Why do we need cross-chain bridges? What are the current popular cross-chain projects?
Compilation of the original text: angelilu
Compilation of the original text: angelilu
The future will be multi-chain, and cross-chain bridges can help us gain more benefits and trading opportunities on the chain.
The cross-chain bridge enables us to gain access to many on-chain benefits and trading opportunities.
Bridging comes in several forms, each with its own combination of security, speed, and reliability.
New tools are being developed that can solve the "bridging trilemma".
introduce
introduce
Cross-chain bridges allow us to transfer tokens between blockchains and have become an indispensable utility for most DeFi users. Demand for these tools has exploded over the past few years as new blockchains emerge alongside new DeFi protocols and revenue opportunities. If you are interested in chasing the highest return on capital, then you will use cross-chain bridges. Cross-chain bridges come in many forms, each with its pros and cons in terms of security, custody, speed, and cost. Here we will try to explain these differences.
Why use a cross-chain bridge?
Three common reasons:
Chasing Yield: DeFi allows anyone to put their assets to work and generate some yield. Every on-chain DeFi protocol wants you to use its business, and often offers incentives to entice you and encourage you to stay.
Evade the high fees of a congested network: If you only have a few hundred dollars in assets, but every transaction costs $20, it's hard to survive. If you can connect this asset to a cheaper chain, you can transact cheaper and have a better chance of surviving.
Wrapping or unwrapping native assets: some exchanges may sell you an ERC20 version of the native token you just bought. If you want to own the actual native token, you may first need to connect your wrapped version to the native network.
DeFi protocols compete for our assets by offering us higher yields than our competitors. Assume that the best offering of ETH on the Ethereum network has an annual rate of return of only 1%, but the rate of return on the wrapped Ethereum wETH on the Avalanche network is 4%. In this case, everyone wants to pack and put their ETH on Avalanche. As every DeFi platform hoping to succeed introduces liquidity mining incentives to attract users and capital, the need for functional and reliable bridges has exploded.
Another obvious need for a good cross-chain bridge is network congestion. Ethereum itself is already a successful blockchain, but is still working on scaling. During the worst period of network congestion, a simple transaction on Uniswap would charge a gas fee of $300 to $500. Several alternative Layer 1s have emerged to meet this need for affordable block space. If the latest EVM replication chain also starts to get congested, someone will start a new chain. As long as these high-yield opportunities exist, the demand for cross-chain tools will continue to grow. A cheaper alternative, Layer 1, fills some of the needs of this market, while a cheaper Layer 2 is being built and waiting to go live. No matter which chain the high yield is in, users want to transfer funds there.
How Cross-Chain Bridges Work
There are three common structures:
1. Locking and Minting
Lock assets on the source chain and mint synthetic tokens on the target chain. This is by far the most common type of bridging. ERC20 tokens are a good example. ERC20 can represent any asset on Ethereum, and Bitcoin becomes wBTC; even Ethereum itself can be wrapped into wETH.
Each network has a native token, and any network can issue the native token of another chain on its own chain through "bridge" assets. This is achieved by locking the native asset on the source chain and providing proof on the destination chain that the asset is indeed locked. This allows the destination chain to issue a wrapped version of the asset backed by the native asset locked in a vault on the source chain. The security of the system depends on the bridges and verifier network that verify the transfer. While this approach is the most popular, issues around centralization, trusted custody, and collusion must be addressed to make this model more resilient. There is also an inherent inefficiency that is still being worked out. These bridges typically require two steps to make the synthetic asset available on the target chain — exchanging ETH for the bridge token, then burning the bridge token to mint the synthetic asset. This presents a clear opportunity for increased efficiency.
2. Atomic Swaps
This is arguably the safest and trust-minimized method of transferring native assets to other chains, but it also has some drawbacks. Both chains must share the same hashing algorithm to ensure that blocks containing transfers can be verified on both chains.
3. Liquidity Providers
Fund pools have been created on both chains to facilitate transfers and charge a certain fee. The system works well when it is sufficiently decentralized, effectively rebalanced, and LPs have sufficient incentives to maintain sufficient liquidity on both sides of the bridge. Cross-chain transactions on this type of bridge are valid on both the source chain and the target chain. Assets are transferred from vaults typically managed by LPs and validators.
What happens behind the scenes at a time when we can easily move across all these different chains involves serious technical chaos, hacks and exploits are possible wherever funds are involved. Vitalikwarn us, he argues that poor bridge architecture poses some real challenges that can create systemic risks. Colluding validators, compromised oracles, centralized relayers, and other hazards must be avoided when designing the way these tools function. Celestia co-founder Mustafa Al-Bassam atduring an interviewResponded briefly to Vitalik's statement, stating that he largely agrees with Vitalik. He has expressed the same concerns in the past. The difference however is, Vitalik's argument is that every chain has to use the same settlement layer to share security because you can't do bridges securely. Mustafa believes that this is still possible with the right tools, and that communication-based cross-chain bridges can be an effective solution.
