A New Front in the North-South Korean Secret War: Upbit, North Korean Hackers' "Nuclear ATM"?
- 核心观点:韩国交易所屡遭国家级黑客攻击。
- 关键要素:
- Upbit再被盗3680万美元资产。
- 朝鲜黑客组织Lazarus为主谋。
- 累计损失超2亿美元。
- 市场影响:暴露交易所安全脆弱性。
- 时效性标注:长期影响
Original title: "Kimchi Premium vs. State Hacking: The North-South Korean Undercurrents After Upbit's Repeated Thefts"
Original author: Deep Tide TechFlow
The market rebounded, but the exchange was hacked again.
On November 27, Upbit, South Korea’s largest cryptocurrency exchange, confirmed a security breach that resulted in the loss of approximately 54 billion won (about US$36.8 million) in assets.
At 04:42 AM Seoul time (KST) on November 27, while most South Korean traders were still asleep, Upbit's Solana hot wallet address experienced an unusually large outflow of funds.
According to on-chain monitoring data from security organizations such as SlowMist, the attackers did not use a single asset transfer method, but instead carried out a "clear-out" plunder of Upbit's assets on the Solana chain.
The stolen assets included not only the core token SOL and the stablecoin USDC , but also almost all the mainstream SPL standard tokens within the Solana ecosystem.
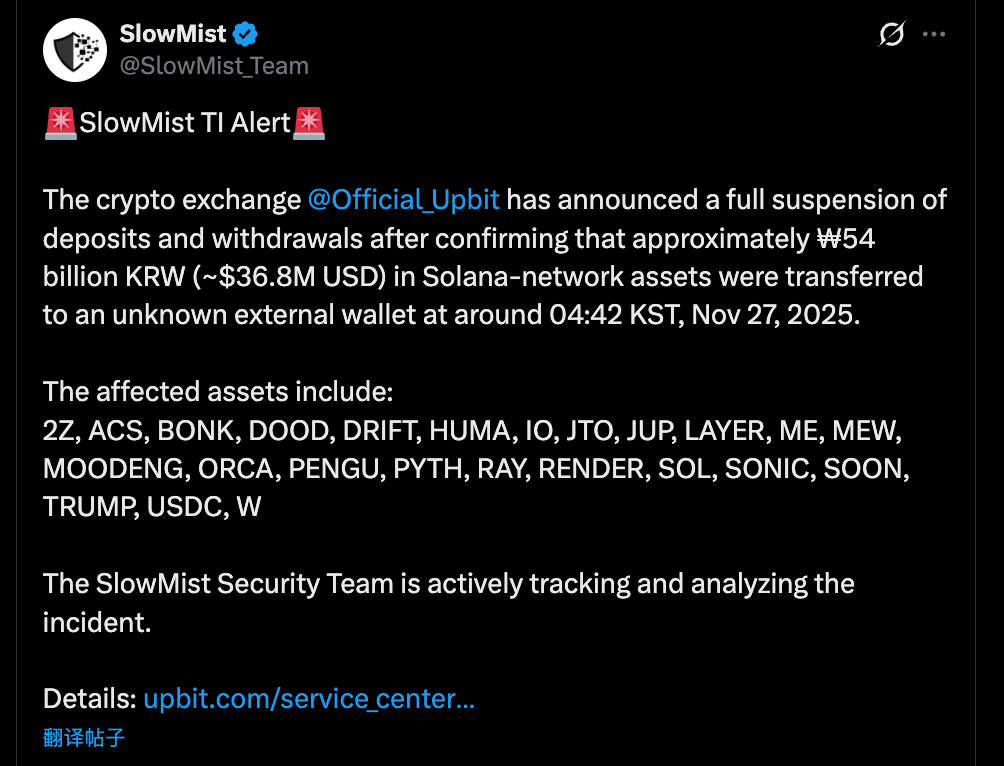
List of stolen assets (partial):
- DeFi/Infrastructure : JUP (Jupiter), RAY (Raydium), PYTH (Pyth Network), JTO (Jito), RENDER, IO, etc.
