This article was created by Vitalik Buterin and translated by Eigen Labs. Please click to read the original text to view the original English version. Eigen Team continues to deliver blockchain cutting-edge dry goods content for you~
Special thanks to Itamar Lesuisse from Argent and Daniel Wang from Loopring for their feedback.
Cryptocurrency and blockchain have brought many users concerns about security issues, which hinder them from using cross-chain apps. Both loss of property and theft are serious, often costing innocent blockchain users thousands of dollars and, in some cases, wiping out years of hard-earned savings.
So, how do you prevent users from losing or stealing their funds?
secondary title
Wallet security needs to be resolved urgently
Concerns about wallet security have been prevalent in the blockchain ecosystem almost since its inception. In 2011, when the only cryptocurrency was Bitcoin, lost and stolen keys were very, very rampant. In fact, before I joined Ethereum, as a co-founder and author of Bitcoin Magazine, I wrote an entire article detailing the horrors of hacks, lost coins, and stolen coins that occurred at the time.
Let's look at a case:
Around 9:00 last night, I opened a link on CoinChat, and I was prompted to run java. I thought it was a legitimate chat room, so I followed the prompts, everything was fine, and I closed the window, not thinking about it. About 14 minutes later, I opened my bitcoin-qt wallet, only to find a transaction that I didn't approve, which transferred almost the entire amount of my wallet...
The person's loss was 2.07 bitcoins, worth $300 at the time, and over $70,000 today. There is another case:
In June 2011, Bitcointalk member allinvain lost 25,000 bitcoins (worth $500,000 at the time) when an unknown hacker somehow gained direct access to his computer. The hacker directly manipulated the wallet.dat file in the allinvain computer and quickly emptied his wallet. It is not known whether he let the allinvain computer itself send a transaction or just updated the wallet.dat file so that it was emptied locally.
In today's value, that equates to a loss of nearly $1 billion. But coin theft isn't the only problem. Losing your own private key will also cause property damage. Here is the case of Stefan Thomas:
Bitcoin developer Stefan Thomas has three backups of his wallet — an encrypted USB stick, a Dropbox account, and a Virtualbox virtual machine. Unfortunately, however, he deleted two of them and forgot the passcode for the third, thus forever losing 7,000 bitcoins (worth $125,000 at the time). Thomas' response: "Since then, I've been working on creating better wallet clients."
An analysis of the bitcoin ecosystem shows that up to 1,500 bitcoins are lost every day—a fee that is ten times higher than what users spend on transaction fees. Over the years, the cumulative amount of Bitcoin lost is equivalent to 20% of the total supply. These cases and figures have all confirmed an unavoidable reality without exception: wallet security is of paramount importance, and we should not underestimate the impact of such tragedies on users.
secondary title
Relying on hardware wallets alone? not enough
Hardware wallets are often touted as the best technology for cryptocurrency fund management. A hardware wallet is a specialized hardware device that connects to your computer or phone (for example via USB) and contains a specialized chip that can only generate private keys and sign transactions. Once activated on your computer or phone, the transaction will have to be confirmed by the hardware wallet before it can be sent. The private key is kept on your hardware wallet, so hackers cannot steal your funds if they break into your computer or phone.
Hardware wallets significantly increase security and will protect victims of fake Java chat room attacks. But hardware wallets are clearly not perfect. I think there are two main problems with hardware wallets:
-Supply chain attack: If you buy a hardware wallet, it means that you fully trust the participants involved in the production of it, including the design party, production party and transport party. They can pass off a fake as a hardware wallet. Hardware wallets are potential targets for such attacks, with a very high ratio of stolen funds to the number of devices stolen. However, manufacturers of hardware wallets like Ledger have taken a number of steps to guard against these risks. However, some risks remain. Fundamentally, hardware devices cannot be verified for security like open source software.
secondary title
Relying on mnemonics alone? not enough
Many wallets, whether hardware or software, have a setup process where they output a mnemonic phrase, which is a human-readable 12 to 24 word encoding of the wallet root private key. As shown below:
If you lose your wallet but have a seed phrase, you can restore your account by entering the phrase when setting up a new wallet, since the seed phrase contains the root key from which all your other keys can be retrieved generate.
secondary title
What kind of plan is needed?
