Multichain Vulnerability Post Analysis and Compensation Plan
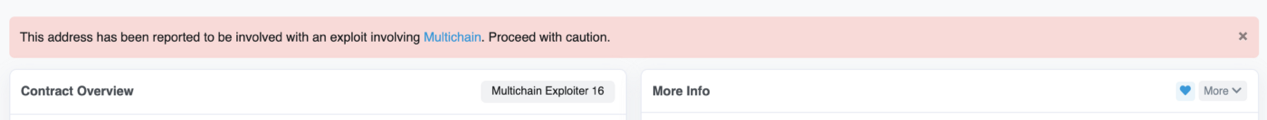
On February 19, 2022, Multichain, which focuses on cross-chain infrastructure, released a post-event analysis of the vulnerability that occurred on January 10, and is preparing to launch a user compensation plan. The main content of the full text is as follows:

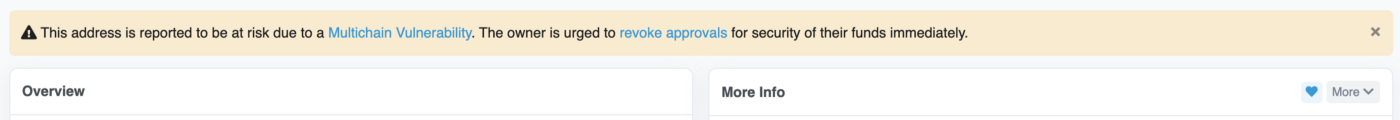
On January 10, 2022, Multichain received two serious vulnerability alerts about the Multichain liquidity pool contract and router contract issued by the security company Dedaub, and it was later confirmed that 8 tokens (WETH, WBNB, MATIC, AVAX, MFI, WSPP , TLOS, IOTEX) were affected by the vulnerability. Once the liquidity pool vulnerability was reported, the Multichain team immediately deployed the affected token liquidity upgrade to the new contract, so that the vulnerability was quickly fixed. However, the risk remains for users who have not deauthorized the affected routing contracts. Importantly, the deauthorization must be handled by the user himself. Therefore, Multichain made an official announcement on the vulnerability on January 18 and urged users to take immediate action according to the instructions.
event impact
Data statistics as of: 24:00 UTC time on February 18.
l A total of 7962 user addresses are affected, 4861 addresses have been deauthorized, and the remaining 3101 addresses have not yet taken action to cancel.
image description
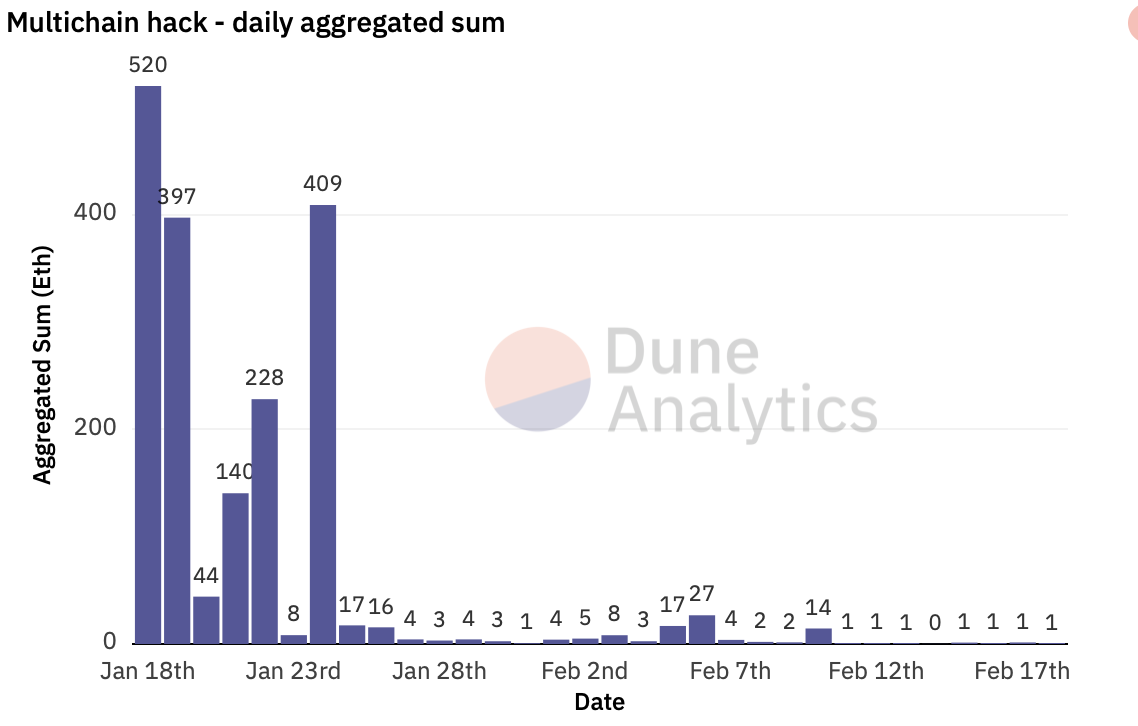
Daily hack sum, by @Dune Analytics
