In-depth analysis of the working principles and security of 9 cross-chain bridges
Original title:How do Blockchain bridges really work & can you trust them?
Original title:
Author: Ross Middleton
Original source: Rhino.fi
Original compilation: Fenbushi Capital
Cross-chain bridges enable data and funds to flow freely between blockchains, thus playing an integral role in a multi-chain world. However, these cross-chain bridges have been the subject of controversy over the past few months following a series of destructive hacks.
On August 2, hackers stole more than $190 million from Nomad, a cross-chain bridge between Ethereum and Moonbeam. Coupled with this latest hack, Defi cross-chain bridge users have lost nearly $2 billion in less than 12 months.

This article is not to recommend which bridges to use, but to state the facts so as to help users make an informed choice. In this post, we will detail the pros and cons of each type of cross-chain bridge and how they actually work.
How to classify cross-chain bridges: by transmission type
Lock & Mint Examples: Polygon official bridge, StarkNet official bridge, Shuttle.
Token Issuer Burn & Mint MakerDao, Arbitrum Teleport.
Specialized Burn & Mint Hop, Debridge.
Atomic Swap Stargate.
Third Party Networks/Chains (Third Party Networks/Chains) Thorchain.Cross-chain bridges are distinguished by two types:Let's divide it from the transmission type first. The cross-chain aggregation protocol Lifi has identified three main types of cross-chain bridges according to the transmission type. Because the dividing line is a little fuzzy, it can actually be divided into five types.
first level title
Lock & Cast
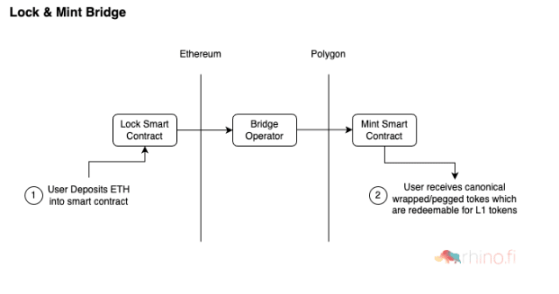
The simplest and most common cross-chain bridge involves locking and minting tokens and burning them. The following is the workflow diagram:
When the asset crosses the chain, the token from the source chain is locked into the smart contract of the cross-chain bridge, and then a new version is generated on the target chain, which can be a mapped token & a standard token.
Wrapped token: It will maintain a 1:1 anchor with the native token.
Canonical token: refers to the native tokens circulating on each chain.Both tokens are fully minted with their underlying assets fully collateralised. When the asset crosses the chain, the new token is burned on the target chain,and the native token is then unlocked/released on the source chain. This formula is very common: most "official" layer1>
advantage:
advantage:
100% collateralized to back the target chain token, making scale possible.
shortcoming:
Smart contracts on the source chain are easy targets for hackers, and if source chain funds are stolen, target chain tokens may be worthless. Hacker attacks are aimed at cross-chain bridge smart contracts that hold a large number of tokens. For example, in March 2022, hackers used the Ronin Bridge vulnerability to steal 600 million US dollars.
Slow cross-chain speed - when it comes to cross-chains from Polygon to Ethereum or from StarkNet/Ex to Ethereum, users may still be willing to wait a few hours, but for cross-chains on OP rollups such as Arbitrum and Optimism, users are not willing to wait a few days.
first level title
Burned & minted by the token issuer
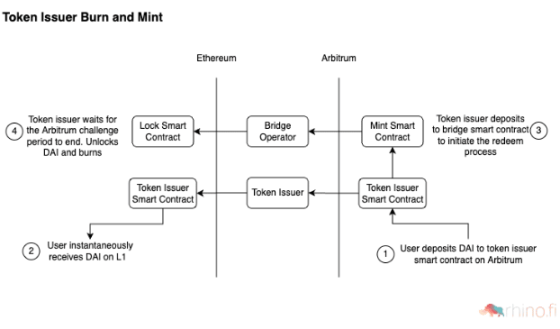
This approach is slightly different, providing liquidity across chains by incentivizing token issuers. In other words, when the OP rollup challenge period is relatively long, the token issuer can step in instead of relying on a third party to "provide" liquidity.MakerDao Arbitrum Teleporter。MakerDAO enables users to quickly obtain DAI, a cross-chain asset, when Wormhole returns to Layer1 from Arbitrum cross-chain. In this case, the MakerDAO protocol tracks the final settlement of funds in the background through a network of oracles.
advantage:
This approach removes friction costs for most users, while also keeping issuers safe with fraud-proof redundancy when the oracle network goes offline (eg MakerDao protocol).
shortcoming:
If MakerDao Arbitrum Teleporter is used, bad debts arise within Dao (such as MakerDao), and the issuer of the token needs to bear the risk of liability.
first level title
Specific Burning & CastingSome cross-chain bridge protocols combine the "burn and mint" model with AMM liquidity pools.