The wallet design we need must meet the following three key conditions:
1. No single point of failure: There is no single password or private key that, in the event of theft, would result in loss of funds. Or you can be denied access to your funds if lost.
2. Low mental consumption: As far as possible, users are not required to learn new behaviors, nor do they need to spend brain power to remember certain specific behavior patterns.
secondary title
text
In fact, as early as 2013, multi-signature became the best technology to solve such problems. A user has a wallet with three keys, any two of which are required to send a transaction.
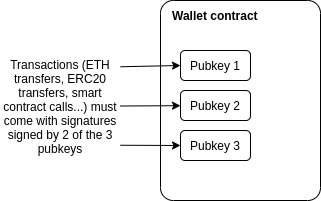
This technology was originally developed in the Bitcoin ecosystem, and now there are excellent multi-signature wallets in Ethereum (eg: Gnosis Safe). Multi-signature wallets are very successful in multi-person co-governance of wallets. The Ethereum Foundation uses a 4-of-7 multi-signature wallet, and many other Ethereum ecological organizations do the same.
For a privately held multisig wallet, the main challenges are: who owns the funds, and how do they approve transactions? The most common scenario is "where the user holds two easily accessible but separate keys, for example, a computer and mobile phone, plus a third, more secure but inaccessible backup kept offline by a friend or institution".
secondary title
Social recovery becomes "darling"
My favorite way to keep your wallet safe is social recovery. The social recovery system works as follows:
1. Only one "signing key" can be used to approve transactions
2. At least 3 (or more) "guardians", most of whom can cooperate to change the signing key of the account.
The signing key has the ability to add or remove guardians, but the whole process takes a while (usually 1-3 days).
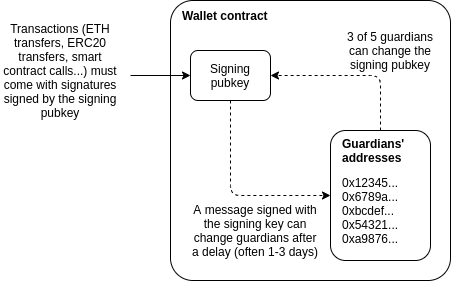
In all normal cases, users can use the social recovery wallet as they would a normal wallet, confirming transactions with their signing keys. This way, each transaction is quickly completed with a single confirmation, just like in "traditional" wallets such as Metamask.
This is where social recovery kicks in if a user loses their signing key. Users simply contact their guardians and ask them to sign a special transaction that changes the signature public key registered in the wallet contract to a new signature. This is much simpler: the guardian can visit a web page, such as security.loopring, view the recovery request and sign it. The whole process is as simple as a Uniswap transaction.
The three most common guardian options are:
1. Other device (or paper seed phrase) owned by the wallet holder
2. Friends and family
3. Agency (will sign recovery information upon receipt of confirmation from your phone number or email, or if necessary, verify your identity in person via video call)
Guardians are easy to add: you can simply enter their ENS name or ETH address (but most social recovery wallets will require guardians to sign transactions on the recovery web page). In any properly designed social recovery wallet, guardians do not need to download and use the same wallet as the owner of the funds, but can use any type of Ethereum wallet. Now that adding guardians is so convenient, if you have a large number of Ethereum users in your social circle, you may wish to choose more guardians (ideally more than 7), which is especially safe. If you already have a wallet, there is no need to worry about guardians, any recovery operations you do will be done through your existing wallet. If you don't know too many Ethereum users, you can choose to set up less technically trusted guardians.
In order to reduce the risk of guardians being attacked and guardians jointly doing evil, users' guardians do not have to be made public: guardians do not need to know each other's identities. This can be achieved in two ways. First, instead of storing the guardian's address directly on-chain, store the hash of the list of addresses on-chain. Wallet owners only need to publish the full list when restored. Second, each guardian is required to generate a unique address for a specific recovery. This means they can use this address to send any transaction except in the case of recovery. To aid in the implementation of these protections, users are advised to choose a diverse mix of guardians from different social circles (ideally including an institutional guardian); the above recommendations will make it difficult for guardians to be attacked simultaneously or to do evil together.
secondary title
Social recovery is not betrayal
A common perception of proposals to use multisig, social recovery, or other forms is that such solutions all stem from trust in people, which is a betrayal of the values of the blockchain and cryptocurrency industry. There is nothing wrong with thinking this way, but what I want to say is that this criticism comes from users' misunderstanding and prejudice against encryption technology.
