Beosin's Annual Highlight | 2025 Web3 Blockchain Security Landscape Report
- 核心观点:2025年Web3安全损失达33.75亿美元,黑客攻击激增。
- 关键要素:
- 黑客攻击损失31.87亿美元,同比大增77.85%。
- 中心化交易所损失最高,占52.3%,Bybit事件损失14.4亿。
- 以太坊链损失占比66.79%,合约漏洞利用为最常见攻击手法。
- 市场影响:凸显基础设施与供应链安全为行业核心挑战。
- 时效性标注:中期影响

*This report was jointly produced by Beosin and Footprint Analytics. Reply "2025" in the official WeChat account to get the full report.
*This article is the 2025 Web3 Security Landscape Report. We will release reports on virtual asset anti-money laundering compliance and other related topics in the future. Please continue to follow the Beosin WeChat official account.
Foreword
This research report, initiated by the Blockchain Security Alliance and co-authored by alliance members Beosin and Footprint Analytics, aims to comprehensively explore the global blockchain security landscape in 2025. Through analysis and assessment of the current state of global blockchain security, the report will reveal the current security challenges and threats, and provide solutions and best practices. Blockchain security and regulation are key issues in the development of the Web3 era. Through in-depth research and discussion in this report, we can better understand and address these challenges to promote the security and sustainable development of blockchain technology.
1. Overview of Web3 Blockchain Security Landscape in 2025
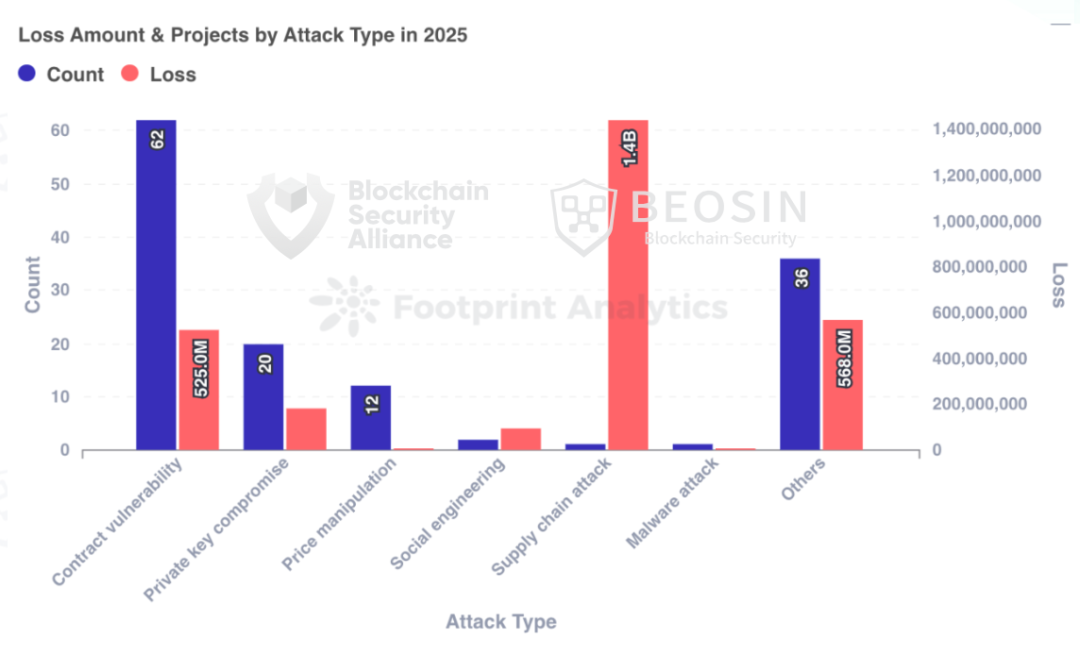
According to Alert, a platform under Beosin, a blockchain security and compliance technology company, the total losses in the Web3 space due to hacking, phishing scams, and project rug pulls reached $3.375 billion in 2025. There were a total of 313 major blockchain security incidents, including 191 hacking incidents with total losses of approximately $3.187 billion; project rug pulls with total losses of approximately $11.5 million; and 113 phishing scams with total losses of approximately $177 million.
