An article to understand ransomware---the main profit method of hacker organizations

In June 2021, JBS USA Holdings, the U.S. subsidiary of Brazilian meat processing giant JBS SA, suffered a ransomware attack that shut down several of the company's factories responsible for processing nearly one-fifth of the nation's meat supply. An $11 million ransom in Bitcoin was paid to resolve the attack.
In recent years, ransomware attacks have occurred frequently. Computer hijacking will not only cause personal losses, but also damage key infrastructure in the fields of energy and electricity, endangering public safety.
first level title
The Past and Present of Ransomware
text
text
In 1989, the first ransomware appeared in the world, named "AIDS Information Trojan Horse". Its developer was a biologist named Joseph Pope who received a doctorate from Harvard University in 1989. He presented to the World Health Organization AIDS Conference Participants distributed 20,000 infected disks with"AIDS Information - Getting Started Floppy Disk", when the floppy disk is inserted into the computer, the following message is displayed:
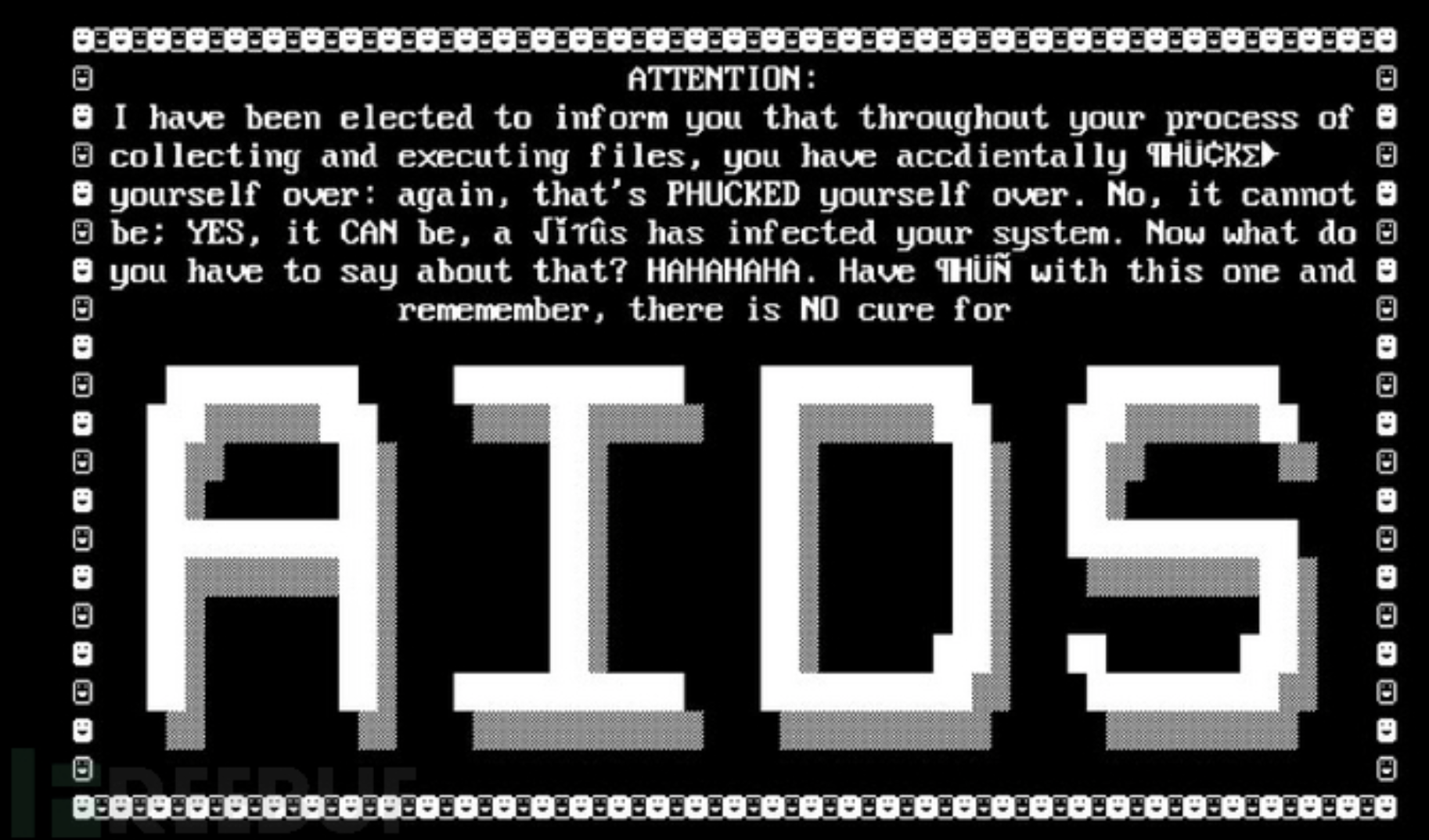
The ransom message required users to send $189 to PC Cyborg Corporation at a postal box in Panama to unlock access, and the first ransomware in history was born.
text
text
With the birth of Bitcoin in 2008, ransomware attacks have entered a new stage of development—the Bitcoin ransom stage. In the second half of 2013, a Trojan horse named CryptoLocker appeared, which is a malicious malware in the form of ransomware. Software, with the Windows operating system as the main attack target.
