TokenPocket flash exchange service provider was stolen, quickly check how many "unlimited authorizations" you have opened
Today, the cross-chain DEX aggregator Transit Swap was attacked, causing a large number of users' funds to be withdrawn from their wallets. As of now, the estimated loss exceeds 23 million US dollars.
After discovering the theft, the Transit Swap technical team urgently suspended the service, the contract has been completely suspended, and no operations can be performed. Before the press release, Transit Swap officially announced that the cause of the previous hacking incident was a code error, and the hacker’s IP, email address, and related on-chain addresses have been identified. The Transit Swap team stated that it will try its best to track down the hackers and try to communicate with them to help users recover their losses.
According to SlowMist analysis, the main reason for this attack is that the Transit Swap protocol did not strictly check the data passed in by the user during the token exchange, which led to the problem of arbitrary external calls. Specifically, the routing contract itself does not impose any restrictions on the transferFrom parameter, nor does it check the parsed exchange contract address and call data. The attacker takes advantage of the defect that the routing proxy contract, routing bridge contract, and authority management contract do not check the incoming data, and calls the callBytes function of the routing bridge contract through the routing agent contract to transfer the constructed data, thereby stealing all permissions. Tokens for users who manage contracts for authorization.
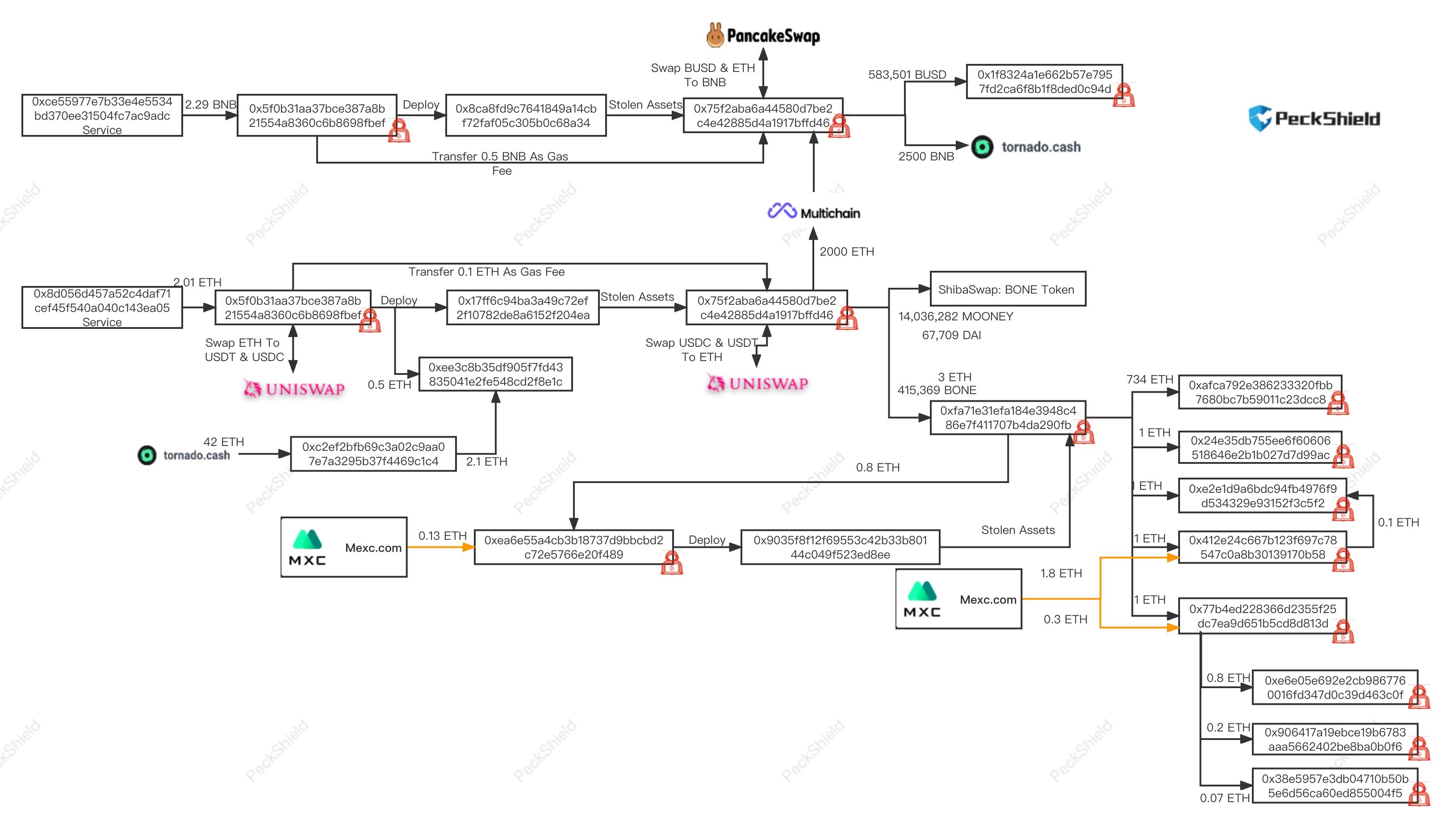
At present, the hacker has transferred 2,500 BNB to Tornado Cash, and the remaining funds are scattered in the hacker's address. After analyzing the traces of hackers, it was found that hackers had traces of deposits and withdrawals from platforms such as LATOKEN.