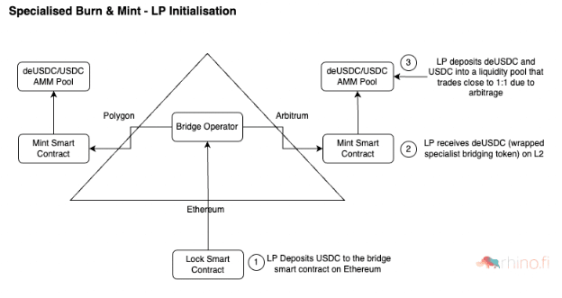
This liquidity pool can contain two or more assets, including specially minted cross-chain assets. Importantly, just like the Lock and mint bridges, this model facilitates quick asset cross-chain between Layer2 and other chains and back to the source chain. deBridge Finance and HOP fall into this category. When users lock ETH on a layer of Ethereum, deBridge will mint specific cross-chain bridge tokens (such as deETH) on Arbitrum and other chains.
As far as deETH itself is concerned, it does not have many use cases on Arbitrum, because there are other forms of ETH that are more widely used in this ecology. Liquidity providers can deposit a combination of ETH and deETH into the DeBridge liquidity pool, and can also (at Curve Factory) obtain transaction fees and arbitrage opportunities from cross-chain bridge users. Then set/initialize the cross-chain by casting specific cross-chain bridge tokens on each chain, and then through the AMM liquidity pool.
When slippage occurs in the AMM pool (when deUSDC or USDC is removed or added from the pool), external LPs rebalance the liquidity pool by depositing or withdrawing funds. In contrast, ordinary Lock&mint requires a longer waiting period when redeeming collateral. The Hop bridge works in much the same way, and both Hop and DeBridge have a reward and punishment system for node validators to ensure that the cross-chain bridge operates within a certain service level agreement.
advantage:
By using specific cross-chain bridge assets in the AMM pool as an intermediate step across chains, it can effectively increase the liquidity within the ecosystem, and at the same time allow LPs to earn arbitrage income due to slippage.
shortcoming:
This approach is more costly for users as the AMM liquidity pool does not provide a 1:1 exchange rate, resulting in slippage. There are also risks for LPs who deposit funds into a dedicated cross-chain bridge liquidity pool or hold cross-chain bridge assets (in the form of IOUs).
first level title
atomic swap
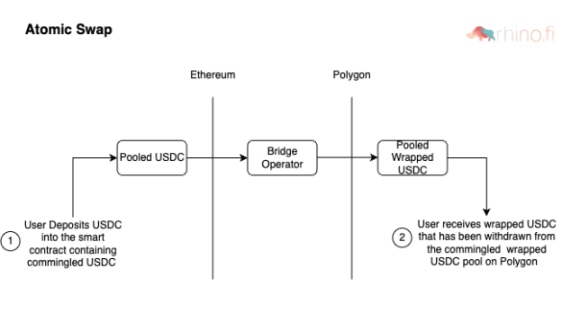
The Atomic Swap Bridge leverages pre-existing standard/mapped tokens (e.g. USDC) that already cross-chain to the target chain and pools these tokens in a single asset pool on both the source and target chains.
On the basis of the atomic exchange bridge, some bridges also add automatic market maker trading functions at the end to build additional services.
advantage:
Users will no longer rely on the security of the cross-chain bridge to ensure the token value preservation on the target chain. You can rely on another cross-chain bridge (in the case of a non-native token), or you can just hold the native token on the target chain. Asset transfers can also be very fast and cheap.
shortcoming:
Since the target chain pool needs a large amount of tokens to expand, it may be costly to incentivize token deposits through liquidity mining. Pools are also easily drained when there is a lot of one-way traffic.
first level title
It can be said that this type of transmission is not considered a cross-chain bridge at all, but a completely independent chain or network acting as an intermediate chain. When smart contracts and messaging are incompatible (such as the Bitcoin network), or cross-chain protocols need to achieve generalization goals (such as cross-chain communication), cross-chain assets in a decentralized manner require a third-party network/chain to act Bookkeeping and the middle layer. Such a network relies on a threshold signature system (node network) on the source chain and the target chain, and each node needs to be motivated to ensure honesty.
advantage:
Third-party networks and chains enable more blockchains to cross-chain in a decentralized manner.
shortcoming:
shortcoming:
These cross-chain bridges require the deployment of a large amount of capital. One is to motivate the nodes on each chain to maintain honesty, and the other is to establish a liquidity pool that requires continuous injection of funds. These systems are also more architecturally complex, the most famous example being ThorChain, which was hacked three times. In another case, third-party network Synapse prevented an $8 million hack in late 2021 after it discovered unusual activity in its AMM pool.