It is usually transmitted through email attachments. After the attachment is executed, a specific type of file will be encrypted, and then a payment message window will pop up.
The ransom message stated that if the bitcoin ransom is paid within the specified time limit, the files can be decrypted, otherwise the private key will be destroyed and the files can no longer be opened.
text
3. Explosion
image description
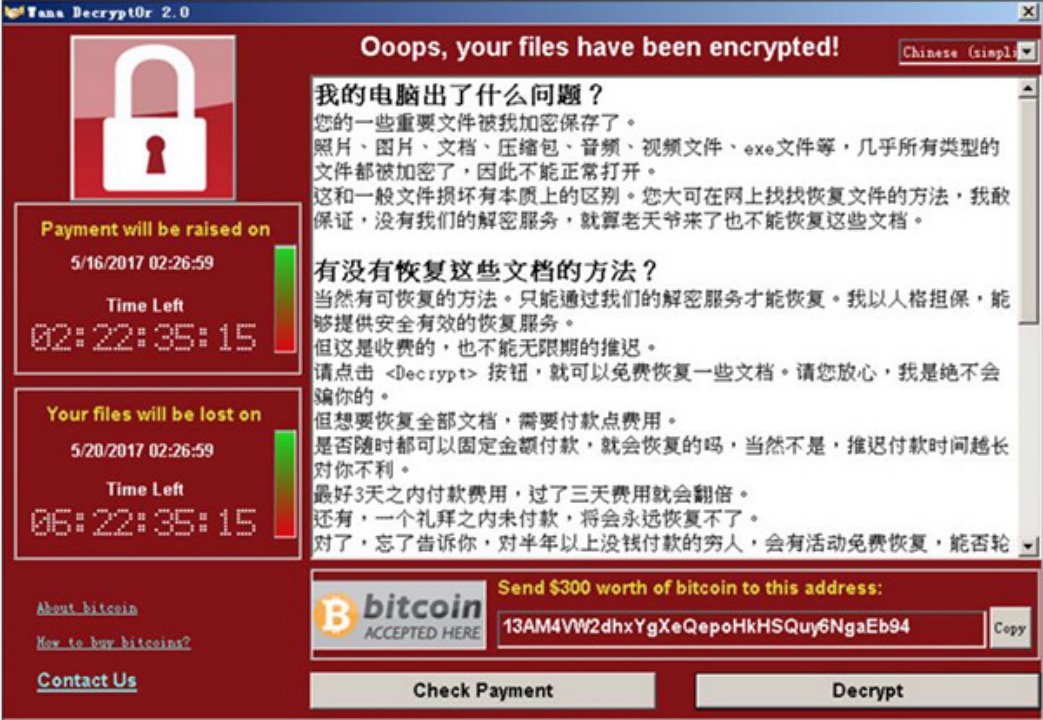
WannaCry lock screen
text
4. Platformization
text
5. Diversification
first level title
Several forms of ransomware
There are various forms of ransomware attacks, which can be mainly divided into: encrypting data, locking the system, data leakage, and intimidating users.
encrypted data: This form is the most common, because this form is the attack form with the largest number of victims and the widest social influence. Attackers usually use asymmetric encryption algorithms (almost impossible to crack in theory) to encrypt important data in the system of the attacked , data documents, etc., without the attacker's private key, the locked files cannot be decrypted. Then inform the user that if they want to open the profile data, they must complete the decryption by paying virtual currency.
locking system: After the system is locked, even the system cannot be logged in. For example, if the system power-on password is tampered with, the victim cannot access the server without a specific digital key. The attacker uses this as a threat to blackmail the user.
In early May 2019, hackers invaded and controlled about 10,000 government computers in Baltimore, Maryland, USA, and demanded 13 bitcoins (worth $100,000), but the city government refused to pay the ransom. Government departments cannot access servers without a specific digital key, government servants cannot access their email accounts, and ordinary citizens cannot use basic municipal services, including paying water bills, property taxes, and parking tickets.
data leak: This type of form is mainly implemented for hotels, enterprises, hospitals, etc. Hackers steal relevant confidential data (user privacy information, secret documents, etc.) This batch of data will be made public at a certain time.
intimidate usersfirst level title
Spread of ransomware
Ransomware is evolving rapidly and incorporates the propagation characteristics of many malware. New ransomware can quickly spread and infect the entire network in enterprises, encrypting various data that can be accessed, and even many enterprises have caused business losses due to this. Interruption, which poses a huge challenge to the security defense of enterprises.