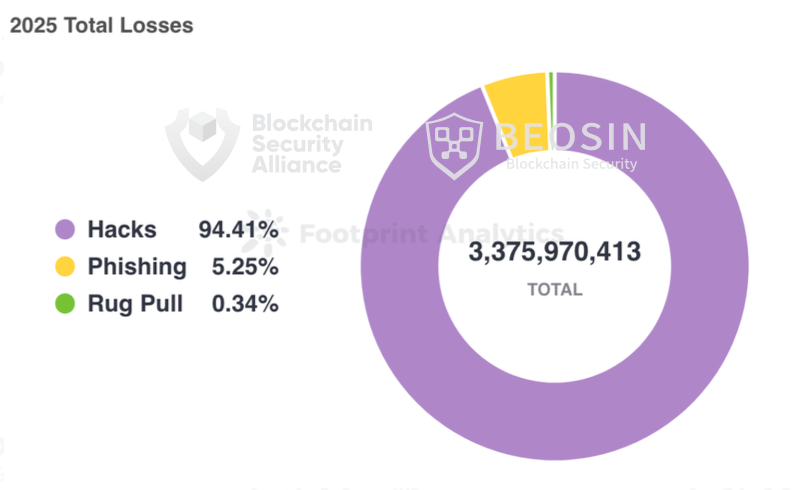
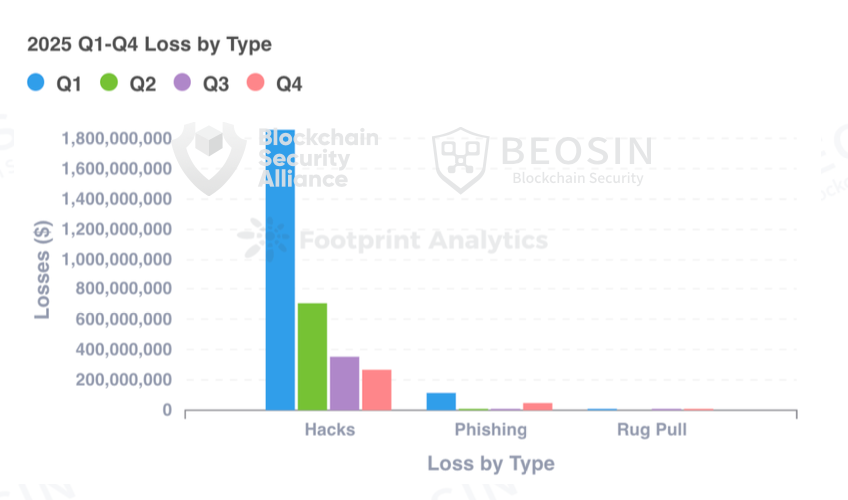
The first quarter of 2025 saw the most significant losses, with the vast majority stemming from the Bybit hack. While the amount of money lost due to the hack continued to decline quarter by quarter, it saw a substantial increase compared to 2024, rising by 77.85%. Losses from phishing scams and Rug Pull incidents both decreased significantly compared to 2024, with phishing scam losses decreasing by approximately 69.15% and Rug Pull losses decreasing by approximately 92.21%.
In 2025, the types of projects attacked included DeFi, CEXs, public blockchains, cross-chain bridges, NFTs, Memecoin trading platforms, wallets, browsers, third-party code packages, infrastructure, and MEV bots, among others. DeFi remained the most frequently attacked project type, with 91 attacks targeting DeFi resulting in losses of approximately $621 million. CEXs suffered the highest total losses, with 9 attacks targeting CEXs causing losses of approximately $1.765 billion, accounting for 52.30% of the total losses.
In 2025, Ethereum remained the public blockchain with the highest losses , with 170 security incidents on Ethereum causing approximately $2.254 billion in losses, accounting for 66.79% of the total losses for the year.
In terms of attack methods, the Bybit incident caused approximately $1.44 billion in losses due to supply chain attacks, accounting for 42.67% of the total losses, making it the most damaging attack method. Besides this, contract exploitation was the most frequent attack method , accounting for 62 out of 191 attacks (32.46%).
