Hacking incidents occur frequently, please accept this Crypto anti-theft guide
This article comes from MediumThis article comes from

, the original author: Kofi Kufuor, compiled by Odaily translator Katie Kufuor.Hackers have stolen more than $2 billion from encryption apps this year. During the National Day, the industry experienced anotherTokenPocket flash exchange service provider was stolen(losing more than $21 million) andBNB Chain cross-chain bridge BSC Token Hub was attacked
(losing approximately $566 million) in crypto theft.
As the crypto ecosystem grows, the security battle will only intensify. Therefore, this article will:
Propose a taxonomy of cryptographic security incidents;
List the most profitable attack methods for hackers so far;
Discuss the future of cryptographic security.
first level title
The encrypted application ecosystem consists of interoperable protocols, supported by smart contracts, and relies on the underlying infrastructure of the chain and the Internet. Each layer of this stack has its own unique vulnerabilities. We can classify cryptographic hackers based on the layer of the stack exploited and the method used.
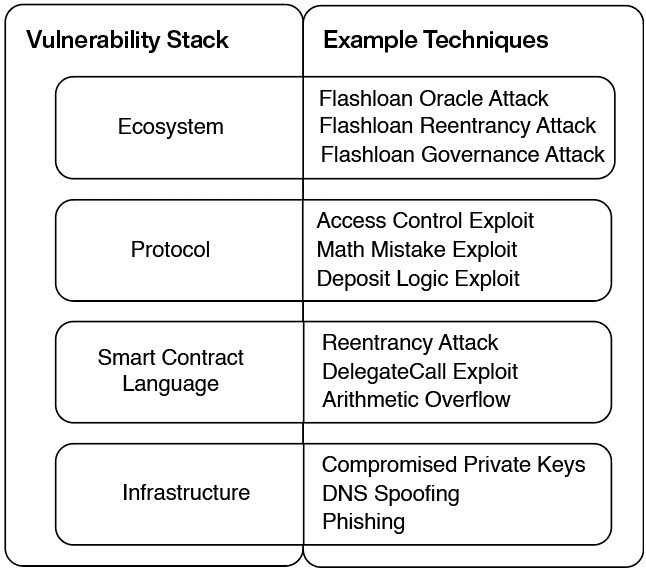
secondary title
Attacks on the infrastructure layer exploit weaknesses in the underlying systems of cryptographic applications: reliance on blockchains for consensus, internet services for front-ends, and tools for private key management.
secondary title
Hackers at this layer take advantage of the weaknesses and vulnerabilities of smart contract languages such as Solidity, such as reentrancy and the dangers of implementing delegate calls, which can be circumvented by following security specifications.
secondary title
attack protocol logic
This type of attack exploits errors in the business logic of a single application. If a hacker finds a bug, they can use it to trigger behavior that the application developer didn't expect.
Protocol logic level attacks can also exploit governance systems used to control application parameters.
secondary title
attack ecosystem
first level title
data analysis
data analysis
I've compiled a dataset of the 100 largest cryptocurrency hacks from 2020, totaling $5 billion in stolen funds.
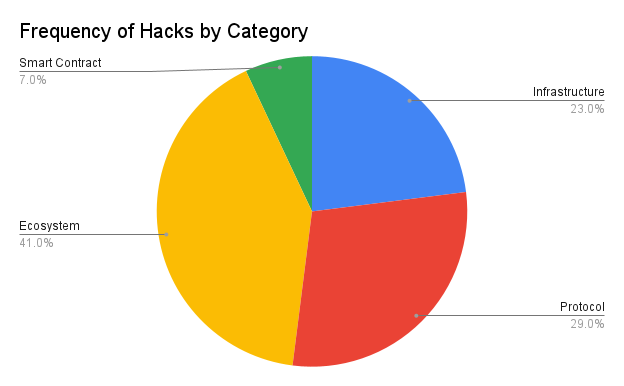
Ecosystems are most frequently attacked. They account for 41%.
Vulnerabilities in protocol logic resulted in the most monetary losses.