On January 18, the Multichain team notified affected users through all channels. After a month of hard work, more than 61% of users have successfully deauthorized so far. According to monitoring data from Dune Analytics, the attacks mainly occurred in the first week after the release of the vulnerability. After January 25, hacker transactions and amounts began to drop sharply. Although attacks have also occurred in the past two weeks, the amounts involved are relatively small.
compensation plan
With the joint efforts of Multichain and white hat hackers, nearly 50% of the amount has been recovered (912.7984 WETH and 125 AVAX). Despite Multichain's best efforts to salvage the loss, 976.8628 WETH were stolen.
In order to compensate for user losses, Multichain initiated a proposal to compensate 100% of user losses (including miner fees), and the funds will be returned to the following two types of users:
(1) Users whose authorization has been canceled
(2) Users who submit tickets on the Multichain help desk (https://multichain.zendesk.com/hc/en-us/requests/new).
The Multichain team stated that it has been a month since the official disclosure of the vulnerability on January 18 and urging users to cancel authorization. During this month, the Multichain team has done its best to take all feasible ways to notify the affected users. Once the compensation plan is made public, it is difficult to avoid malicious attacks by hackers. Therefore, the Multichain team will no longer compensate for any losses incurred after 24:00 (UTC time) on February 18. However, Multichain stated that it will continue to do its best to recover as much stolen funds as possible from the attack and will continue to update the news. All funds recovered after 24:00 (UTC time) on February 18 will also be fully refunded to users (minus miner fees).
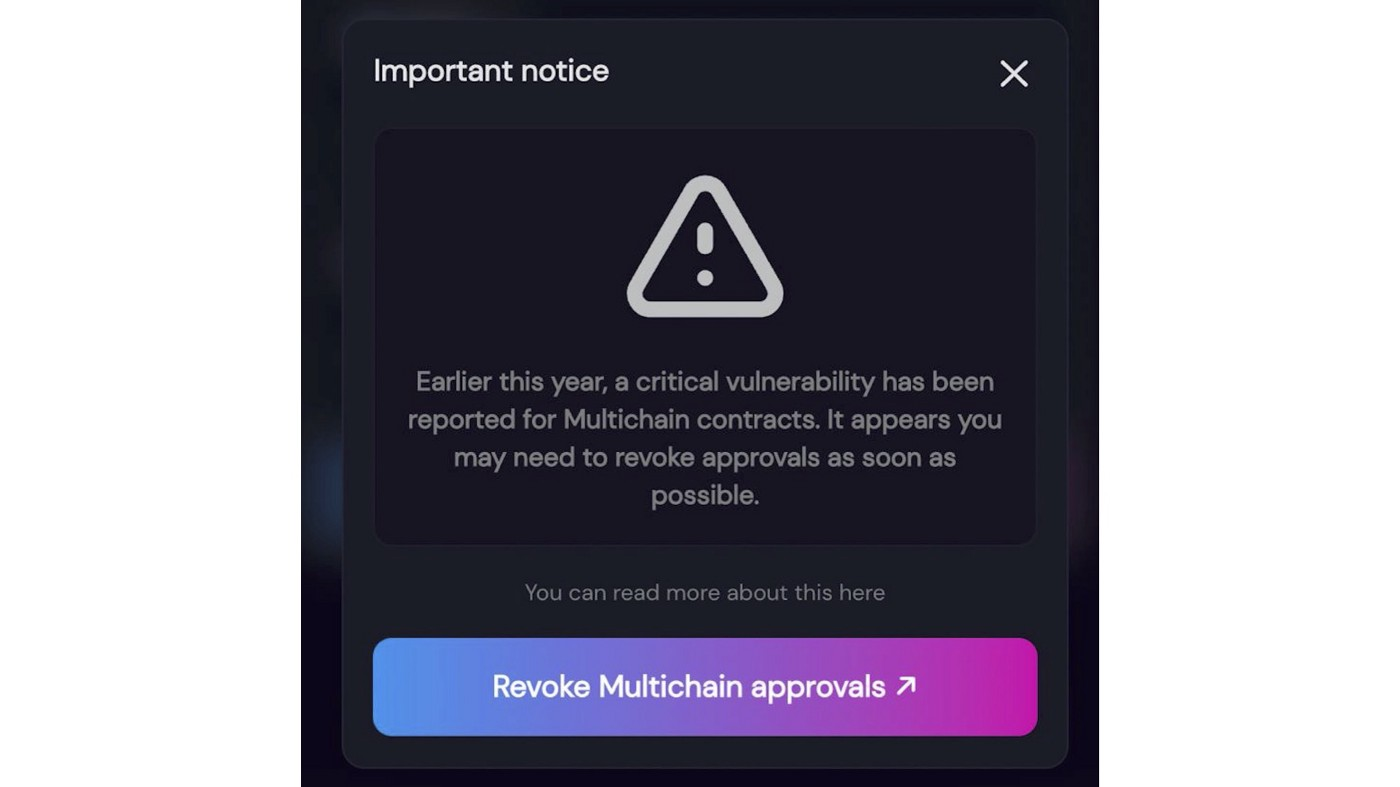
