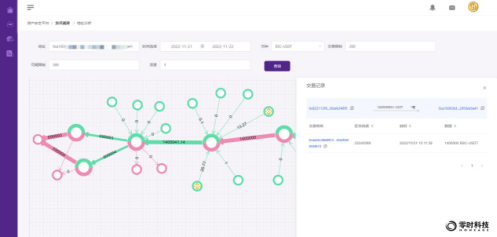
Among them, 1.4 million US dollars of stolen funds entered the hacker's address 0xa160...9a41. After a few hours, the hacker transferred the funds to the address 0x570C...BdDb, and then transferred the two addresses through multiple transactions, and finally pooled them to the address 0x8785...8885 ,As shown below:
Through analysis, it is found that the handling fee of the hacker address 0xa160...9a41 comes from the Binance trading platform, and the handling fee of the transferred address 0x570C...BdDb comes from the mexc.com trading platform.
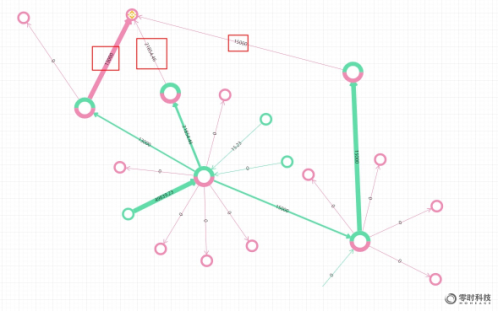
Another $80,000 stolen funds entered the hacker's address 0x319c...8486, 0xad8...95b9, and then transferred through multiple scattered transactions, and finally gathered to the Binance trading platform. Through analysis, it was found that the transaction fee of the hacker's address also came from the Binance transaction. platform, as shown below:
The security team of Zero Hour Technology will continue to pay attention to the spread of this malicious chat software, monitor the fund transfer dynamics of relevant hacker wallet addresses, provide timely intelligence warnings, and prevent more user assets from being stolen.
summary advice
In this case, the victim downloaded the malicious WhatsApp chat software, which resulted in the tampering of the transfer target address and the loss of a large amount of funds. There are many similar cases, such as through malicious fake trading platforms, fake wallets, fake Telegram, etc.
The security team of Zero Hour Technology has received a large number of requests for assistance in the loss of user assets, and found that there are more and more cases of interception and modification of transfer addresses through social software and other malicious software. In order to avoid financial losses, here we recommend again:
First, when downloading and using the APP, multiple confirmations are still required, look for the official download channel, and check the signature consistency;
Second, large-amount transfers are carried out multiple times, first confirm the transfer status of the small amount, and then continue the transfer;
Third, confirm the transfer address multiple times when transferring money, including checking the correctness of the address, and try to check every character.
3 Analysis and Tracking of the Stolen Assets of the Founder of Fenbushi Capital’s $42 Million
event background
On November 23, 2022, Shen Bo, founder of Fenbushi Capital, tweeted that $42 million worth of personal wallet assets were stolen, including 38 million USDC and 1,606 ETH, in the early hours of November 10, New York time. The stolen assets are personal funds and have nothing to do with distributed related funds. The case has been reported locally, and both the FBI and lawyers have been involved.
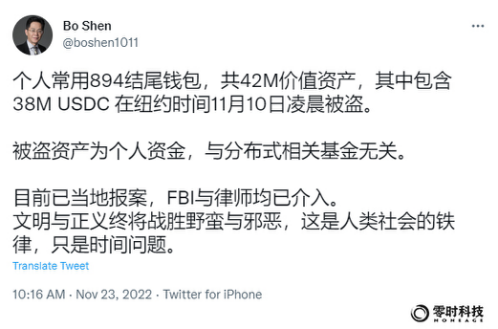
After the security team of Zero Hour Technology monitored the news, it followed up and analyzed it in time.