- Memes/community-related : BONK, WIF, MOODENG, PENGU, MEW, TRUMP, etc.
- Other projects include: ACS, DRIFT, ZETA, SONIC, etc.
This sweeping attack suggests that the attackers likely gained access to the private key of Upbit's hot wallet for the Solana ecosystem, or that the signing server was directly controlled, enabling them to authorize the transfer of all SPL tokens under that wallet.
For Upbit, a giant that holds 80% of the South Korean market share and prides itself on having the highest security level certification from the Korea Internet & Security Agency (KISA), this is undoubtedly a painful breach of its defenses.
However, this is not the first time that a South Korean stock exchange has been hacked.
If we extend the timeline, we will find that the South Korean crypto market has actually been targeted by hackers, especially North Korean hackers, for the past eight years.
The South Korean cryptocurrency market is not only the world's most frenzied casino for retail investors, but also the most convenient "cash cow" for North Korean hackers.
Eight years of North-South Korean conflict, a stolen chronicle
From early brute-force attacks to later social engineering infiltrations, the attack methods have continuously evolved, and the history of suffering for Korean stock exchanges has also been prolonged.
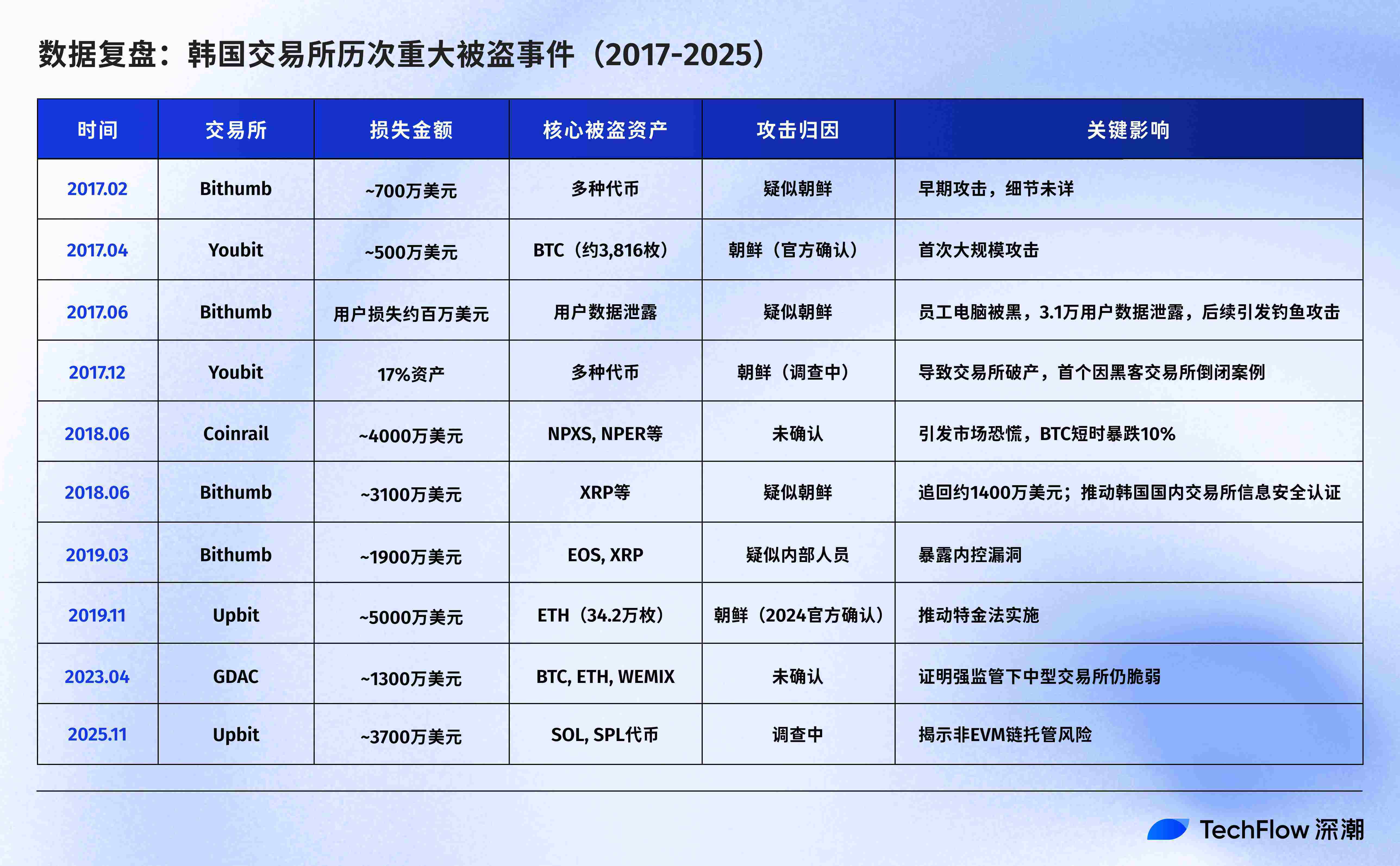
Total losses: Approximately $200 million (based on the price at the time of the theft; if calculated at current prices, it exceeds $1.2 billion, of which the 342,000 ETH stolen from Upbit in 2019 alone are now worth over $1 billion).
2017: The Wilderness Era - Hackers Target Employee Computers
2017 marked the beginning of the crypto bull market, but also the start of a nightmare for South Korean exchanges.
That year, Bithumb, South Korea's largest online exchange, was the first to be affected. In June, hackers broke into a Bithumb employee's personal computer, stealing the personal information of approximately 31,000 users. They then used this data to launch targeted phishing attacks, stealing about $32 million. Subsequent investigations revealed that the employee's computer contained unencrypted customer data, and the company hadn't even installed basic security updates.