Additionally, Multichain once again strongly urges users who authorized affected token contracts to deauthorize before sending any tokens to their wallets. Users can perform status checks and deauthorization through the Multichain UI. If you don't know how to do it, you can follow the instructions given by Multichain. At the same time, users are reminded that if they encounter any problems, they can submit a ticket at the Multichain help desk, or contact them through the official Telegram, and the Multichain team will provide assistance.
Multichain UI:https://app.multichain.org/#/approvals
Instructions:https://medium.com/multichainorg/action-required-critical-vulnerability-for-six-tokens-6b3cbd22bfc0
Multichain help desk:https://multichain.zendesk.com/hc/en-us/requests/new
Telegram:https://t.me/anyswap
Bug Bounty Payments
thank you
thank you
Multichain would like to express its gratitude to every project and community member who reached out during critical times, with special mention to Etherscan Team, Sorbet Finance, Ava Labs, Sushiswap, Spookyswap, Metamask, Opensea, Looksrare, Tether, Popsicle Finance, Frax Finance, Gemini , Synapse Protocol, BlockSec, 0xlosha, MevRefund and all community members.
event review
January 10:
After receiving Dedaub's report, Multichain immediately set up a joint team to discuss and take a series of measures to protect the security of funds.
• Multichain checked all token contracts (1500+) and found that 6 tokens (WETH, WBNB, MATIC, AVAX, MFI, WSPP) may be at risk, and the loopholes related to their liquidity pools have been fixed within 24 hours.
• Suspension of router contracts for 6 tokens.
• Conduct a comprehensive inspection with partners to troubleshoot affected user addresses.