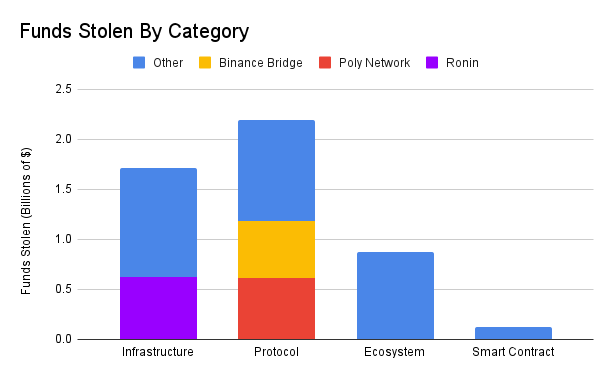
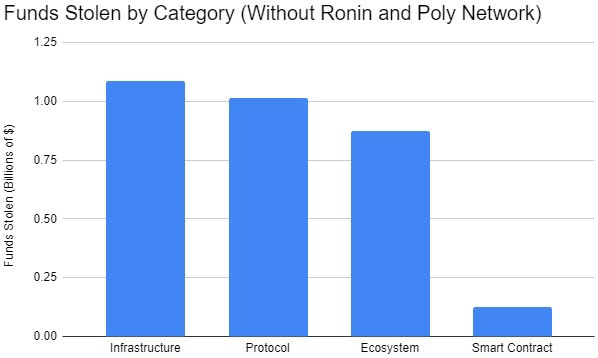
If the top three attacks are excluded, theft cases against infrastructure are the category that loses the most money.
secondary title
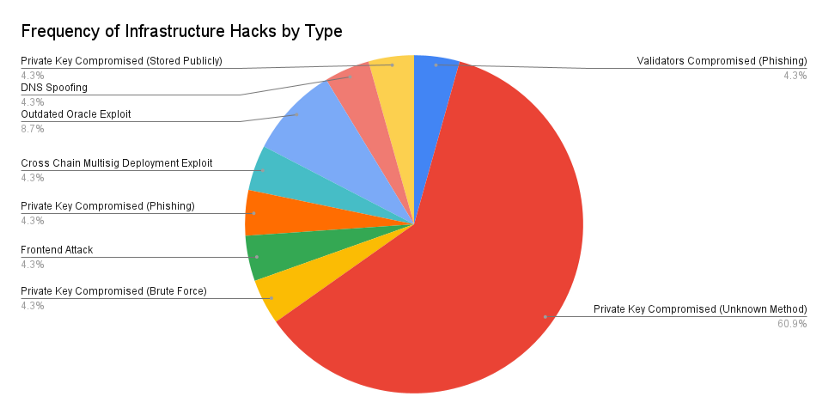
infrastructure
infrastructureIn 61% of infrastructure breaches, private keys were leaked through unknown means. Hackers may use phishing emails andand other social attacks to obtain these private keys.
secondary title
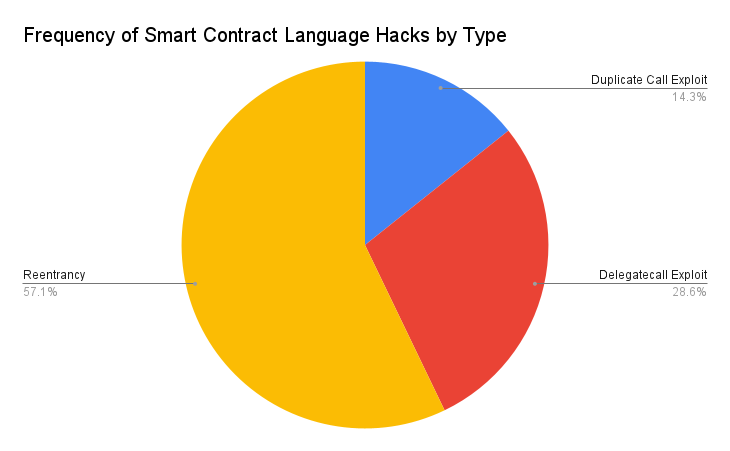
smart contract language
Reentrancy attacks are the most popular attack type at the smart contract language level.
For example, in the Siren Protocol hack, the function to withdraw collateral tokens was easily re-entrant and called repeatedly (every time the malicious contract received tokens) until all collateral was exhausted.
secondary title
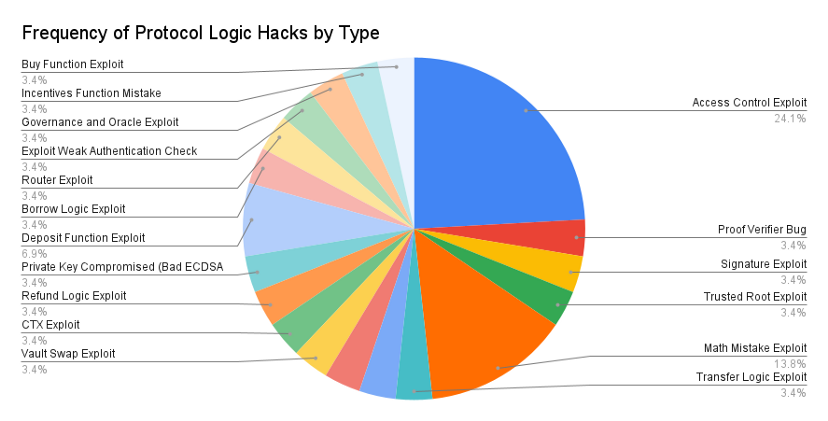
protocol logic
Most vulnerabilities on the protocol layer are unique to a particular application, since each application has unique logic (unless it is a pure fork).