Here's an example of a cross-chain transaction on Layer Zero that shows how complex it can be:
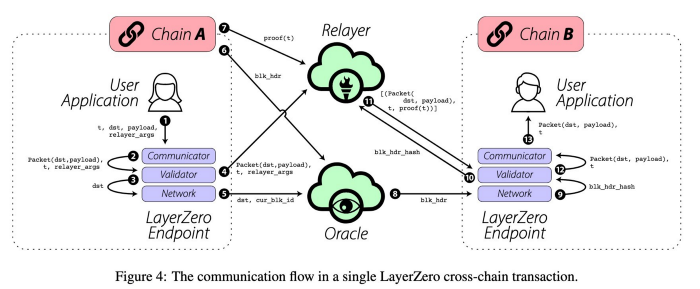
centralized
centralizedspeed
speedliquidity problem
liquidity problemSmart Contract Risk
Smart Contract RiskSecurity Question
Security Question
The recent hack of Axie Infinity's Ronin chain demonstrates why bridging security is critical. The Ronin Bridge was attacked and 173,600 ETH and 25.5 million USDC were lost. How is this possible? The vault holding the wrapped assets is controlled by a 5/9 multi-signature wallet managed by Ronin chain validators. The keys of 5 of the signers were compromised and the hacker in control was able to send all wETH to themselves.
This particular incident was a case of too much concentration of bridges with rather poor trust assumptions and little oversight. During periods of high network congestion, a signer was given temporary approval rights that were not revoked immediately afterwards. This is the last link the attacker needed to move funds after taking over 4 of the 9 signers controlling the bridge funds.
The more common bridging attacks usually involve exploitable code in smart contracts. The wETH you earn on Ronin can be spent as the asset represents native ETH locked in a vault. If you can figure out a way to mint an infinite amount of wETH and exchange it for real ETH using the bridge, then congratulations, you just robbed a cross-chain bridge. Now the remaining wETH (on the Ronin chain in this case) is basically worthless, since all the ETH locked as collateral for its wrapped version has already been claimed. A hack of this scale also has the potential to significantly disrupt the entire crypto market. If a bridgejacker can make a fortune like this and start dumping $500 million worth of ETH on the market, that's (at least temporarily) bad news for long-term ETH holders.
It is a valuable lesson to hope that an attack of such a large amount can catch the hacker and return all the funds to the original place. We need to carefully consider the construction and mechanism of these cross-chain bridges to limit large-scale systemic risks. There may be a better way, and we find that there are currently several interesting and fascinating cross-chain interoperability projects introducing new bridging methods and strategies.
Currently interesting cross-chain projects
Chainlink CCIP
Chainlink builds a programmable token bridge. It uses Chainlink's off-chain reporting protocol (OCR2.0), a network of hundreds of independent oracle nodes, and its cross-chain interoperability protocol. CCIP provides an interface for all cross-chain communication and can be easily integrated into any smart contract application. It supports any generic message and has reassembly protection. Their Programmable Token Bridge also supports computation, allowing developers to transfer tokens across blockchain networks and initiate programmable operations on the target chain. By using Chainlink's decentralized oracle network and messaging router, a smart contract can securely send a message to the target chain, have it verified by another messaging router, and then send the message to the smart contract on the target chain .
Stargate
Stargateis a fully composable cross-chain bridging protocol built onLayerZeroOn top of that, users are allowed to transfer native tokens across various blockchains.
LayerZero is an Omnichain interoperability protocol designed for passing lightweight messages across chains. LayerZero provides authentic and guaranteed messaging with configurable distrust. The protocol is implemented as a set of efficient, non-upgradeable smart contracts.
Most existing cross-chain bridges cannot send native tokens from one chain to another, instead relying on intermediate or "wrapper" tokens to complete the bridging process. This approach creates a slow and extremely inefficient user experience. Stargate is built around a unified liquidity pool shared by multiple chains, ensuring sufficient liquidity is always available and fast finality. The ultimate goal is to achieve a seamless bridge across chains through a single transaction.
How Stargate solves the bridging trilemma:
Instant Guaranteed Certainty:Stargate assures users and dApps that any transfer requests they make on the source chain will reach the destination chain. However, there must be liquidity on the target chain, otherwise the transaction will be returned. With Stargate's bridge, there is no need to wrap tokens, and users do not need to manually exchange tokens on the receiving chain.
Cross-chain composability:The Stargate bridge can be composed of smart contracts of the source chain and the destination chain. This will allow users to complete multiple transactions in a single cross-chain transaction. Imagine exchanging wBTC on Fantom for JOE on Avalanche and entering an LP position with a single transaction without leaving Fantom.