• Establish a real-time monitoring system.
• Develop the front end of the webpage and set up the deauthorization portal (https://app.multichain.org/#/approvals).
• Create asset preservation contracts.
• Notify user of deauthorization.
January 18:
Multichain issued an official announcement, urging the affected users to cancel the authorization, and constantly updated all users with the latest situation of the incident. At the same time, Multichain contacts all possible channels (including Opensea, MetaMask, Polygon Bridge, Dapps, etc.) to call on users to take immediate action to secure funds, thereby maximizing the proportion of deauthorized users.
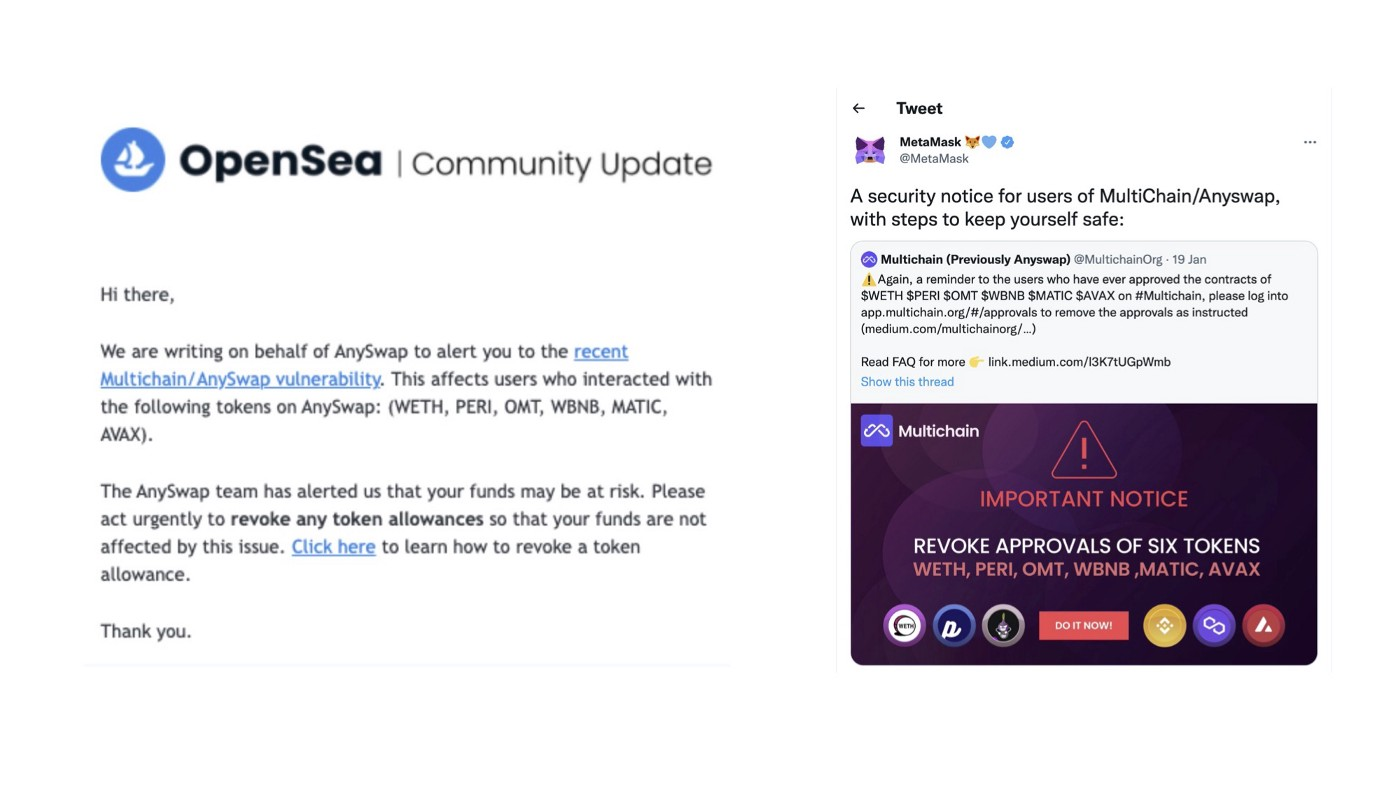
The first hack occurred 16 hours after the tip announcement, and Multichain and security firm Dedaub immediately fought to save users by running Whitehat bots.
