Privacy is a fundamental right of every human being.
In 1993, Eric Hughes stated at the beginning of his famous "Punk Manifesto":
Privacy is necessary for an open society in the electronic age. Privacy is not secrecy. A private matter is something one doesn't want the whole world to know, but a secret matter is something one doesn't want anybody to know. Privacy is the power to selectively reveal oneself to the world.
Privacy is indispensable in an open society in the electronic age. Privacy is no secret. Someone doesn't want the world to know something, that's privacy; someone doesn't want anyone to know something, that's a secret. Privacy is the power to selectively reveal oneself to the world.
Obviously, in the era of digital Internet, privacy protection has become the most basic need and the most severe challenge facing everyone. And it is considered as one of the important directions of Web3.0.
Privacy coins such as Zcash have tried to make up for this market demand, but in the Web3 era, privacy protection and private computing of smart contracts and off-chain data have become new rigid needs.
However, as a kind of "just-needed existence", more and more top VCs and developers are still entering the field. The competition for the privacy track has become increasingly fierce since the second half of 2021. Both the protocol and the application layer have given birth to many privacy-focused projects, some of which try to use trusted execution environment (TEE), multi-party secure computing, etc. to protect data privacy (blockchain hybrid architecture), such as identity information, medical information, and some projects focus on using ZKP (Zero-Knowledge Proof data) and other solutions to protect transaction information and contract logic.
first level title
Why is privacy protection so important?
Privacy protection is imminent for giant whale users.
In the early morning of March 11, the Cosmos smart contract platform Juno initiated a proposal on the governance platform, intending to upgrade the contract and delete JUNO assets from the whale player account, and send all of them to the Juno community fund pool, and only reserve a reasonable 50,000 JUNO for this account , the user actually pledged more than 3.1 million JUNO, which means that about 3.05 million JUNO will be confiscated by the project party. Based on the current price of 39.6 US dollars, the asset is worth 120 million US dollars. This is the first time that a large investor has been directly proposed by the DAO to confiscate assets. How whale users can protect their property and other privacy in the future is imminent.
However, as an ordinary user, you still face very serious privacy protection problems.
Every time you eat at a restaurant and scan the QR code to fill in your mobile phone number to order food, do you worry that your phone number will be collected and sold by an unknown centralized application development team? Even if a giant like Facebook (the predecessor of Meta) continues to leak the privacy of hundreds of millions of users, do you worry that your personal information and private documents will be sold on the black market? Since the European GDPR was promulgated in 2018, there have been more than 900 fines, with a fine amount of up to 1.54 billion euros.
When the transaction relationship between your blockchain accounts and your Twitter friend relationship network are captured, you will worry that the crawler will associate your identity with the blockchain account through certain topology analysis techniques. Lead to leakage of personal asset information.
When Russia invaded Ukraine and the centralized exchange froze the blockchain accounts of Russian users, would you worry that your account might also be frozen at any time?
first level title
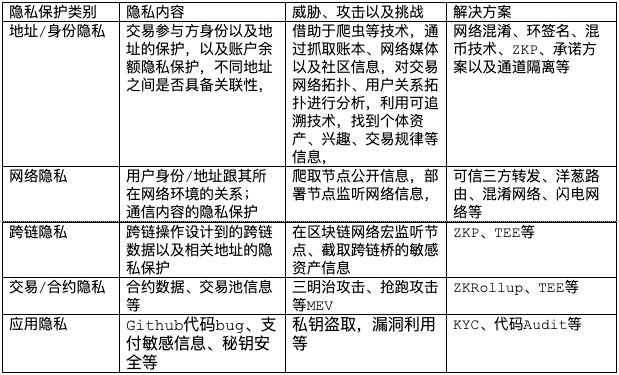
Privacy Protection Objectives
first level title
History of Blockchain Privacy Protection Technology Development
Privacy protection technology develops rapidly with the development of blockchain, here we make a simple context.
Blind signature: David Chaum proposed in 1983 that blind signature is different from general digital signature. The idea of general digital signature is to generate a string of numbers that only the sender can generate, which cannot be forged by others. A valid proof of the authenticity of the message sent by the sender. The difference is that the signer of the blind signature does not know the specific content of the signed message, and only proves the authenticity of the signature at a certain point in the future (as a notary). Early David was used in E-Cash.
