Canton Network: The first open, scalable, privacy-enabled enterprise blockchain protocol
On May 9, the financial technology company Digital Asset announced that it will launch a privacy-enabled interoperable blockchain network (Canton Network), which aims to provide institutional clients with a decentralized infrastructure. Its participants include BNP Paribas ( BNP), Deloitte, CBOE Global Markets (CBOE), Goldman Sachs (GS), Broadridge (BR), S&P Global and Microsoft (MSFT), among others.
“Canton Network is a strong response to the industry’s call for a solution that harnesses the potential of blockchain while preserving the fundamental privacy requirements of institutional finance,” said Chris Zuehlke, partner at DRW and global head of Cumberland, another participant. "This unique approach, coupled with the ability to execute atomic transactions across multiple smart contracts, are the building blocks needed to bring these workflows on-chain."
The network connects applications built using Daml, Digital Asset's smart contract language, allowing various systems in financial markets to interoperate and synchronize.
"Solutions like this are a key component of the infrastructure for future digital and distributed financial markets," said Jens Hachmeister, Head of Issuer Services and New Digital Markets at Deutsche Börse AG.
secondary title
Canton Network: A network of networks for smart contract applications
Features:
Release the scale value of network connections;
Security, privacy and scale are guaranteed at the same time;
The first open blockchain network to support privacy protection;
selective decentralization;
Existing blockchain networks have two limitations that significantly limit effective adoption by traditional financial institutions and other businesses. The first limitation is that each application is required to inherit the governance properties of the underlying network and a fully transparent privacy model; the second limitation is that the transaction throughput is low and will be blocked.
According to the white paper, the existing blockchain network has the following limitations:
1. All assets, applications, and users share all data permanently and publicly. But most assets are heterogeneous;
2. The connection between assets and applications is decentralized, and application operators cannot easily control the interaction between users and applications;
3. Applications compete for global network resources;
4. Applications cannot be expanded independently or choose which infrastructure provider to deploy on;
5. Gas is interactive and unpredictable. An increase in the usage of an application will increase the cost of all users.
Additionally, existing blockchains lack support for application heterogeneity, leading to two important negative consequences: First, due to the privacy constraints of these networks, only those assets and data that can be part of a permanent public record can be permanently public. Assets and data as part of records are brought onto public blockchains; experiments with cryptocurrencies and NFTs are seen, but we don’t see businesses and governments bringing traditional assets and records onto public blockchains.
Second, in order to overcome the competition for global shared resources, most of the application logic of blockchain applications is established off-chain, which means that key functions are run off-chain, negating the user's access to the public blockchain Expectations of independence and verifiability.
In Ethereum and similar blockchain networks, there are the following limitations:
1. Data is completely transparent to anyone who can connect to the ledger.
2. There are strict vertical restrictions on transaction capacity (Layer 1)
3. Layer 2, side chain and other scalability solutions lack the composability of transactions
secondary title
About Canton
Canton is a smart contract network. Developers can create any consensus-based application with complete control. Like the existing blockchain, Canton can synchronize data on the chain between participants in real time. Canton has built-in "Daml" The programming language of smart contracts makes the ledger of each application independent, and each asset or data has programmable privacy. In addition, Canton's scalability and independence improve network utilization and reduce gas costs.
As such, the Canton Network fills a major gap in the public ledger space: it hosts smart contracts on a single virtual ledger. It has smart contracts on a single virtual ledger, similar to Ethereum, Solana, Tezos, etc., and it has built-in privacy and optional transparency, similar to Bitcoin's Lightning Network and Zcash.
secondary title
Overview of the Daml programming language
Daml is an open-source 6-part smart contract language and framework designed to make it easy to develop, operate and maintain multi-party applications in a way that preserves privacy and data consistency. more specifically:
1.Daml provides some concepts to capture the rules governing real-world business transactions, which helps programmers only focus on business logic while avoiding common security pitfalls;
2.Daml allows specifying access and authorization policies in smart contract code, making them easy to keep in sync. Data is kept private by default, while access policies are easily defined so that smart contract programmers can understand and maintain them effortlessly;
3.Daml supports application interoperability;