This exposed the rudimentary state of security management at the South Korean stock exchange at the time, where even basic principles like "don't store customer data on personal computers" were not established.
Even more significant was the collapse of the mid-sized exchange Youbit. This exchange suffered two devastating blows within a year: losing nearly 4,000 bitcoins (approximately $5 million) in April, and then having 17% of its assets stolen in December. Overwhelmed, Youbit declared bankruptcy, with users only able to withdraw 75% of their balance, the remainder awaiting a lengthy liquidation process.
Following the Youbit incident, the South Korean Internet Security Agency (KISA) publicly accused North Korea of being behind it for the first time. This also sent a signal to the market:
The exchanges are no longer dealing with ordinary cyber thieves, but with state-sponsored hacking groups with geopolitical motives.

2018: The Hot Wallet Heist
In June 2018, the South Korean market suffered a series of severe blows.
On June 10, mid-sized exchange Coinrail was attacked, suffering losses exceeding $40 million. Unlike previous attacks, this time the hackers primarily targeted then-popular ICO tokens (such as Pundi X's NPXS), rather than Bitcoin or Ethereum. Following the news, the price of Bitcoin briefly plummeted by over 10%, and the entire crypto market lost over $40 billion in market capitalization within two days.
Just ten days later, Bithumb, a leading South Korean exchange, also suffered a breach, with approximately $31 million worth of XRP and other tokens stolen from its hot wallet. Ironically, just days before the attack, Bithumb had announced on Twitter that it was "transferring assets to cold wallets to upgrade its security system."
This is the third time Bithumb has been hacked in a year and a half.
The series of defaults severely damaged market confidence. Following the incident, the South Korean Ministry of Science and Technology conducted a security audit of 21 domestic exchanges, finding that only 7 passed all 85 checks, while the remaining 14 were "at risk of being exposed to hacker attacks at any time," with 12 of them having serious vulnerabilities in their cold wallet management.