CryptoNote and ring signature: CryptoNote (CryptoNight) is the originator of blockchain privacy technology. Conceptually, in a distributed network, CryptoNote uses traceable ring signature encryption technology to confuse messages between a group of nodes. Improvements to the CryptoNote protocol have been shown to yield high levels of anonymity at scalable levels of operation. Bytecoin was also a pioneer in adopting CryptoNote, which was released in 2012. Monero, the anonymous currency with the highest market value, is also an encrypted currency based on the CryptoNote protocol.
zk-SNARKS: The protocol behind ZCash is zk-SNARKs. zk-SNARKs are novel zero-knowledge cryptographic algorithms that allow one party (the prover) to prove to another party (the verifier) that a statement is correct without revealing the actual content of the statement. Since the release of Zcash, zk-SNARKs have been applied to different blockchain technologies. Based on Zcash, many other anonymous coins have been forked, including Komodo, Zcoin, Horizon, etc., and the zk-SNARKs protocol almost supports half of the anonymous coins;
TEE Trusted Execution Environments (Trusted Execution Enviorments): Trusted execution environments are a recently popular method of introducing trusted computing into the blockchain. For example, Intel's Software Guard Extensions (SGX) TEE technology isolates code execution, remote attestation, secure configuration, secure storage of data, and trusted paths for code execution. APPs running in TEE are secured and almost impossible to be accessed by third parties. Related projects based on TEE technology include SecretNetwork, Oasis, Eigen Network, etc.
MimbleWimble protocol: MimbleWimble protocol was launched in 2016 to improve the scalability, privacy and substitutability of digital currency. It combines multiple privacy protection technologies such as confidential transactions, transaction mixing and Dandelion Protocol to protect transaction amounts and transaction addresses, making it It simplifies the transaction size while protecting transaction privacy. Based on the MimbleWimble protocol, two twin star projects, Grin and Beam, were born and have been highly recognized by the market.
first level title
Project Classification and Typical Implementations
Anonymous currency: Anonymous currency is a special blockchain token that hides the transaction amount, hides the sender and the receiver during the transaction. Among them are Dash based on CoinJoin technology, Monero based on ring signature and one-time address technology, Zcash based on zk-SNARKs technology, and Grin based on recognition protocol. From CoinJoin to commitment protocol and to zk-SNARKs, basically represents the continuous development of zero-knowledge proof technology.
Privacy transaction network: The privacy transaction network mainly conducts privacy processing for on-chain transaction data (the type and amount of currency held or traded), supports users to conduct private transactions natively through technologies such as zero-knowledge proof, and supports the development of more Types of privacy apps. This type of project is mainly based on general-purpose zero-knowledge proof virtual machines, currency mixing, and network obfuscation solutions. Zero-knowledge proof solutions typically include building ZKP virtual machines based on zero-knowledge virtual machines represented by Aztec to achieve privacy protection such as contracts. Others include Dusk, Suterusu, Aleo, Espresso, Iron fish, and Zecrey; Including Tornado, CoinMixer, Onion Mixer, etc.; network obfuscation solutions, including XXNetwork, NYM, HOPR, etc.
Privacy protocols and applications: based on private transaction networks or private computing technologies, privacy protection for user assets, user transaction records, and user behavior; such as privacy cross-chain bridges, emails, asset encryption, confidential transactions, etc.; typically include supporting assets Encryption and transaction encryption Railgun, privacy transaction and exchange protocol Eigen Network, privacy computing middleware Automata, cross-chain privacy protection middleware Raze Network, decentralized VPN Boring protocol, decentralized mail service DMail, etc.
Project Introduction
Project Introduction
Below we introduce the typical projects under each of the above categories, and introduce the typical privacy guardians under Web3.0.
secondary title
MONERO(XMR)
The UTXO model is based on the CryptoNote protocol (proposed in 2012, Bytecoin) to confuse messages between a group of nodes.
Realize anonymous payment. CryptoNote uses one-time privacy address and ring signature technology. One-time privacy address, reducing the correlation of addresses between different transactions. The sender and receiver use the secret key to confirm whether the transaction is valid (One-time-stealth). This protocol obviously enhances the privacy security of the receiver. This scheme is a typical ECDH-based address hiding scheme.
secondary title
Dash(DASH)
First forked from Litecoin, it supports InstantSend and PrivateSend. PrivateSend is a currency mixing technology based on CoinJoin.
secondary title
Zcash(ZEC)
secondary title
Grin(MWC)
Confidential Transactions,The concept of Confidential Transactions (CT) was first proposed by Blockstream CEO Adam Back in 2013, and was later extended by Bitcoin developer Gregory Maxwell. In the first part, Maxwell outlined the problems of "homogeneity" and "weak anonymity" mentioned, and proposed corresponding solutions. CT adopts the Pedersen commitment scheme, so that only the transaction participants can know the specific value.
Mimblewimble protocol(Andrew Poelstra,2016) further extended CT, the transaction address and amount can be hidden, and the size of the block can be reduced through the Cut-Through mechanism.
