This article is translated by Eigen Labs, and the original author is Zhen Yu Yong. Please click to read the original text to get the original English version of the article. Eigen Team will continue to deliver the latest blockchain dry goods for you, please continue to pay attention! Enjoy~
As blockchain and other crypto use cases proliferate, private keys are given more value, economically and more. It follows that the importance of key management continues to rise. At present, there are already multiple key management systems. This article will further discuss several issues of key management and the trade-offs of key management systems.
01 Key management based on user equipment
This is pretty much the most basic way to manage a key pair - storing it on the user's device. Devices include their browser, desktop, mobile device or hardware wallet/ledger. This is by far the most common way of managing private keys on a wallet, but it has several disadvantages.
First, most users are not familiar with key and mnemonic management methods. Furthermore, standard key management is a trade-off between security (the possibility of the key being compromised) and redundancy (losing the key without a backup) and convenience. This leads to other management options
02 Escrow key management
A trusted third party manages the private key on behalf of the user and returns the private key to the user upon login.
03 Password management model
The password management model encrypts client-generated keys with user-supplied, easy-to-remember passwords, and then stores these encrypted keys and password hashes on the server.
The password management model means that the private key is encrypted on the client side through the password set by the user, and they store the encrypted private key and password hash on the server.
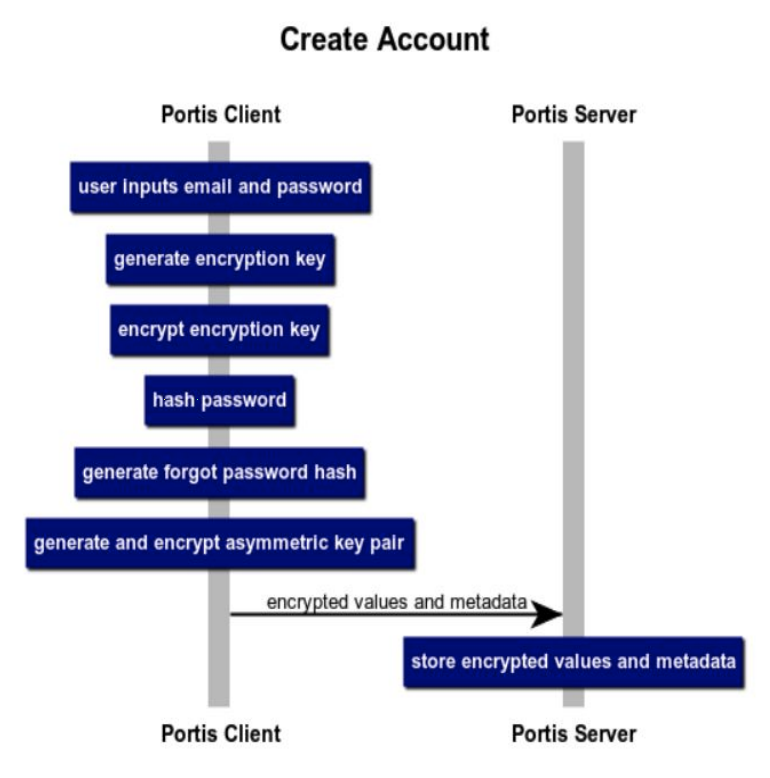
When a user logs in, they provide a username/password hash combination to the server, which is retrieved and encrypted and decrypted locally. Especially convenient, this model allows users to use any device to access their keys.
The non-custodial nature of the password management model still leaves us with trade-offs when using this model. Since the user key is encrypted with a passphrase, this model is also subject to the same brute force/rainbow attacks as traditional cryptosystems. Any attacker who has access to the password hash/encryption key will be able to make repeated attempts to decipher the user key. For passwords with symbols, letters, and numbers, it took 34 seconds to crack a 6-character combination and 1-2 days for an 8-character combination. Additionally, access to encryption keys may be denied, leading to censorship headaches.
04 Threshold key management
Threshold key management typically uses some kind of key sharing to split a user's key into multiple shares. A key shard with a certain minimum number of shares can be used to reconstruct a user key. Threshold key management allows multiple EOAs to control a single account, allows users to have multiple shards for a key, allows users to keep shards as backups without compromising the master key, and allows Realize the reuse of key shards under the premise.
The properties of the threshold key management model depend on where the user saves each key shard. Different wallets and schemes have developed different approaches based on actual use cases.
05 Smart contract wallet model
Smart contract wallets are not passwords, but contracts that hold and manage user assets, managed by private keys or externally owned accounts (EOAs). Therefore, the properties of smart contract wallets also depend on the application and how its EOA is managed. Similar to threshold key management, smart contract wallets have the advantage of multiple EOAs controlling a single account. In addition, abstract computing can also be utilized to implement functions such as daily spending restrictions or permissions, thereby protecting user assets.
solution
solution
Below we describe a few different products. The features of these products are somewhat different, but hopefully our summary will give you an overview of the current mainstream solutions. If there are any mistakes or omissions, please contactzhen@tor.usErrata.