Distinguish cross-chain bridges with trust assumptions
In addition to different transport methods, we also need to consider different trust assumptions.
The different levels of confidence can be broken down into the following categories:
Centralized Bridges: Binance to Arbitrum
Verification/multi-sig bridges: Wormhole, Axelar, Connext.
Protocol level bridge: Cosmos IBC.
first level title
centralized bridge
Centralized bridges typically rely on single-party signatures to process and control the movement of funds. For example, when you advance from Arbitrum to Binance, you rely on Binance to credit your account with the funds that exist in the smart contract.
The centralized bridge solves the short-term demand for fast transfers. However, they are not transparent, scalable or censorship resistant, and thus limited to simple cross-chaining.
first level title
Verification/multi-signature bridge
These types of bridges are more secure than centralized bridges with weaker trust assumptions.
It incentivizes several different types of agents to act as oracles monitoring activity on both ends of the bridge and reporting ongoing deposits/withdrawals. However, this mechanism requires a certain amount of trust in the centralized validator, and in most cases it is nothing more than a basic multi-signature.
This is an example of a Connext bridge.
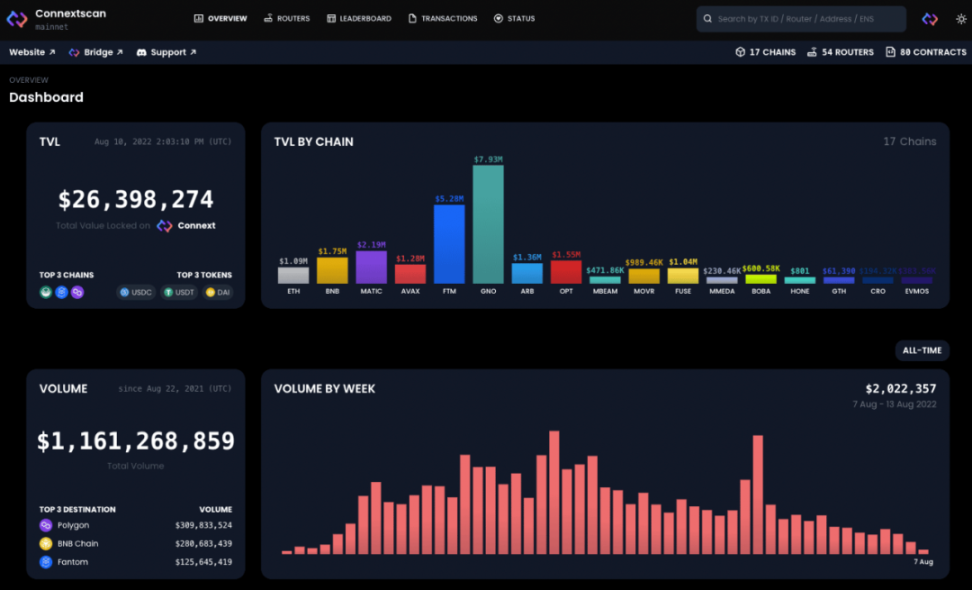
first level title
Status Proof Bridge
Proof-of-state bridges require weaker trust assumptions than validators. They prove the state between chains, which means validators don't need to act as oracles (these can be ZK proofs or optimistic proofs). Furthermore, Proof of State bridges do not require trust in any third parties, although relayers may still be required. No collateral is required on either side of the bridge, as these state proof bridges can be used to securely lock assets on the source chain and then “mint” assets on the target chain.
This is the mechanism of Hop Bridge.