To me, the goal of cryptocurrencies has never been to eliminate the need for trust, but to give people the power to choose who to trust by providing encrypted economic blocks, and allow people to build trust based on constraints. The point to make is that empowering someone doesn't mean giving them the power to do whatever they want. Viewed in this light, multisig and social recovery are a perfect embodiment of this principle: each participant has some influence over the ability to accept or reject transactions, but no one can unilaterally transfer funds. This logic is more complicated, but it establishes a safer mechanism.
secondary title
How does social recovery prevent stolen coins?
As mentioned above, social recovery can effectively mitigate the risk of users losing their wallets. The risk of signing key theft is not completely eliminated: say someone hacks into your computer while you are logged in, or takes control of your computer by brute force, or even just uses some user interface glitch to trick you into signing certain transactions. These possibilities have laid hidden dangers for key theft.
secondary title
Existing social recovery wallets
At present, there are mainly two types of wallets that implement social recovery: Argent wallet and Loopring wallet:
Argent Wallet is currently the first mainstream and most popular "smart contract wallet", and social recovery is one of its main selling points. The Argent wallet includes an interface to add and remove guardians:
In order to prevent coin theft, the wallet has a daily limit: transactions within the daily limit can be completed instantly, but transactions exceeding this amount require the approval of the guardian to complete the withdrawal.
secondary title
Migrating to Layer2 - Addressing remaining challenges
As mentioned above, there are two key challenges: (1) reliance on relayers to complete transactions; (2) high transaction fees. The first challenge stems from relayer dependencies, an increasingly common problem in Ethereum applications. This problem arises because there are two types of accounts in Ethereum: externally owned accounts (EOAs), which are accounts controlled by a single private key, and contract accounts. Every transaction in Ethereum must start with an EOA; EOAs represent "users", contracts represent "applications", and applications can only run if the user interacts with them. If we want to have wallets with complex policies like multisig and social recovery, we need to use contracts to represent users. The challenge with this is that if your funds are in the contract, you need to have some other account with ethereum to be able to start trading, and it also requires quite a bit of ethereum in case transaction fees sometimes become very high.
Argent and Loopring solve this problem by running a "repeater". The relayer listens for off-chain digitally signed "messages" submitted by users, and wraps these messages in a transaction and publishes them on-chain. But in the long run this is not a good solution as it adds an extra center point. If users do need to make a transaction with relayers down, they can send it from their EOA, but there is always a trade-off between centralization and inconvenience anyway. People struggle to solve this problem and gain convenience without adopting centralized solutions; the main solutions are either to create a generalized decentralized relay network, or to modify the Ethereum protocol so that transactions can start from contracts. But neither of these solutions solves the problem of transaction fees, and in fact, they are more inconvenient due to the inherently complex nature of smart contracts themselves.
Fortunately, we can solve both problems at the same time by finding a third solution: shifting the ecosystem to Layer 2 protocols such as optimistic rollups and ZK rollps. Both optimistic rollups and ZK rollups can be designed with built-in account abstractions, avoiding the need for relayers. Therefore, wallet developers focused on the migration process of rollups. This is also a big challenge to the entire ecosystem.
secondary title
Eigen Network
Eigen Network is the first end-to-end privacy computing network on Layer2.
Based on privacy computing technologies such as TEE and unlimited expansion of Layer 2 computing power, Eigen can solve two problems currently facing: 1) data privacy leakage on the chain caused by the openness of natural data in the blockchain; 2) problems caused by insufficient scalability of ETH The problem of high fees. In addition, Eigen will also reform the current production relationship of data assets on the chain, consider individual privacy protection from application scenarios to technology stacks, and become a developer-friendly and feasible privacy protection infrastructure for the development of Web2 to Web3. Convert contributions.