4. Daml supports interoperability with other systems through integration tools.
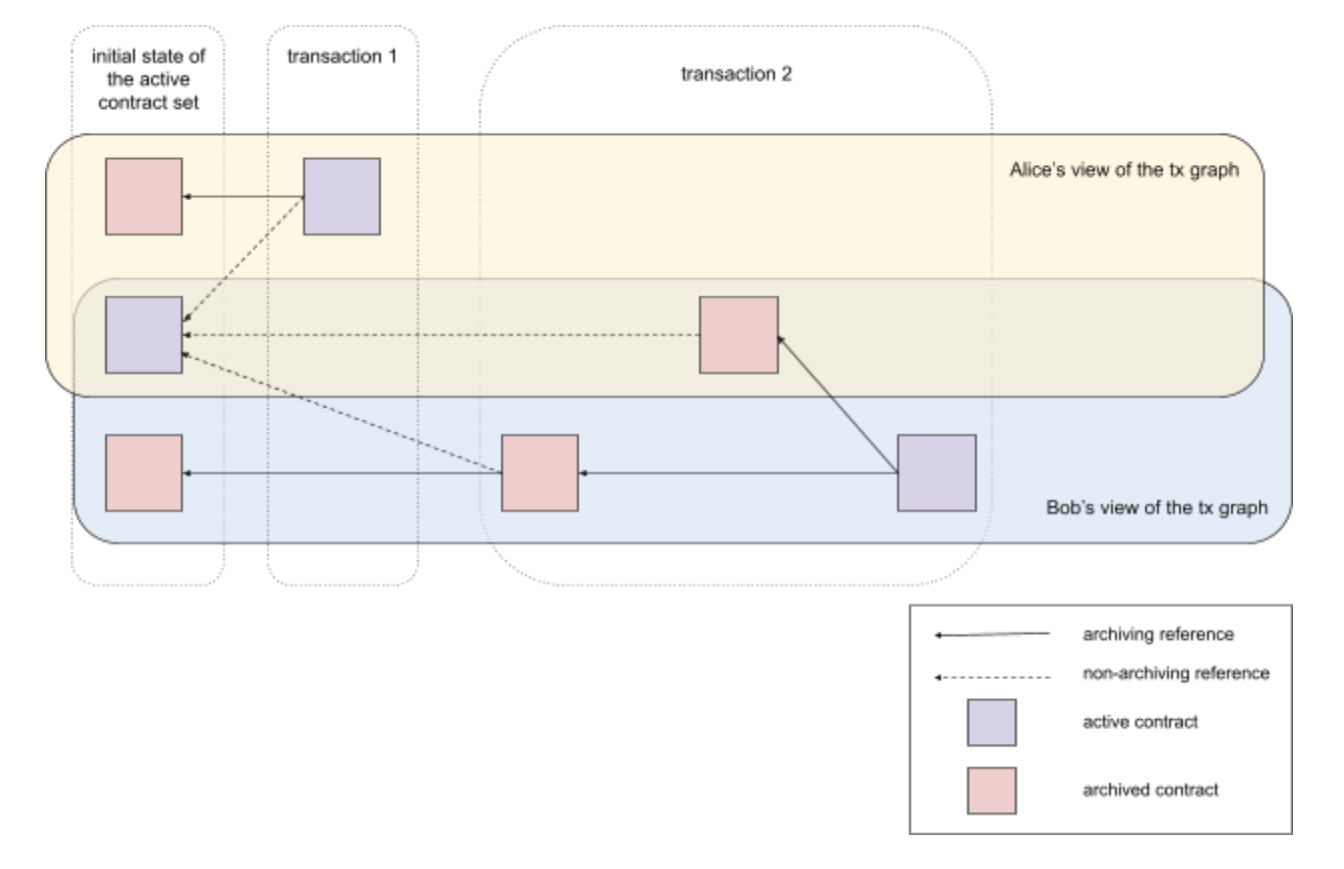
Figure 1: Transaction legend with subtransaction privacy. Alice and Bob each only have a partial view of the full transaction graph, transactions 1 and 2 submitted by Alice and Bob respectively evolve into an active contract set (ACS), archive the two initial contracts, and create two new active contracts .
The main difference from other blockchains is that in Canton, each party only sees a subset of the ACS and a subgraph of the global transaction graph, which is the view of one party. A subset of the global transaction graph, also known as a party's view. This party-specific view is always a valid ledger that can be verified locally by that party's nodes; the party does not need to trust any other party to be verified. Upon receiving a transaction or sub-transaction, a party's node will verify three things: that the transaction agrees with that party's point of view, that the transaction conforms to the logic in the smart contract, and that the transaction is properly authorized.
In addition to managing access control, we take this partitioning of the ledger a step further to allow for parallel processing. Since transactions explicitly declare their dependencies, independent infrastructure can process independent transactions in parallel; this allows the Canton network to scale out by increasing network capacity, adding capacity as network demand fluctuates.