Note: Mr. Shen Bo is an early investor in Ethereum and an early preacher of Ethereum. Founded in 2015, Fenbushi Capital is China's first venture capital company that focuses on investing in blockchain technology-related companies.
event analysis
0x6be85603322df 6 DC 66163 eF 5 f 82 A 9 c 6 ffBC 5 e 894
The wallet address of Mr. Shen Bo, the victim of this security incident, is:
0x24b93eed37e6ffe948a9bdf365d750b52adcbc2e
The attacker's wallet address is:
0xf6ff8f672e41b8cfafb20881f792022f6573bd9fbf4f00acaeea97bbc2f6e4f7
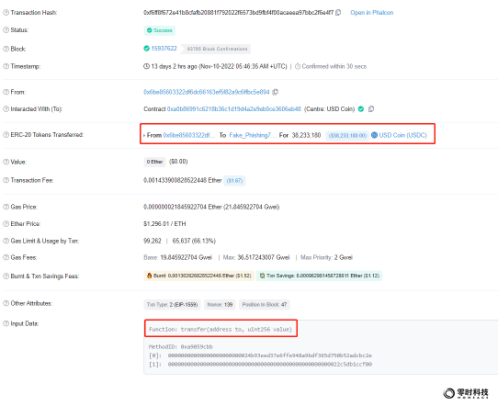
The stolen 38, 233, 180 USDC are directly transferred out through the transfer function, and the transaction hash is:
0 xbc 9 ce 2 f 860 ee 2 af 834662782 d 30452 a 97 eb 3654 ecaf 9 c 4 d 00291 d 1233912 a 3 f 5
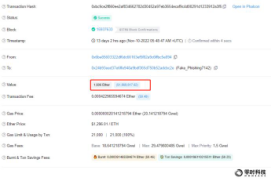
The stolen 1606 ETH transaction hash is:
0x04c43669c930a82f9f6fb31757c722e2c9 cb 4305 eaa 16 baafce 378 aa1c09 e 98 e
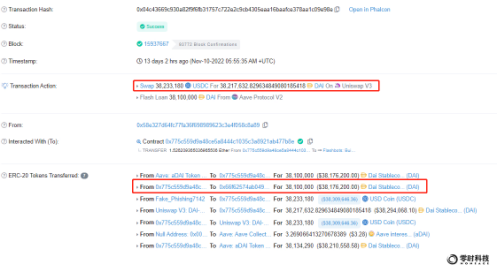
Then the attacker exchanged 38, 233, 180 USDC for DAI, and the transaction hash is:
0x66f62574ab04989737228d18c3624f7fc1edae14
The exchanged 38,100,000 DAI were sent to another address, which has not been transferred yet. The address is as follows:
Through analysis, it is found that the address 0x66f62574ab04989737228d18c3624f7fc1edae14 receiving DAI received a transaction fee of 0.1594 ETH from the address 0x077d360f11d220e4d5d831430c81c26c9be7c4a4, and it was marked by the Zero Time Technology Virtual Currency Analysis Platform 0x077d360f11d220e4d5d831430c81c26c9be7c4a4 is the address of the ChangeNow exchange platform, which is used by attackers to cover up transaction traces Behavior.
At present, 38,100,000 DAI and 1,606 ETH are still in the attacker's address and have not been transferred. The security team of Zero Hour Technology has joined the monitoring list and continues to track the asset transfer dynamics.
summary advice
First of all, the asset theft incident was directly transferred through the victim’s wallet, so it is suspected that the private key of the wallet was leaked, and then the attacker converted USDC into DAI in time. At present, it is temporarily impossible to freeze this asset through a centralized organization.
Next, the asset tracking work for this incident can be done as follows:
First, obtain the wallet address of the attacker’s exchange fee for ETH through the ChangeNow platform to trace the source and find clues;
Second, synchronously monitor the asset transfer of the attacker's address in real time to track;
Third, get in touch with the attacker through on-chain transactions.
The security team of Zero Hour Technology will continue to track this incident, and once again appeal to everyone to keep their private keys safe, raise security awareness, pay attention to the security of wallets and assets, and contact us as soon as possible if any assets are lost.
Note: For detailed analysis of other classic attack cases in the industry, please pay attention to the official account of Zero Hour Technology.
Nomad Cross-chain Bridge Stolen $180 Million Event Analysis Suggestions
Analysis of Beanstalk Farms 450 million RMB Attack
epilogue
epilogue
Web3 has become a thriving new generation of network infrastructure due to its huge innovation capabilities and open source advantages, bringing a more credible and value-delivering ecosystem to the entire Internet world. Although security incidents in the Web3 industry continue, hackers and criminals emerge in an endless stream, but this does not hinder the healthy development of the Web3 industry.
On the contrary, just like the two sides of the game, the "white hats" of the Web3 world, and security agencies like our Zero Hour Technology, will definitely escort this lush ecology, protect the assets of users in the new world, and fight wits and courage with hackers for We will continue to work hard to establish a more complete mechanism, a stronger technical system, and safer transactions.