2019: Upbit's 342,000 ETH stolen
On November 27, 2019, Upbit, South Korea’s largest cryptocurrency exchange, suffered what was then the largest single theft in the country’s history.
Hackers took advantage of exchanges' wallet cleanup to transfer 342,000 ETH in a single transaction. Instead of immediately dumping the funds, they used "peel chain" technology to break the money down into countless small transactions, transferring it layer by layer until it finally ended up in dozens of non-KYC exchanges and mixers.
The investigation revealed that 57% of the stolen ETH was exchanged for Bitcoin at a discount of 2.5% below market price on exchanges suspected to be operated by North Korea, while the remaining 43% was laundered through 51 exchanges in 13 countries.
It wasn't until November 2024, five years later, that South Korean police officially confirmed the case was perpetrated by the North Korean hacking groups Lazarus Group and Andariel. Investigators identified the attackers through IP tracking, financial flow analysis, and the North Korean-specific term "흘한일" (meaning "not important") appearing in the attack code.
South Korean authorities collaborated with the US FBI to track the assets, and after four years of legal proceedings, finally recovered 4.8 bitcoins (approximately 600 million won) from a Swiss exchange, which were then returned to Upbit in October 2024.
However, compared to the total amount stolen, the amount recovered is almost negligible.
2023: GDAC Event
On April 9, 2023, mid-sized exchange GDAC suffered an attack, losing approximately $13 million—23% of its total assets under custody.
The stolen assets included approximately 61 BTC, 350 ETH, 10 million WEMIX tokens, and 220,000 USDT. The hackers took control of GDAC's hot wallet and quickly laundered some of the funds using the Tornado Cash mixer.
2025: Six years later, on the same day, Upbit fell victim again.
On the same day six years ago (November 27), Upbit lost 342,000 ETH.
History has repeated itself. At 4:42 a.m., Upbit's Solana hot wallet experienced an unusual outflow of funds, with approximately 54 billion won (US$36.8 million) transferred to an unknown address.
Following the Upbit incident in 2019, South Korea officially implemented the Specific Financial Information Act (Special Financial Information Act) in 2020, requiring all exchanges to obtain ISMS (Information Security Management System) certification and open real-name accounts with banks. Many smaller exchanges that failed to meet the requirements were forced to exit the market, shrinking the industry landscape from a "hundred-exchange battle" to one dominated by a few giants. Upbit, backed by resources from the Kakao group and having obtained certification, once held a market share exceeding 80%.
However, six years of compliance efforts did not save Upbit from this crisis.
As of press time, Upbit has announced that it will fully compensate users for their losses with its own assets, but the company has not yet released detailed information regarding the attacker's identity and the specific attack path.
Kimchi premium, state-owned hackers and nuclear weapons
The frequent hacking of South Korean stock exchanges is not simply a matter of technological incompetence, but a tragic reflection of geopolitics.
In a highly centralized market with extremely high liquidity premiums and a unique geographical location, the Korean exchange is essentially using the security budget of a commercial company to fight against a national-level hacking force with nuclear deterrence aspirations.
This unit has a name: Lazarus Group.

Lazarus, belonging to the North Korean Reconnaissance General Bureau (RGB), is one of Pyongyang's most elite cyber warfare forces.
Before turning to cryptocurrencies, they had already proven their strength in the traditional financial sector.
In 2014, they breached Sony Pictures; in 2016, they stole $81 million from the Central Bank of Bangladesh; and in 2017, they orchestrated the WannaCry ransomware attack that affected 150 countries.
Starting in 2017, Lazarus shifted its focus to the cryptocurrency field. The reason is simple:
Compared to traditional banks, cryptocurrency exchanges are more loosely regulated, have inconsistent security standards, and once they succeed, funds can be quickly transferred across borders via on-chain transfers, bypassing international sanctions.
South Korea happens to be the ideal hunting ground.
First, South Korea is a natural target for geopolitical confrontation. For North Korea, attacking South Korean companies not only provides access to funds but also creates chaos in an "enemy country," achieving two goals at once.