Unified Mobility:Most existing bridges require decentralized liquidity to function. Each chain integrated into a bridge needs to designate a liquidity pool for each asset bridged. Users may also experience long delays or failed transactions if there is insufficient liquidity. A bridge that wants to add a new blockchain must also bootstrap a new pool to accommodate the new chain with enough liquidity on each existing chain.
Stargate proposes a unified approach where all connections are drawn and withdrawn from a single liquidity pool, enabling Stargate to achieve scalability and efficiency not possible with lock and mint or burn and redeem bridges . Stargate also features efficient rebalancing and self-limiting mechanisms to manage spikes in withdrawal activity. Each chain on the protocol can maintain a single liquidity pool that is "soft partitioned" into different shards, each corresponding to a specific chain in the network.
Gravity Bridge
Gravity Bridgeis a bridge between EVM and Cosmos SDK-based blockchain, it is powered byAltheabuilt by excellent people. They created a non-upgradeable Solidity contract that allows users to lock assets on Ethereum and mint equivalent tokens on any Cosmos chain. They can be sent back or sent between other Cosmos chains. Different Cosmos chains can use this bridge to access ERC20 assets such as wETH, DAI, USDC and wBTC. Assets from Ethereum can flow into the Cosmos ecosystem and interact with various applications such as Akash Network, Sentinel, Regen, and Osmosis. Assets on the Cosmos ecosystem can flow to Ethereum and interact with Ethereum DeFi.
Why Gravity Bridge?
Non-custodial: You only need to trust the security of Ethereum and Cosmos when transferring assets.
Trusted neutrality: The bridge is not focused on capturing users for a specific blockchain or DEX. It is designed to allow traffic to flow on the bridge, and the neutral nature of the bridge lowers the barrier to accessing liquidity in the Ethereum ecosystem while allowing new and small blockchains to participate on the Cosmos Hub.
Interoperable: For a long time, Binance’s BNB was the only common asset between the Cosmos and Ethereum ecosystems. Ironically, the only way to connect from one decentralized ecosystem to another is through a centralized exchange token. The DEXs in the Cosmos ecosystem are basically stranded on their own islands, unable to trade with other chains. With Gravity Bridge, Osmosis, Umee or Gravity DEX will be accessible to all market participants.
Security: There is an active validator set on the Cosmos SDK-based chain. Validators must stake a large amount of tokens, and any misbehavior by the validator is punished by slashing the validator's stake. It is also permissionless and censorship resistant. Representative tokens are minted when at least 2/3 of the validators prove to have a deposit. Withdrawals occur when a bridge batches multiple "SendToEth" messages.
Interlay.io
InterlayIntroduced Kintsugi, the first trustless Bitcoin bridge on Kusama, Polkadot's canary network, Polkadot will soon have its own bridge. Interlay's wrapped bitcoin, kBTC, is very similar to Maker's DAI. It is algorithmically pegged to BTC and secured by a decentralized network of vaults, a multi-collateral system and cross-chain cryptography. This familiar collateral-backed vault leverages Polkadot's shared security model and Bitcoin's classic security model.
Nomad
Nomadis a new design for very cheap cross-chain communication, skipping the need for block header verification. Nomad draws a lot of inspiration from the Optimism team. Nomad itself is actually theirOptics agreement(OPtimistic Interchain Communication) implementation and extension. But Nomad only has a 30-minute delay (instead of ORU's one-week fraud window). The way it works is like a notarization service, the source chain generates and sends some "documents" (messages), the "notary" (called an Updater) makes a contract to sign the documents, and is incentivized to only approve valid messages that might otherwise Risk of being financially penalized and losing their "notary license". themin the documentexpress:
“Nomad creates a verified data structure on any main chain and forwards updates to that data structure on any number of replicas. Therefore, the main chain and all replicas [maintain a queue of pending updates, accept proofs, and send messages] contract] will agree on the state of the data structure. By embedding data (messages) within this data structure, we can propagate it between chains with a high degree of confidence.”
The team's close collaboration with the Optimism team and the Connext team speaks volumes about their reputation and credentials, and they are approaching cross-chain issues from a very new angle.
We're all tired of clichés like "Wild West" and "New Frontier," but they're clichés because they're such apt tropes. Some may debate whether it is too late to start encrypting, but there is no doubt that we are still in the early stages of cross-chain communication and bridging. The progress made across chains this year has been astounding, and we expect this pace to continue. Below is a list of some of the cross-chain bridges we explored and experimented with as we delved deeper into the topic:
multi-chain bridge
native cross-chain bridge
Gravity Bridge(Cosmos) coming soon
Cosmos IBCTransfer assets between any IBC compatible chain
Top 10 EVM cross-chain bridges by volume
AnySwap: Fantom $672 million
Avalanche: $577 million
Wormhole: $294 million
Polygon: $131 million
Celer: $86 million
Metis: $84 million
Near: Rainbow $80 million
Synapse: ETH Bridge Proxy $72 million
Synapse: L1 Bridge Zap $63 million
Original link