Access control errors were the most common recurring issue in the sample group. For example, in the case of the Poly Network hack, the "EthCrossChainManager" contract had a function that anyone could call to perform cross-chain transactions.
For example, many Compound forks such as CREAM, Hundred Finance, and Voltage Finance fell victim to reentrancy attacks because Compound's code didn't need to check the effects of an interaction before allowing it. This worked well for Compound because they vetted every new coin they supported for vulnerabilities, but the team making the fork didn't.
secondary title
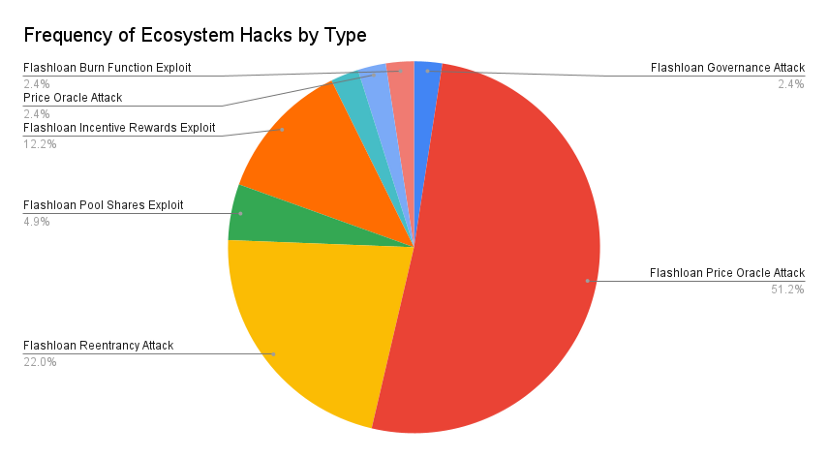
ecosystem
Flash loan attacks generally follow the following formula: use the loan to make a large transaction, driving up the price of the token on the AMM that the loan protocol uses as a price feed. Then, in the same transaction, use the inflated token as collateral to obtain a loan far above its true value.
first level title
Where do hackers start?
The dataset is analyzed according to the chain on which the stolen contract or wallet resides. Ethereum had the highest number of hackers, accounting for 45% of the sample group. Binance Smart Chain (BSC) came in second with a 20% share.
There are many factors that contribute to this situation:
Ethereum and BSC have the highest TVL (funds deposited in the app), so the scale of the reward is larger for hackers on these chains.
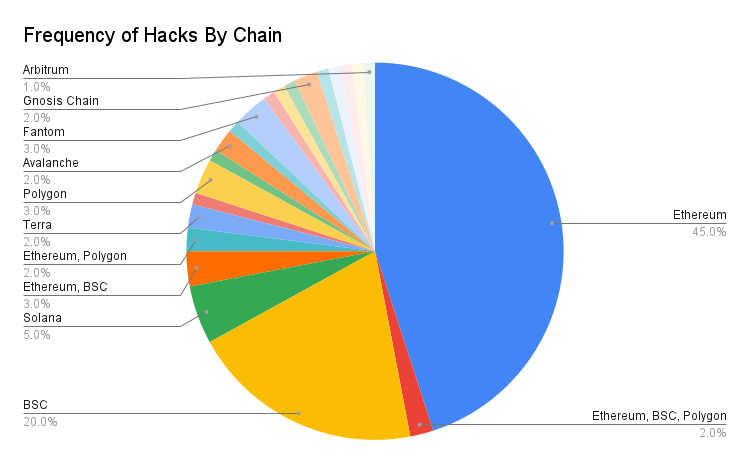
Most cryptocurrency developers are aware of Solidity, the smart contract language on Ethereum and BSC, and there are more sophisticated tools supporting this language.