Secondly, the premium on cryptocurrencies reflects a lucrative pool of funds. South Korean retail investors are world-renowned for their fervor for cryptocurrencies, and the premium is essentially a result of supply falling short of demand, with large amounts of Korean won flooding in to chase limited crypto assets.
This means that South Korean exchanges' hot wallets hold far more liquidity than other markets. For hackers, this is a gold mine.
Third, they had an advantage in language. Lazarus' attacks didn't rely solely on brute-force techniques. They were adept at social engineering, such as forging job postings, sending phishing emails, and impersonating customer service to obtain verification codes.
North and South Korea share the same language and culture, with zero language barrier, which significantly increases the success rate of targeted phishing attacks against South Korean employees and users.
Where did the stolen money go? That's probably the most interesting part of the story.
According to a UN report and tracking by several blockchain analytics firms, the cryptocurrency stolen by Lazarus ultimately flowed into North Korea's nuclear weapons and ballistic missile programs.
Previously, Reuters cited a confidential UN report stating that North Korea used stolen cryptocurrency funds to help fund its missile development program.
In May 2023, Anne Neuberger, the White House Deputy National Security Advisor, publicly stated that about 50% of the funding for North Korea's missile program came from cyberattacks and cryptocurrency theft; this figure was a further increase from the "about one-third" she gave in July 2022.
In other words, every time a South Korean stock exchange is hacked, it may indirectly contribute to the development of nuclear warheads on the other side of the 38th parallel.
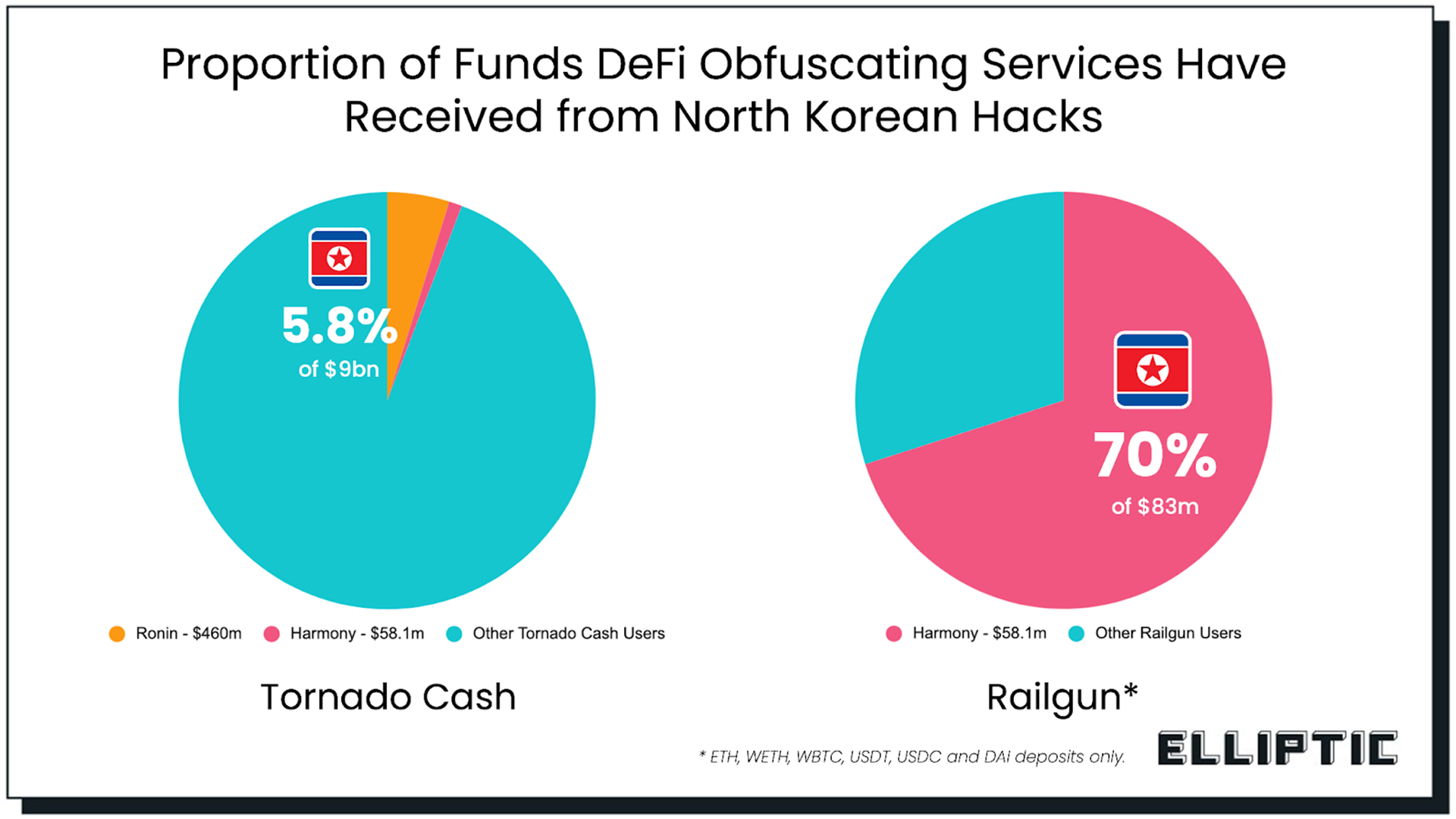
Meanwhile, the money laundering methods are quite sophisticated: stolen assets are first split into countless small transactions using "stripping chain" technology, then their origin is obscured by coin mixers (such as Tornado Cash and Sinbad), then they are exchanged for Bitcoin at a discounted price through a North Korean-built exchange, and finally exchanged for fiat currency through underground channels in China and Russia.
