SlowMist: Vulnerability Analysis of "Zero Yuan Purchase" in TreasureDAO NFT Trading Market
Contract address
Related Information
Contract address
TreasureMarketplaceBuyer:
0x812cda2181ed7c45a35a691e0c85e231d218e273
TreasureMarketplace:
0x2e3b85f85628301a0bce300dee3a6b04195a15ee
Analysis of Vulnerability Details
1. The user purchases NFT through the buyItem function in the TreasureMarketplaceBuyer contract. This function will first calculate the total purchase price and enter the Token required for payment into the contract, and then call the buyItem in the TreasureMarketplace contract to buy NFT from the market to the TreasureMarketplaceBuyer contract , and then transfer the NFT to the user from the TreasureMarketplaceBuyer contract.
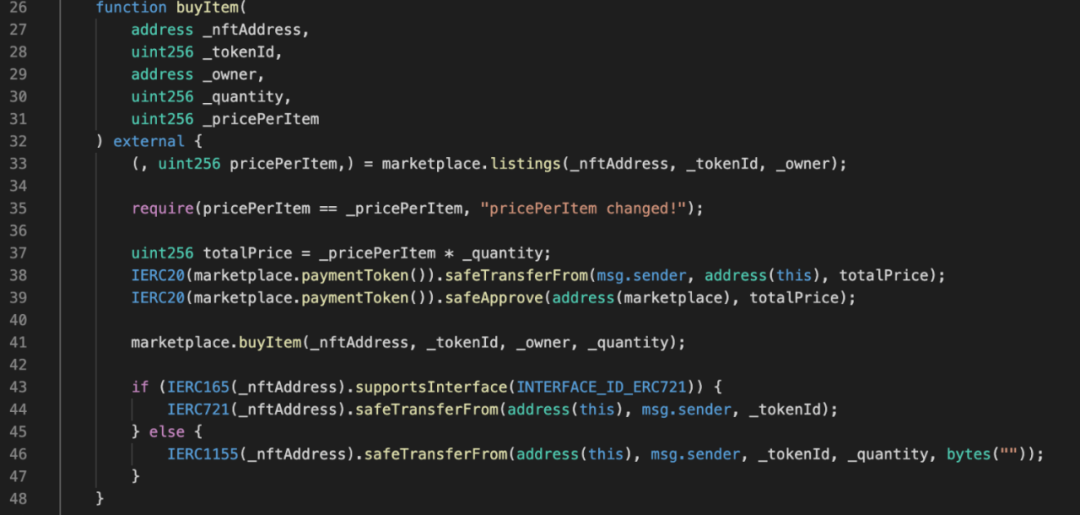
2. In the TreasureMarketplace contract:
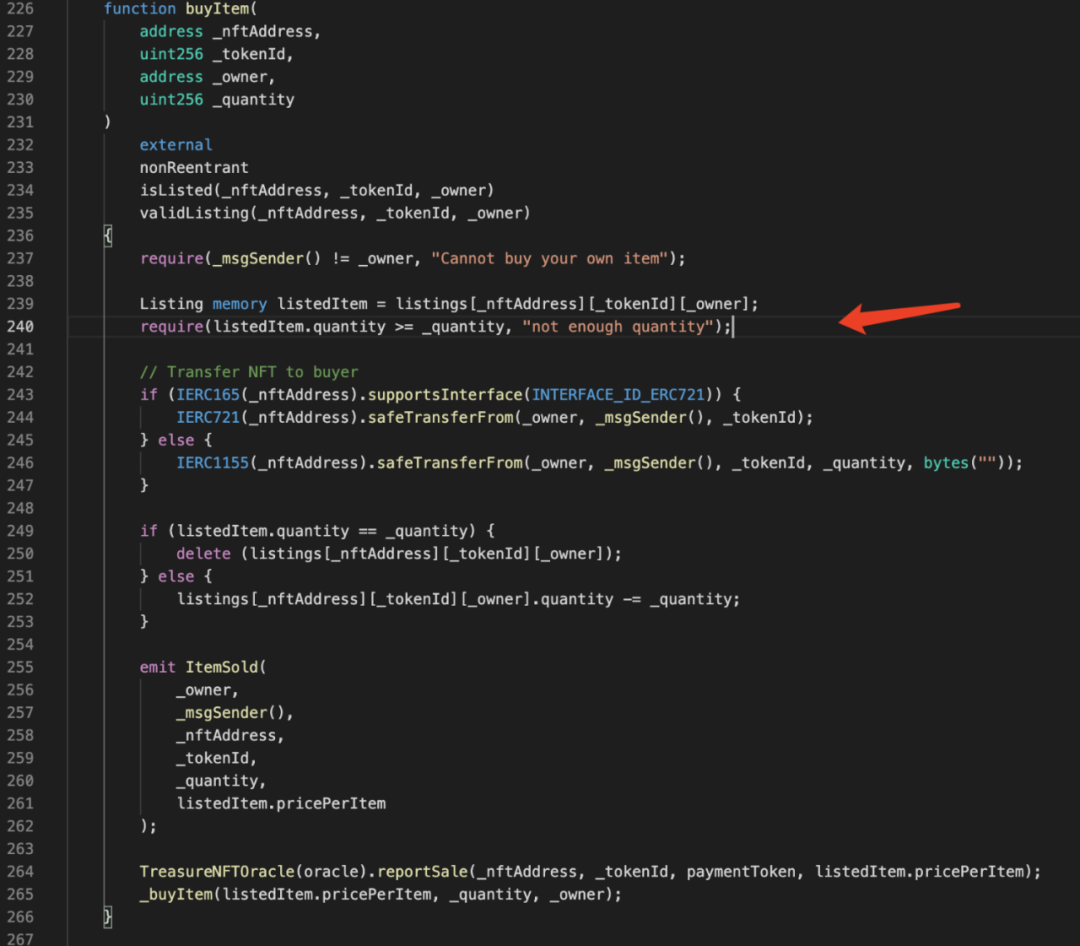
It can be found that if the incoming _quantity parameter is 0, you can directly pass require(listedItem.quantity >= _quantity,"not enough quantity"Attack transaction analysis