2. Top Ten Security Incidents in 2025
In 2025, there were three security incidents that resulted in losses exceeding $100 million: Bybit ($1.44 billion), Cetus Protocol ($224 million), and Balancer ($116 million) . Following these were Stream Finance ($93 million), BTC whales ($91 million), Nobitex ($90 million), Phemex ($70 million), UPCX ($70 million), Ethereum users ($50 million), and Infini ($49.5 million).
Unlike previous years, two of this year's top 10 security incidents involved significant losses for individual users , caused by social engineering/phishing attacks. While these attacks are not the most financially damaging, their frequency is increasing annually, making them a major threat to individual users.
*Details of the top ten security incidents can be viewed in the full report.
3. Types of projects attacked
Centralized exchanges became the project type with the highest losses.
In 2025, centralized exchanges suffered the most losses, with nine attacks targeting them resulting in approximately $1.765 billion in losses , accounting for 52.30% of the total losses. Bybit suffered the largest loss, approximately $1.44 billion. Other exchanges with significant losses included Nobitex (approximately $90 million), Phemex (approximately $70 million), BTCTurk ($48 million), CoinDCX ($44.2 million), SwissBorg ($41.3 million), and Upbit ($36 million).
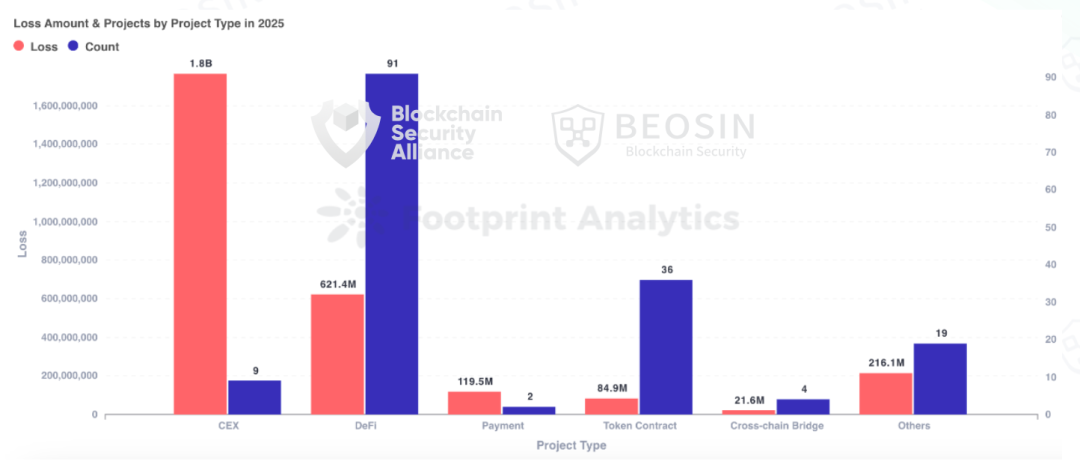
DeFi was the most frequently attacked project type , with 91 attacks targeting DeFi resulting in losses of approximately $621 million, ranking second in terms of total losses . Cetus Protocol suffered a loss of approximately $224 million, accounting for 36.07% of the total stolen DeFi funds, while Balancer lost approximately $116 million. Other DeFi projects with significant losses included Infini ($49.5 million), GMX ($40 million), Abracadabra Finance ($13 million), Cork Protocol ($12 million), Supply ($9.6 million), zkLend ($9.5 million), Ionic ($8.8 million), and Alex Protocol ($8.37 million).
4. Loss details for each chain
Ethereum suffered the highest amount of losses and had the most security incidents.
As in previous years, Ethereum remains the public blockchain with the highest amount of losses and the most security incidents. 170 security incidents on Ethereum resulted in losses of approximately $2.254 billion, accounting for 66.79% of the total losses for the year.