Metamask
Metamask can be accessed in the normal Chrome browser as a Chrome extension wallet or mobile wallet. Metamask can manage the key on the device, which is easy to operate and non-custodial, but it needs to synchronize the mnemonic with the device
Portis
Use the password manager model to save keys. As a web wallet integrated into the DAPP, Portis utilizes the user's browser iFrame and domain security model to protect the user's keys. Portis has an npm package (a well-known package management tool for javascript) that provides Web3 support for developers.
Fortmatic/Magic
Magic (formerly Ethereum wallet solutions provider Fortmatic) is often mistaken for a password manager model due to its use of a password/email combination. However, they are actually held by HSMs (Hardware Security Modules) and AWS (Amazon Cloud Services). After digging into the inner workings of Fortmatic, we found that its blog also confirmed our conclusion:
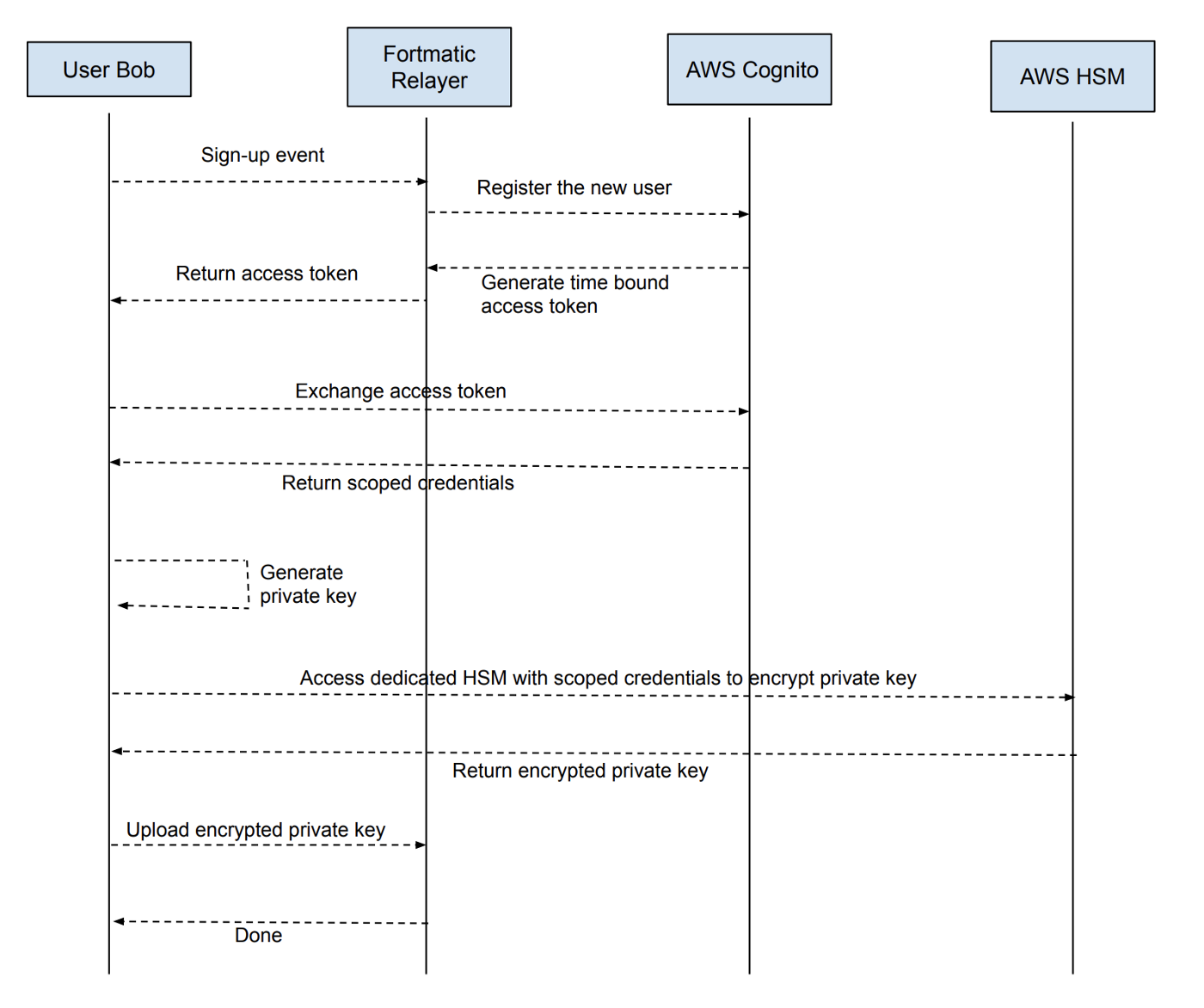
The figure above shows us the interaction flow during the registration process. Explicit authentication of its access key depends on the calling credentials (Access Token). The fortmatic relayer and AWS cognito can also access this call credentials.
