About the application of Sinsemilla hash function in OlaVM
Delighted, we released on July 25, 2022OlaVM, an EVM-compatible ZKVM scheme. Since ZKEVM itself has always been a popular track, soOlaVMOnce it was released, it was a great honor to receive some attention from the big names in the industry.
Here, first of all, we would like to thankDaira Hopwoodbig guy (alsoZcash protocolandECDSAandSchnorrThe Hash selection problem in the signature algorithm is specifically expressed as shown in the figure below:
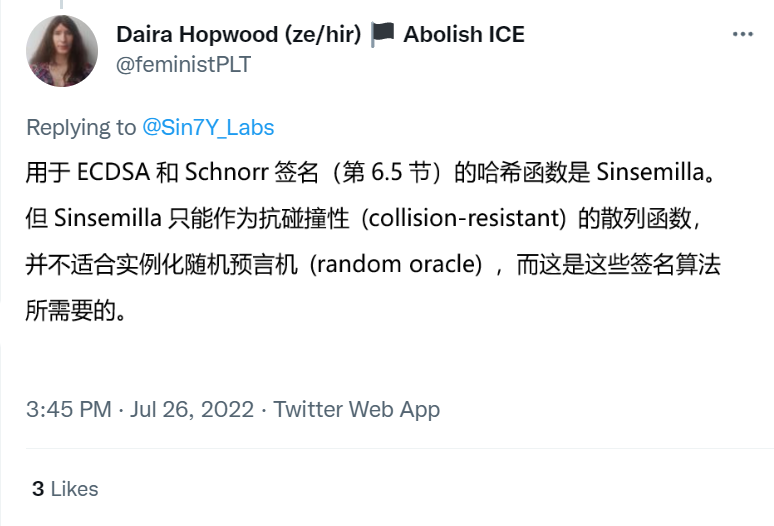
Daira HopwoodThe meaning can be simply understood as:Sinsemilla HashandECDSAandSchnorrfirst level title
1. What are the security properties of cryptographic hash function (CHF)?
According to the paperCryptographic Hash-Function BasicsAccording to the definition in , there are three types of security attributes corresponding to CHF:
• preimage-resistance— Basically for all prespecified outputs, it is computationally infeasible to find any input that hashes to that output, e.g., to find such that h(x')=y when given any unknown input y All preimages x' of .
• 2nd-preimage resistance— It is computationally infeasible to find any second input that has the same output as any given input, e.g., given x, to find a second preimage x' = x such that h(x') = h (x).
• collision resistance— It is computationally infeasible to find any two distinct inputs that hash to the same output, e.g. such that h(x') = h(x).
have to be aware of is:
a. 2nd-preimage resistance can be reduced to collision resistance, that is, if collision resistance is satisfied, then 2nd-preimage resistance must be satisfied.
b. preimage-resistance cannot be reduced to collision resistance, that is, collision resistance is satisfied, then preimage resistancenot necessarilyfirst level title
2. What is a random oracle (RO)?
random oracle(RO)Described by the following model:
• There is a black box. A dwarf lived in the box, along with a large book and some dice.
• We can enter some data (arbitrary sequence of bits) into the box.
• Given some input that the dwarf has not seen beforehand, he uses dice to uniformly and randomly generate a new output in some regular space (the oracle output space). The gnome also writes down the input and newly generated output in the book.
• If the gnome is given an input that he has seen, he restores the output he last returned with the book, and returns again.
Simply summarize the behavior of RO, assuming the input is x:
• If x has been input before, directly return the corresponding H[x].
• If x has not been entered, RO will be incompletely randomGenerates a string consisting of 0,1 in the value field.
have to be aware of is:
• herecompletely randomIt means that even RO itself does not know what value it will end up with. It has no rules to follow. This is the main difference from Hash. Any Hash has its own calculation rules.
But in the real world, it is difficult to achieve a real RO; Therefore, we need to find a potential candidate for RO, and we need to make the output look as random as possible. Hash function is a good choice. A safe Hash function needs to satisfy preimage-resistance, 2nd-preimage resistance, and collision resistance.A Hash that can be used as an RO must satisfy these three attributes, but a Hash that satisfies these three attributes may not necessarily be used as an RO; between them is aNecessary not sufficientfirst level titleWhat is the "Random Oracle Model" and why is it controversial?
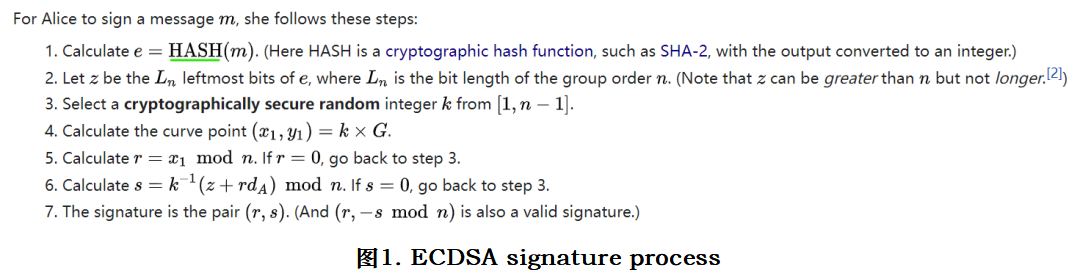
3. Hash requirements in ECDSA and Schnorr signature calculation?
andOn the security of ECDSA with additive key derivation and presignaturesandOn the Exact Security of Schnorr-Type Signatures in the Random Oracle Modelfirst level title

4. About the Sinsemilla hash function?
The Sinsemilla hash function is given byDaira Hopwood and Sean BoweDesign together, low-level dependenciesECDLP(Elliptic Curve Discrete Logarithm Problem). Under fixed-length input, the Sinsemilla hash function satisfies collision resistance,The preimage resistant attribute is not satisfiedofDaira Hopwoodofaccording to。
according toZcash Protocol Specificationfirst level title

5. Summary
Thanks againDaira Hopwoodguidance, let uscryptographic hash function (CHF)The use has a deeper understanding. We will continue to listen to opinions extensively, and continue to optimize the design scheme in terms of efficiency and safety.
The Sinsemilla hash function will still be used in other suitable modules in the Olavm design; for the Hash function of the signature part, we will choose the best among the safe hash functions, such asPoseidonhash function,Reinforced ConcreteWeChat public account: Sin7Y
about Us
Sin7y was established in 2021 and is composed of top blockchain developers. We are both a project incubator and a blockchain technology research team, exploring the most important and cutting-edge technologies such as EVM, Layer2, cross-chain, privacy computing, and autonomous payment solutions.
WeChat public account: Sin7Y
GitHub | Twitter | Telegram | Medium| Mirror | HackMD | HackerNoon