MW is based on the commitment agreement for amount protection. MW does not require an address during the entire transaction process, and uses the blinding factor as the private key.
secondary title
Aztec Network
Unlike most private networks, Aztec Network is a private transaction network built on Layer 2. The main network has been launched in November 2020. The Aztec protocol uses zero-knowledge proofs to implement encrypted transactions on Ethereum, enabling transaction logic to be verified while maintaining anonymity and privacy. Aztec Private Rollup can hide Layer 1 DeFi transactions with only one Rollup. This privacy protection makes it impossible to track when users trade tokens, and which protocols are used to do so. In addition, Aztec combines homomorphic encryption and range proofs, and chooses a unique scheme for encrypting data, which can quickly and effectively verify zero-knowledge range proofs, reducing the gas cost of transactions on Ethereum. Even the Aztec DeFi bridge can batch process thousands of transactions in each Rollup, saving at least 10 times the gas fee in various operations.
secondary title
Aleo
Focus on building a developer-friendly privacy public chain.
Aleo uses zero-knowledge cryptography for privacy and programmability, and uses it as the basis for a system called ZEXE (Zero-Knowledge Execution). In ZEXE, users perform state transitions offline. This process produces a proof, which is bundled into an on-chain transaction. This transaction updates the system state by consuming/creating on-chain records. Because transactions contain only proofs, not the inputs that generated them, the system provides strong privacy guarantees. Like Ethereum, ZEXE can support smart contracts, enabling users to interact or transfer value in a predefined way.
secondary title
NYM
In 2021, the A-round financing of US$13 million will be completed, and the Cosmos-based blockchain mainnet Nym will be launched in January 2022.
secondary title
Tornado Cash
first level title
secondary title
Railgun
secondary title
Eigen Network
Eigen Network provides anonymous payment, privacy exchange and privacy computing network. Eigen Network has two products, EigenSecret, which focuses on personal asset security and privacy, and EigenShare, a privacy computing network.
Eigen Secret aims to provide a series of composable asset privacy protection tools through a self-hosted and modular contract wallet. The modular-based smart contract wallet provides fine-grained management of personal assets. Its modular design enables Eigen's contract wallet to quickly integrate with its currency mixers and privacy exchanges to achieve privacy protection for personal assets, transactions, and asset exchanges. EigenMixer is implemented using Plonk and TEE Relay, and Eigen Privacy Exchange uses ZKP and Mixer to hide address and order information. At present, some functions of EigenSecret have started public testing.
secondary title
Manta
Manta Network is Polkadot's ecologically focused DeFi privacy protection network, providing complete end-to-end privacy protection in the form of Polkadot parachains. Its first product, called MantaSwap, is a privacy-focused decentralized exchange.
Manta released the test network Dolphin Testnet in December last year, and launched the zkSNARK-based privacy payment function DolphinPay. DolphinPay can convert assets in the Polkadot ecosystem into privacy tokens, and supports the transfer and redemption of privacy tokens.
secondary title
Automata
Web3 privacy middleware.
Based on Intel SGX & Oblivious RAM technology. Oblivious RAM is mainly used to solve the side channel attack problem of Intel SGX.
At present, Automata Network will launch related privacy protection applications such as anonymous voting (Witness) and DEX anti-advance transaction system
first level title
secondary title
PlatOn
A distributed privacy computing network that supports various complex privacy tasks such as AI. Connect data owners, data users, algorithm developers and computing power providers, and plan to realize a general artificial intelligence network through three stages: privacy computing network, artificial intelligence market and collaborative artificial intelligence network. PlatON main network has been launched at the end of 2021 .
secondary title
ALEPH ZERO
secondary title
Oasis
secondary title
Ruby protocol
Focus on building an encryption infrastructure for personal data monetization, realize data sharing based on function encryption (FE) and attribute encryption scheme of CP-ABE ciphertext strategy, and provide data market, data pricing model and data copyright protection mechanism.
The Web3 grant project will complete a new round of financing of US$7.3 million in 2022.
Summarize
Summarize
The privacy track is booming, especially the Ethereum ecological derivatives. In addition to many different sub-fields, covering payment, transactions, DEX, cross-chain bridges, contracts, data analysis and utilization, and many other aspects, there have been many different fields in various fields. The privacy guardian has injected unlimited power into the strong development of the privacy track.
But for guardians, privacy protection itself must not only consider individual privacy protection, but also further consider compatibility with necessary regulatory requirements. Moreover, the usability of protected data and the cost of privacy protection, especially the composability support with other protocols, are still not enough. I hope that the guardians will work together to build a strong privacy protection infrastructure for Web3.0.
Eigen Labs China