Attack transaction analysis
Attack transactions:
Attack transactions:
https://arbiscan.io/tx/0x82a5ff772c186fb3f62bf9a8461aeadd8ea0904025c3330a4d247822ff34bc02
attacker:
0x4642d9d9a434134cb005222ea1422e1820508d7b
Attack details:
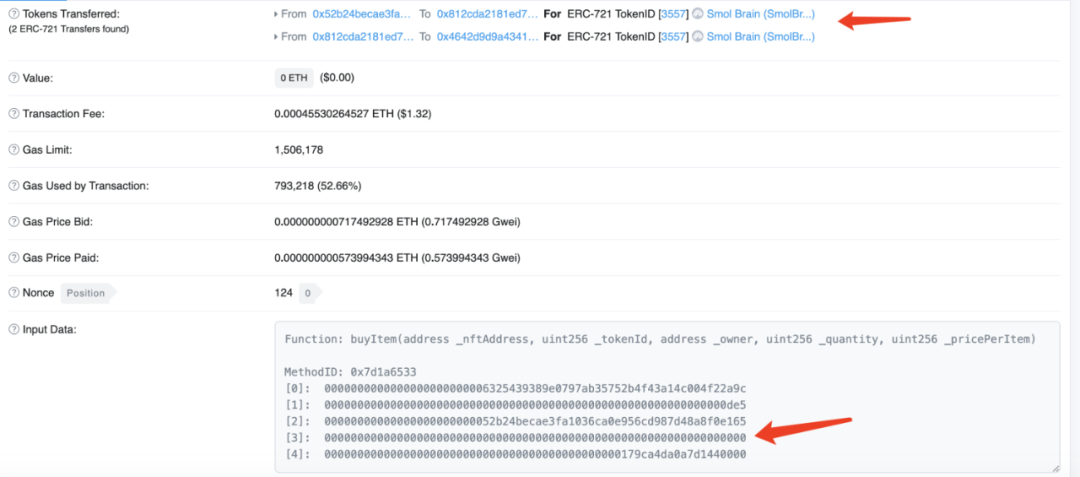
As can be seen from the figure below, the attacker calls the buyItem function in the TreasureMarketplaceBuyer contract and makes the incoming _quantity parameter 0.
Summarize
Summarize
The core of this vulnerability is that before transferring the NFT of the ERC-721 standard, there is a lack of judgment that the incoming _quantity parameter is not 0, which leads to the fact that the NFT of the ERC-721 standard can be transferred directly and the purchase of the NFT when calculating the price The required cost is calculated as 0. In response to such vulnerabilities, the SlowMist security team recommends that before transferring the NFT of the ERC-721 standard, it is necessary to make a good judgment on the incoming quantity to avoid such problems from happening again.