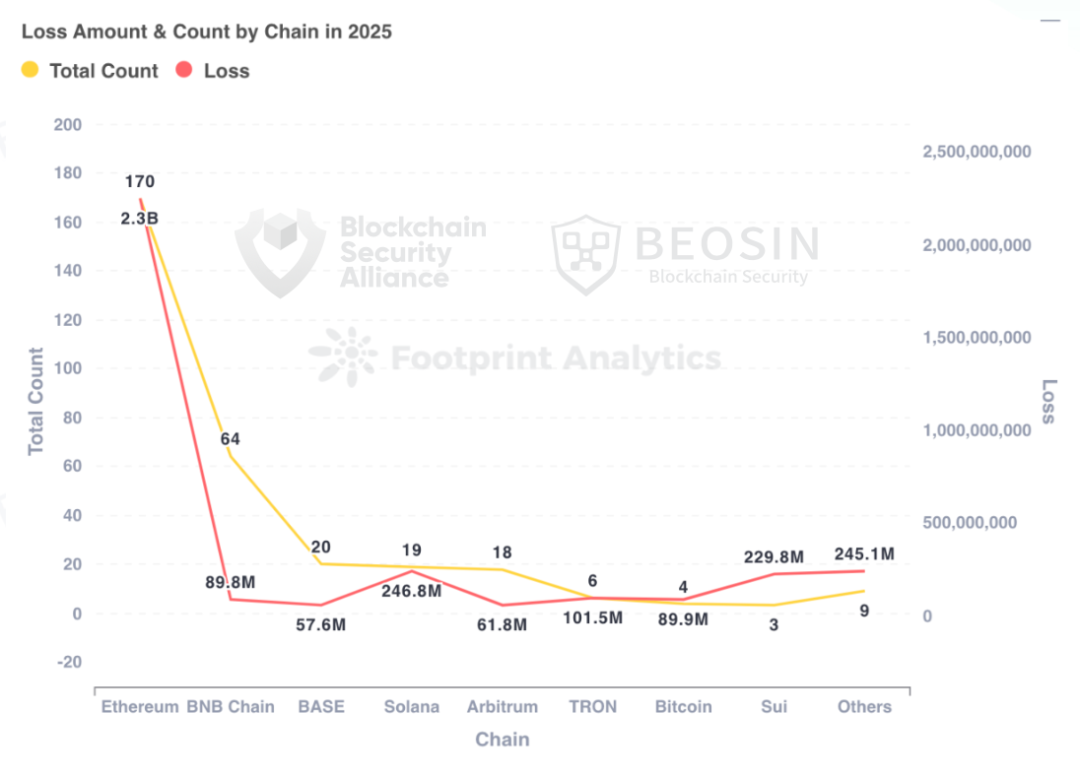
The public blockchain ranking second in terms of the number of security incidents is BNB Chain , with 64 security incidents resulting in losses of approximately $89.83 million. While BNB Chain experienced a high number of on-chain attacks, the total amount of losses was relatively small . However, compared to 2024, both the number of security incidents and the amount of losses increased significantly, with the amount of losses increasing by 110.87%.
Base ranks third in terms of the number of security incidents, with a total of 20 incidents. Solana follows closely behind with 19 security incidents.
5. Analysis of attack methods
Contract vulnerability exploitation is the most frequent attack method.
Of the 191 attacks, 62 were contract vulnerability exploits , accounting for 32.46%, resulting in a total loss of $556 million. This was the largest type of attack in terms of financial loss, second only to Bybit's supply chain attack.
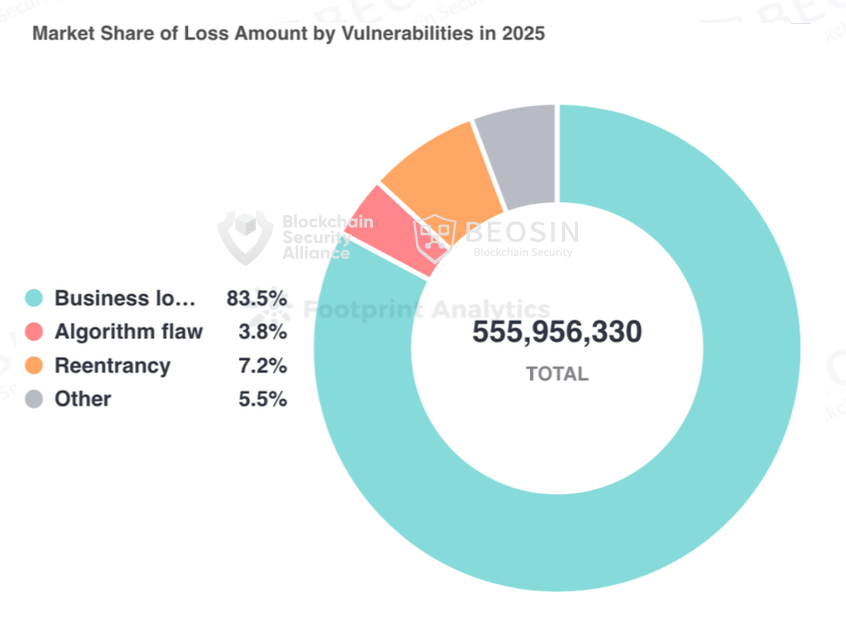
According to the breakdown of contract vulnerabilities, the most damaging vulnerability was the business logic vulnerability, which resulted in losses of $464 million. The top three most frequent contract vulnerabilities were business logic vulnerabilities (53 times), access control vulnerabilities (7 times), and algorithmic flaws (5 times).