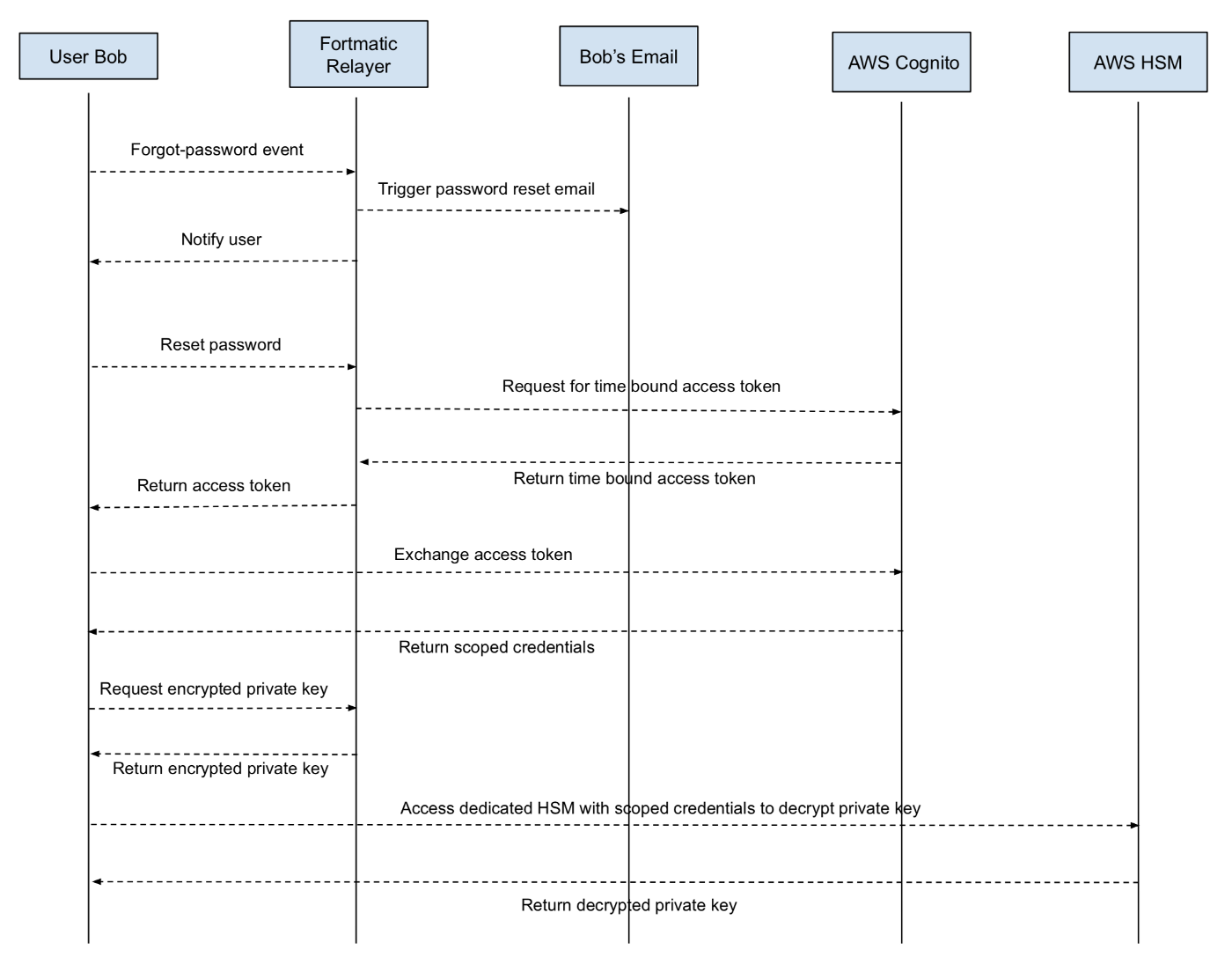
Magic's key recovery process confirms the above conclusion. Unless you're brute-forcing a user's password, key recovery is impossible with the password manager model. But Magic can email, verify and reset your password without knowing your previous password.
Bitski
Bitski is a custodial e-wallet. They never disclose user keys on the front end or in the browser, thus avoiding system vulnerabilities and increasing security.
Argent
Argent uses a smart contract wallet and keys stored in its mobile application. Argent works with other Argent smart contract wallets to implement social recovery and even pay gas fees on behalf of users.
Authereum
Authereum is also a smart contract wallet designed for network use, and its EOA is managed through a password manager model. Authereum supports key recovery, the entire recovery process is done by attaching and downloading another key.
Torus/tKey
Torus implements a threshold model called tKey. They store user keys in shards across devices, inputs, and the Torus network—users can choose any two of the three to recover their keys. Torus network shares/factors are further sharded among its currently licensed node participants. Users access these shards by logging in with OAuth (such as Google, Linkedin, WeChat, etc.).
When users use tKey on different devices, they increase the number of shards they hold, reducing the possibility of losing keys. Users can also choose to increase their threshold, which increases the security of their access keys, creating a two-factor authentication (2FA)-like experience.
Fireblocks
summary
summary