Attackers spread ransomware by sending emails, which look extremely similar to the interface of some well-known institutions, brands, or social networking sites, to reduce the vigilance of the attacked, and the attackers put malicious links directly in the email As long as the attacker clicks on the link or opens the attachment, the file containing the ransomware will be automatically downloaded and triggered.
Case: Starting from March 11, 2019, an overseas hacker organization launched a blackmail virus email attack on relevant government departments in my country. The content of the email is "You must report to the police station at 3:00 pm on March 11!", and the attachment name is "03-11-19.rar".
The study found that the version number of the ransomware is GANDCRAB V5.2, which is one of the most active ransomware in China. Mail transmission is the most widely used way of transmission, and due to the use of RSA+Salsa20 encryption, the victim users cannot get The private key in the hands of the virus author cannot be decrypted. After the virus runs, it will encrypt the data on the hard disk of the user's host and require the victim to pay a ransom.
Website and Downloads
Users browse to infected websites and download software, misleading users into thinking it is genuine software when it is actually ransomware containing ransomware.
Case: In 2016, KeRanger, the first ransomware targeting the Apple operating system, was released. It spread rapidly through the installer of the already infected Transmission BitTorrent client. Mac OS X users who downloaded Transmission on March 4 and 5, 2016 were at risk from the malware.
Once a user installs the ransomware, KeRanger searches for about 300 different file types and encrypts any it finds. Subsequently, the ransomware will pop up a ransom note asking the victim to pay a ransom of 1 bitcoin, and ask the victim to complete the ransom payment through the dark web.
Spread by exploit
Attackers seize the misconception that many people think that patching is useless and will slow down the system, and then use vulnerabilities that have just been repaired or are not paid much attention to spread.
If the user does not update the system or install patches in time, even if the user does not perform any improper operations, it is possible to get ransomware without warning. This type of ransomware is no different from traditional ransomware in terms of destructive functions, but because of the different transmission methods, it is more difficult to prevent. Users need to improve their security awareness, update vulnerable software or install corresponding security patches as soon as possible.
Case: WannaCry is a "worm-like" ransomware software with a size of 3.3MB, which is spread by criminals using the dangerous vulnerability "EternalBlue" leaked by NSA (National Security Agency, US National Security Agency).
first level title
virtual currency as ransom
From a technical point of view, we have to admit that the combination of ransomware and virtual currency is perfect. Before virtual currency is widely used, it is not easy for virus makers to directly profit from ransomware. In addition to holding the victim's computer equipment or files hostage, the victim has to pay cash or bank transfer to obtain benefits, which is too easy to be caught by the police.
Therefore, in the past few decades, although ransomware has existed for a long time, it has not exploded on a large scale and caused a huge impact. The emergence of virtual currency has broken this balance. Victims pay in the form of virtual currency. The anonymity and global circulation of virtual currency can not only make cross-border transactions extremely fast, but also avoid supervision to a certain extent.
Businesses hit by ransomware receive a ransom note, which asks the victim to pay the ransom in virtual currency and often includes instructions on how to buy the virtual currency from an exchange.
first level title
Stop Loss and Precautions
When we have been confirmed to be attacked by ransomware, we should take necessary stop loss measures in time to avoid further expansion of losses.
After confirming that the server has been infected with ransomware, the infected host should be isolated immediately. On the one hand, it is to prevent the infected host from automatically continuing to infect other servers through the connected network; on the other hand, it is to prevent hackers from continuing to manipulate other servers through the infected host.
The common operation methods for isolation are disconnection and shutdown. The main operation steps of network disconnection include: unplug the network cable, disable the network card, and if it is a laptop, turn off the wireless network.
After the infected host has been isolated, other machines in the LAN should be checked to see if the core business system is affected, whether the production line is affected, and whether the backup system is encrypted to determine the scope of the infection.
In addition, if the backup system is safe, you can avoid paying the ransom and recover files smoothly.
Therefore, when it is confirmed that the server has been infected with ransomware and the infected host has been isolated, the core business system and backup system should be checked immediately.
Based on the characteristics of ransomware that is preventable, controllable and incurable, Zhifan Technology security experts remind everyone:
Business users: Build a network security protection system, strengthen data security protection, set up firewalls, update virus databases in a timely manner, obtain threat information extensively, and establish an enterprise virus early warning mechanism.
personal user: Improve network security awareness, regularly patch the operating system, do not click on emails, links and software from unknown sources, and back up important data and documents in time.