There were 20 private key breaches this year, resulting in total losses of approximately $180 million. The number of breaches and the resulting losses are significantly lower than last year . Exchanges, project teams, and users have shown increased awareness of private key protection.
6. Typical Security Incident Attack Analysis
6.1 Analysis of the Cetus Protocol $224 Million Security Incident
Event Summary
On May 22, 2025, the DEX Cetus Protocol on the Sui ecosystem was attacked. The vulnerability stemmed from an implementation error in the left shift operation within the open-source library code. Taking one of the attack transactions (https://suivision.xyz/txblock/DVMG3B2kocLEnVMDuQzTYRgjwuuFSfciawPvXXheB3x?tab=Overview) as an example, the simplified attack steps are as follows:
1. Enable flash loans: The attacker borrowed 10 million haSUI through flash loans.
2. Create a liquidity position: Open a new liquidity position with a price range of [300000, 300200].
3. Increased Liquidity: Using only 1 unit of haSUI increased liquidity, but yielded a liquidity value of up to 10,365,647,984,364,446,732,462,244,378,333,008.
4. Remove Liquidity: Immediately remove liquidity from multiple transactions to deplete the liquidity pool.
5. Repay Flash Loans: Repay flash loans and retain approximately 5.7 million SUIs as profit.
Vulnerability Analysis
The root cause of this attack lies in an implementation error in the `checked_shlw` function of `get_delta_a`, which caused the overflow check to fail. Attackers only need a small number of tokens to exchange for a large amount of assets in the liquidity pool, thus enabling the attack.
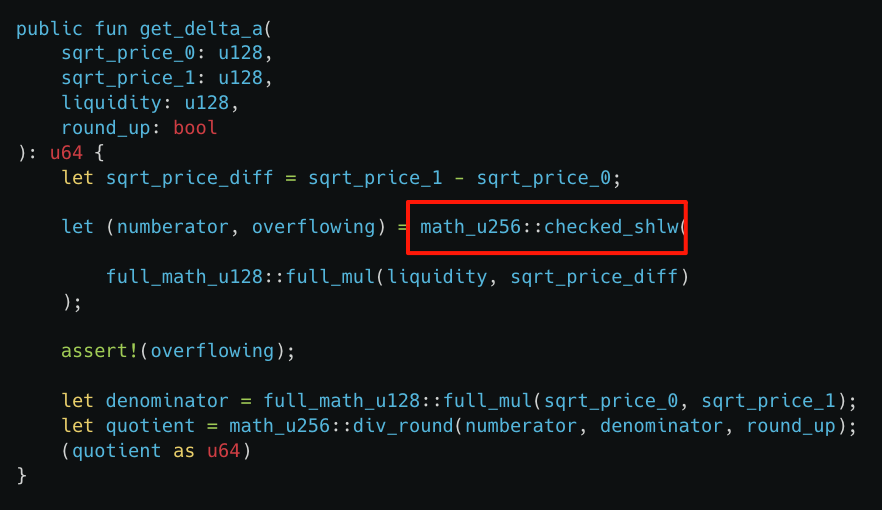
As shown in the diagram, `checked_shlw` is used to determine whether shifting the u256 number left by 64 bits will cause an overflow. Input values less than 0xffffffffffffffff << 192 will bypass the overflow detection, but the input value may exceed the maximum value of u256 after shifting left by 64 bits (overflow). `checked_shlw` will still output "no overflow occurred" (false). This will severely underestimate the number of tokens required in subsequent calculations.