In 2019, South Korean police officially released the results of their investigation into the theft of 342,000 ETH from Upbit. The investigation revealed that 57% of the stolen ETH was exchanged for Bitcoin at 2.5% below market value on three exchanges suspected to be operated by North Korea, while the remaining 43% was laundered through 51 exchanges in 13 countries. The entire process lasted several years, and the vast majority of the funds have yet to be recovered.
This may be the fundamental dilemma facing South Korean stock exchanges:
On one side is Lazarus, a hacker force supported by national resources, capable of operating 24/7, and willing to invest any amount of money; on the other side are commercial companies like Upbit and Bithumb.
Even top-tier exchanges that have passed censorship are still powerless when faced with state-sponsored high-persistence threat attacks.
It's not just a problem in South Korea.
Eight years, more than ten attacks, and approximately $200 million in losses—if you only consider this local news in South Korea's crypto industry, you're missing the bigger picture.
The ordeal of South Korean exchanges is a preview of the crypto industry's struggle against a national-level adversary.
North Korea is the most conspicuous player, but not the only one. Certain high-threat Russian attack groups have been linked to multiple DeFi attacks, Iranian hackers have launched attacks against Israeli crypto companies, and North Korea itself has long since expanded its battlefield from South Korea to the global arena, such as the $1.5 billion Bybit attack in 2025 and the $625 million Ronin attack in 2022, with victims across continents.
The crypto industry has a structural paradox: everything must go through a centralized entry point.
No matter how secure the blockchain itself is, users' assets will ultimately have to flow through "choke points" such as exchanges, cross-chain bridges, and hot wallets.
These nodes, which concentrate massive amounts of funds, are operated by commercial companies with limited budgets; for state-sponsored hackers, this is a highly efficient hunting ground.
The resources of the attacking and defending sides are fundamentally unequal; Lazarus can fail a hundred times, while the exchange can only fail once.
The kimchi premium will continue to attract global arbitrageurs and local retail investors. Lazarus will not stop just because it has been exposed. The battle between South Korean exchanges and state-sponsored hackers is far from over.
I just hope that next time your money gets stolen, it won't be your own.