Daml's well-defined authorization schema enables manual intervention by contract stakeholders to correct unexpected situations.
Templates specify exactly where, how and by whom to intervene during execution without requiring a priori knowledge of the exact type of intervention or any relaxation of security safeguards.
Signatories can agree to co-archive, upgrade or create new contract instances, as long as they agree. If any one of the signatories is a consortium, their consent is subject to the underlying consensus agreement of that party/consortium, e.g. a ⅔ supermajority may be required rather than unanimity, observers are entitled to be notified and can independently verify any such changes party, but its authorization is not required.
All actions on contracts—their creation, archiving, and calls to choices—are events in the event tree in the transaction and form a complete, non-repudiable audit log of all changes.
This ability to change contracts temporarily, with the appropriate authorization, enables application providers to upgrade data, processes, and operating procedures due to unforeseen events. For example, to deal with regulatory or judicial decisions that require retroactive modification of business transactions, Daml organizes templates into modules and packages, where packages can depend on other packages, including across applications that may be deployed to multiple networks.
This ability to rely on software packages in applications across different Canton subnets enables an open architecture. Architecture, where parties can combine workflows with other parties, like building blocks.
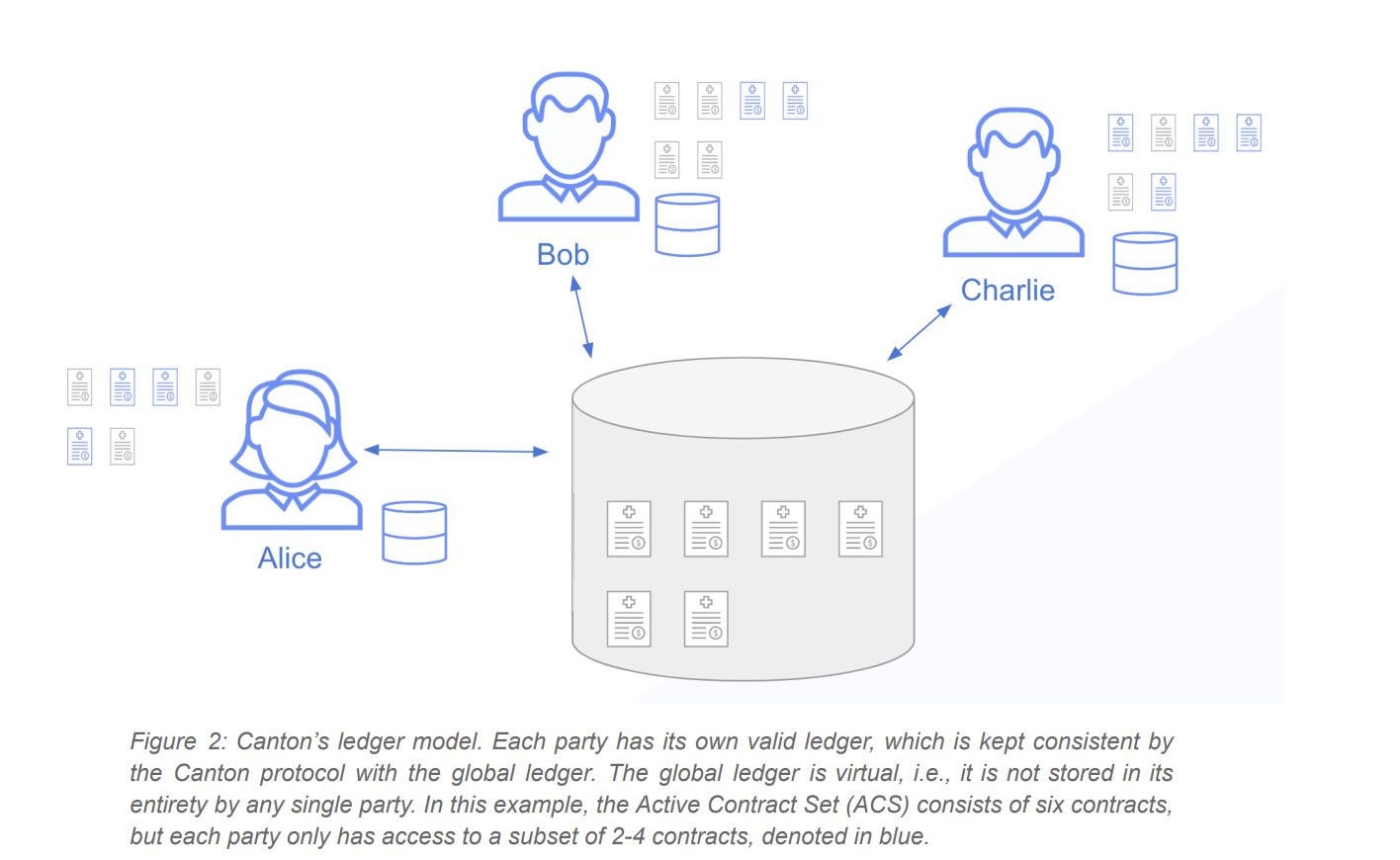
Network Topology
Nodes in the Canton network are called participant nodes. A user or company, called in Daml"Party"。
Represented as a party in Daml, one or more participating nodes are deployed; these participating nodes represent the party. To transfer data between nodes and determine the order of messages, each participant node connects to one or more private or public Canton Service Providers (CSPs). They operate a domain called a sync domain ("sync domain"), anyone can become a CSP and deploy a sync domain at will, and the reasons for deploying a new sync domain can include increasing throughput and reducing latency.