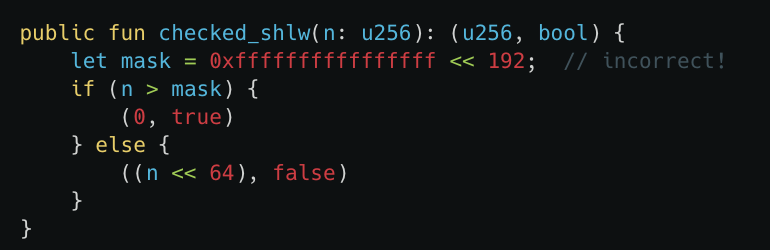
Furthermore, in Move, integer arithmetic is designed to prevent overflow and underflow, as these can lead to unexpected behavior or vulnerabilities. Specifically: if the result of addition and multiplication is too large for an integer type, the program will terminate. If the divisor is zero, division will terminate.
The unique feature of left shift (<<) is that it does not stop when an overflow occurs. This means that even if the number of bits shifted exceeds the storage capacity of the integer type, the program will not terminate, which may lead to erroneous values or unpredictable behavior.
6.2 Balancer $116 Million Security Incident Analysis
On November 3, 2025, the Balancer v2 protocol was attacked, resulting in losses of approximately $116 million across multiple blockchains for several projects, including its fork protocol. For example, the attacker's transaction on Ethereum was: 0x6ed07db1a9fe5c0794d44cd36081d6a6df103fab868cdd75d581e3bd23bc9742
1. The attacker first launched an attack transaction through the bulk swap function, using BPT to swap out a large number of liquidity tokens from the pool, causing the pool's liquidity token reserves to become very low.
2. The attackers then began swapping liquidity tokens (osETH/WETH).
3. Then exchange the liquidity tokens back into BPT tokens, and repeat the above operation in multiple pools.
4. Finally, withdraw the money to realize your profit.
Vulnerability Analysis
ComposableStablePools uses Curve's StableSwap invariant formula to maintain price stability among similar assets. However, scaling operations during invariant calculations introduce errors.
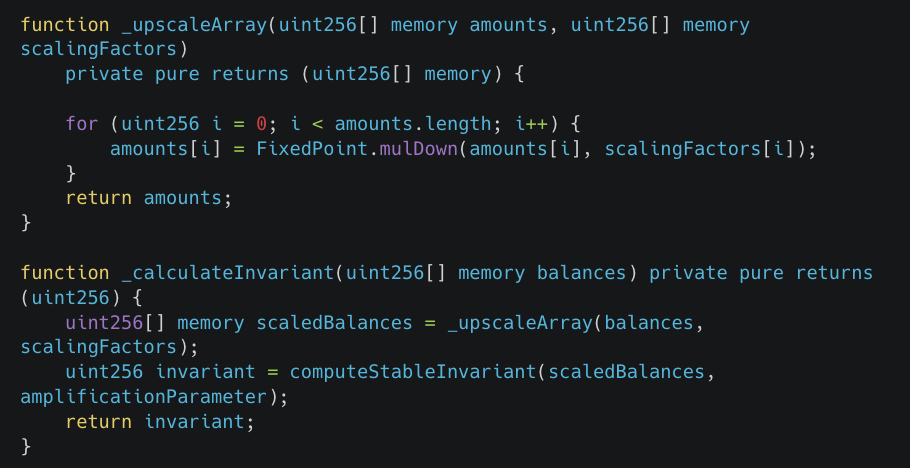
The mulDown function performs integer division down to the floor. This precision error is propagated to the calculation of invariants, causing the calculated value to be abnormally low, thus creating an opportunity for attackers to profit.
7. Analysis of Typical Anti-Money Laundering Cases
7.1 US sanctions against drug cartel led by Ryan James Wedding
According to documents disclosed by the U.S. Treasury Department, Ryan James Wedding and his team smuggled tons of cocaine through Colombia and Mexico and sold it to the United States and Canada. Their criminal organization used cryptocurrency to launder money, thereby accumulating vast sums of illicit wealth.