In addition, the security team PeckShield has confirmed the flow of hacker funds.
secondary title
What is flash exchange?
At present, almost all wallets have embedded DeFi functions, and some wallets have created and applied the concept of "flash exchange" for the sake of ease of use.
The so-called flash exchange is deeply integrated with the wallet, which has a more obvious independent entrance, a simpler operation process, and more convenient operation in the product. Users who use Quick Exchange can conveniently and quickly complete encrypted asset transactions. For example, the "Approve" operation is usually integrated into the transaction process with a simple one-click operation, and the user is almost insensitive.
secondary title
How many risks are hidden in contract authorization?
"No one can forcibly take away your encrypted assets" is a broad consensus among investors on the characteristics of blockchain. Once the assets on the chain are owned by the wallet, there is no coercive means to transfer them. But when we use DEX for on-chain transactions, how does DEX take one asset and transfer it to another asset?
Licensing is the key to all this. Before users sell assets on DEX, they need to perform the "Approve" operation. After this operation, the contract has the authority to use a certain token of the user.
secondary title
Audit = Security?
Even if the contract has the ability to transfer encrypted assets after authorization, it is still safe to use this ability only within a reasonable range. And if it has been audited by a trusted security agency, does it mean that this ability will not be abused, and only the necessary assets for the transaction amount will be transferred when the user conducts a transaction?
From a static point of view, this logic is valid. Just like Uniswap, although it has the ability to empty the user's wallet at any time, it will not really do so. But from a dynamic perspective, this logic is still dangerous.
In modern software development, upgrading is an indispensable ability. The same goes for smart contracts. In the Solidity smart contract, there are two upgrade methods, Transparent and UUPS. With these two functions, contract agency and upgrade are almost the standard configuration of contracts in the industry.
How does the project party upgrade the contract? Usually, the contract accessed by the user is not the core contract that directly runs the business logic, but a "proxy contract". After receiving the user request, the proxy contract forwards it to the core business contract, and then the business contract processes it. The contract upgrade is to replace the business contract that is finally forwarded to. To put it simply, although the smart contract cannot be modified, the contract that the user finally accesses and runs the business logic can be replaced. This is also a common practice in the industry.
And even for the most secure contracts, as long as the "contract upgrade" is carried out, its business contract has changed, and the previous audit report has become a piece of waste paper.
secondary title
How Dangerous Are Unlimited Licenses?
Fortunately, authorization does not mean that the user is exposed to the danger of wallet emptying at any time. Another important rule of the authorization mechanism is that authorization contains quantity. The user "Approve" contracts a certain number of tokens, and the contract can only use this amount at most, even if there are more tokens in the wallet, the contract can no longer be used.
But the danger is that most DeFi contracts are unscrupulously asking for "unlimited authorization" from users, that is, by default, the number of tokens approved by users is unlimited.