January 19:
In order to prevent users from suffering losses, Multichain began to send on-chain transactions to all affected AVAX, MATIC, and WBNB addresses, prompting users to cancel authorization as soon as possible.
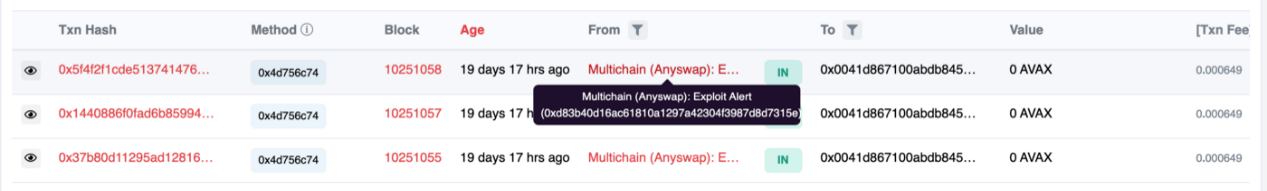
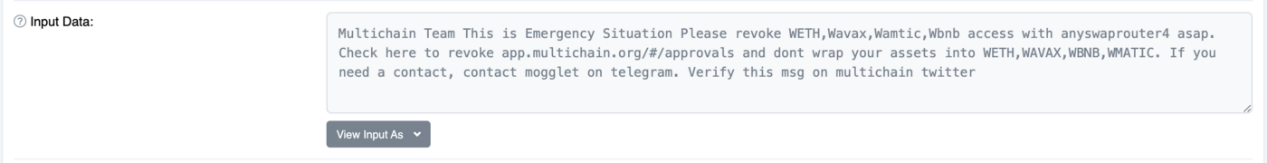
Additionally, Multichain communicated with the Etherscan browser to set up a warning bar for the attacker and affected WETH addresses.
January 20:
After negotiation, a hacker agreed to return 259+63 ETH.
January 22:
Security firm BlockSec assisted Multichain in its white hat rescue operation.
January 24:
Multichain has developed an authorization-cancellation API for Dapps. By integrating the API, users on the Dapps can directly cancel the authorization. SpookySwap, SushiSwap, SpiritSwap, AVAX bridge, AAVE, etc. have all been integrated.
January 25:
A community member (twitter handle @0xlosha) joined the white hat rescue and successfully secured 125 AVAX.
Multichain found a vulnerability affecting two other tokens (TLOS, IOTEX) and took timely measures to resolve it. The vulnerability was successfully repaired within 24 hours without causing any loss.
January 29:
Multichain assisted WSPP holders in resolving a theft of funds that occurred on January 26th.
February 14:
With the help of community members, Multichain got in touch with Tether, which froze USDT worth more than $715,000 in a hacker’s Ethereum address.
February 17:
All affected tokens have been upgraded to V6 contracts and support native currency cross-chain without requiring users to authorize tokens.