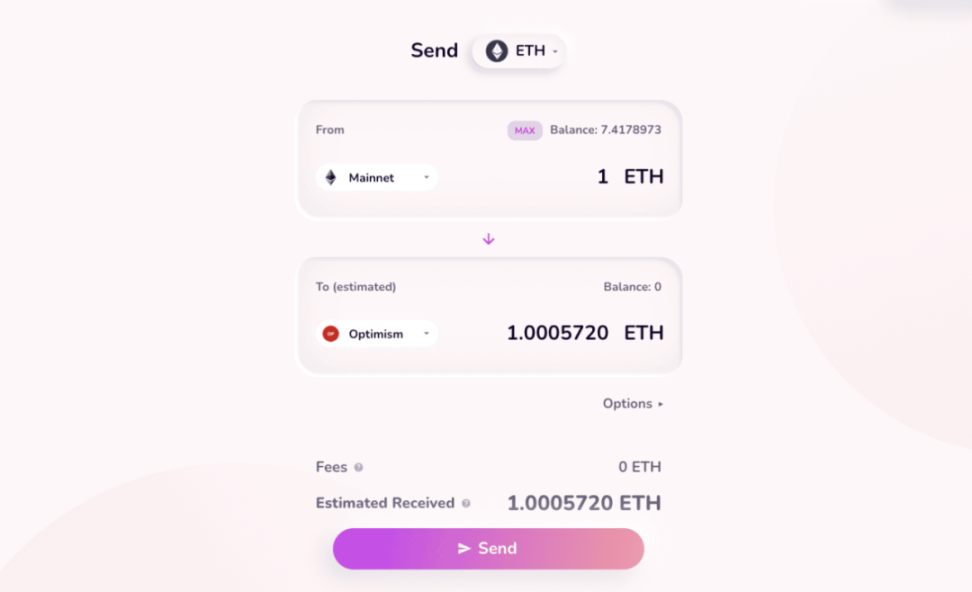
first level title
Protocol level cross-chain bridge
Protocol-level cross-chain bridges are the most friendly to trust assumptions. Perhaps the most notable example of this is the Interoperable Blockchain Protocol (IBC) in the Cosmos ecosystem. This is indeed a proof-of-state bridge, but it is also a protocol level that can be operated on different chains.
By implementing at the protocol level, it is possible to:
Completely eliminates the need for collateral on both sides of the bridge.
Make sure all chains have the same assets to mint and burn.
Standardize the interface on each chain.
Reduce the risk of hacking of smart contract-based cross-chain bridges.
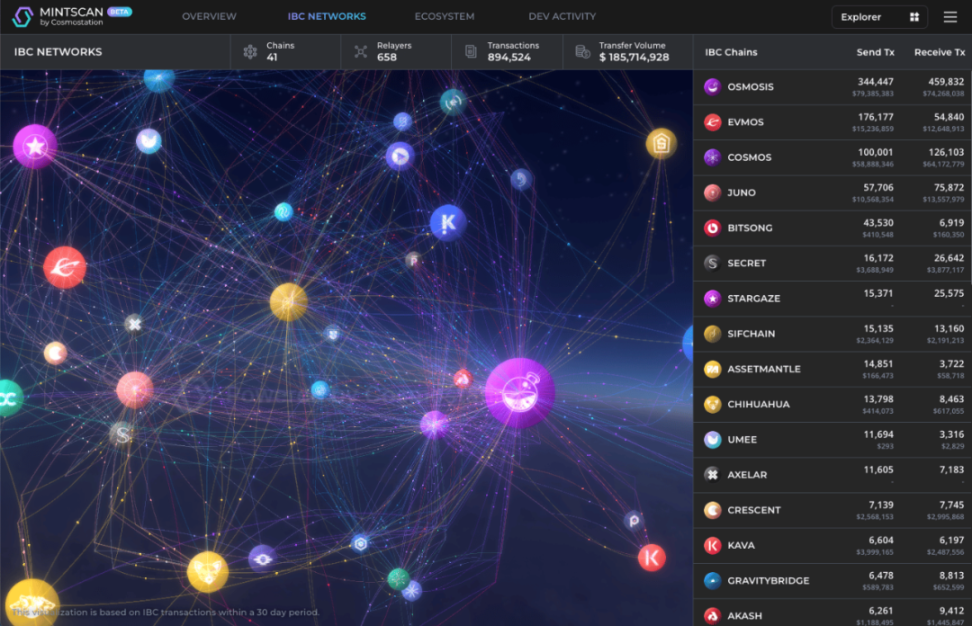
This is the visual interface of IBC:
In general, all mainstream public chains and ecosystems will use protocol-level cross-chains to maximize the liquidity and security of assets on the chain. Until now, the cross-chain bridge has failed to give a promise of asset security.
This doesn't mean you can't trust the bridge: despite the media reports whenever there is trouble, hacking is still a rare event, and the cross-chain bridge helps users solve the problem of asset circulation between chains, although the process is quite difficult (although rhino.fi is trying to solve this problem with its multi-chain feature).