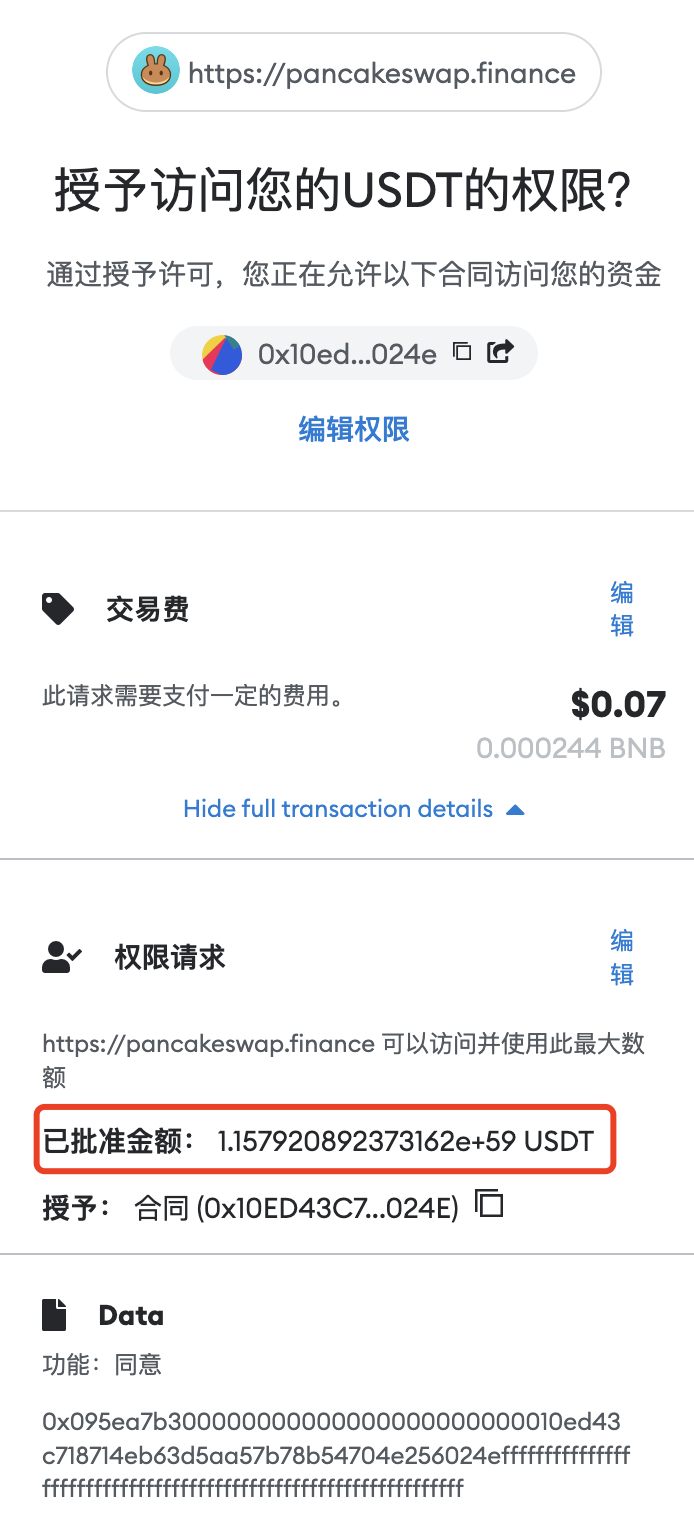
secondary title
How can users guard against it?
Without authorization, there is no security risk. When performing operations on the chain, if the Approve operation is required, the user should follow the principle of "how much is used and how much is granted". If I only need to sell 1000 TOKEN, then I should manually modify the Approve amount to 1000. It is accumulated when calculating the contract transfer amount, that is, if only 1000 is authorized, and the amount of this transaction is exactly 1000, the contract authorization amount has just been exhausted. Even if there is a security risk in the contract in the future, it is no longer possible to transfer any assets from the user's wallet.