technical analysis
technical analysis
After receiving the vulnerability warning provided by the security company, the Multichain team developers quickly checked, reproduced, and verified the existence of the vulnerability, and thoroughly checked all possible contracts involved, and finally confirmed that the vulnerability involved two contracts AnyswapERC20 (V5 and previous versions), AnyswapRouter (V5 and previous versions), the specific vulnerability methods involved in the contract are:
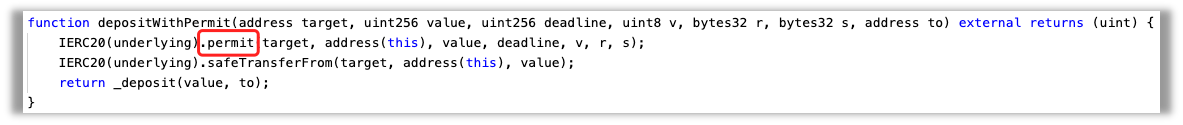
①AnyswapERC20:
· depositWithPermit
②AnyswapRouter:
· anySwapOutUnderlyingWithPermit
· anySwapOutExactTokensForTokensUnderlyingWithPermit
· anySwapOutExactTokensForNativeUnderlyingWithPermit
(1) Causes
This vulnerability is caused by the joint action of the Anyswap contract and the underlying token contract. The main reason is that for some underlying token contracts, there is no permit method implementation, and there is a fallback function. When calling its permit method, it will be executed, so that Subsequent operations related to funds were executed, affecting the security of funds.
The main purpose of the AnyswapERC20 contract is the capital liquidity pool. As soon as the vulnerability warning was received, the team immediately repaired and deployed the V6 version of the security contract, and at the same time sent an alarm request to the MPC network to recharge funds into the security liquidity pool. So far, this part of the funds is safe.
The AnyswapRouter contract is mainly used for inter-chain asset routing. The assets mainly affected by this vulnerability are user assets that have been authorized by the contract, and the deauthorization of assets needs to be handled by the user himself. The team immediately opened the forced deauthorization page for vulnerable assets on the homepage of the application, and notified the user as much as possible to cancel the authorization. At the same time, they set up an asset preservation contract and closely monitored the changes in this part of the funds.
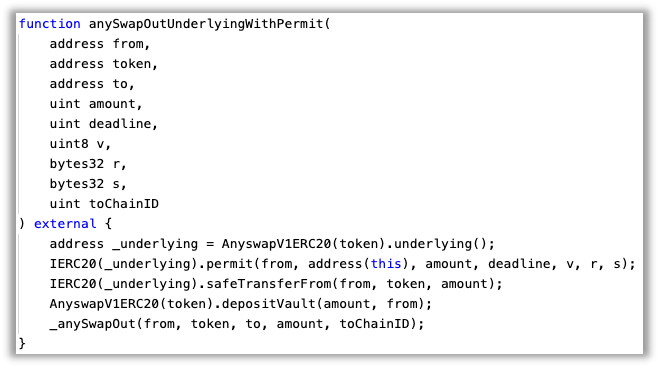
The following is a specific attack example to show the vulnerability. The final effect is: the user funds that have been authorized for the risk asset token as AnyswapRouter are transferred to the attack contract.
(2) How to attack
The attacker deploys the attack contract and sets the underlying parameter of the attack contract as the risk asset token address, calls the anySwapOutUnderlyingWithPermit method of the AnyswapRouter contract, where from is the address of the user who authorized the above token for AnyswapRouter, token is the address of the attack contract, and amount is the fund balance of the above user , and other parameters are arbitrary.
Further Security Measures
Further security audits. Multichain will conduct further security audits on contracts, cross-chain bridges and MPC. The Multichain team will continue to work hard to enhance the security of the entire cross-chain bridge architecture and closely monitor all new contracts.
MULTI security fund. Multichain will initiate a governance proposal for the Security Fund. When Multichain causes asset loss due to possible loopholes in its own systems and services, the security fund can be used as a necessary and possible rescue measure. The establishment and use of the fund will be announced later.
Bug bounty program. Multichain encourages the community to continue reviewing Multichain's code and security. Multichain will partner with Immunefi on a bug bounty program that recognizes the value of independent security researchers and teams. Multichain will offer rewards ranging from $500 to $1,000,000 for discovering and submitting vulnerabilities. See https://docs.multichain.org/security/bug-bounty for more details.
Open the free REVOKE-APPROVAL API to the public. The authorization-cancellation API developed by Multichain for this event has proven to be effective. Protocols and applications integrating this API can detect and alert affected user addresses to take appropriate action. Multichain is updating it and will provide a free public API for all projects.
Original link