Using Beosin Trace, an on-chain tracing and investigation tool owned by Beosin, we analyzed the cryptocurrency addresses associated with Wedding's drug trafficking group. The results are shown below:
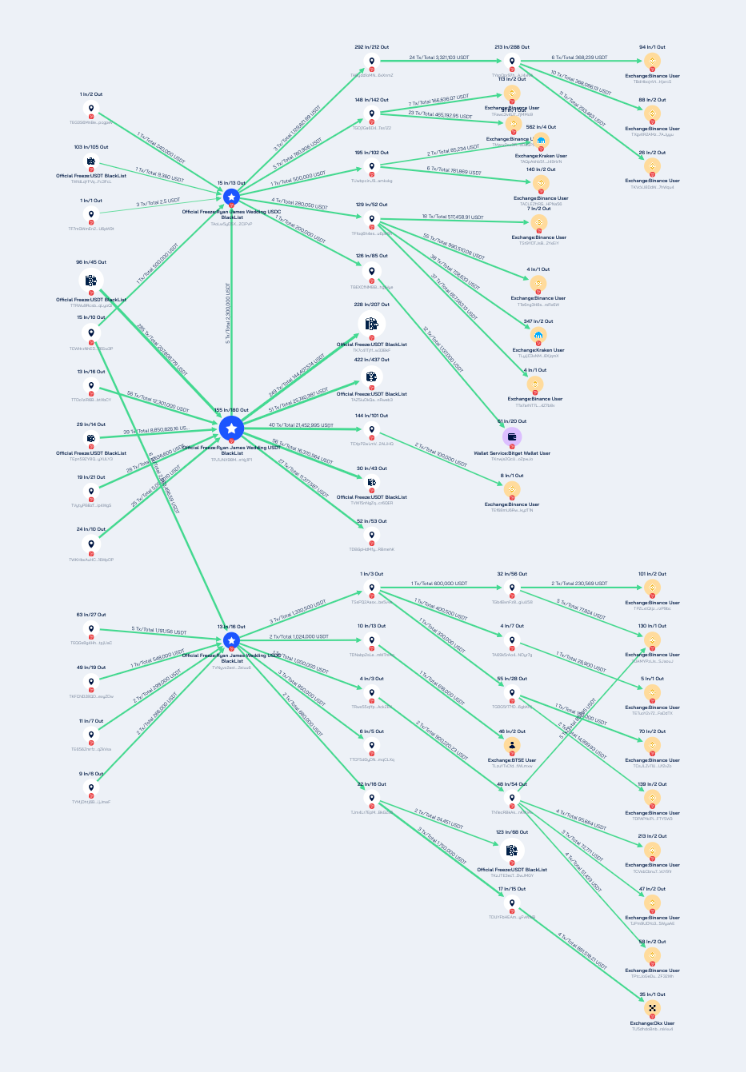
The addresses held by the three Weddings, TAoLw5yD5XUoHWeBZRSZ1ExK9HMv2CiPvP, TVNyvx2astt2AB1Us67ENjfMZeEXZeiuu6 and TPJ1JNX98MJpHueBJeF5SVSg85z8mYg1P1, handled a total of 266,761,784.24 USDT. Some of these assets have been frozen by Tether, but most of them have been laundered through high-frequency trading addresses and multi-level transfers, and deposited into platforms such as Binance, OKX, Kraken, and BTSE .
The Sokolovski group holds addresses on multiple blockchain networks (BTC, ETH, Solana, TRON, BNB Beacon Chain), and the analysis of their fund flows can be viewed in the full report.
7.2 GMX $40 million theft case
On July 10, 2025, GMX was compromised due to a reentrancy vulnerability, resulting in hackers profiting approximately $42 million. Beosin Trace's investigation of the stolen funds revealed that the attacker's address, 0x7d3bd50336f64b7a473c51f54e7f0bd6771cc355, used DEX protocols to exchange various stablecoins and altcoins for ETH and USDC, and then transferred the stolen assets to the Ethereum network through multiple cross-chain protocols.