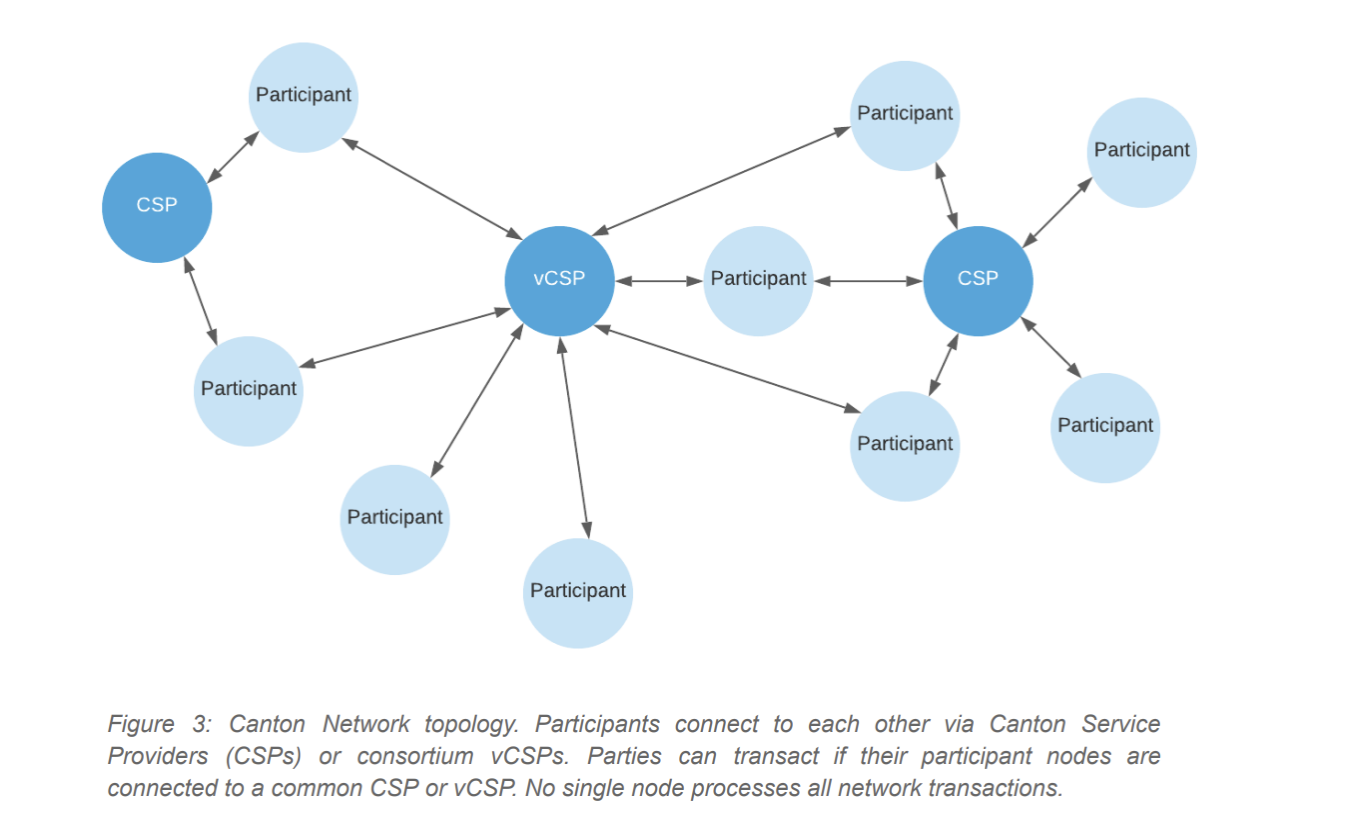
The Canton network has no single centralized administration or access and usage policies; each constituent node or subnetwork develops its own policies.