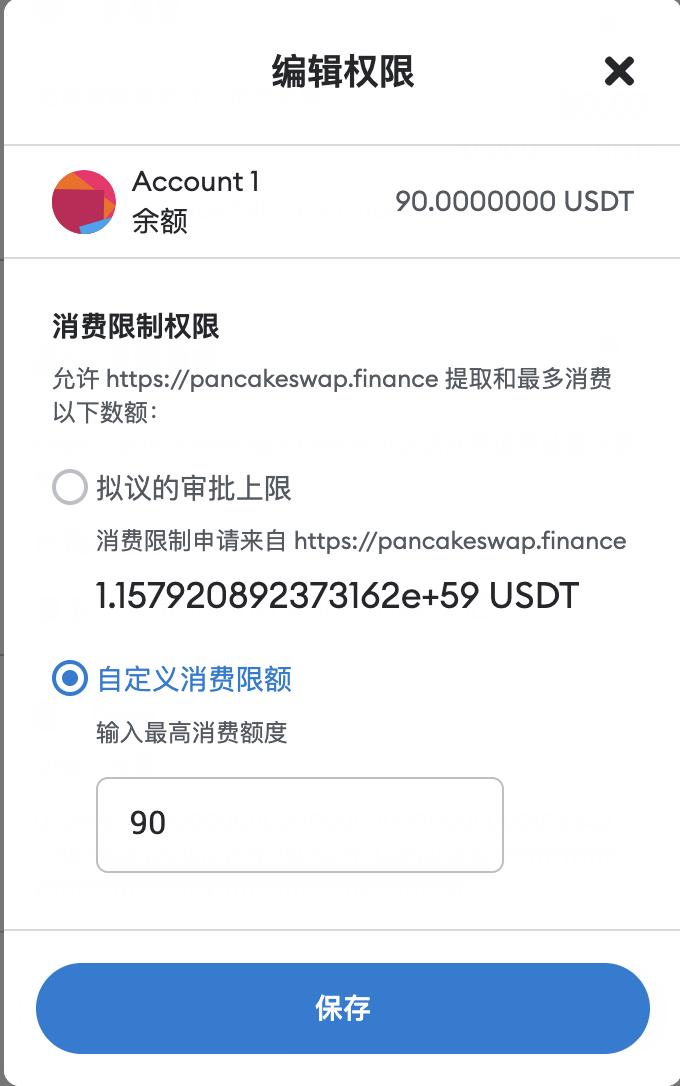
(Users can manually modify the authorized amount)
For authorized users, the deauthorization operation can also be initiated. (An interesting detail is that Ethereum does not support "deauthorization", which essentially authorizes the contract with a "0" amount.)
Commonly used deauthorization websites are as follows (recommended by the security company SlowMist):
1. Dappstar:https://tac.dappstar.io/#/
2. Revoke:https://revoke.cash/
3. Approved.zone:https://approved.zone/
4. Rabby Wallet
secondary title
https://cn.etherscan.com/tokenapprovalchecker
https://bscscan.com/tokenapprovalchecker
Who is responsible for the theft of DeFi?
"Dark Forest" is a widely circulated description of the order on the chain, and it also reminds users of the dangers and high risks of this world. But if such security incidents happen again and again, can it really be all attributed to the user's security awareness?
In such incidents, the DeFi project’s unrestrained request for user authorization is the original source of hidden dangers. Almost all projects, when requesting authorization, their default option is unlimited authorization. Although users can modify it manually, a responsible market should take responsibility for investor protection and user education.
How many crypto users are still unaware of the dangers of authorization? In this context, the project party is still asking for extremely dangerous unlimited authorization.
The abuse of authorization in DeFi has long been a common practice in the industry, and this high-risk situation endangers almost all users' huge assets. Its impact is far-reaching, extensive, and hidden dangers are huge. I am afraid that there is not yet a security risk that can be compared. This risk fundamentally violates the simple intuition that "no one can take the coins in the wallet". This is also the risk and challenge that the industry needs to face all the time.
After the theft happened, Shenyu made an appeal on Twitter, "I appeal to the project party to standardize the use of authorization functions, use as much authorization as you want, and don't use unlimited authorization. Everyone can rest assured."
Decentralization is full of opportunities and risks. Remember the original vision of crypto? "Protect your assets, no one can take away the cryptocurrency in your wallet." The establishment of a benign order does not require complicated codes and obscure concepts to ensure that every ordinary user can safely use encryption technology. It still requires the joint efforts of every participant in the industry.