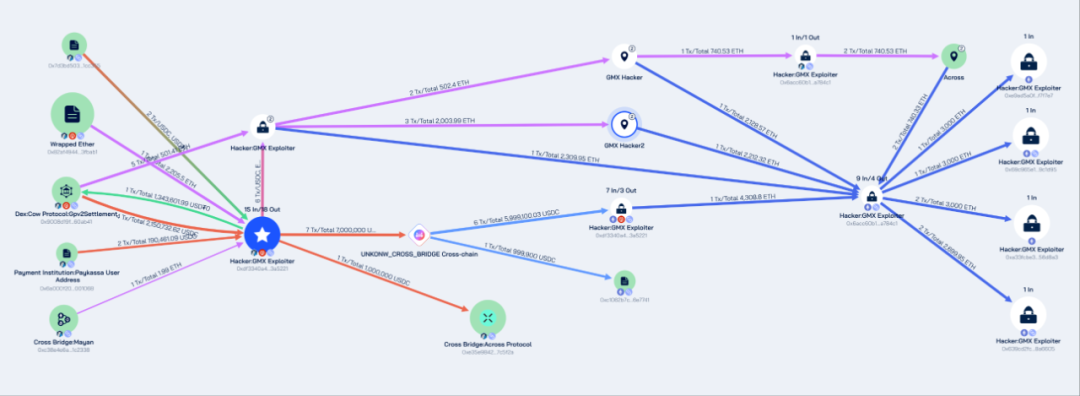
Subsequently, approximately 32 million ETH worth of the stolen GMX assets were stored in the following four Ethereum network addresses:
0xe9ad5a0f2697a3cf75ffa7328bda93dbaef7f7e7
0x69c965e164fa60e37a851aa5cd82b13ae39c1d95
0xa33fcbe3b84fb8393690d1e994b6a6adc256d8a3
0x639cd2fc24ec06be64aaf94eb89392bea98a6605
Approximately $10 million in assets were stored at address 0xdf3340a436c27655ba62f8281565c9925c3a5221 on the Arbitrum network.
The money laundering path in this incident is very typical. Hackers used DeFi protocols, cross-chain bridges, and other methods to obfuscate and hide the path of funds in order to evade tracking and freezing by regulatory agencies and law enforcement agencies.
8. Summary of Web3 Blockchain Security Landscape in 2025
In 2025, losses from phishing scams and project-driven rogue pulls both decreased significantly compared to 2024. However, hacker attacks remained frequent, resulting in losses exceeding $3.1 billion , with exchanges still suffering the highest losses. Meanwhile, security incidents related to private key breaches decreased. The main reasons for this shift include:
Following last year's rampant hacking activities, the entire Web3 ecosystem is placing greater emphasis on security this year. From project teams to security companies, efforts are being made in various aspects, such as internal security operations, real-time on-chain monitoring, increased focus on security audits, and actively learning from past contract vulnerability exploitation incidents. Security awareness is being continuously strengthened in areas such as private key custody and project operational security. As contract vulnerabilities and the theft of private keys become increasingly difficult, hackers are beginning to use other methods, such as supply chain attacks and front-end vulnerabilities, to trick users into transferring assets to addresses controlled by hackers .
Furthermore, with the integration of the crypto market and the traditional market, attack targets are no longer limited to DeFi, cross-chain bridges, and exchanges, but have shifted to a variety of targets such as payment platforms, gambling platforms, crypto service providers, infrastructure, development tools, and MEV bots . The focus of attacks has also shifted to more complex protocol logic flaws .
For individual users, social engineering/phishing attacks and potential coercion pose significant threats to their personal assets . Currently, many phishing attacks go unreported or unrecorded due to the small amounts involved and the victims being individual users, leading to an underestimation of their losses. However, users should raise their awareness of how to prevent such attacks . Furthermore, physical methods of coercion, such as kidnapping, targeting crypto users have occurred repeatedly this year. Users must protect their personal identification information and minimize the public exposure of their crypto assets.
Overall, Web3 security in 2025 still faces significant challenges, and project teams and individual users cannot afford to be complacent. In the future, supply chain security is likely to become paramount for Web3 security. How to continuously protect various infrastructure service providers within the industry and monitor and alert on threats in the supply chain is a major challenge that all parties in the industry need to address collectively . Furthermore, AI-driven social engineering/phishing attacks are likely to continue to increase , necessitating the construction of a multi-layered, real-time, and dynamic defense system, from individual awareness and technological barriers to community collaboration.