Data Storage and Processing
Canton provides history pruning and editing capabilities for its logs. Participants and sync domain operators can configure their nodes to store or prune historical encrypted data, allowing them to trade off auditability and the ability to delete archived contracts to comply with right-to-forget regulations such as the EU's General Data Protection Regulation.
secondary title
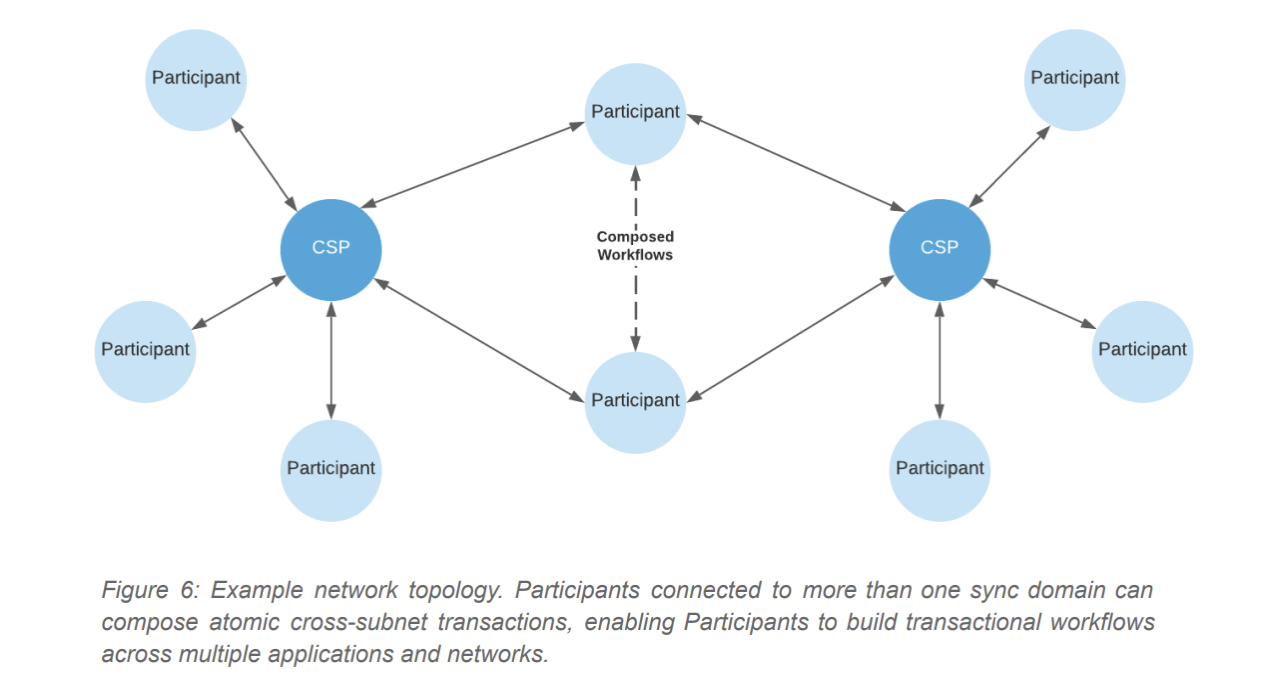
Part of the Canton Network
1. Application Providers - Application providers build and maintain smart contract applications. They operate one or more participating nodes, the backend infrastructure for applications, and the frontend network interfaces for those applications. Application providers can choose to be the CSP for their applications, or they can use the services of other CSPs.
2. Users - Most users interact with applications through Application Programmable Interfaces (APIs) and web user interfaces.
in conclusion
in conclusion
In this paper, we start from the limitations of existing public blockchains, namely the lack of privacy and scaling limitations imposed by a globally replicated state, and show how Canton creates a global network without these limitations. We further discussed the imminent opening of the Canton network to public use, with the launch of a virtual Canton Service Provider (vCSP), run by a Super Validator Collective (SVC). The permissioned Canton network currently in operation will become a subnetwork of the open Canton network, making the Canton network the first public blockchain for institutional assets.