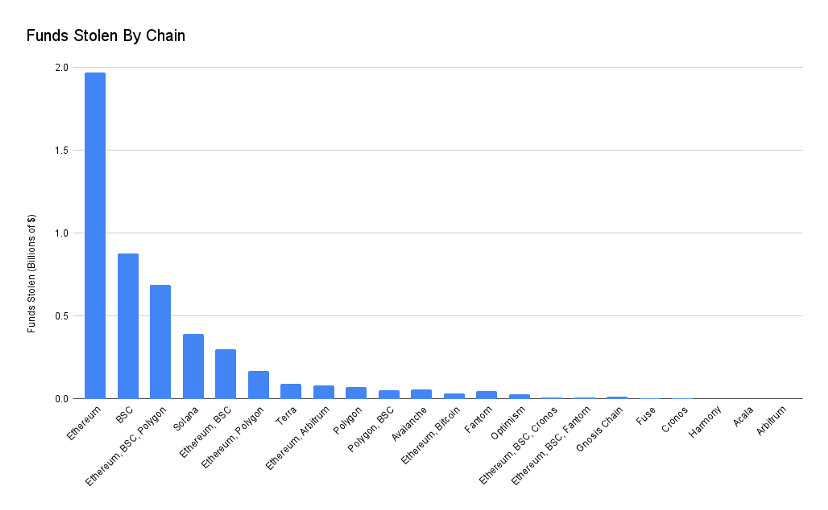
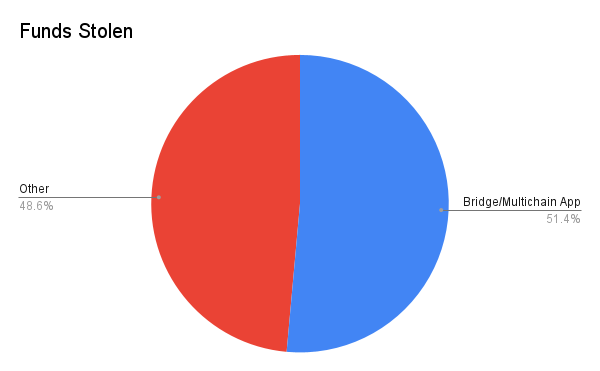
Involving cross-chain bridges or multi-chain applications (such as multi-chain transactions or multi-chain lending) has a huge impact on the dataset. Although these hacks accounted for only 10% of the total, $2.52 billion was stolen.
first level title
secondary title
infrastructure
infrastructure
Most large infrastructure hacks involve hackers obtaining sensitive information such as private keys. Following good operational security (OPSEC) steps and doing regular threat modeling can reduce the likelihood of this happening. A development team with a good OPSEC process can:
Identify sensitive data (private keys, employee information, API keys, etc.);
Identify potential threats (social attacks, technology exploits, insider threats, etc.);
Identify gaps and weaknesses in existing security defenses;
Develop and implement a threat mitigation plan.
secondary title
Smart contract language and protocol logic
1. Fuzzing tools
Fuzzing tools, such as Echidna, test how smart contracts react to a large number of randomly generated transactions. This is a great way to detect edge cases where specific inputs produce unexpected results.
2. Static analysis
Static analysis tools, such as Slither and Mythril, automatically detect vulnerabilities in smart contracts. These tools are great for quickly finding common vulnerabilities, but they only catch a predefined set of problems. If there is a problem with the smart contract that is not in the tool specification, it will not be found.
3. Formal verification
Formal verification tools, such as Certora, will compare smart contracts to specifications written by developers. The specification details what the code should do and the required properties. For example, when a developer builds a lending application, they specify that each loan must be backed by sufficient collateral. If any possible behavior of the smart contract does not conform to the specification, the formal verifier will identify the violation.
The disadvantage of formal verification is that the tests are only as good as the specification. If the provided specification does not address certain behaviors or is too permissive, the validation process will not catch all errors.
4. Audits and peer reviews
During an audit or peer review, a group of trusted developers will test and review the project code. Auditors will write a report detailing the vulnerabilities they found, along with recommendations for how to fix them.
Having a contract reviewed by a professional third party is a great way to find bugs that the original team missed. However, auditors are human too, and they will never catch all bugs. Also trust the auditors, if they find a problem they will tell you rather than exploit it yourself.
5. Ecosystem attack
Although ecosystem attacks are the most common and damaging type, not many of the existing tools are suitable for preventing these types of attacks. Automated security tools focus on finding bugs in one contract at a time. Audits often fail to address how the interactions between multiple protocols in the ecosystem are exploited.
Threat detection models can be used to spot malicious transactions in mempools, where transactions exist before nodes process them, but hackers can bypass these checks by using services such as flashbot to send transactions directly to miners.
first level title
The Future of Cryptographic Security
I have two predictions for the future of cryptographic security:
1. I believe the best teams will move from viewing security as an event-based practice (testing -> peer review -> auditing) to seeing it as a continuous process. They will:
Perform static analysis and obfuscation of every new addition to the main codebase;
Formal verification of every major upgrade;
Establish monitoring and alerting systems with responsive actions (pause the entire application or specific modules affected);
Have some team members develop and maintain a security automation and attack response plan.Security work should not end after an audit.
2. In many cases, such as the Nomad cross-chain bridge hack, the vulnerabilities were based on bugs introduced in post-audit upgrades.The process by which the crypto security community responds to hacks will become more organized and streamlined.
Whenever a hack occurs, contributors flood the encrypted secure group chat, eager to help, but a lack of organization means important details can get lost in the chaos. I think in the future, these group chats will transform into a more organized form:
Use on-chain monitoring and social media monitoring tools to quickly detect active attacks;
secondary title



